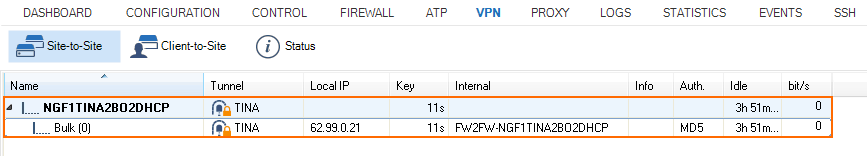
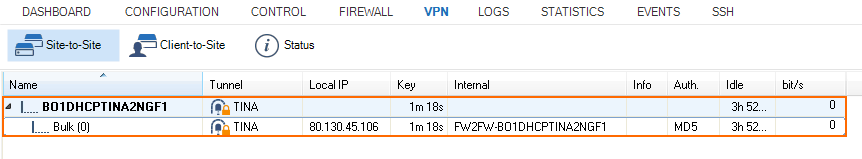
In this example setup, two CloudGen Firewalls are connected via a TINA site-to-site VPN tunnel over the Internet. The firewall on the local site is using a WAN connection with a static public IP address. The remote firewall uses a dynamic WAN connection. Since the dynamic IP address of the remote firewall is volatile and can change, the remote firewall must be configured as the active VPN endpoint of the VPN tunnel.
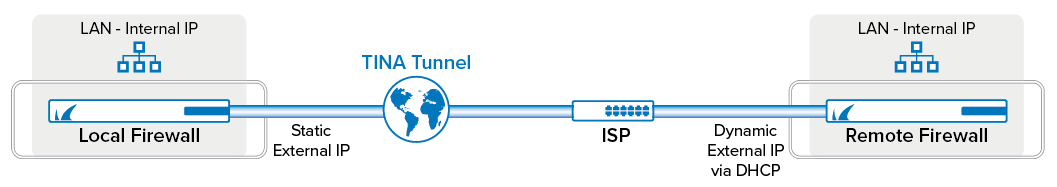
The following table refers to the image and serves as an example. You must adjust the settings to your specific network and host IP values.
| Local Firewall | Remote Firewall | |
|---|---|---|
| External IP address | 62.99.0.21/32 (static) | Dynamic via DHCP |
| Local Networks | 10.0.10.0/25 | 10.0.80.0/24 |
| Remote Networks | 10.0.80.0/24 | 10.0.10.0./25 |
| State of Tunnel Server | Passive | Active |
Step 1. Configure the TINA Site-to-Site VPN Tunnel on the Local Firewall
Traffic coming from the internal network 10.0.80.0/24 behind the remote firewall is forwarded through the TINA site-to-site VPN tunnel to the internal network 10.0.10.0/25 behind the local firewall. Since the public IP address of the remote firewall is dynamic, the Call Direction of the local firewall must be set to Passive.
- Log into the local firewall.
- Go to CONFIGURATION > Configuration Tree > Box > Assigned Services > VPN > Site to Site.
- Click Lock.
- Click the TINA Tunnels tab.
- Right-click the table and select Add new TINA Tunnel. Alternatively, you can click the + sign in the top-right corner of the window.
- Select Add Tunnel.
- In the Tunnel Name field, enter a name for the new VPN tunnel.
- Select a configured Scheme for the local network (optional), or select explicit. To configure a scheme, click the Local Networks tab and create a New Local Network. Then, enter a Name and add the network address.
- In the Local section, enter the Network Address(es) of your local network(s) in CIDR-notation and click Add. (i.e.
10.0.10.0./25) - In the Remote section, enter the local network address(es) of the remote peer in CIDR-notation and click Add. (i.e.
10.0.80.0/24)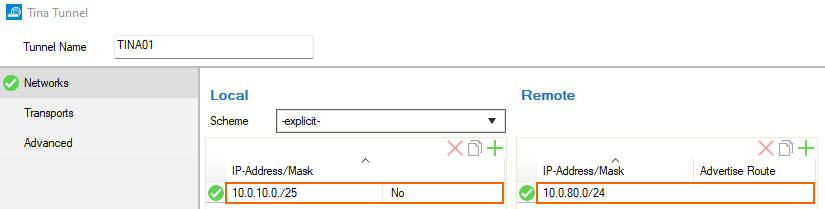
- In the left menu, click Transports.
- Click + to add a new transport for the VPN tunnel. The Edit Transport window opens, showing the Basic tab.
