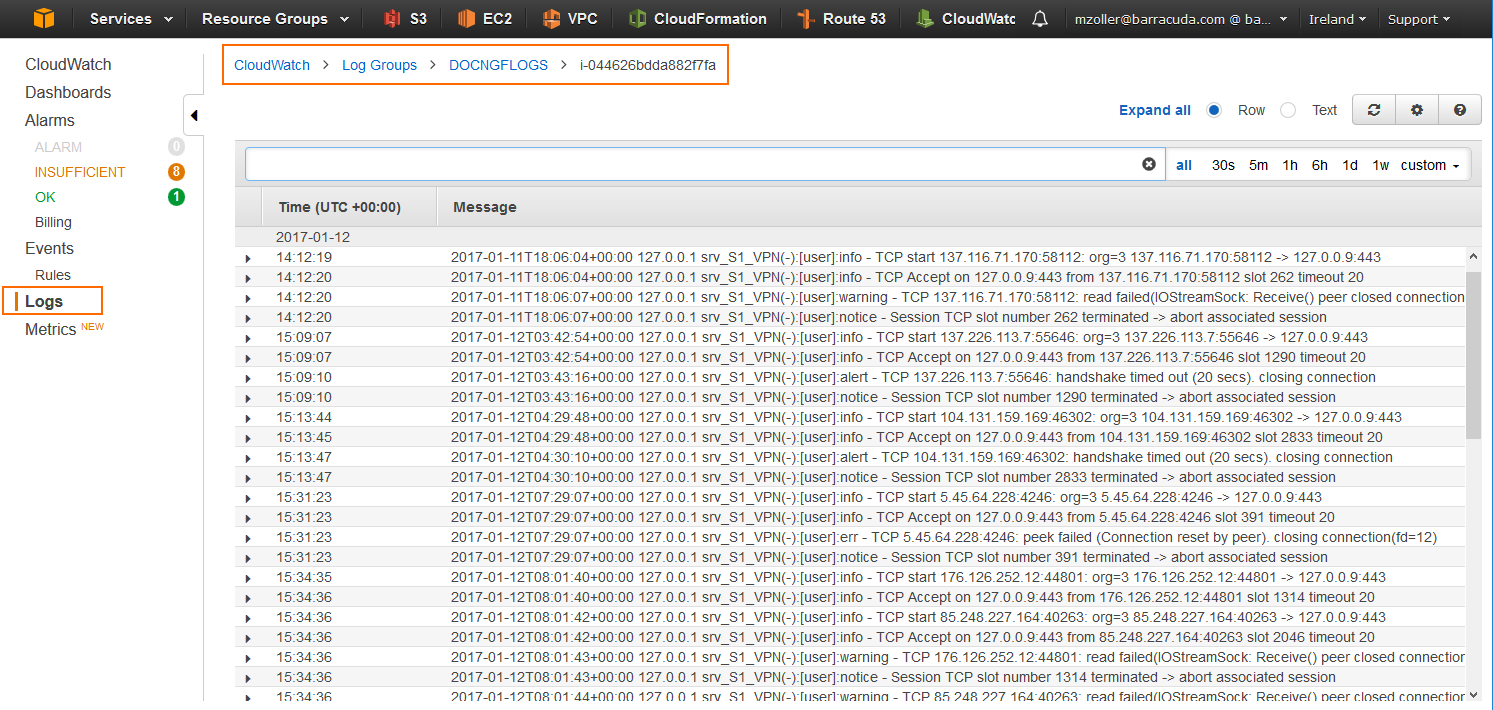
To stream log data from your firewall to AWS CloudWatch, you must configure AWS Cloud Integration and configure syslog streaming on the firewall. The IAM role assigned to the firewall instance must include an IAM policy allowing the firewall instance access to AWS CloudWatch. Configure syslog streaming with AWS CloudWatch as the destination. The configured log group is automatically created, and the logs are placed into a folder using either the instance ID or the hostname as the name. No additional configuration is required for AWS CloudWatch to collect the following metrics:
Before You Begin
The firewall must be deployed with an IAM role that allows access to AWS CloudWatch. For more information, see How to Create an IAM Role for a CloudGen Firewall in AWS.
Step 1. Enable Syslog Streaming
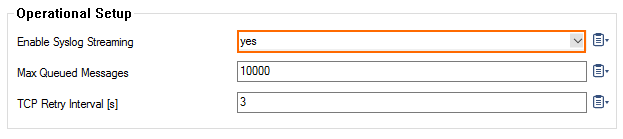
Enable syslog streaming and, optionally, configure the AWS region if it is different from the region of the firewall instance.
- Go to CONFIGURATION > Full Configuration > Box > Infrastructure Services > Syslog Streaming.
- Click Lock.
- Set Enable Syslog Streaming to yes.
- In the left menu, expand the Configuration Mode section and click Switch to Advanced View.
- Enter the AWS CloudWatch region. E.g.,
eu-west-1 - Click Send Changes and Activate.
Step 2. Configure Logdata Filters
Define profiles specifying the log file types to be transferred / streamed. Log file are classified into top level, box level, and service level log data sources.
- Go to CONFIGURATION > Full Configuration > Box > Infrastructure Services > Syslog Streaming.
- In the left menu, select Logdata Filters.
- Click Lock.
- In the Filters table, click + to add a new filter. The Filters window opens.
- Enter a Name.
- Click OK.
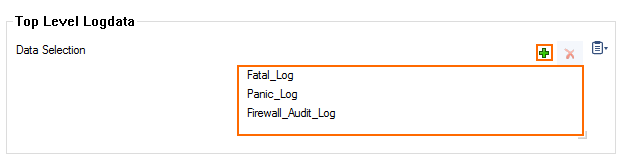
- In the Data Selection table, add the Top Level Log Files log files to be streamed. You can select:
- Fatal_log
- Firewall_Audit_Log – Data can be streamed as a part of the firewall service logs.
Panic_log
- Configure the Box Level Logfile filters:
- From the Data Selector list, select which files for this category are streamed:
- All – All box level logs are streamed.
- None – Box level logs are not streamed.
- Selection – Only box level log files defined in the Data Selection list are streamed.
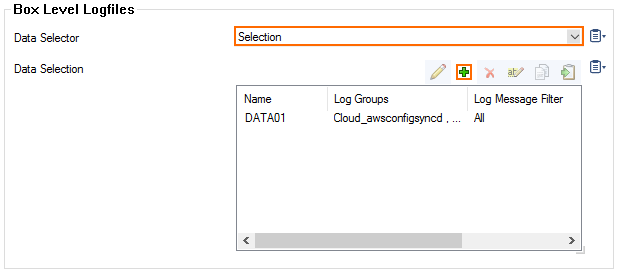
- (Selection only) Click + to add custom filters to the Data Selection table.
- In the Log Groups table, click +.
- Select the box level log files, or select Other to enter a user defined log group pattern to stream log files matching this pattern.
- (optional) From the Log Level Filter list, select the message types from the log group that are streamed.
- (Selection only) In the Selected Messages Types table, click + to add message types.
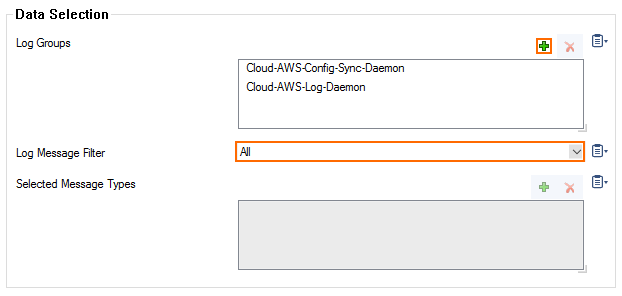
- From the Data Selector list, select which files for this category are streamed:
- Configure the Service Level Logfile filters:
- From the Data Selector list, select which files for this category are streamed:
- All – All service logs are streamed.
- None – Service level logs are not streamed.
