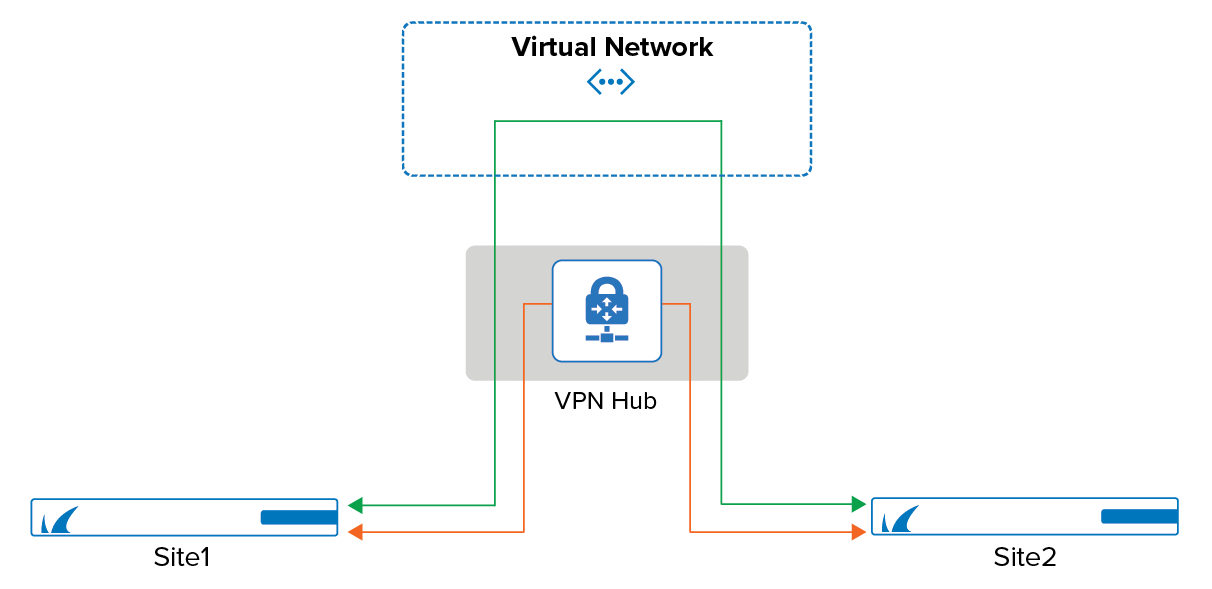
VPN connections from a CloudGen Firewall to the Azure Virtual WAN hub are provisioned automatically. The automatic configuration provides a robust and redundant connection by introducing two active-active IPsec IKEv2 VPN tunnels for each ISP with the respective BGP setup and fully automated Azure Virtual WAN site creation on Microsoft Azure. All necessary services on the CloudGen Firewall (BGP and VPN) are created and configured automatically. The finished deployment allows for both branch-to-branch and branch-to-cloud connections. If you disable or delete the configuration on your CloudGen Firewall, make sure to delete the resources in Azure as soon as Virtual WAN is no longer needed.
Before You Begin
- For CC admins to be able to trigger the virtual WAN configuration, cloud integration permissions are required. For the CC admin to be able to see the automatically created services, read permissions for VPN and BGP services are required. The automation service itself is not run in the scope of the CC admin that triggered the connection.
Create an Azure service principal to allow the firewall to authenticate to the Azure Virtual WAN APIs. For more information, see How to Create a Service Principal for Azure Virtual WAN.
- Verify that Barracuda Online Services can be accessed by the appliance. For more information, see Best Practice - Hostname List for Barracuda Networks Online Services.
Before You Connect a Firewall Hosted in the Public Cloud to Azure Virtual WAN
Before you start with Step 1, configure the following on firewalls hosted in the public cloud:
- The firewall virtual machine must have multiple network interface cards (at least 2). Those network interface cards must be attached to different subnets.
- Each network interface card used for the connection to the Virtual WAN needs its own public IP address.
- Configure Direct Internet Access for each interface used for the connection to the Virtual WAN. See Step 1.