Set the Call Direction to Passive so that the local firewall listens for incoming VPN tunnel requests.
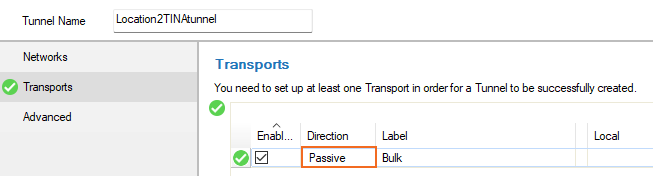
Configure the Basic transport settings. For more information, see TINA Tunnel Settings.
- (optional) Provider – If providers have been configured by a name in CONFIGURATION > Configuration Tree > Network > IP Configuration > Shared Networks and IPs, select a provider for the transport source and SD-WAN classification.ult.
- Transport – Select the transport encapsulation (recommended: UDP).
- Encryption – Select the data encryption algorithm.
- Authentication – Select the hashing algorithm for packet authentication.
In the left menu, click Peers.
Select a configured Template for the transport source, or select explicit and choose the IP address(es) or interface(s) that should be used to establish the VPN connection from the Transport Source list (To configure a template, click the Parameter Templates tab and create a New Tunnel Parameter Template. Then, enter a Name and add the tunnel address.):
- First Server IP – The connection gets established from the first shared IP address.
- Second-IP – The connection gets established from the second shared IP address.
- Dynamic (via routing) – The firewall uses a routing table lookup to determine the IP address.
- Explicit List – Enter one or more explicit IP addresses. Multiple IP addresses are tried in the listed order. Click + and add the IP address(es) or interface(s) used as tunnel address.
- In the Remote section, enter
0.0.0.0/0for tunnel requests coming from the second firewall via the Internet.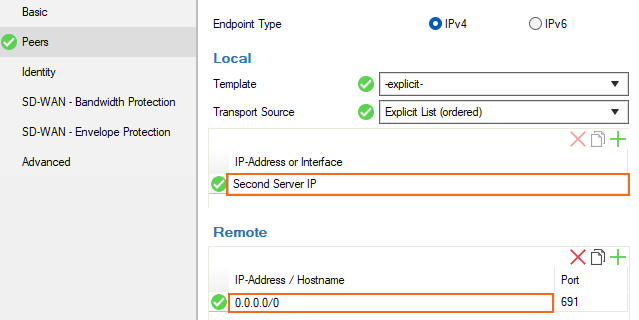
Configure SD-WAN and Advanced transport settings to match the settings configured for the local firewall. For more information, see the lower section in TINA Tunnel Settings.
- Click OK. The TINA Tunnel configuration window opens.
- Configure the Advanced tunnel settings to match the settings configured for the local firewall. For more information, see the lower section in TINA Tunnel Settings.
- Click OK.
- Click Send Changes and Activate.
Step 2. Configure the TINA Site-to-Site VPN Tunnel on the Remote CloudGen Firewall
Since the local firewall's tunnel is working in passive mode, only the remote firewall can initiate a tunnel connection. Therefore, the Call Direction must be set to Active.
- Go to CONFIGURATION > Configuration Tree > Box > your remote firewall > Assigned Services > VPN > Site to Site.
- Click Lock.
- Click the TINA Tunnels tab.
- Right-click the table and select Add new TINA Tunnel. Alternatively, you can click the + sign in the top-right corner of the window.
- Select Add Tunnel.
- In the Tunnel Name field, enter a name for the new VPN tunnel.
- Select a configured Scheme for the local network, or select explicit.
- In the Local section, enter the Network Address(es) of your local network(s) in CIDR-notation. (i.e.,
10.0.80.0./24) - n the Remote section, enter the local network address(es) of the remote peer in CIDR-notation. (i.e.,
10.0.10.0/25)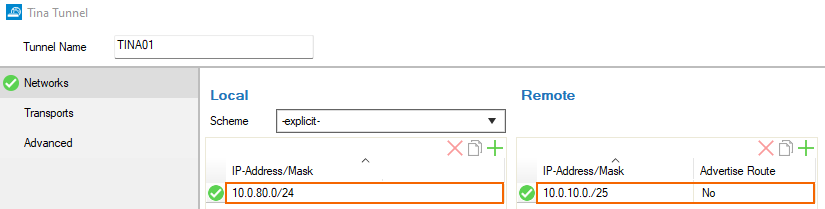
- In the left menu, click Transports.
