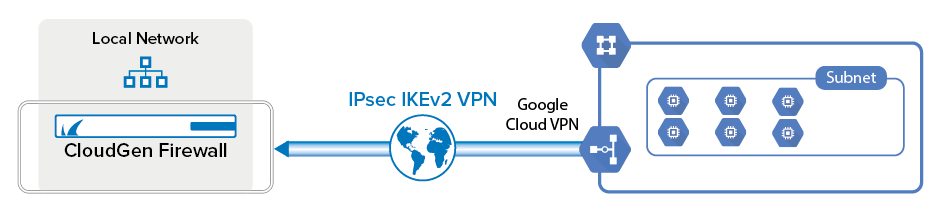
To connect to the Google Cloud VPN gateway, create an IPsec IKEv2 site-to-site VPN tunnel on your CloudGen Firewall and configure BGP to exchange information with the Google BGP peer.
Before You Begin
- You will need the following information:
- Public IP address of your on-premises CloudGen Firewall
- (private) ASN number
- Create a VPC network in Google Cloud.
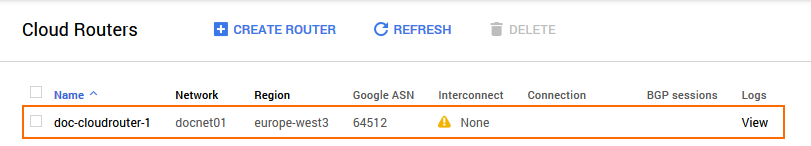
Step 1. Create a Google Cloud Router
- Go to https://console.cloud.google.com.
- Click the hamburger menu in the upper-left corner.
- In the Networking section, click Network Connectivity.
- In the left menu, click + Cloud Routers.
- In the main area, click CREATE ROUTER.
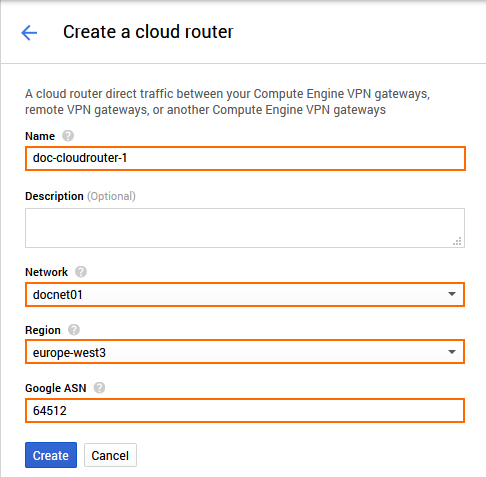
- Configure the settings for the Google Cloud router:
- Name – Enter a name for the cloud router.
- Network – Select the network from the list.
- Region – Select the region from the list.
- Google ASN – Enter a private ASN. This ASN number must be unique in your network.
- Click Create.
Step 2. Create a Google VPN
- Go to https://console.cloud.google.com.
- Click the hamburger menu in the upper-left corner.

- In the Networking section, click Network Connectivity.
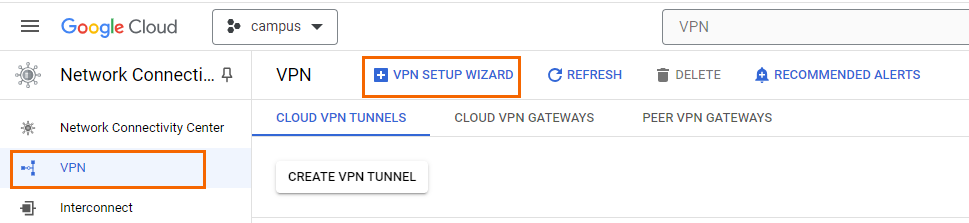
- In the left menu, click VPN.
- In the main area, click + VPN SETUP WIZARD.