Step 1. Configure WAN Connection
You must have a static IPv4 public IP address. Your links must have similar bandwidth and latency if you want to use more than one ISP. The management interface can not be used as an ISP link port.
- Configure your ISP. For more information, see How to Configure an ISP with Static IP Addresses, How to Configure an ISP with Dynamic IP Addresses (DHCP), xDSL WAN Connections or WAN Connections.
Verify that the setting Direct Internet Access is enabled in your ISP configuration, unless you are using xDSL.
- Configure direct attached routes to announce the local networks that should have access to cloud resources. For more information, see the Advertise Route setting in How to Configure Directly Attached Routes .
Step 2. Create Virtual WAN Service in Microsoft Azure
- Log into the Azure portal: https://portal.azure.com
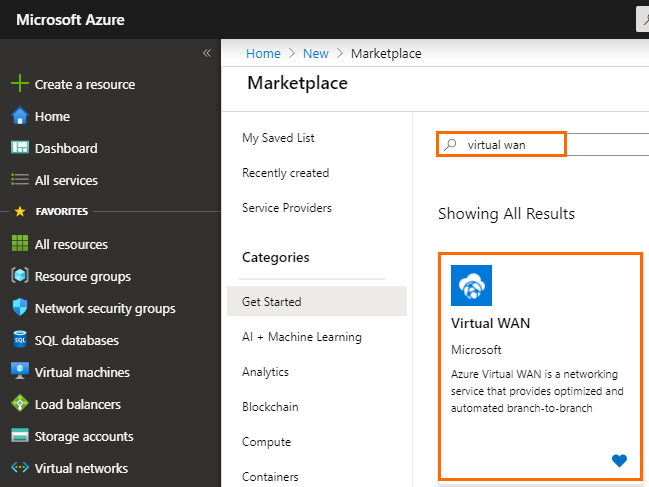
- In the left menu, click Create a resource and search for Virtual WAN.
- Click Virtual WAN.
- In the next blade, click Create.
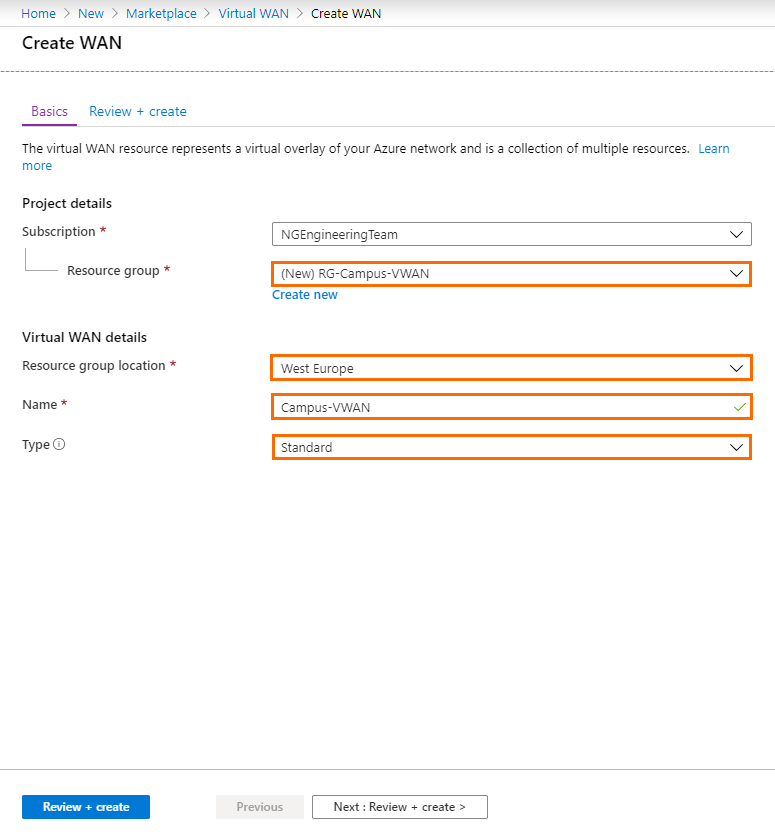
- In the Create WAN blade, specify values for the following:
Resource Group – Select an existing resource group from the drop-down menu, or create a new one.
