Microsoft introduced the notion of managed identities for Azure resources. This feature permits Azure Resources like the Barracuda CloudGen Firewall to be integrated much faster and easier during the provisioning process into the cloud infrastructure. The VM can issue calls towards the Azure backend to read routing tables and the location of the resources and to adapt routing on HA failover.
For more information, see the Microsoft documentation website:
Enable Managed Identities for Azure Resources
During Deployment
During deployment of the Barracuda CloudGen Firewall using ARM templates, you can add the following snippet in the ‘Microsoft.Compute/virtualMachines’ resource on the same level as the ”type”: “Microsoft.Compute/virtualMachines” property.
"identity": {
"type": "SystemAssigned"
},
More information is available on the Microsoft documentation website:
An example ARM template can be found here:
The Barracuda CloudGen Firewall will automatically detect when managed identity is enabled, and enable cloud integration and fill in known fields: Enable Cloud Integration and Subscription ID (masked in the screenshot with a gray bar).
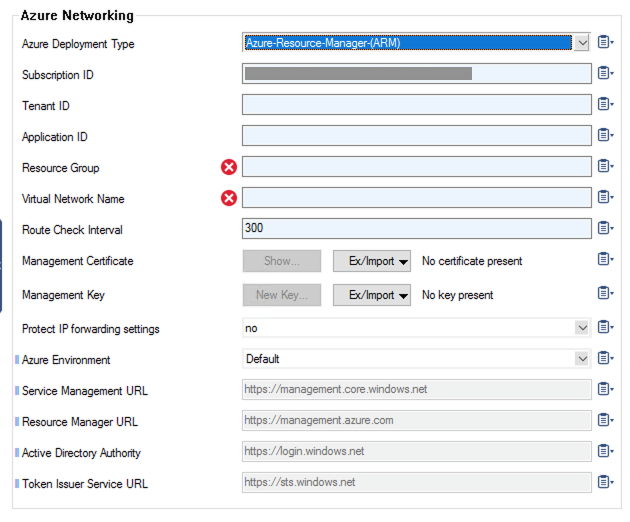
After Deployment
If you already have the Barracuda CloudGen Firewall deployed in your environment but want to enable a managed identity for Azure resources, you can do so via the Microsoft Portal, Azure CLI, Powershell, or other means.
In the Azure Portal, find your Barracuda CloudGen Firewall VM and open the Identity settings. To enable a managed identity for Azure resources, you need to set the System assigned option to on.
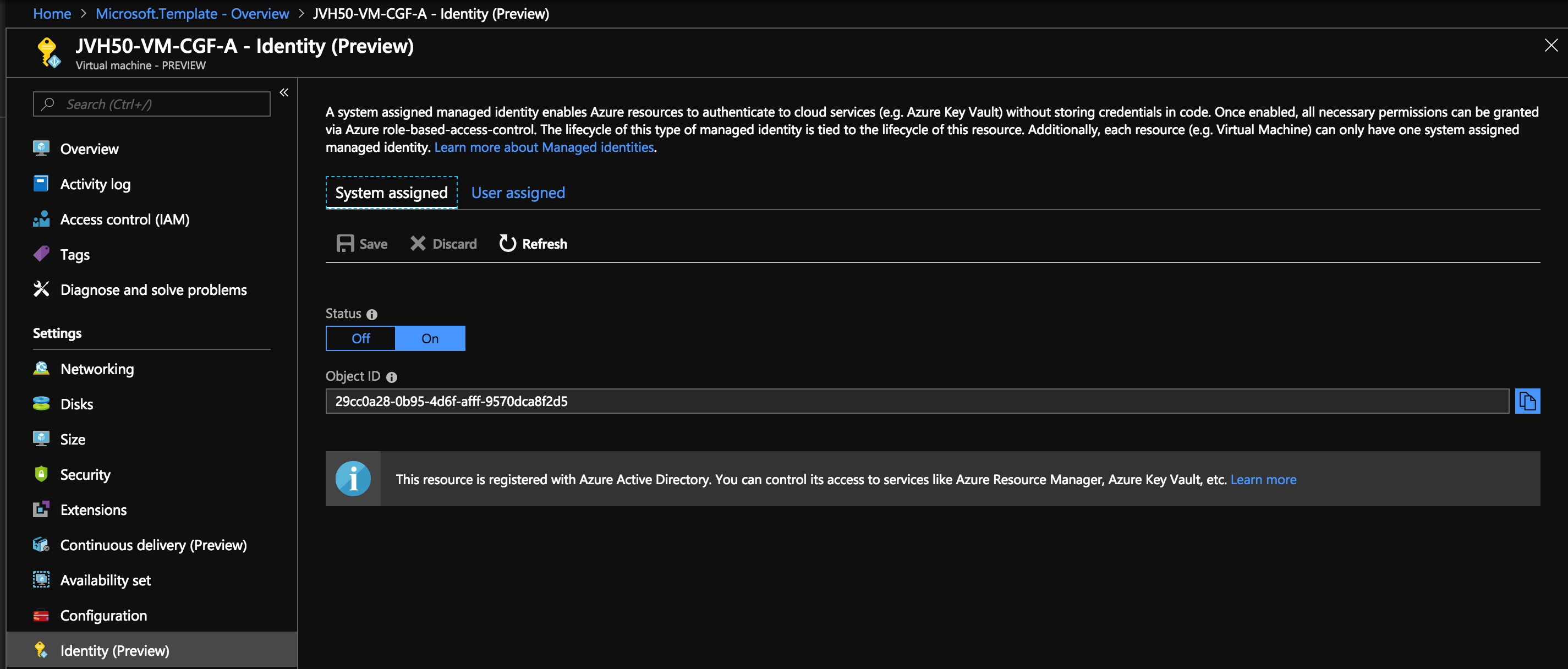
Other options are documented on the Microsoft documentation website:
Granting Access to Resources
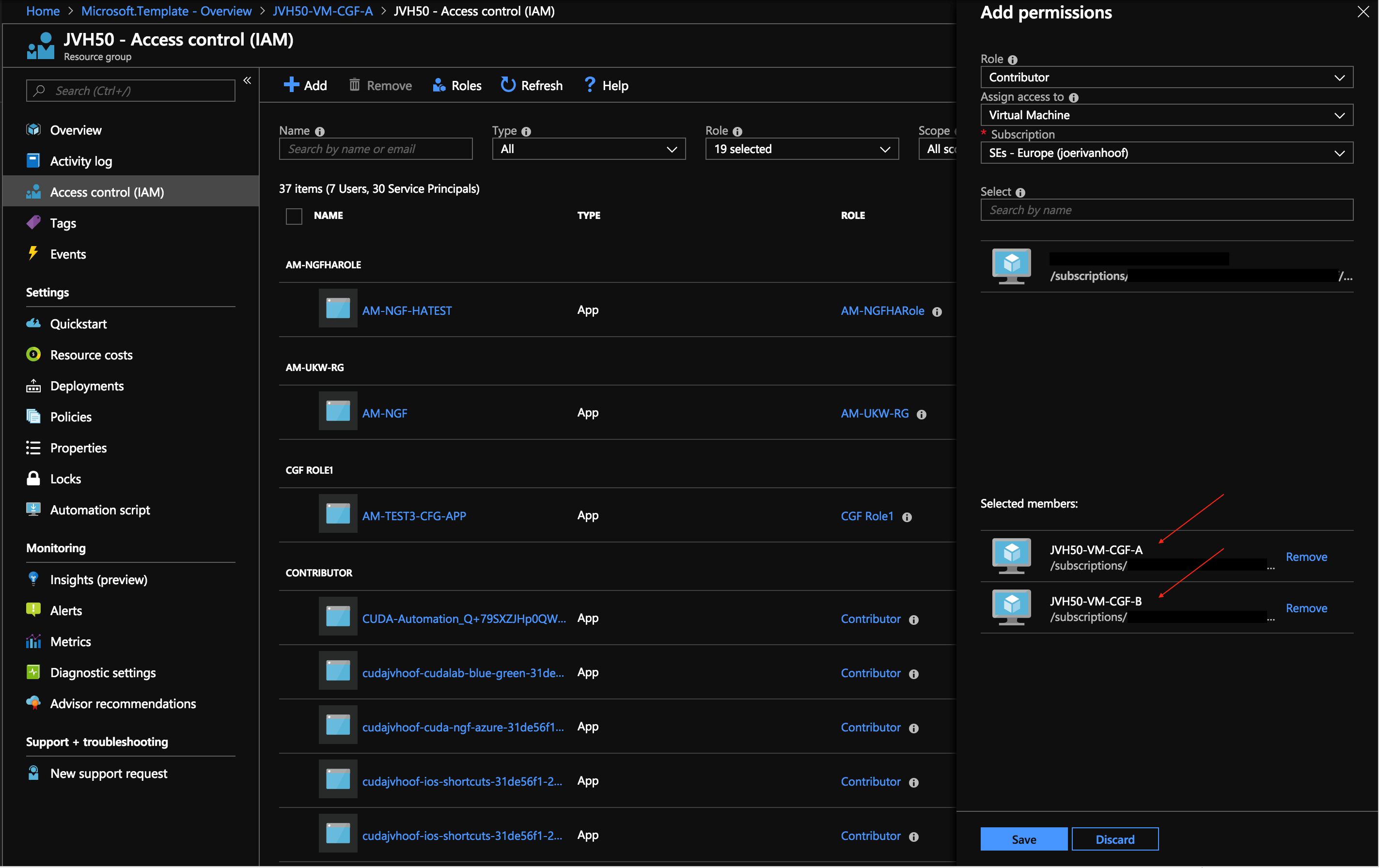
After enabling the managed identity, you need to grant access to the different resources that the Barracuda CloudGen Firewall needs access to.