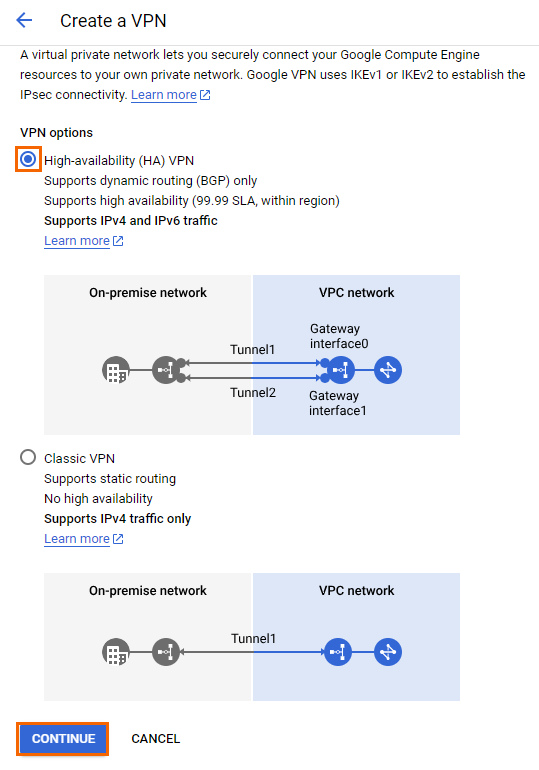
- The Create a VPN page opens. Select High-availability (HA) VPN and click CONTINUE.
- Configure the Create Cloud HA VPN gateway settings:
- VPN gateway name – Enter a name.
- Network – Select your Google Cloud network from the list.
- Region – Select the region for the Google VPN gateway. Select a location close to your on-premises CloudGen Firewall appliance.
- VPN gateway IP version – Select an HA VPN gateway IP version. Note that the IP version of the HA VPN gateway and the peer VPN gateway must be the same.
- VPN gateway IP stack type – Select a stack type for the VPN gateway.
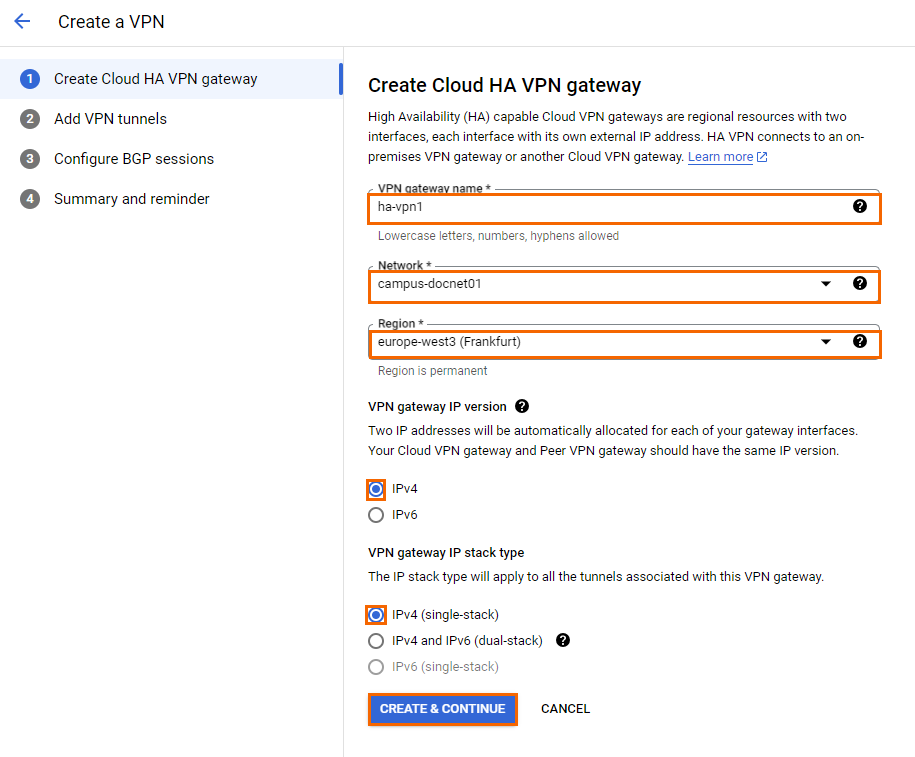
- Click CREATE & CONTINUE.
