To allow an on-premises firewall or a firewall not running in AWS to connect to AWS services such as AWS CloudWatch, you must manually configure authentication credentials. For firewalls running in AWS, use IAM roles instead. Cloud integration allows your firewall to exchange information with the underlying cloud platform for things like streaming logs to AWS CloudWatch. The IAM user uses the same IAM policies that are assigned to the AWS IAM role.
Before You Begin
Create the required IAM policies for your firewall. For more information, see How to Create an IAM Role for a CloudGen Firewall in AWS.
Step 1. Create the IAM User
Create the IAM user that is used to connect the firewall instance to the cloud fabric.
- Go to AWS IAM: https://console.aws.amazon.com/iam.
- In the left menu, click Users.
- Click Create user.
- In the User details window, enter the User name.
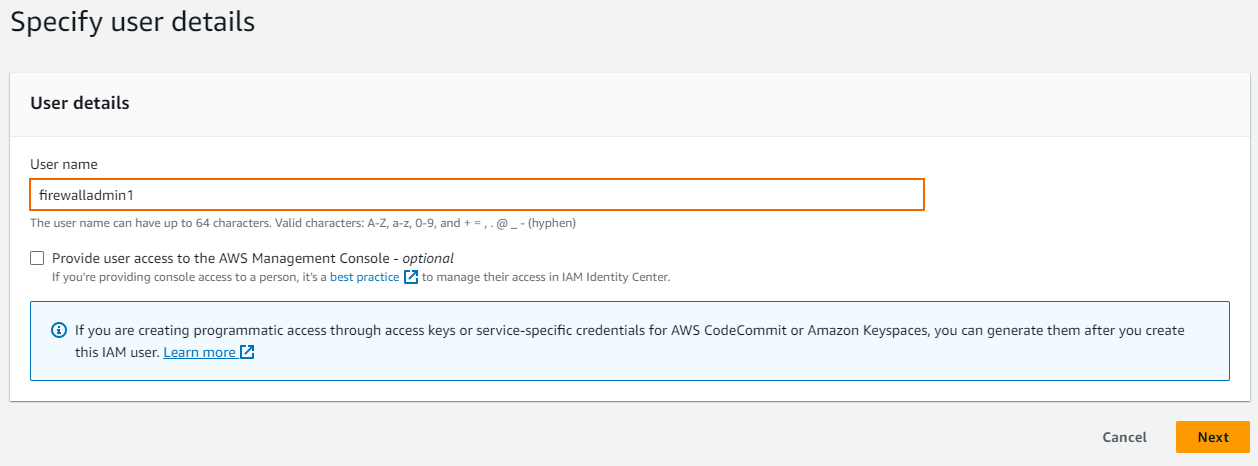
- To allow access to the AWS user interface, select Provide user access to the AWS Management Console. (For SSH access, the user must have Programmatic access enabled.)
- Click Next.
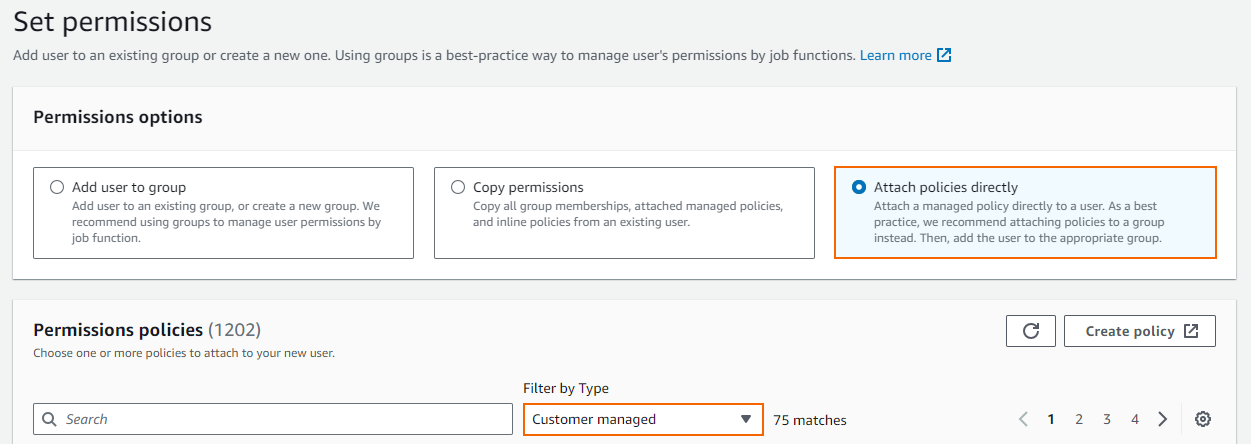
- The Set permissions window opens. Select Attach existing policies directly.
