Scaling policies are required for the firewall cluster to adjust the capacity in response to changes in demand. Define CloudWatch alarms for the high and low thresholds. Use the custom metrics collected from the firewall cluster or the default EC2 system metrics. Add scaling policies to the Auto Scaling group that trigger a scaling action when the health check is in alarm state.
Custom Metrics
The firewall published the following custom metrics in the Barracuda/CGF namespace:
Step 1. Create CloudWatch Alarm
Create two CloudWatch alarms, one for the high and one for the low alarm threshold.
- Log into the AWS console.
- Click Services and select CloudWatch.
- In the left menu, expand Alarms and select All alarms.
- Click Create alarm.
- Click Select metric.
- From the Browse Metrics drop-down list, select the Barracuda CloudGen Firewall.
- Filter for the Auto Scaling group name.
- Select the check box for the metric.
- Click Next.
- Enter a Name.
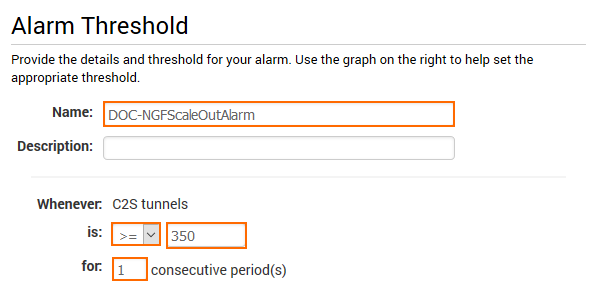
- Configure the Alarm Threshold:
- Logic operator – Select >= when defining an alarm to scale out, <= when defining and alarm to scale in.
- Alarm threshold – Depending on the instance and metric type, enter the threshold. If unsure, use CloudWatch to monitor your cluster under load to determine the correct value to match your workload.
- Period – Enter the time period the threshold must be exceeded for alarm to be triggered.
- In the Alarms section, click delete to not receive a notification when the alarm is triggered. Alternatively, select an SNS topic that is configured to send notification emails when the alarm is triggered.
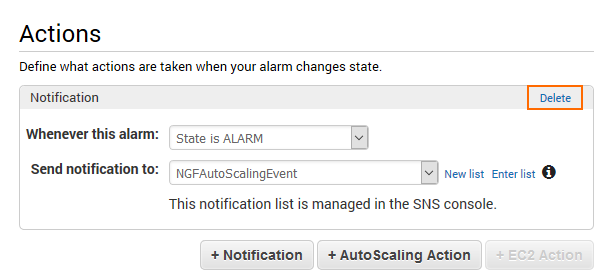
- From the Period drop-down list, select the number of minutes.
- From the Statistics drop-down list, select Average or Sum depending on the metric.
- Click Create Alarm.
The alarm is in the INSUFFICIENT state until there is enough data for the alarm. As soon as enough data is available, the alarm state changes to OK or Alarm.
Step 2. Add Scaling Policy to Scale Out
- Log into the AWS console.
- Click Services and select EC2.
- In the left menu, click Auto Scaling Groups.
- Select the CloudGen Firewall Auto Scaling group.
- In the lower half, click the Scaling Policies tab.
- Click Add policy.
- Enter a Name.
- From the Execute policy when drop-down list, select the matching CloudWatch alarm created in Step 1.
- Configure the action:
- Action – Select add to scale out, or Remove to scale in. Click set to use an explicit number of instances.
- Number of instances – Depending on the action, enter the number of instances to scale (add / remove) or the number of instances to scale to (set).
- (optional) Click add steps to define a more granular scaling policy that takes into account by how much the threshold is exceeded.
- In the Instances need text box, enter the number of seconds to wait before the next scaling action.
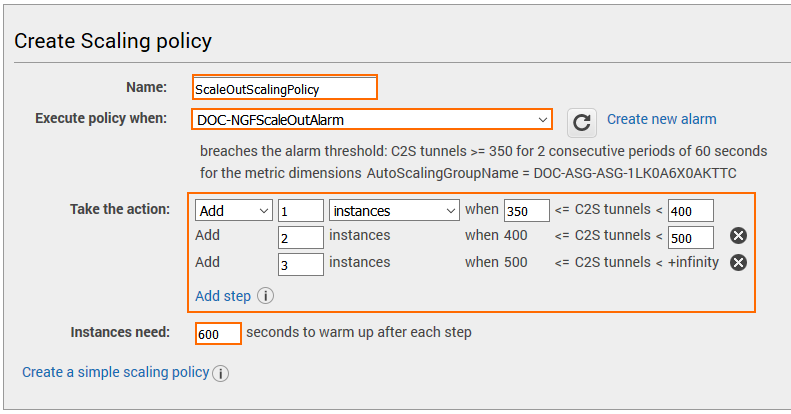
- Click Create.
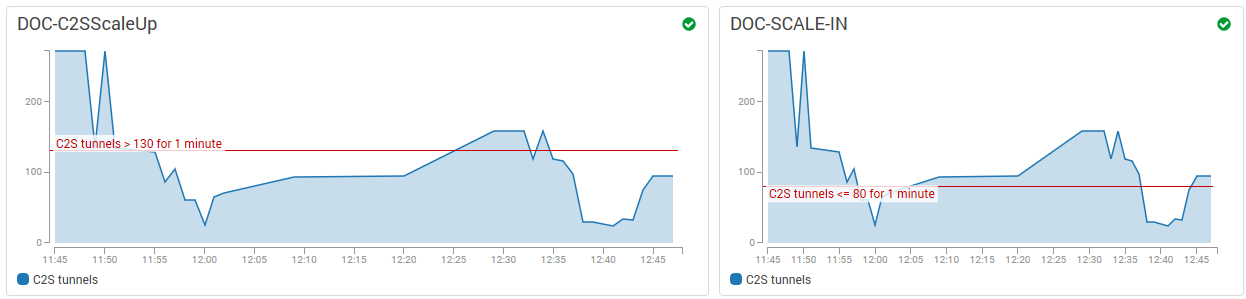
Repeat this for both Scale In and Scale Out policies. Use CloudWatch dashboard widgets to visualize the alarm thresholds