- You can see that two external IP addresses are automatically allocated for each of your gateway interfaces. Make a note of the details of your gateway configuration for future use.
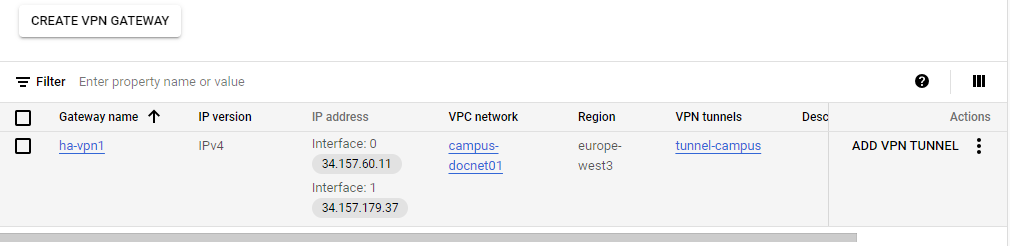
- Configure a VPN tunnel in the Add VPN tunnels settings:
- Peer VPN gateway – Select On-prem or Non Google Cloud.
Peer VPN gateway name – Select an existing peer VPN gateway from the drop-down menu or click Create a new peer VPN gateway.
- High Availability – Select Create a single VPN tunnel. Note: A single tunnel does not provide high availability. However, you can add more tunnels later when needed.
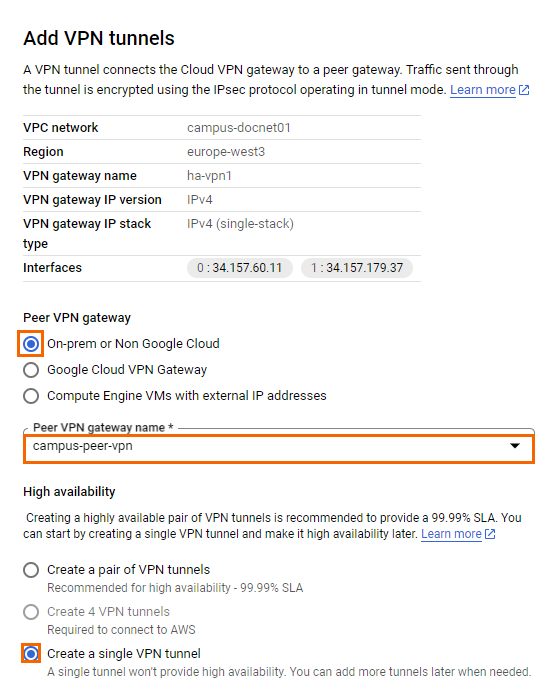
- Verify that the Routing Options display as Dynamic (BGP).
- Cloud router – Select the cloud router created in Step 1.
- Name – Enter the name.
- IKE version – Select IKEv2
IKE pre-shared key – Enter either a passphrase as the shared secret, or click GENERATE AND COPY. Note: Make sure you record the pre-shared key in a secure location.
