Microsoft Entra ID is a secure, cloud-based authentication store that lets you create users, groups, and applications that use authentication mechanisms such as MSAD. To configure MSAD authentication against Microsoft Entra ID, create your domain on the Azure Portal and define users who should be able to manage it. Then, activate Secure LDAP access over the Internet.
Step 1. Add Your Domain to the Azure Portal
Enable Azure AD Domain Services and add your domain.
- Log into the Azure Portal: https://portal.azure.com
- In the left menu, click Create a resource.
- In the search field, type
domainand select Azure AD Domain Services. - Click Create. The Azure AD Domain Services configuration opens.
- In Basics:
- Enter the DNS domain name for your domain.
- Select your Subscription, Resource group, and Location.
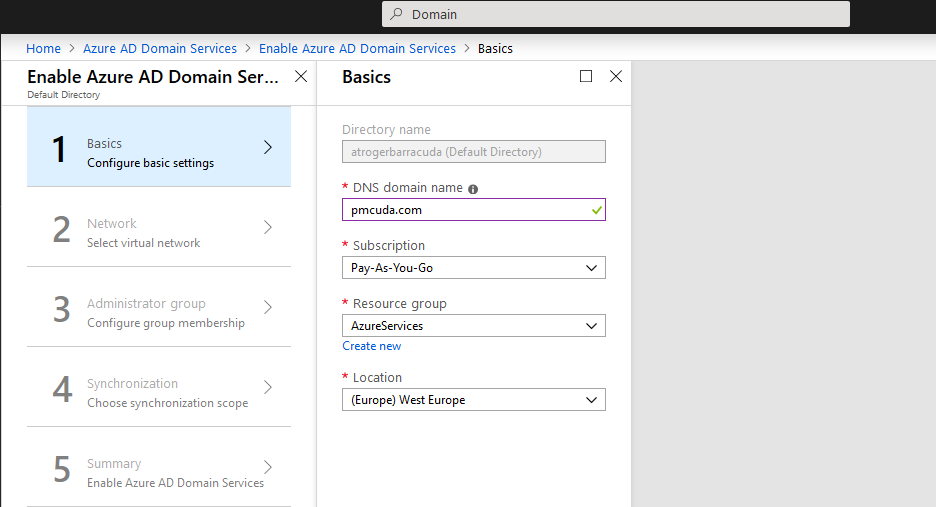
- Click OK. In Network:
- Select or create the Virtual network (VNET).
- Select or create a Subnet for the service.
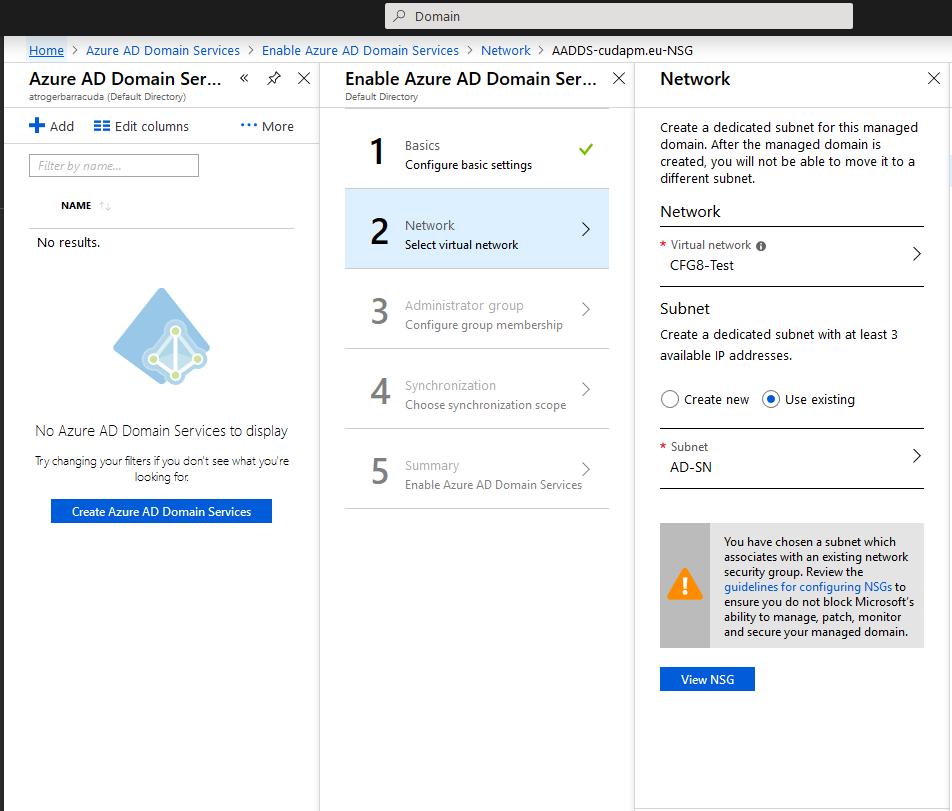
- Click OK. The group AAD DC Administrators will be automatically created.