- Resource group location – Select the region of the Virtual WAN, e.g., West Europe .
- Name – Enter a name for your Virtual WAN.
- Type – Select Standard if you want to use multiple ISP for the connection of your firewall to Microsoft Azure Virtual WAN or hub-to-hub/routing mesh for peered VNETs, or if you want to connect the hubs in Azure. Otherwise, select Basic.
- Click Review + Create.
- Click Create to finish Virtual WAN creation.
Step 3. Create a Hub in Your Azure Virtual WAN
- Log into the Azure portal: https://portal.azure.com
- In the left menu, click All services and search for Resource groups.
- Click on the resource group your vWAN is attached to. See Step 2.
- Click on your vWAN created in Step 2.
- On the left side, click Hubs.
- In the next blade, click + New Hub.
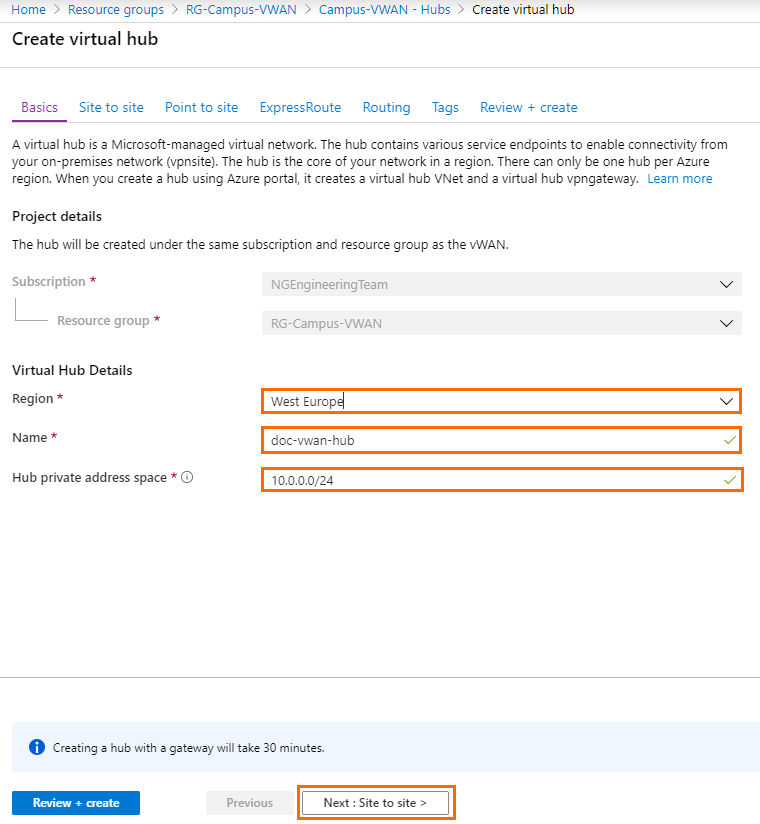
- The Create virtual hub blade opens. Specify values for the following:
- Region – Select a region from the drop-down list, e.g., West Europe
. - Name – Enter a name for the hub, e.g.,
doc-vwan-hub. - Hub private address space - Enter the hub's address range in CIDR, e.g.,
10.0.0.0/24. Select a unique network that is dedicated for the hub only.
- Region – Select a region from the drop-down list, e.g., West Europe
- Click Next: Site to site >.
- The Site to site blade opens. Specify the values for the following:
- Do you want to create a Site to site (VPN gateway) - Select Yes.
- Gateway scale units – Select a scale unit from the drop-down menu according to your requirements.