- Click + to add a new transport for the VPN tunnel. The Edit Transport window opens, showing the Basic tab.
Set the Call Direction to Active so that the firewall can initiate a VPN tunnel after being connected to the Internet via DHCP.
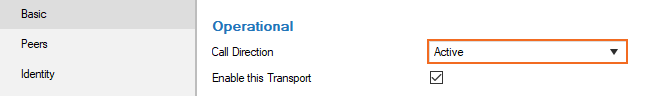
Configure the Basic transport settings. For more information, see TINA Tunnel Settings.
- (optional) Provider – If providers have been configured by a name in CONFIGURATION > Configuration Tree > Network > IP Configuration > Shared Networks and IPs, select a provider for the transport source and SD-WAN classification.ult.
- Transport – Select the transport encapsulation (recommended: UDP).
- Encryption – Select the data encryption algorithm.
- Authentication – Select the hashing algorithm for packet authentication.
In the left menu, click Peers.
- For the Transport Source, select Dynamic (via routing). The firewall must do a routing table lookup to determine the IP address.
- In the Remote section, enter the point of entry of the first firewall. (i.e.,
62.99.0.21) Configure SD-WAN and Advanced transport settings to match the settings configured for the local firewall. For more information, see the lower section in TINA Tunnel Settings.
- Click OK. The TINA Tunnel configuration window opens.
- Configure the Advanced tunnel settings to match the settings configured for the local firewall. For more information, see the lower section in TINA Tunnel Settings.
- Click OK.
- Click Send Changes and Activate.
Exchange the Public Keys Between the Local and Remote Firewall
Start with exporting the public key in the displayed window on the remote firewall.
- Go to CONFIGURATION > Configuration Tree > Box > your remote firewall > Assigned Services > VPN > Site to Site.
- Edit the transport for the TINA tunnel.
- In the left menu, click Identity.
- From the Identification Type list, select Public Key.
- In the Local section, click the cog wheel icon next to Server Protocol Key, and export the public key to clipboard.
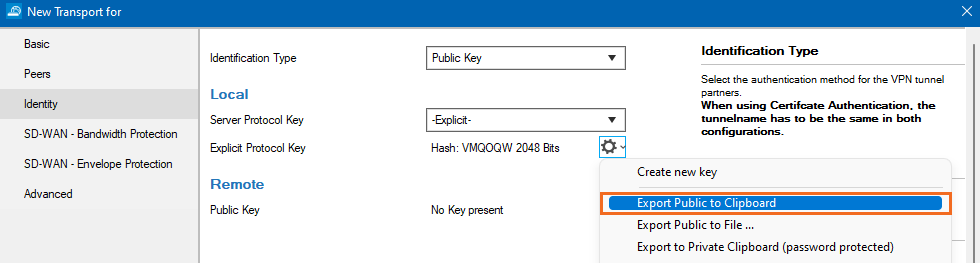
Click OK and close the TINA Tunnel configuration.
- Go to CONFIGURATION > Configuration Tree > Box > your local firewall > Assigned Services > VPN > Site to Site.
- Click Lock.
- Select TINA Tunnels.
- Open the configuration for the site-to-site tunnel transport created in Step 1.
- In the left menu, click Identity.
- In the Remote section, click the cog wheel icon next to Public Key, and import the key from the clipboard.
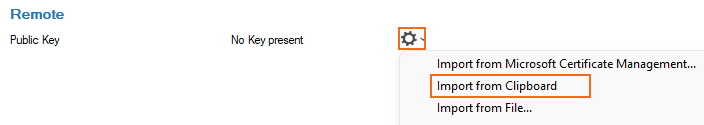
- Click OK.
- Click Send Changes and Activate.
- In the Local section, click the cog wheel icon next to Server Protocol Key, and export the key to clipboard.
- Click OK to close the TINA Tunnel window.
- Go to CONFIGURATION > Configuration Tree > Box > your remote firewall > Assigned Services > VPN > Site to Site.
- Click Lock.
- Select TINA Tunnels.
- Open the configuration for the site-to-site tunnel transport.
- Click the Identity tab.
- In the Remote section, click the cog wheel icon next to Public Key, and import the public key from the clipboard.
- Click OK and close the TINA Tunnel window.
- Click Send Changes and Activate.
Access Rules
You must create Pass access rules on both systems to allow traffic between the two peers. For more information, see How to Create Access Rules for Site-to-Site VPN Access.
Verify that the TINA site-to-site tunnel is established on both firewalls: