Follow this procedure to create a multi-tenant application. To create a single-tenant application, see Integrating a single-tenant Microsoft Defender application.
The steps to integrate a multi-tenant Microsoft Defender application are the following:
Create a multi-tenant application in Azure
Authorize the MSP Application in each tenant
Integrate the application with Barracuda XDR
See the procedures below.
Step One: Create a multi-tenant application in Azure
The following are instructions for creating a multi-tenant application in Azure.
To create a multi-tenant application in Azure
Log in to Azure with a user that has the Global Administrator role.
Navigate to Azure Active Directory > App registrations > New registration.
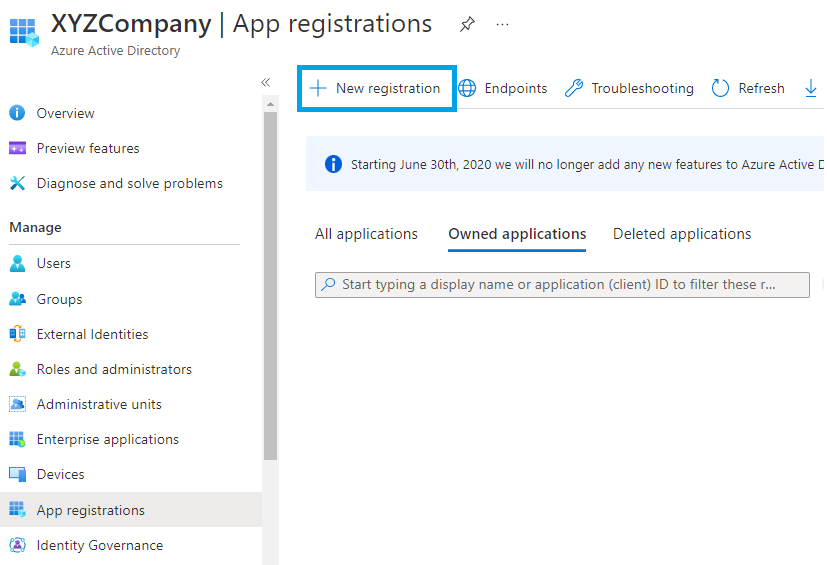
- On the registration form, write a name for your application, and select Multi-tenant.
- In the Redirect URI (optional) section, choose Web and type a redirect URI (https://portal.azure.com).
- Click Register.
- On your application page, click API Permissions.
- Click Add permission.
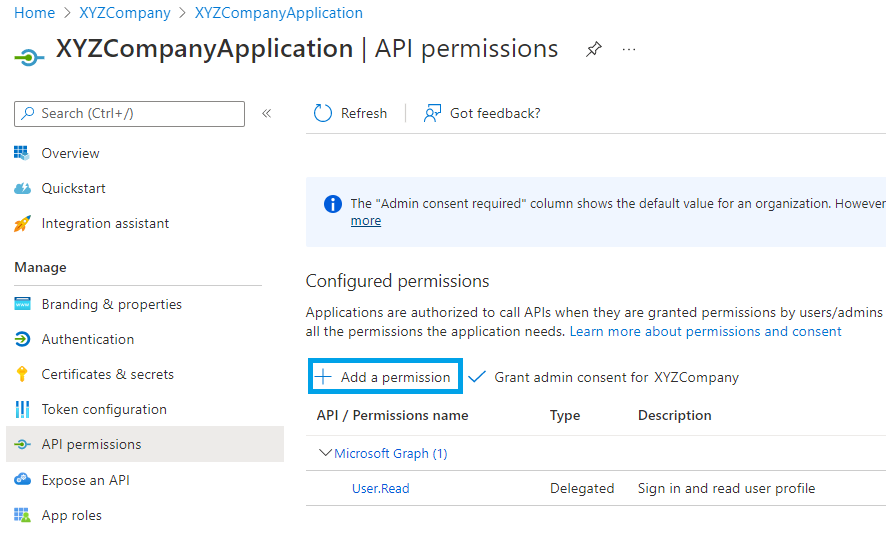
- Click APIs my organization uses. Then type
WindowsDefenderATP.Then select WindowsDefenderATP.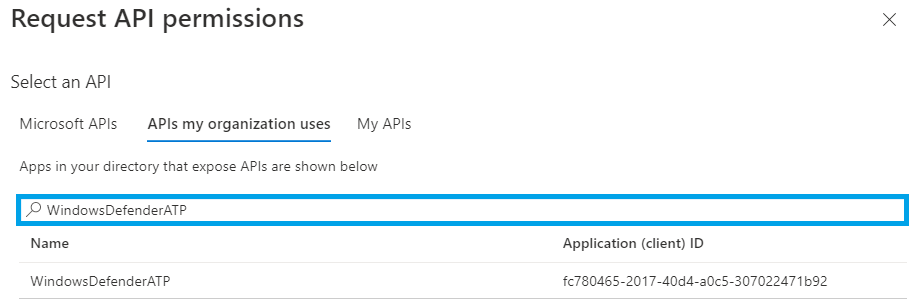
- Click Application permissions. Then click Alert.