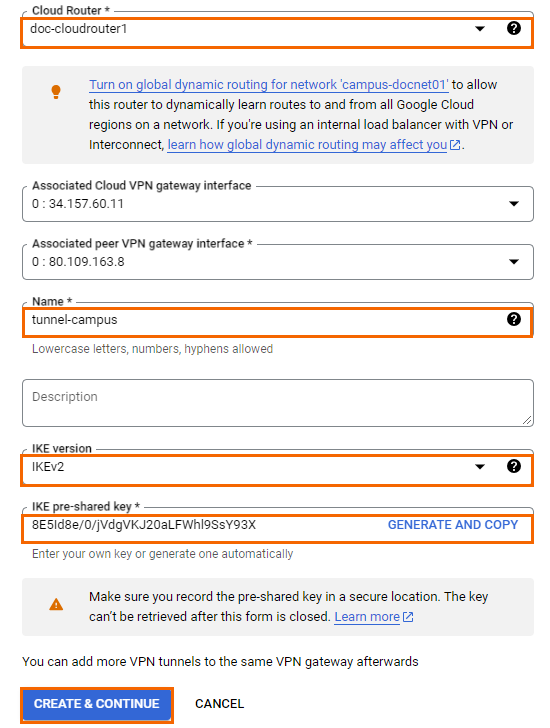
- Click CREATE & CONTINUE.
- The Configure BGP sessions page opens.
- Click CONFIGURE BGP SESSION FOR <TUNNEL-CAMPUS> to configure BGP session.
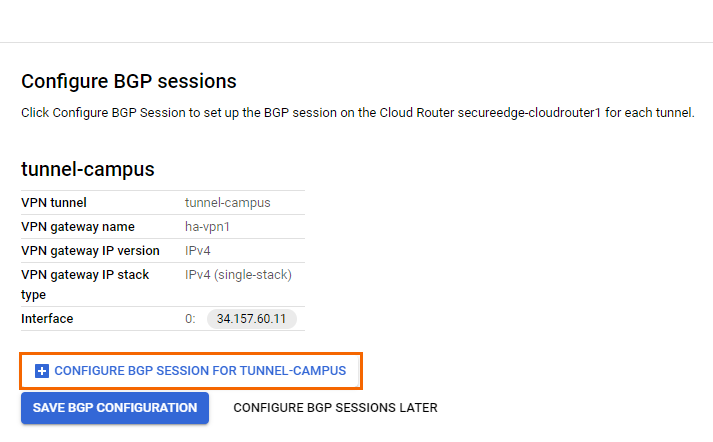
- The Create BGP session page opens. Configure the BGP session for the cloud router:
- BGP session type – Select IPv4 BGP session.
Name – Enter a name for the BGP configuration.
Peer ASN – Enter the ASN assigned to the on-premises CloudGen Firewall appliance.
(optional) Advertised route priority – Enter a priority value. Routes with higher priorities are preferred.
Allocate BGP IPv4 address – Select Manually.
- Cloud Router BGP IPv4 address – Enter the first IP address in a private /30 subnet. The IP address must be in the same /30 network as the peer BGP IP address: E.g.,
169.254.1.1 - Peer BGP IPv4 address – Enter the second IP address in the private /30 subnet used for the Google BGP IP address. E.g.,
169.254.1.2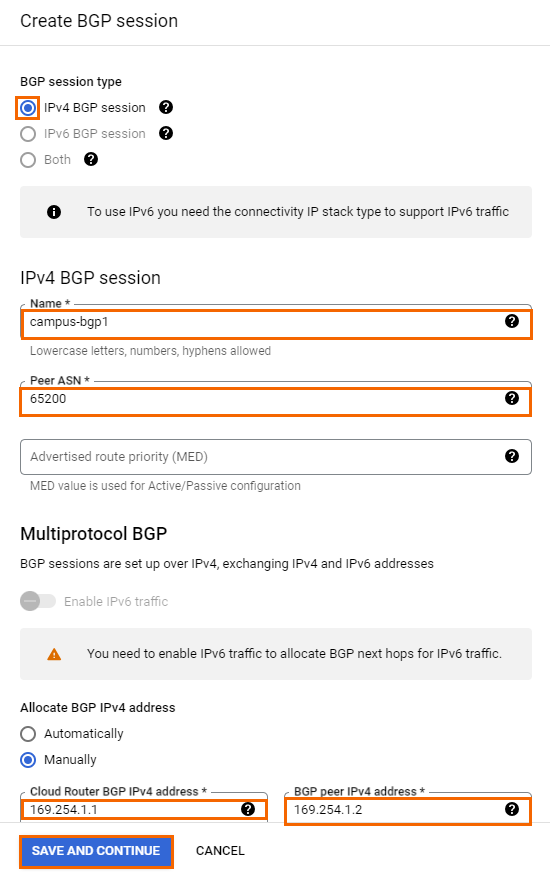
- Cloud Router BGP IPv4 address – Enter the first IP address in a private /30 subnet. The IP address must be in the same /30 network as the peer BGP IP address: E.g.,
- Click SAVE AND CONTINUE.