- Click AAD DC Administrators. Members opens.
- Click + to add the users and / or groups that should be able to manage the created domain.
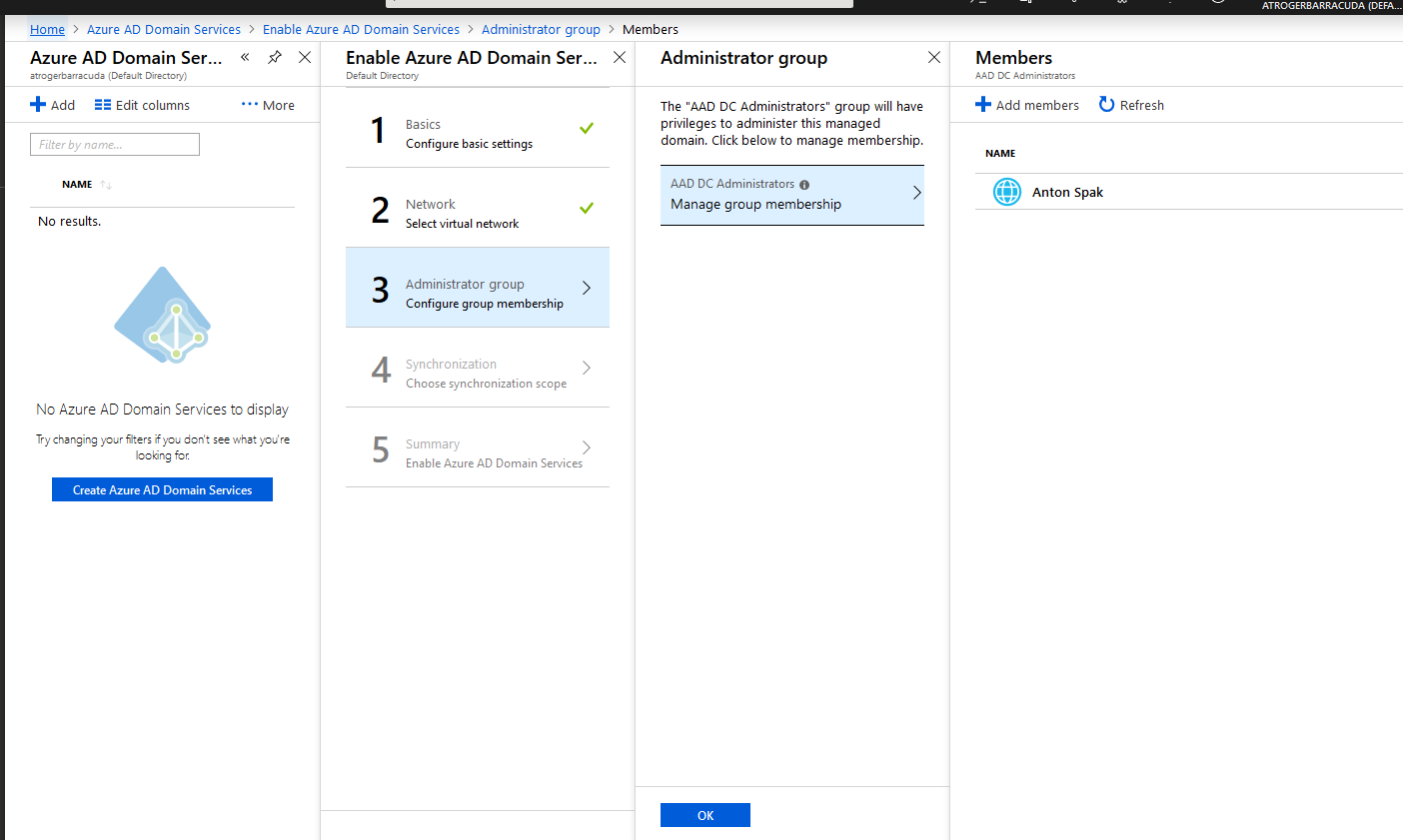
- Click OK. Synchronization opens.
