Microsoft Entra ID (formerly Azure Active Directory) enables single sign-on/authentication for devices, apps, and services for users located almost anywhere. If you want to synchronize Barracuda Content Shield (BCS) users with your Microsoft Entra ID instead of with your local LDAP/AD, follow the steps in this article. Barracuda supports associating device identities with Microsoft Entra ID using the Microsoft Entra hybrid join method for federated domains.
This article assumes that the Microsoft Entra hybrid join has already been set up and configured. In order for the Barracuda Web Filtering Component (WFC) of the Barracuda Content Shield Suite to identify users and sync relevant policies at the endpoint, Microsoft Entra ID needs to be configured on Barracuda Cloud Control (BCC). To do so, follow these steps:
Step 1. Log into your BCC account using your BCS credentials. Click Add Directory, and then select Azure Active Directory. A pop-up window opens as shown below:
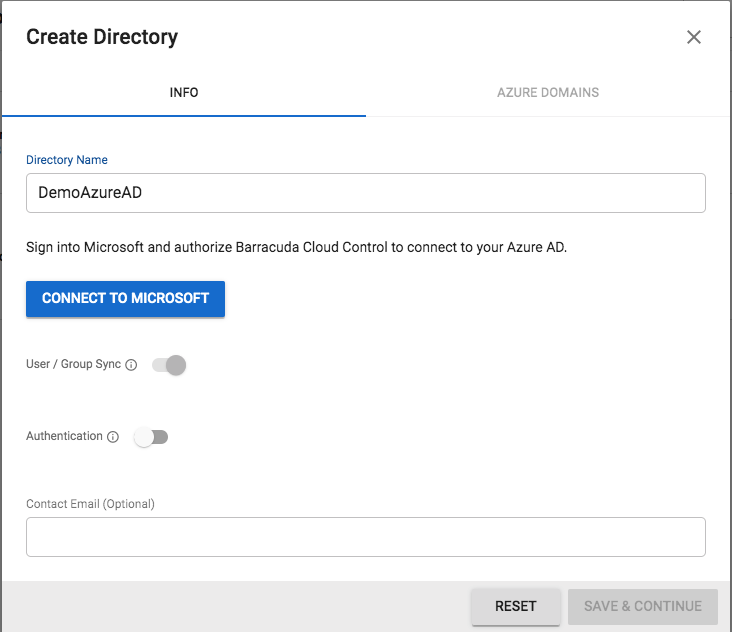
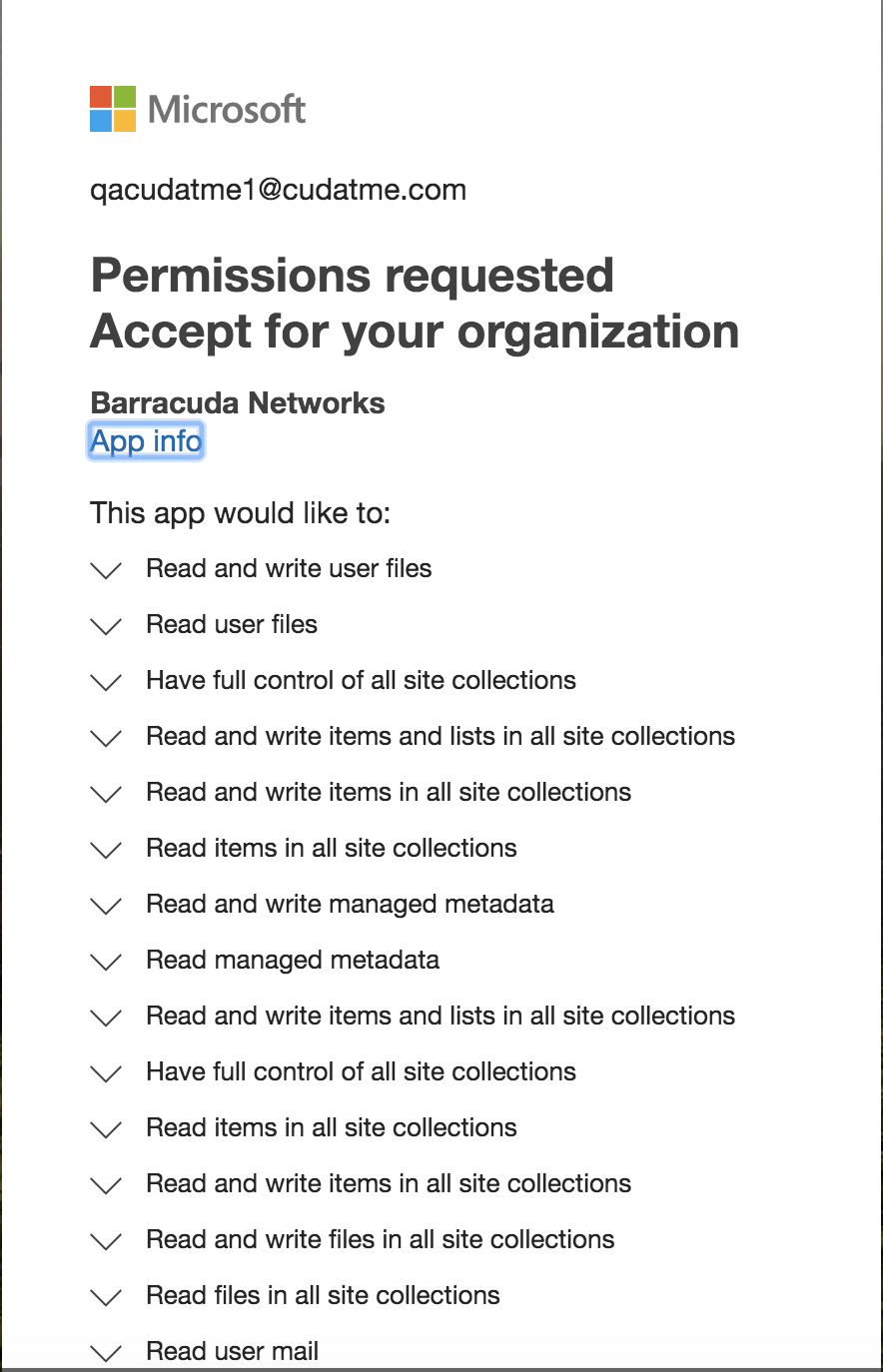
Step 2. Enter the relevant directory name and click Connect to Microsoft . You will be redirected to log in with your Microsoft account. After logging in, you should see the following screen to grant access permissions to Barracuda Networks. Click Accept.
After the Microsoft Entra ID has been added on BCC, it will show up in the Directories section of your BCC account page.
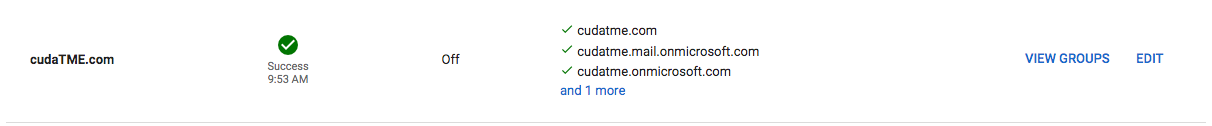
Step 3. After the automatic Sync is completed, you will see a Success message with the time of the last sync. Click VIEW GROUPS to verify if the Groups have synchronized successfully as shown below:
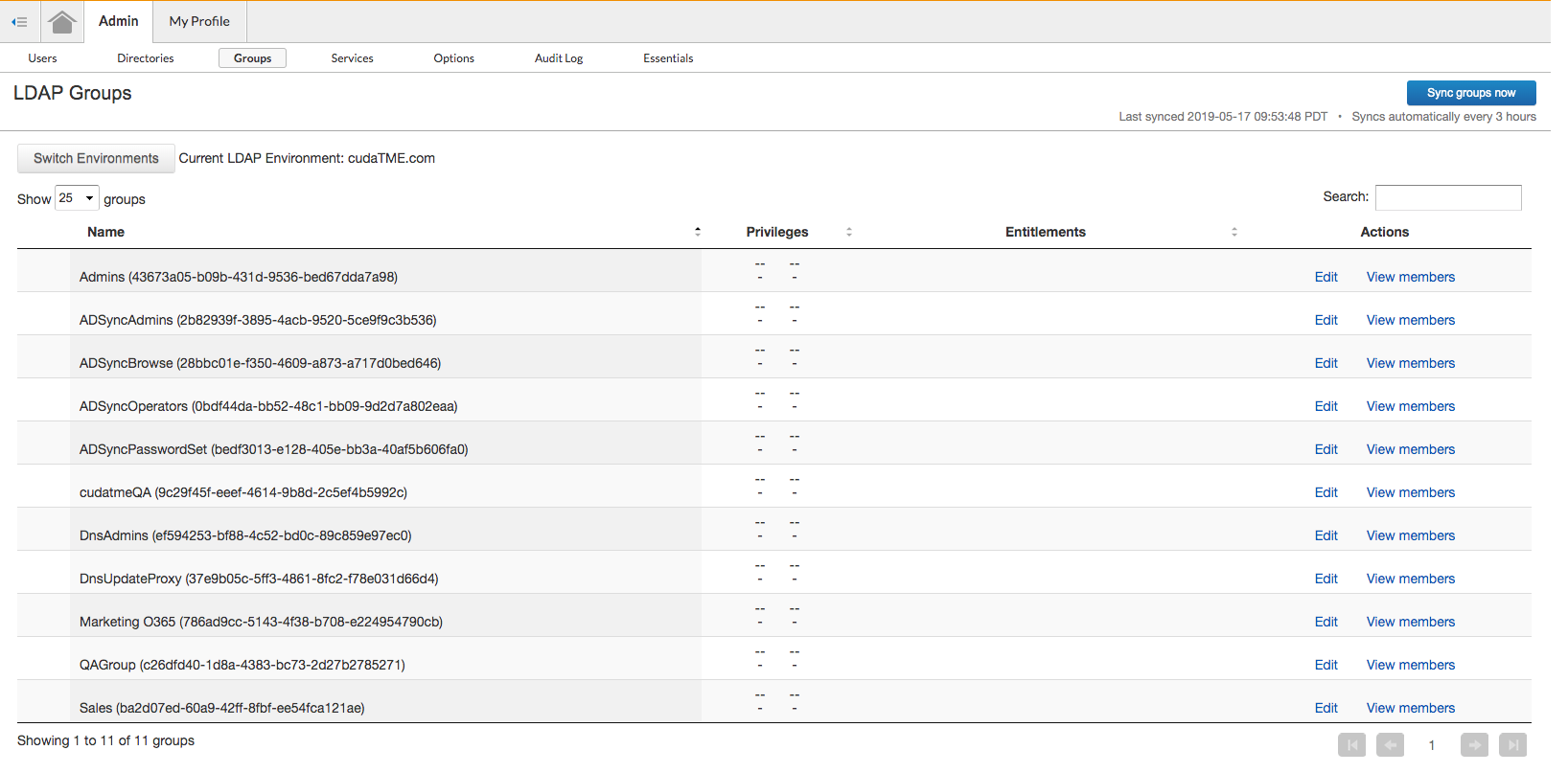
Step 4. Make sure that the Barracuda WFC on the endpoint machine is able to detect Users/Groups and apply relevant policies.
- Log into BCS and go to the USERS page.
- Click Directory Services next to Configure users.
- Log out of BCS.
- Log in as an LDAP user on the client PC, which is joined to the on-premise AD, and verify that user-specific (if configured) policies are applied. You should be able to see the user traffic on the WEB FILTERING LOGS page in the Barracuda Content Shield service.
To finalize the Microsoft Entra hybrid join setup, follow the additional steps described here: https://learn.microsoft.com/en-us/entra/identity/devices/how-to-hybrid-join.
For details on how to set up the Microsoft Entra hybrid join, see Microsoft documentation at https://learn.microsoft.com/en-us/entra/identity/devices/hybrid-join-plan.