- Verify the BGP session you have configured and click SAVE BGP CONFIGURATION.
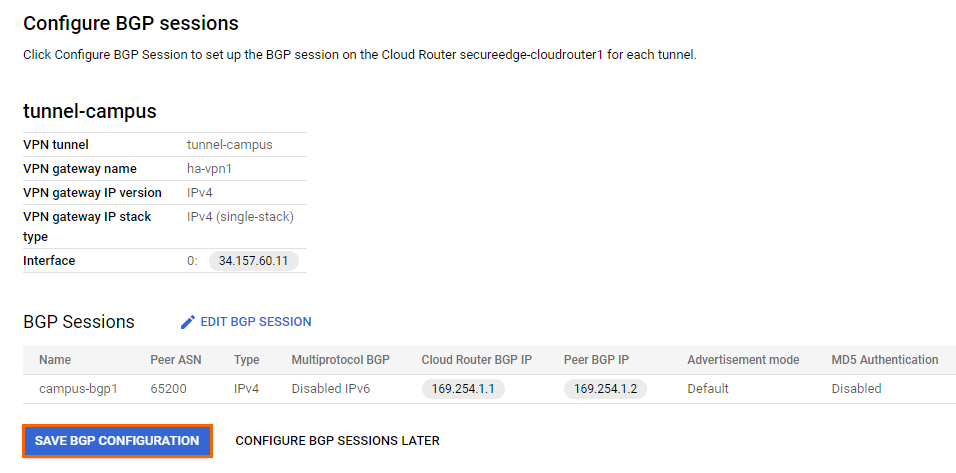
- The Summary and reminder page opens.
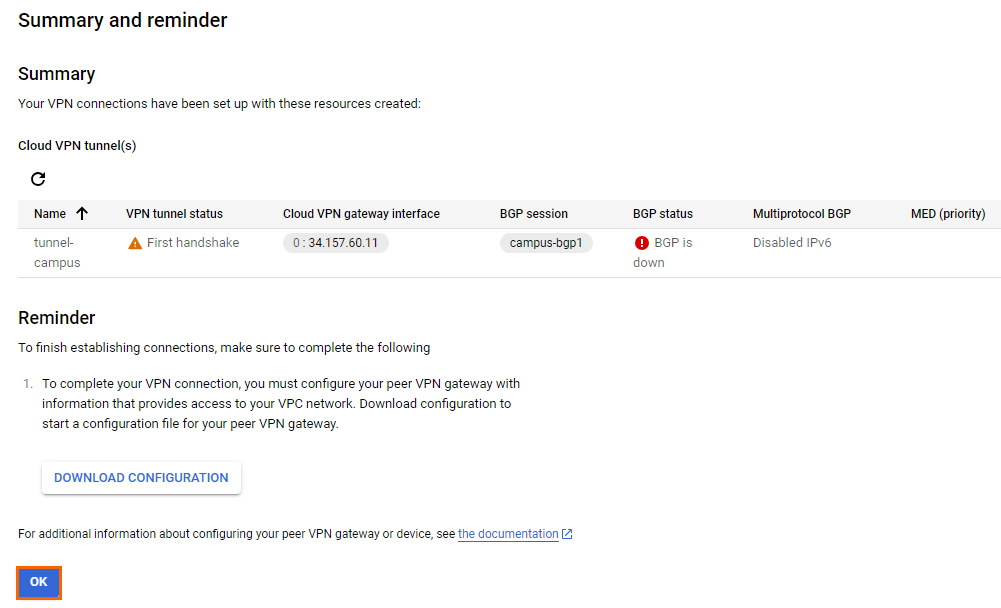
- Click OK.