- Select the scope of the users for domain synchronization.
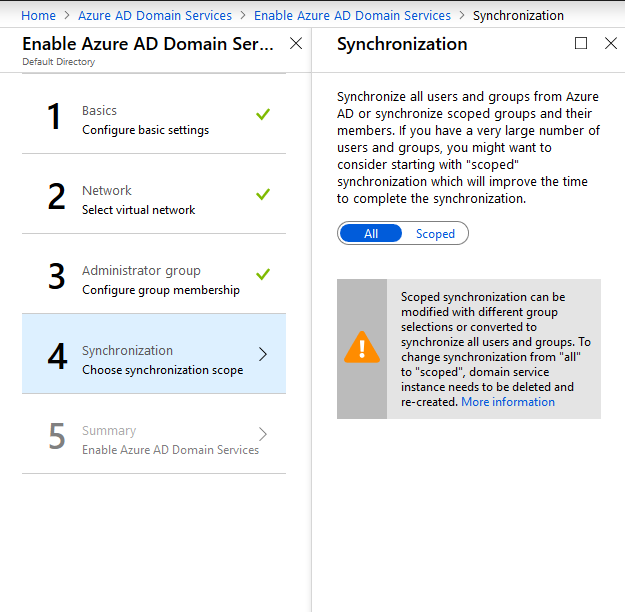
- Click OK. Summary opens.
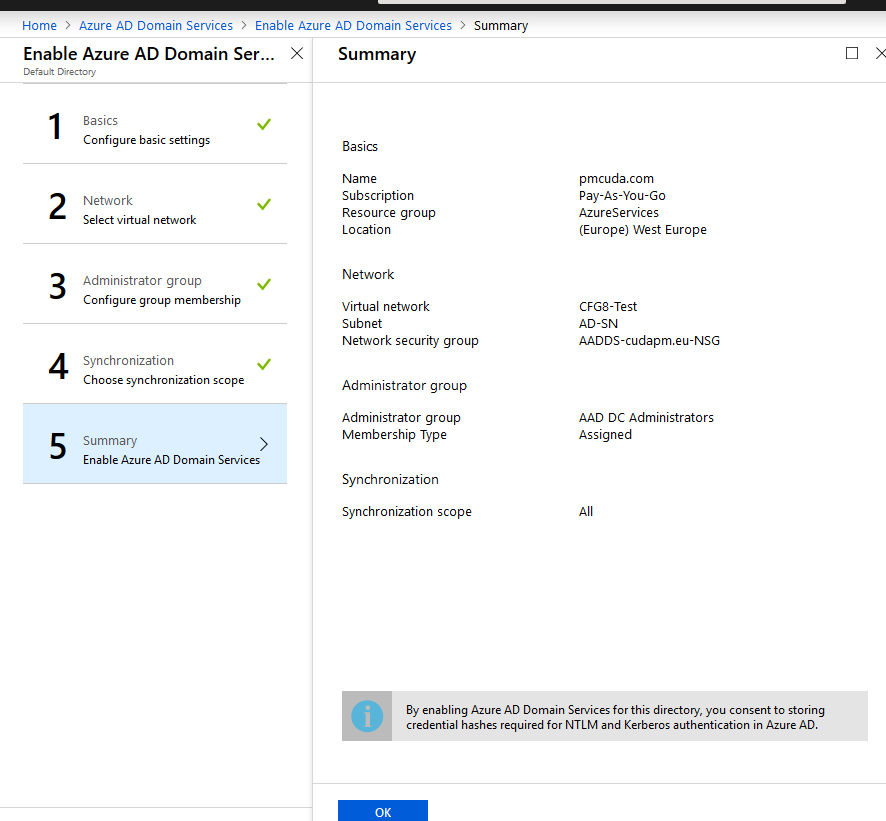
- Double-check your settings and click OK to finish the configuration. The Azure AD Domain Services will now be deployed.