Both Barracuda CloudGen Firewall VMs need access as a Contributor to the following Azure resources:
- Barracuda CloudGen Firewall virtual machine
- Barracuda CloudGen Firewall network interface
- Routing tables
- VNET
If all of them are in the same resource group, you can enable access to the whole Azure resource group as shown in the picture below.
Cloud Integration
After the permissions are in place on the Azure level, the Barracuda CloudGen Firewall VM has access and can perform the following tasks:
- Retrieve cloud information like location, instance size, instance name, public ip, …
- Retrieve routing tables that are linked to the firewall
- Provide failover and update of the routing table in case of failover in a HA cluster
- Command-line tool to retrieve additional information in scripts: cloud-api
The Barracuda CloudGen Firewall will automatically detect if a managed identity is enabled, and enable cloud integration and fill in known fields: Enable Cloud Integration and Subscription ID (masked in the screenshot with a gray bar).
If the managed identity was not configured during deployment, the Cloud Integration needs to be enabled manually and the Subscription ID needs to be filled in manually.
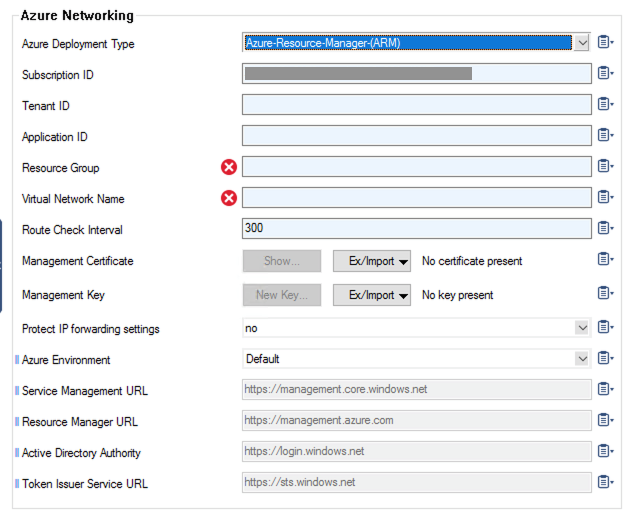
To have all functionalities working, you need to fill in the Resource Group containing the VNET and the VNET containing the Barracuda CloudGen Firewall.
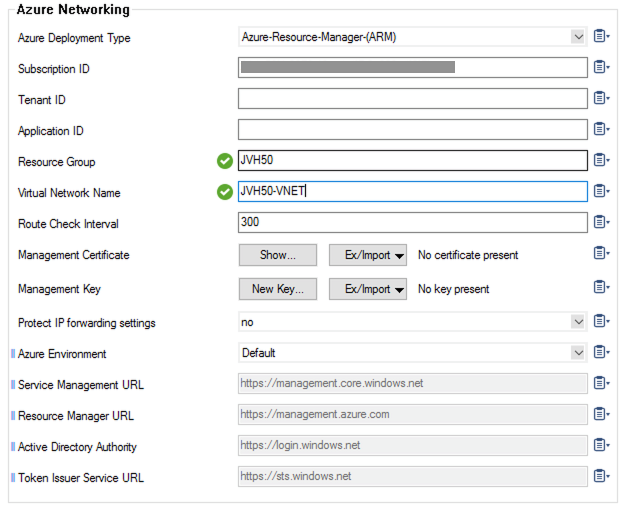
To make sure IP forwarding is always on, which is essential on the Barracuda CloudGen Firewall to operate correctly in Microsoft Azure, you can enable a guard for it as well.