Step 3. Create VPN Next Hop Interfaces
- Log into the Barracuda CloudGen Firewall.
- Go to CONFIGURATION > Configuration Tree > Box > Assigned Services > VPN > VPN Settings.
- Click Lock.
- In the left navigation bar, click Routed VPN.
- Click Add in the VPN Next Hop Interface Configuration section.
- VPN Interface Index – Enter a number between 0 and 99. Each interface index number must be unique.
- MTU – Enter
1398. - IP Addresses – Enter the Peer BGP IP address from Step 2 with a /30 subnet mask. E.g.,
169.254.1.2/30
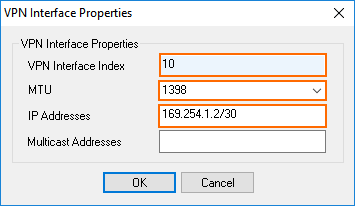
- Click OK.
- Click Send Changes and Activate.
Step 4. Configure a IPsec IKEv2 Site-to-Site VPN on the Firewall
Configure a site-to-site IKEv2 VPN tunnel on the firewall. The firewall is configured as the active VPN endpoint.
- Go to CONFIGURATION > Configuration Tree > Box > Assigned Services > VPN-Service > Site to Site .
- Click the IPsec IKEv2 Tunnels tab.
- Click Lock.
- Right-click the table and select New IKEv2 tunnel. The IKEv2 Tunnel window opens.
- In the IKEv2 Tunnel Name field, enter your tunnel name.
- Set Initiates Tunnel to Yes.
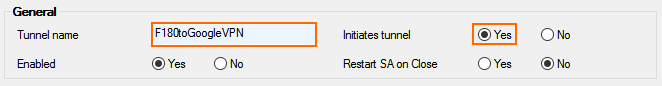
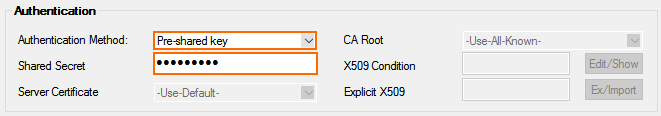
- Configure the Authentication settings:
- Authentication Method – Select Pre-shared key.
- Shared Secret – Enter the passphrase you used to create the Google VPN.
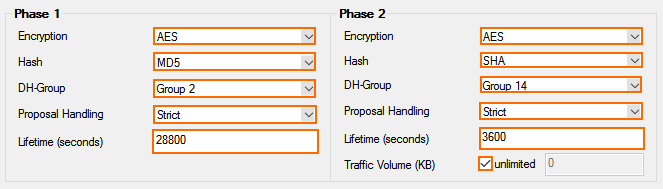
- Configure the Phase 1 encryption settings:
- Encryption – Select AES.
- Hash Meth. – Select MD5.
- DH Group – Select Group 2.
- Proposal Handling – Select Strict.
- Lifetime – Enter
28800.
- Configure the Phase 2 encryption settings:
- Encryption – Select AES.
- Hash Meth. – Select SHA.
- DH Group – Select Group 14.
- Proposal Handling – Select Strict.
- Lifetime (seconds) – Enter
3600 - LIfetime (KB) – Select unlimited.
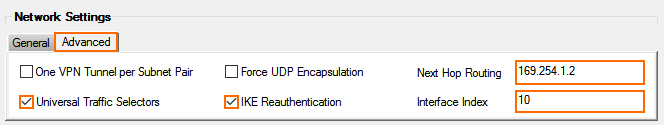
- In the Network Settings section, click the Advanced tab:
- One VPN Tunnel per Subnet Pair – Clear the check box.
- Universal Traffic Selectors – Select the check box.
- Force UDP Encapsulation – Clear the check box.
- IKE Reauthentication – Select the check box.
- Next Hop Routing – Enter the Peer BGP IP address address from Step 2.
- Interface Index – Enter the index of the VPN next hop interface created in Step 3.
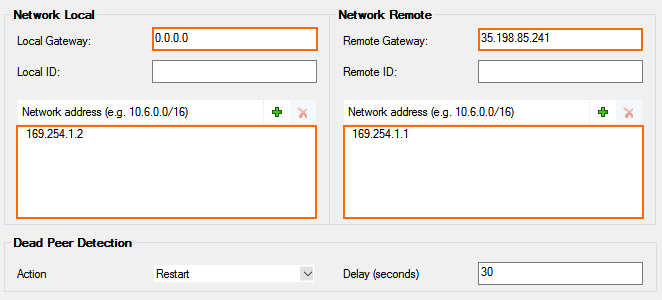
- Configure the Local Network settings:
- Local Gateway – Enter the public IP address of the firewall, or use 0.0.0.0 if you are using a dynamic IP address.
- Network Address – Click + and enter the Peer BGP IP address from Step 2.
- Configure the Remote Network settings:
- Remote Gateway – Enter the gateway IP address of the Google Cloud VPN.
- Network Address – Click + and enter the Google VPN IP address.
- Click OK.
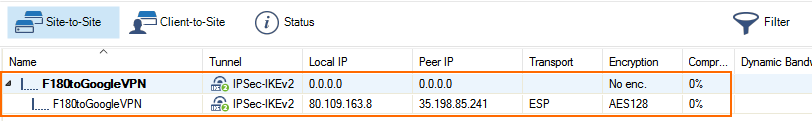
Click Send Changes and Activate.
The VPN tunnel to the Google VPN gateway is now established.
Step 5. Configure the BGP Service
Configure BGP routing to learn the subnets from the remote BGP peer behind the Google VPN on the other side of the VPN tunnels.
Step 5.1. Configure Routes to be Advertised via BGP
Only routes with the parameter Advertise set to yes will be propagated via BGP.
- Go to CONFIGURATION > Configuration Tree > Box > Network .
- Click Lock.
- (optional) To propagate the management network, switch to Advanced view and set Advertise Route to yes.
- In the left menu, click Routing.
- Edit the Routes you want to propagate, and set Advertise Route to yes.
- Click OK.
- Click Send Changes and Activate.
Step 5.2. Enable BGP
Configure the BGP setting for the BGP service on the firewall.
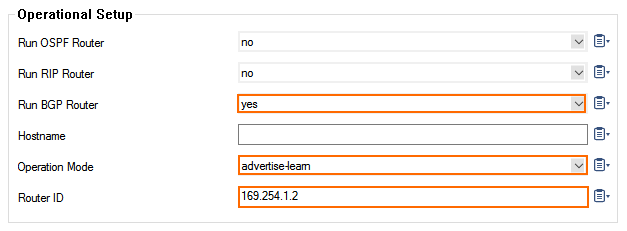
- Go to CONFIGURATION > Configuration Tree > Box > Assigned Services > OSPF-RIP-BGP-Service > OSPF/RIP/BGP Settings .
- From the Run BGP Router list, Select yes.
- From the Operations Mode list, select advertise-learn.
- Enter the local BGP peering IP address as the Router ID.
- In the left menu, click BGP Router Setup.
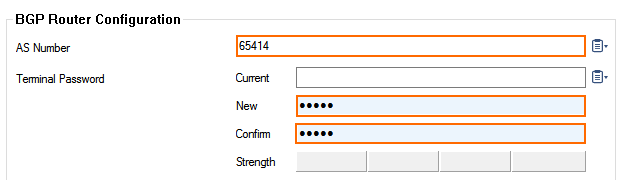
- Enter the AS Number for the local BGP peer as per Step 2. E.g.,
65200 - Enter the Terminal Password.