Step 2. Verify the Domain and Configure a Service User
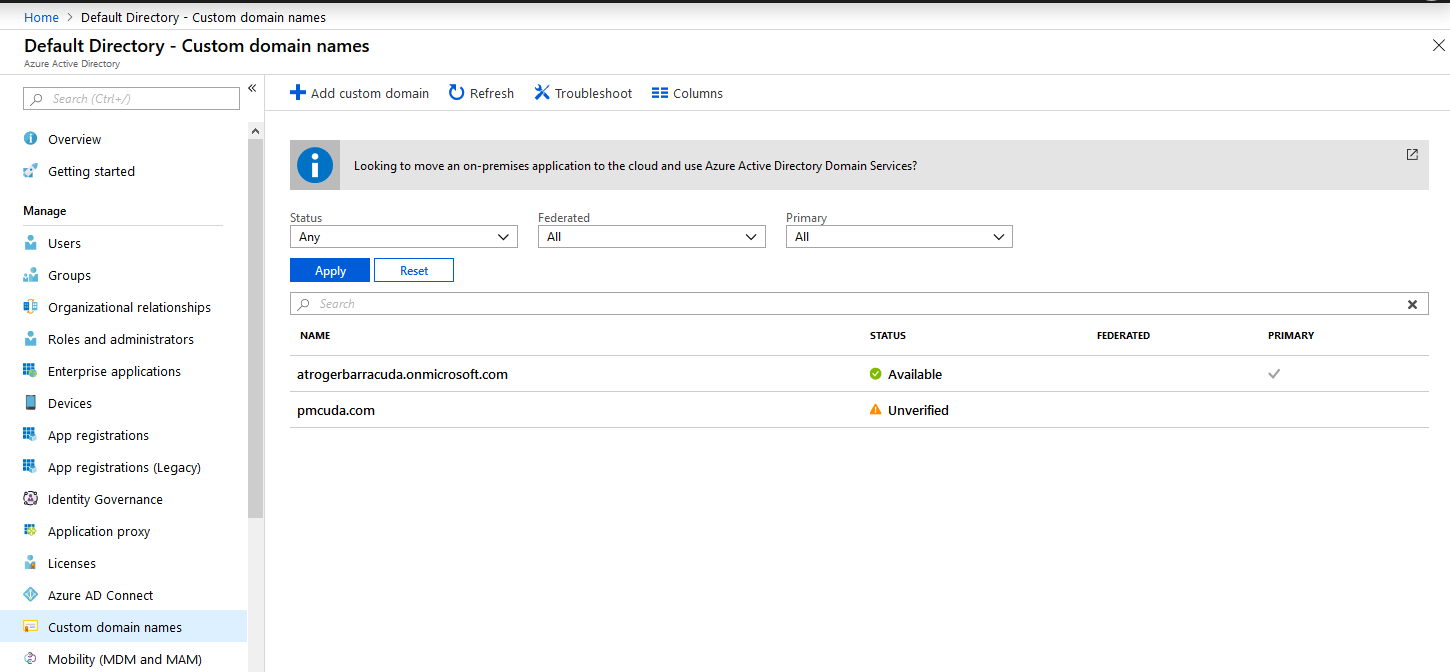
After the deployment has succeeded, add and verify the domain to your Azure AD from the Azure Default Directory - Custom domain names.
- Go to your domain.