- From the Filter drop-down list, select Customer managed.
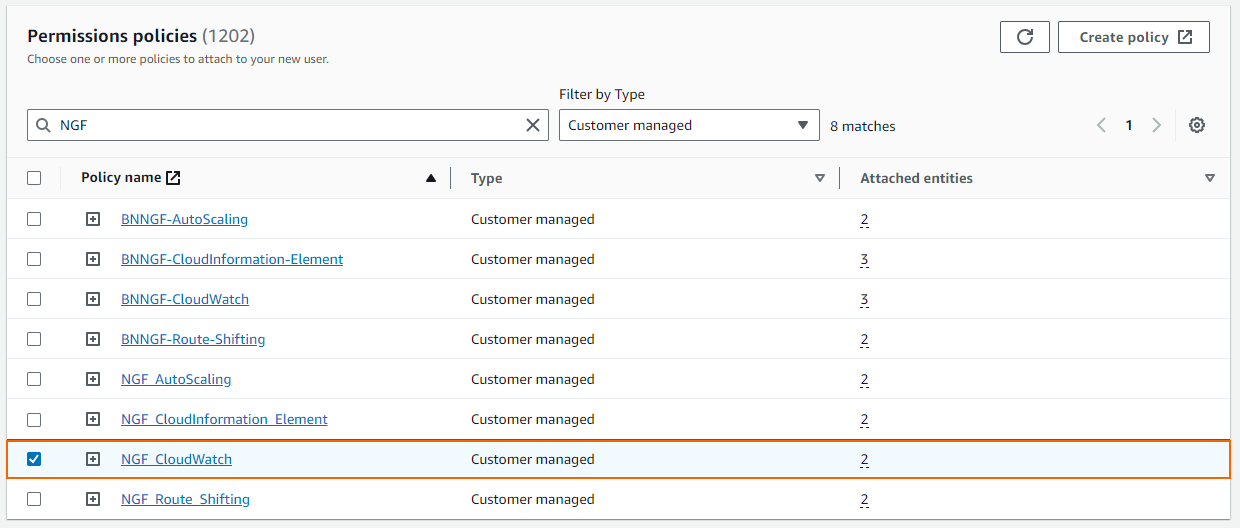
- Select the IAM policies required for the AWS services you need to access. E.g., NGF_CloudWatch to send logs to AWS CloudWatch.
- Click Next.
- Review the settings, and click Create user.
- Download or click Show to write down the user's security credentials (Access key ID and Secret access key). These credentials are required for SSH access.

Step 2. Configure Cloud Integration
Add the access key ID and secret access key to allow the firewall to connect to the AWS cloud fabric.
- Log into the Barracuda CloudGen Firewall instance.
- Go to CONFIGURATION > Configuration Tree > Box > Advanced Configuration > Cloud Integration.
- Click Lock.
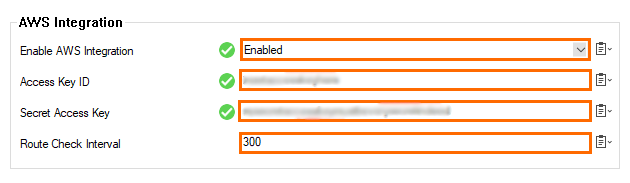
- In the left menu, click AWS Integration.
- From the Enable AWS Integration list, select Enabled.
- Enter the Access Key ID from the IAM user created in Step 1.
- Enter the Secret Access Key from the IAM user created in Step 1.
- Enter a Route Check Interval between 10 and 300 seconds.
- Click Send Changes and Activate.
The firewall instance can now connect to the AWS APIs allowed by the IAM policies.
Next Steps
Configure log streaming to AWS CloudWatch. For more information, see How to Configure Log Streaming to AWS CloudWatch.