- In the left menu, expand Configuration Mode and click Switch to Advanced Mode.
- Click the Set button for the Advanced Settings. The Advanced Settings window opens.
- Set the Hold timer to
30seconds. - Set the Keep Alive Timer to
10seconds. - Click OK.
- Click Send Changes and Activate.
Step 5.3. Add a BGP Neighbor for the Google VPN
To dynamically learn the routing of the neighboring network, set up a BGP neighbor for the Google VPN.
- In the left menu of the OSPF/RIP/BGP Settings page, click Neighbor Setup IPv4.
- Click Lock.
- In the left menu, expand Configuration Mode and click Switch to Advanced Mode.
- Click + to add an entry to the Neighbors table. The Neighbors window opens.
- Enter a Name and click OK.
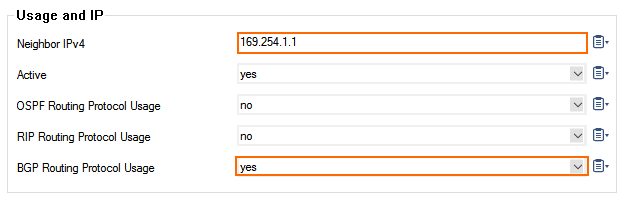
- In the Neighbors window, configure the following settings in the Usage and IP section:
- Neighbor IPv4 – Enter the remote BGP peer IP address.
- OSPF Routing Protocol Usage – Select no.
- RIP Routing Protocol Usage – Select no.
- BGP Routing Protocol Usage – Select yes.
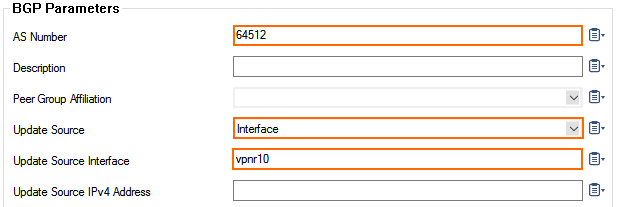
- In the BGP Parameters section, configure the following settings:
- AS Number: Enter the ASN for the remote network as per the information from Step 2. E.g.,
64512 - Update Source: Select Interface.
- Update Source Interface: Enter the vpnr interface. E.g.,
vpnr10
- AS Number: Enter the ASN for the remote network as per the information from Step 2. E.g.,
- Click OK.
- Click Send Changes and Activate
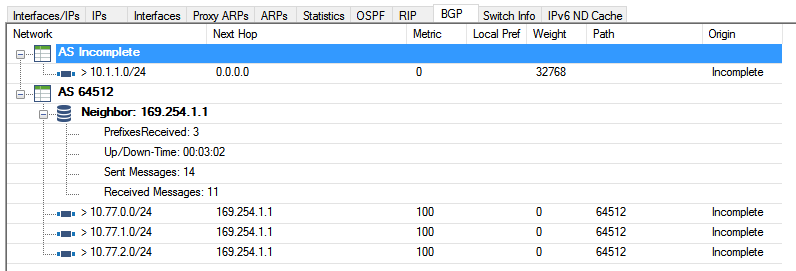
Go to CONTROL > Network > BGP. The firewall is now learning and advertising networks to the Google VPN BGP peer.
Step 6. Create an Access Rule
Create a pass access rule to allow traffic from the local networks to the networks learned via BGP.
- Go to CONFIGURATION > Configuration Tree > Box > Assigned Services > Firewall > Firewall Rules.
- Click Lock.
- Create a PASS access rule:
- Bi-Directional – Enable.
- Source – Select the local on-premises network(s) advertised via BGP.
- Service – Select the service you want to have access to the remote network, or select Any for complete access.
- Destination – Select the network object containing the learned networks.
- Connection Method – Select Original Source IP.
- Click OK.
- Move the access rule up in the rule list, so that it is the first rule to match the firewall traffic.
- Click Send Changes and Activate.