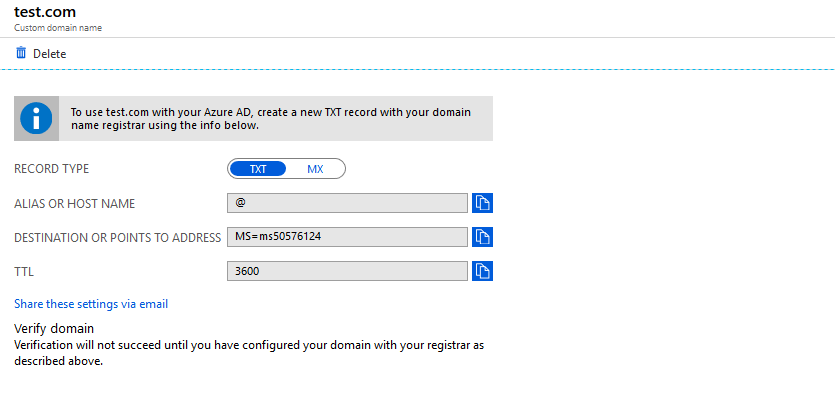
- Configure a TXT or MX record on your domain register to verify the domain.
- From Users on the left panel, add a service user to the domain.
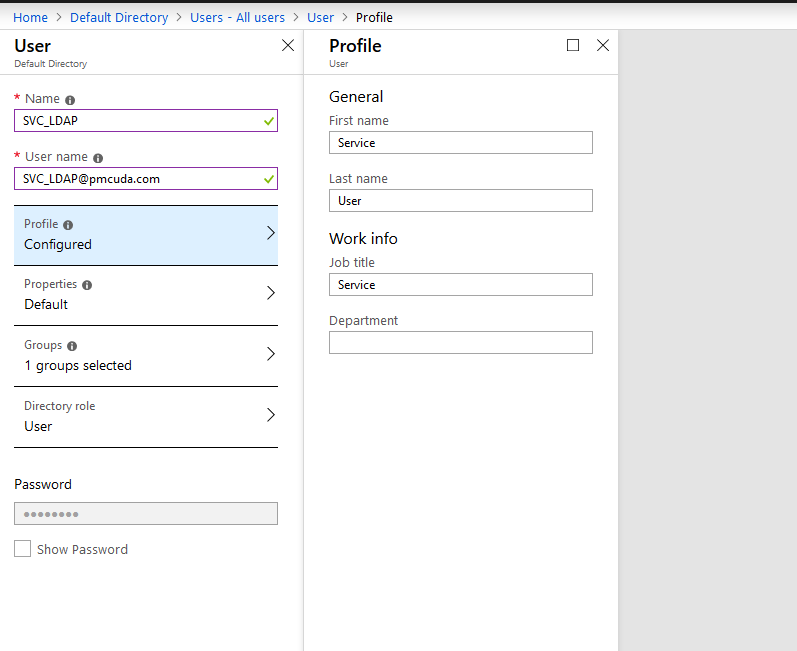
- Add the user to the Azure Admins Group.
- After adding user login with this user, change the Password.
Step 3. Activate LDAPs
- Go to Azure AD Domain Services > your managed domain .
- Update / configure the DNS settings.
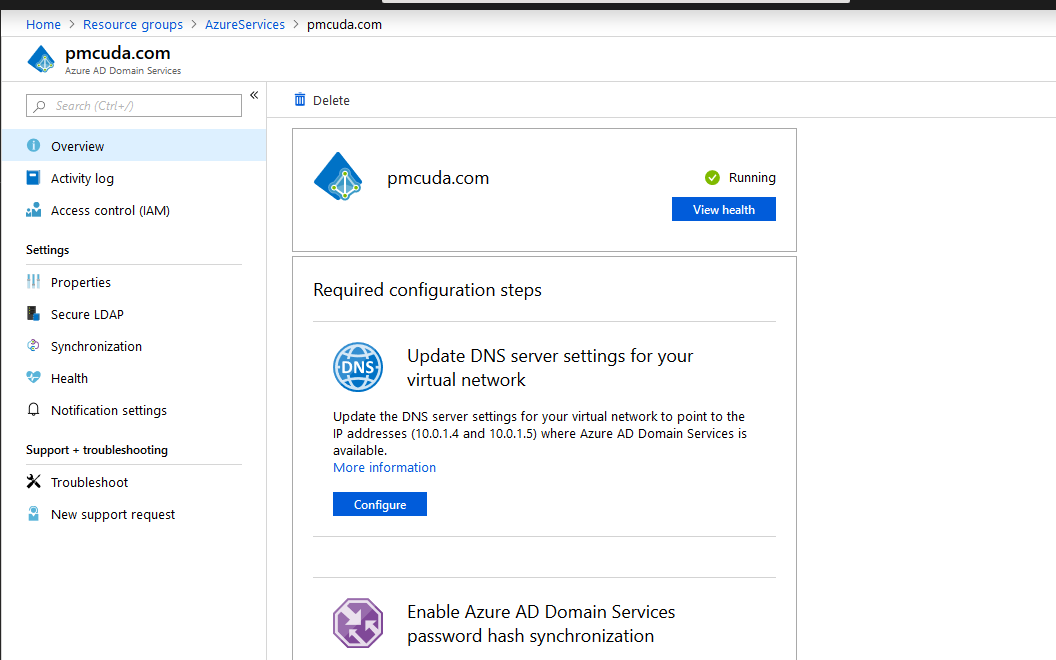
- In the left menu, click Secure LDAP.
- Enable Secure LDAP.
Enable Allow Secure LDAP access over the internet.
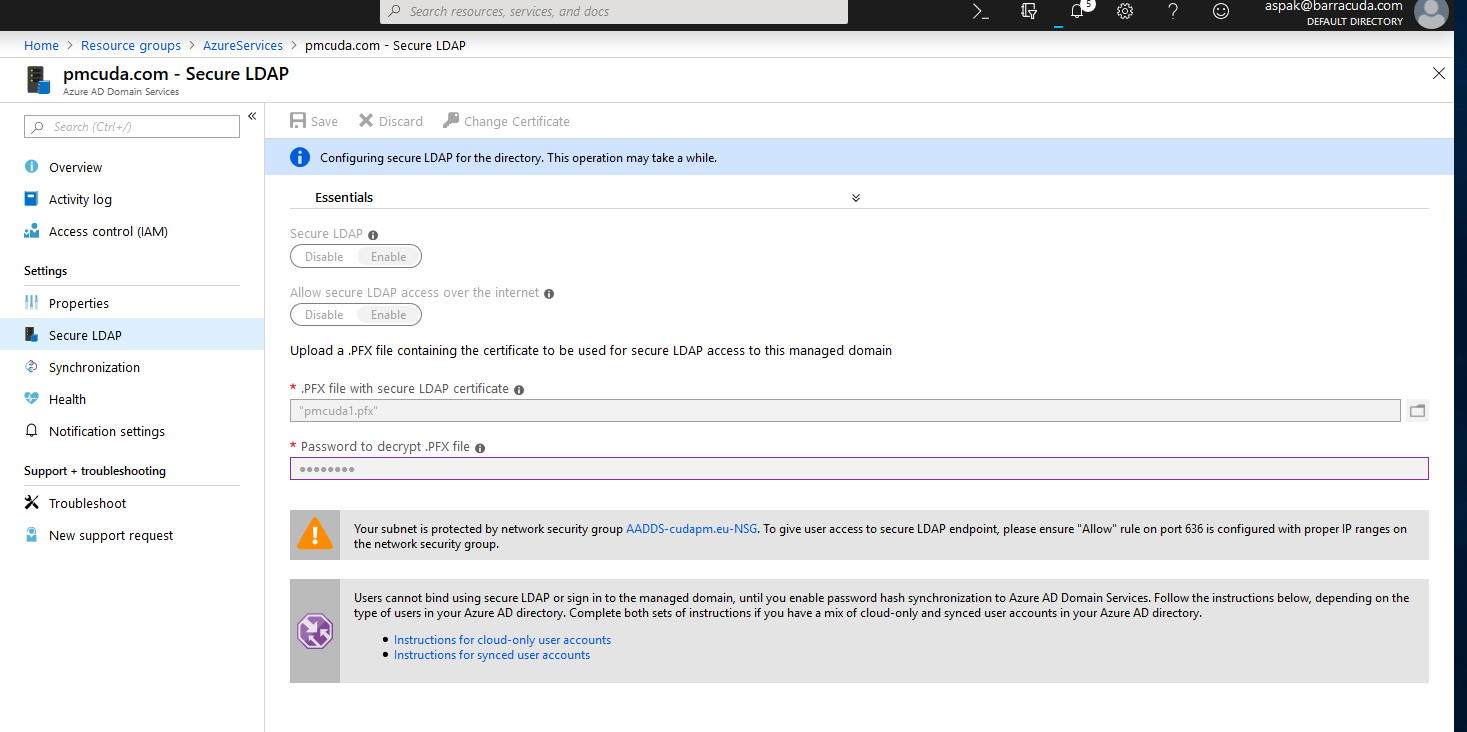
In this case, you will require a certificate for your domain. The certificate can be obtained from the root CA. Alternatively, a self-signed certificate can be used. For detailed information on how to create a self-signed certificate, refer to the Microsoft documentation: https://docs.microsoft.com/en-us/azure/active-directory-domain-services/configure-ldapsRecommendations:
- Use TripleDES-SHA1 encryption. Also make sure the password has at least 8 characters.