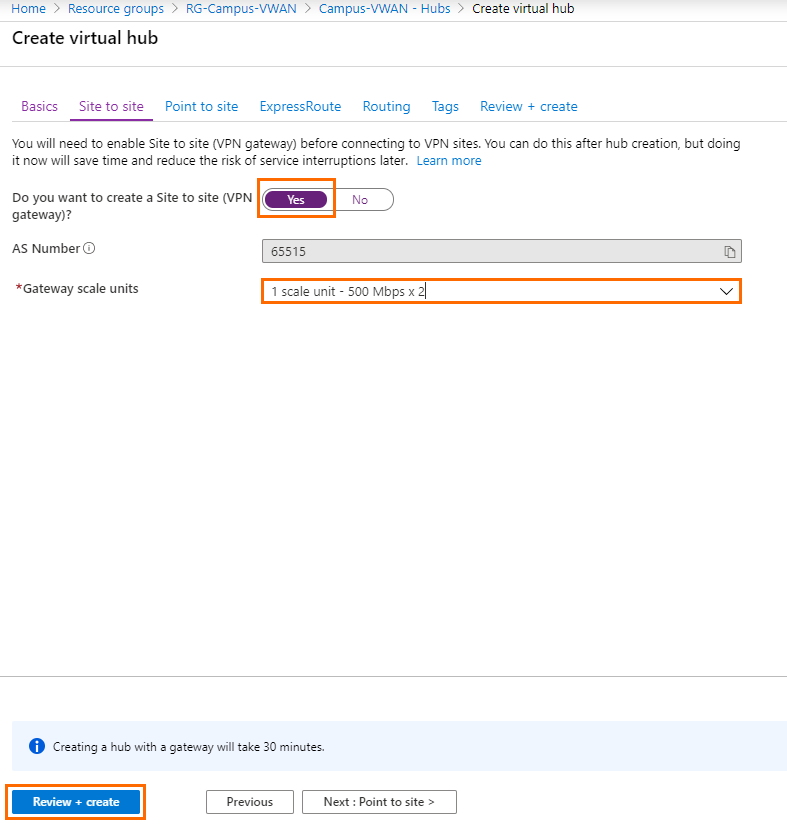
- Click Review + create.
- Review your settings and click Create to start the creation of the hub. This can take up to 30 minutes.
Step 4. Trigger Virtual WAN connection
- Log into the CloudGen Firewall with Firewall Admin.
- Go to CONFIGURATION > Configuration Tree > Multi Range > your range > your cluster > Boxes > your Box > Advanced Configuration > Cloud Integration.
- Select Azure Virtual WAN in the left menu.
- Click Lock.
- In the Azure Virtual WAN Connections section, click +.
- Enter a name for your virtual WAN and click OK.
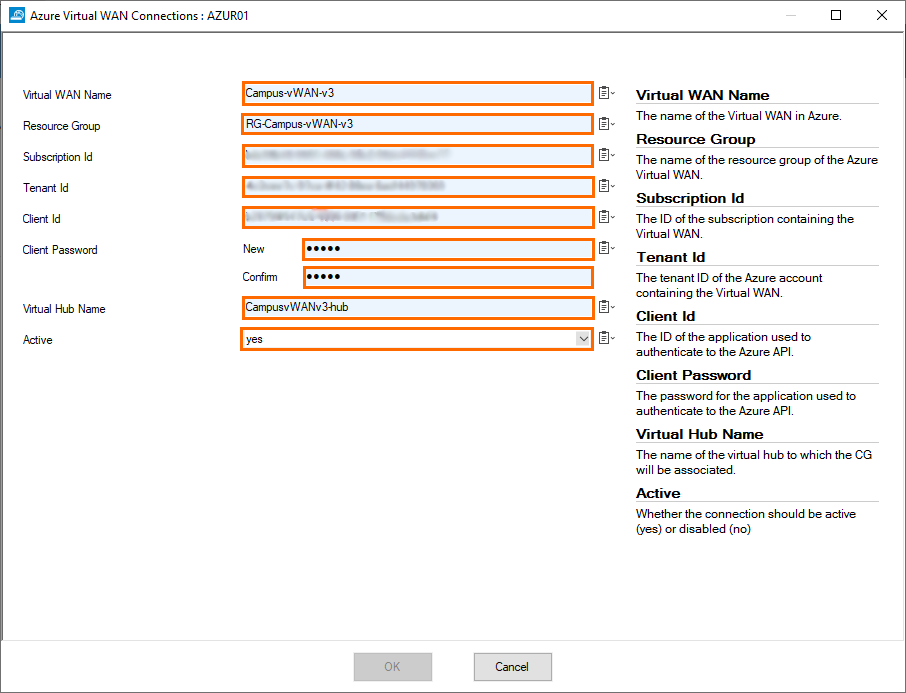
- The Azure Virtual WAN Connections window opens. Specify values for the following:
- Virtual WAN Name – Enter the name of the virtual WAN created in Step 2.