- Select Alert.Read.All. Then click Add a permission.
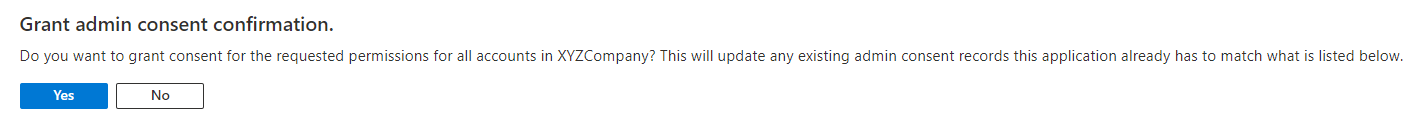
- Select the Application permission and click Grant admin consent.
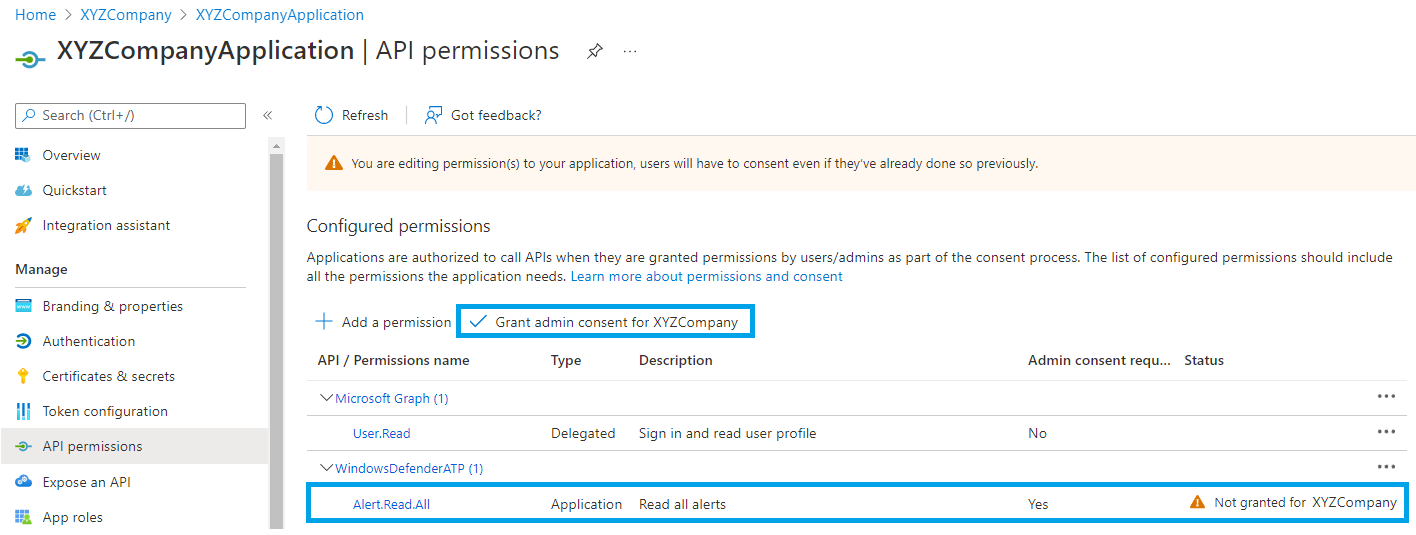
- Click Yes.
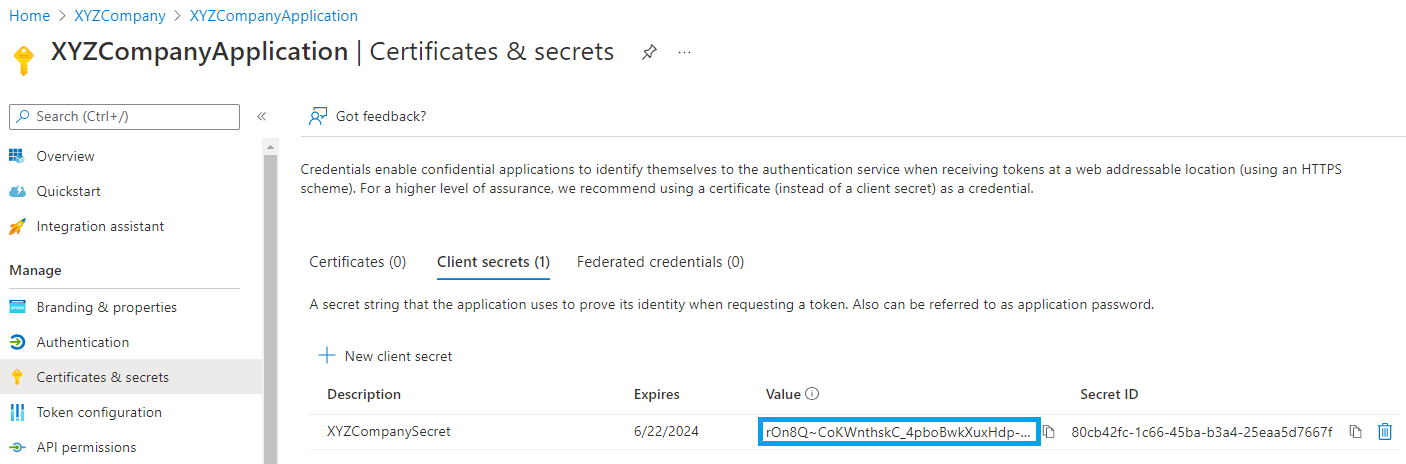
- To add a secret to the application, select Certificates & secrets, add a description to the secret.
- Click Add.

Copy the generated MSP Secret Key value.
- Click Overview.
- Copy the MSP Client ID (Application ID).
Step Two: Authorize the MSP Application in each tenant
Because your application interacts with Defender for Endpoint, the next step is to request that an Admin user each tenant approve the MSP Client ID from the previous procedure.
The Admin user must:
- Be a member of one of the following roles: Application Admin, Cloud Application Admin, or Global Admin.
- Sign in using multi-factor authentication.
- Send an email to each Admin you want to approve the application. The email must contain the following for approval:
https://login.microsoftonline.com/common/oauth2/authorize?prompt=consent&client_id=<00000000-0000-0000-0000-000000000000>&response_type=code&sso_reload=true, where<00000000-0000-0000-0000-000000000000>is the MSP Client ID you copied from the previous procedure. - Each user that authorizes the MSP Client ID, they must log in to Azure AD and retrieve the Tenant ID from the Overview page.
Step Three: Integrate the application with Barracuda XDR
When you've finished the procedure above, complete the integration by entering the Client ID, Secret Key, and Tenant ID in the Barracuda XDR Customer Security Dashboard.
To integrate the application with Barracuda XDR Dashboard
- In the Account list, select the name of the company you created in the previous procedure.
- In Barracuda XDR Dashboard, click to Administration > Integrations.
- In the Microsoft Defender card, click Setup.
- Enter the Client ID, Secret Key, and Tenant ID.
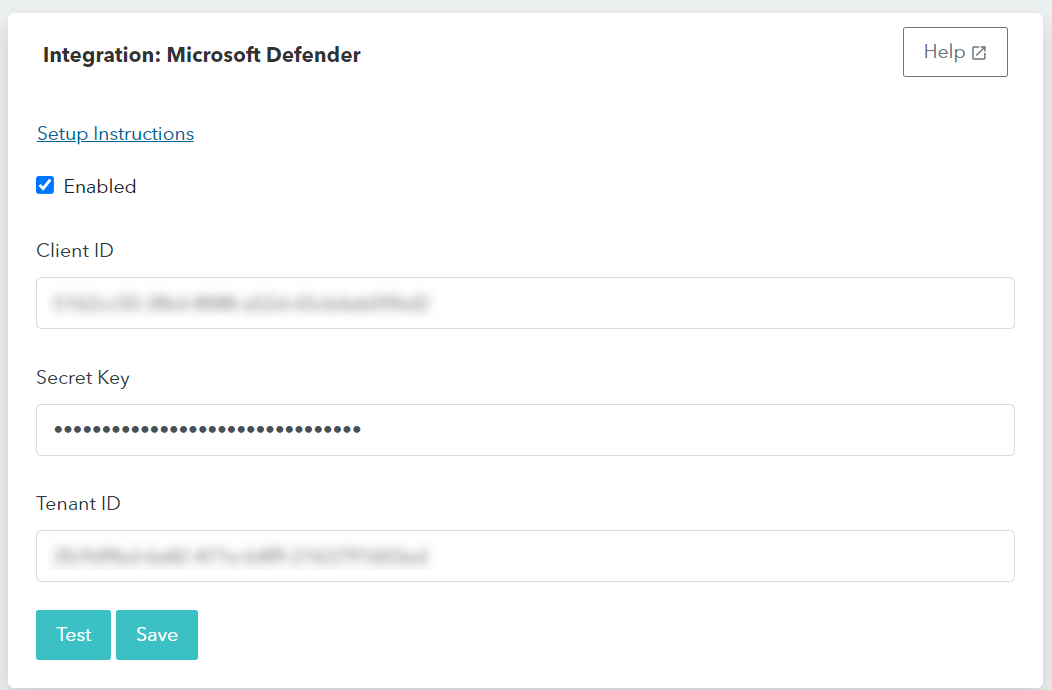
- Click Save.