- The name should only include *.pfx suffix. For example, do not use pmcuda.com.pfx. This will fail with incorrect password.
- Add the certificate to activate LDAPs.
- The public IP and the associated NSG you need to point the CloudGen Firewall to can be found in Properties:
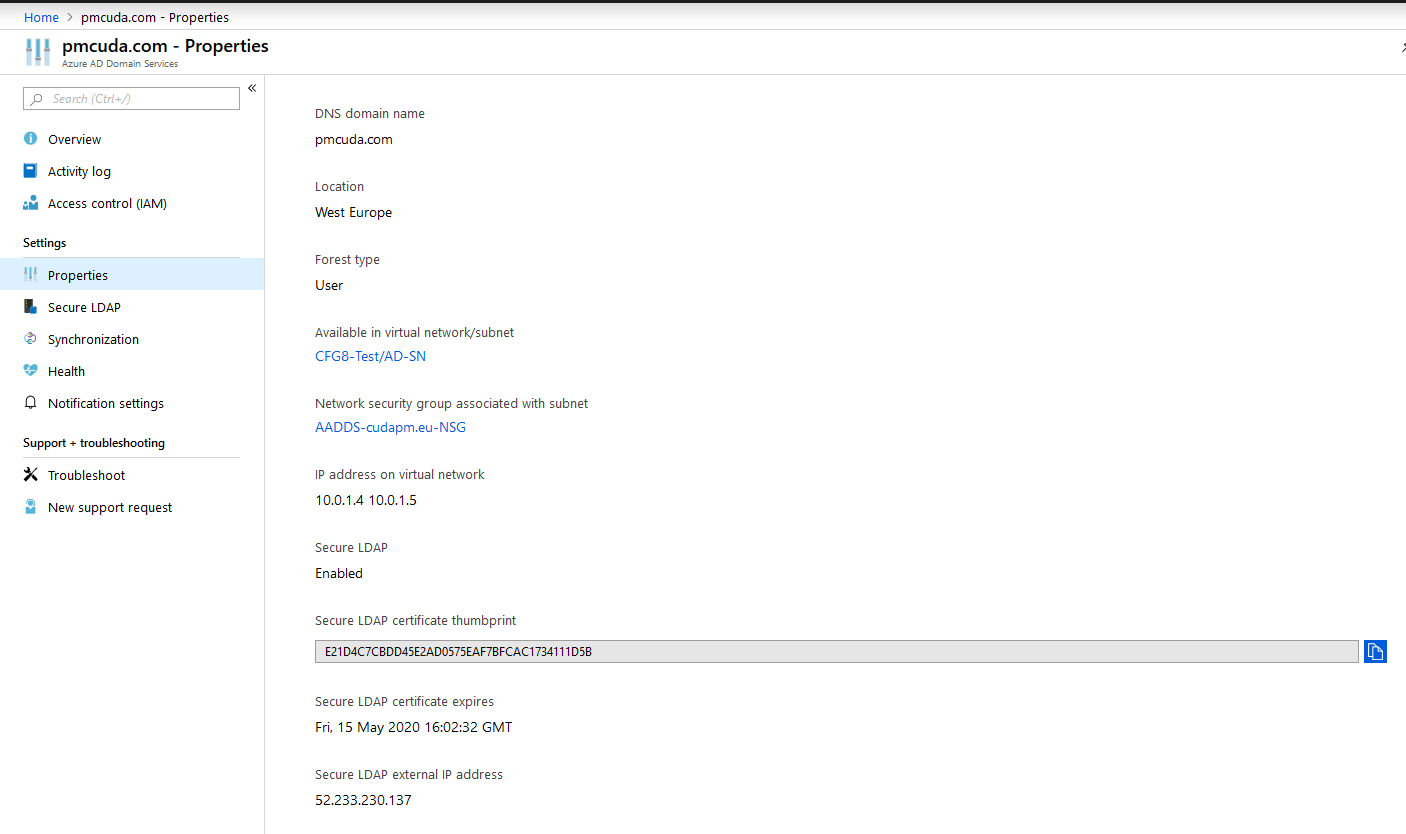
- Set up the Network Security Group (NSG) according to your needs. Add at least port 636 to allow access via LDAPs for the on-premises CloudGen Firewall.