- Resource Group – Enter the name of the resource group containing the virtual WAN.
- Subscription Id – Enter the ID of the subscription containing the Virtual WAN.
- Tenant Id – Enter the tenant ID of the Azure account containing the Virtual WAN.
- Client Id – Enter the ID of the application used to authenticate to the Azure API.
- Client Password New – Enter the password for the application used to authenticate to the Azure API.
- Client Password Confirm – Retype t he password for the application used to authenticate to the Azure API.
- Virtual Hub Name – Enter the name of the hub created in Step 3.
- Active – Select Yes.
- Click OK
- Click Send Changes and Activate.
A VPN site entry is automatically created, and the firewall starts to check for an available configuration every 30 seconds. Wait for the new hub association to complete. The firewall automatically picks up the new configuration and connects to the Virtual WAN.
Step 5. Configure Routes to Be Advertised via BGP
Only routes with the parameter Advertise set to yes will be propagated via BGP.
- Go to CONFIGURATION > Configuration Tree > Multi Range > your range > your cluster > Boxes > your Box > Network.
- Click Configuration Mode.
- Click Switch to Advanced.
- Click Lock.
- (optional) Click IP Configuration. In the Management Networks and IPs section, set Advertise Route to yes in order to propagate the management network.
- In the left menu, click Advanced Routing.
- Double-click on the Routes you want to propagate, and set Advertise Route to yes.
- Click OK.
- Click Send Changes and Activate.
Step 6. Verify Connectivity and Routing
For redundancy reasons, the CloudGen Firewall automatically creates two IPSec-IKEv2 VPN tunnels for each ISP and the required BGP routes to the Microsoft Azure Virtual Hub. Both tunnels for each ISP are in active-active mode. In case one tunnel fails, the routing is changed to automatically use the other tunnel. A failover can take up to 30 seconds, during which no traffic will be forwarded.
Step 6.1 Verify VPN Tunnels and Routing on Your Firewall
- Log into the firewall.
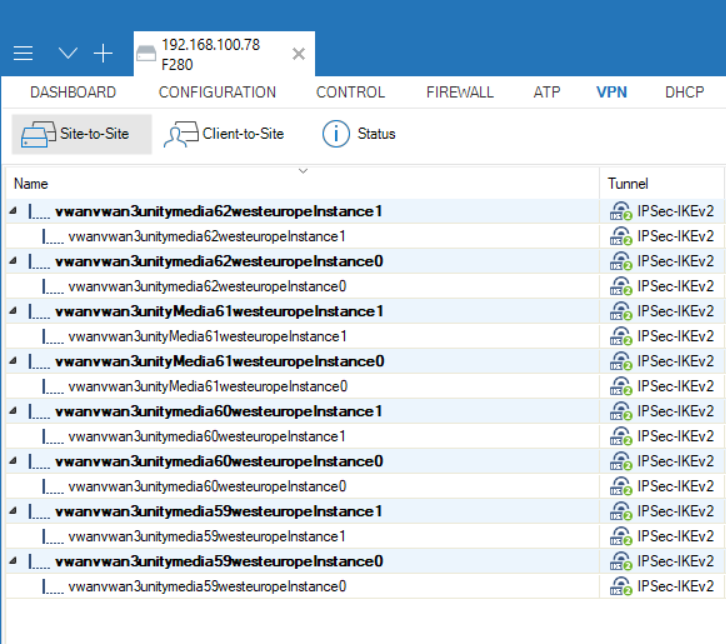
- Go to VPN > Site-to-Site.
- Verify that two IPSec-IKEv2 tunnels for each ISP are up and running. In the example below, four ISPs are configured, resulting in eight tunnels (two tunnels for each link):
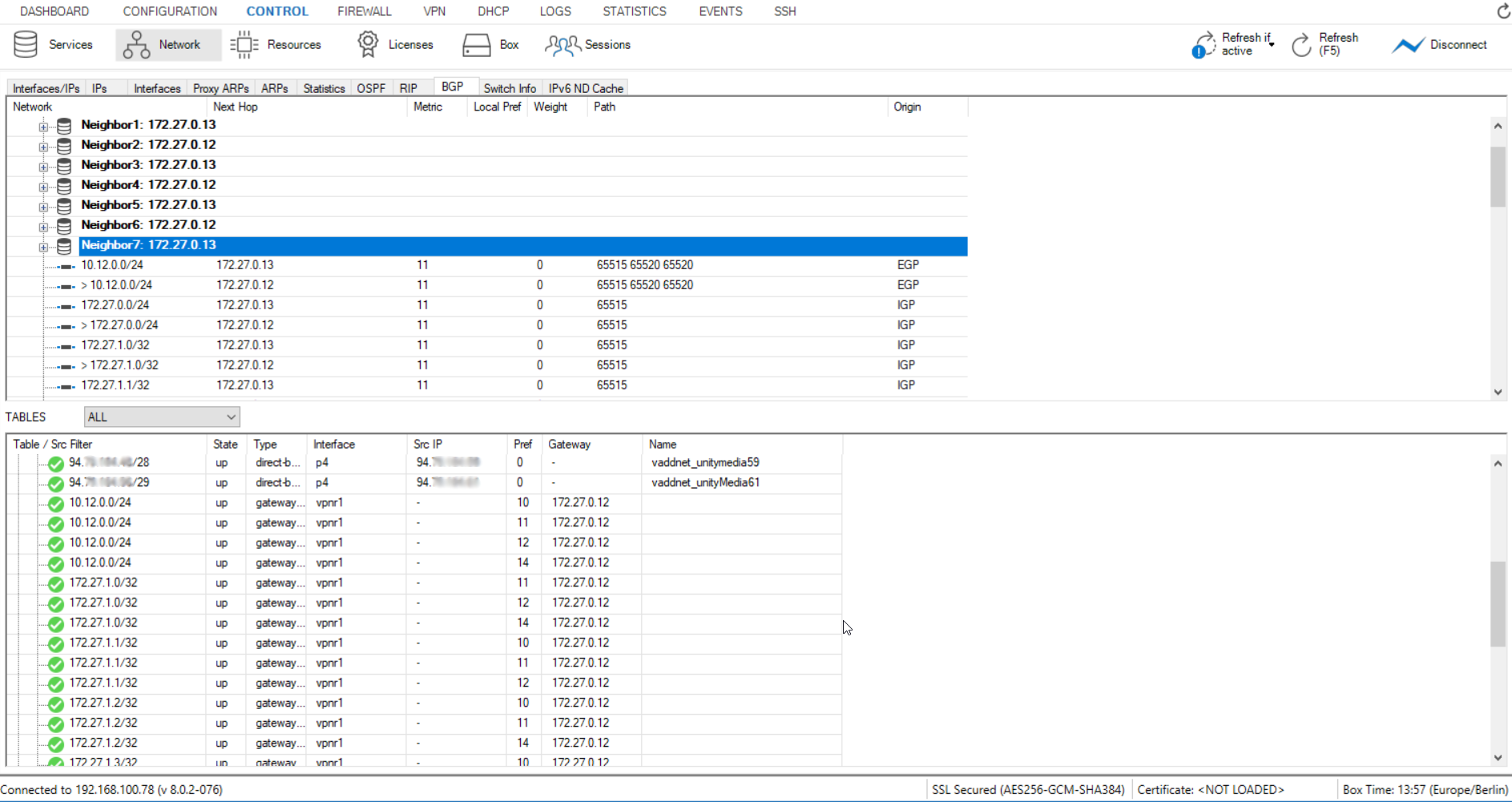
- Go to CONTROL > Network and open the BGP tab.