Step 4. Configure LDAP Authentication on the CloudGen Firewall
- On the CloudGen Firewall or Control Center, go to Authentication Service > LDAP Authentication.
- Configure the LDAPs using MSAD attribute settings according to this example:?
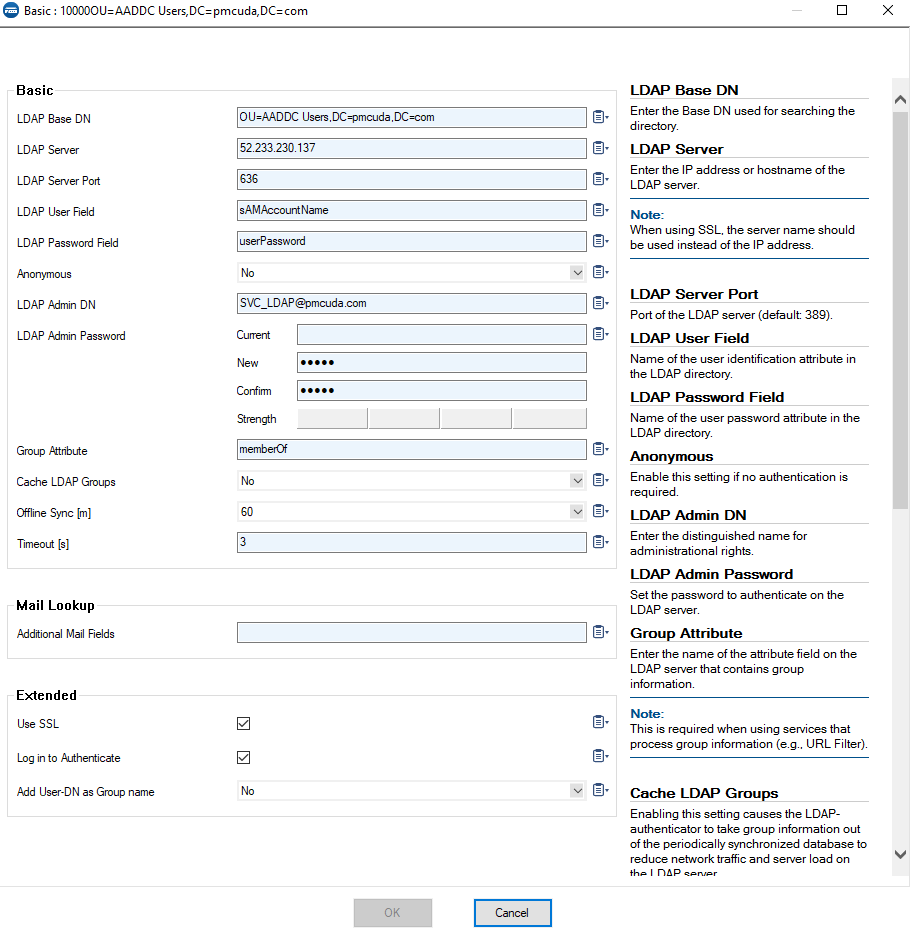
- Click OK.
- Click Send Changes and Activate.
For more information, please refer to the Microsoft documentation: https://docs.microsoft.com/en-us/azure/active-directory-domain-services/create-instance