- Verify that, along with the VPN tunnels, all associated BGP autonomous systems and neighbors are present. In the example below, four ISPs are configured, resulting in eight BGP neighbor entries.
(Optional) Step 6.2 Verify Connectivity and Routing in Microsoft Azure
- Log into the Azure portal: https://portal.azure.com
- In the left menu, click All services and search for Virtual WANs.
- Click on your vWAN created in Step 2.
- Click on your hub created in Step 3.
- Click VPN (Site to site).
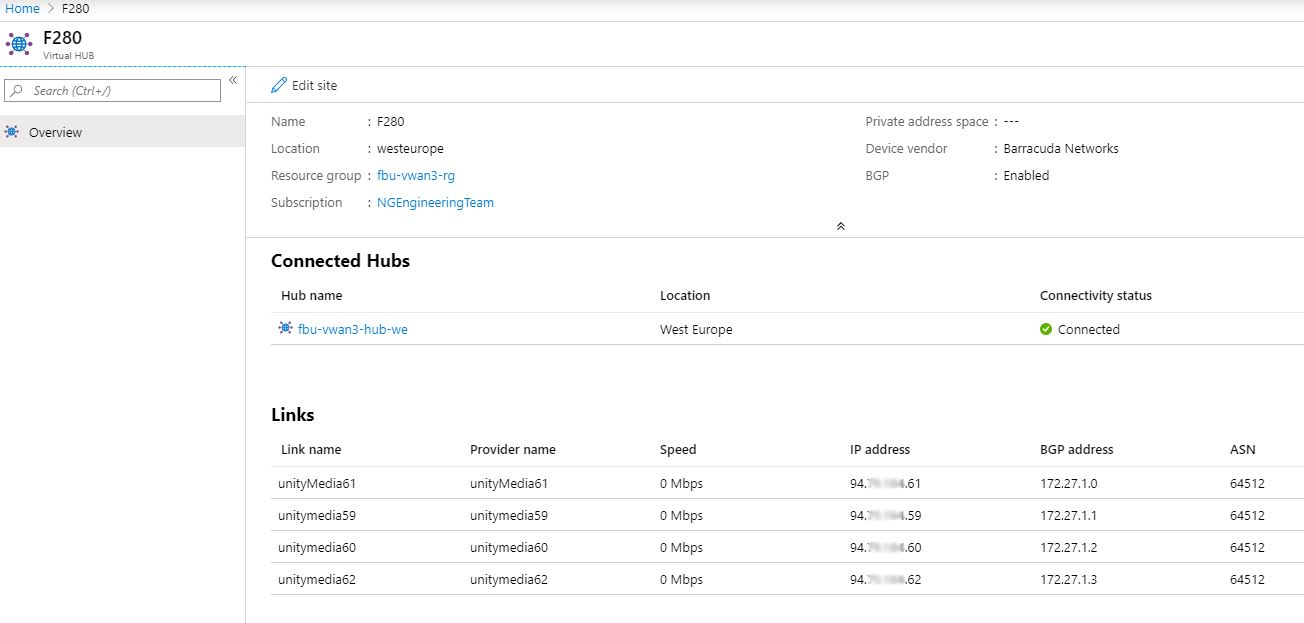
- Click on the entry of your CloudGen Firewall in the site list.
- In the next blade, you can see an entry for each ISP:
Step 7. Configure the Forwarding Firewall Rule Set
To manage and restrict network traffic from and to the Azure Virtual Hub, the forwarding firewall rule set needs to be adapted to allow traffic as required.
For more information, see How to Create a Pass Access Rule.
Next Steps
Attach an Azure Virtual Network to the Virtual WAN hub to use the VPN connection for branch-to-cloud connectivity.