- Selection – Only service level log files defined in the Data Selection list are streamed.
- (Selection only) Click + to add custom filters to the Data Selection table.
- In the Log Groups table, click +.
- Select the box level log files, or select Other to enter a user defined log group pattern to stream log files matching this pattern.
- (optional) From the Log Level Filter list, select the message types from the log group that are streamed.
- (Selection only) In the Selected Messages Types table, click + to add message types.
- Click OK.
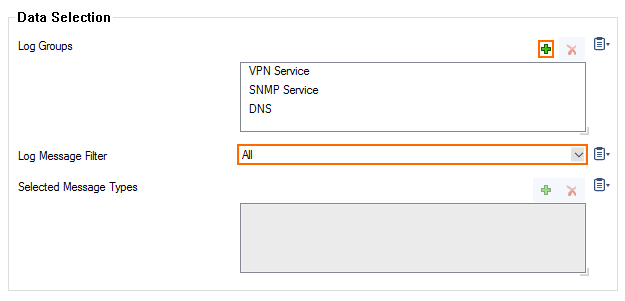
- From the Data Selector list, select which files for this category are streamed:
Click Send Changes and Activate.
Step 3. Configure AWS CloudWatch as the Logstream Destination
Configure the firewall to send the syslog stream to AWS CloudWatch. The AWS CloudWatch log group name is created automatically, with one stream per firewall.
- Go to CONFIGURATION > Full Configuration > Box > Infrastructure Services > Syslog Streaming.
- In the left menu, select Logstream Destinations.
- Click Lock.
- In the Destinations table, click + to add a new filter. The Destinations window opens.
- Enter a Name.
- Click OK.
- From the Logstream Destination list, select AWS CloudWatch.
- In the AWS CloudWatch section, enter the name of the AWS CloudWatch log Group Name.
- (optional) Select the Stream Name from the drop-down list, or select Other and enter the stream name. The stream name must be unique in the AWS CloudWatch group.
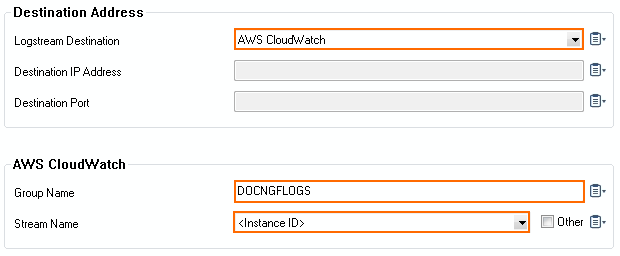
- Click OK.
- Click Send Changes and Activate.
Step 4. Configure the Logdata Streams to AWS CloudWatch
Combine the logdata filters and logstream destination to a logdata stream.
- Go to CONFIGURATION > Full Configuration > Box > Infrastructure Services > Syslog Streaming.
- In the left menu, select Logdata Streams.
- Click Lock.
- In the Streams table, click + to add a new syslog stream. The Streams window opens.
- Enter a Name.
- Click OK.
- Set Active Stream to yes.
- In the Log Destinations table, click + and select the logstream destination configured in step 3.
- In the Log Filters table, click + and select the logdata filter configured in step 2.
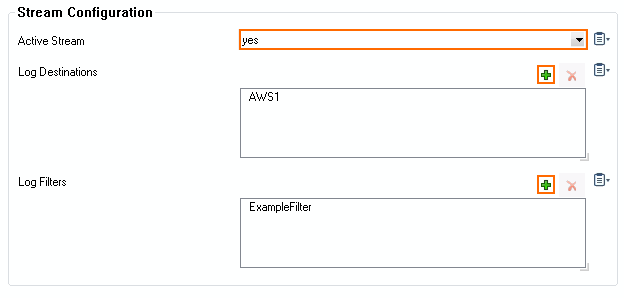
- Click OK.
- Click Send Changes and Activate.
All logs covered by the logdata filter are now streamed to AWS CloudWatch. It might take up to 30 minutes for logs to be displayed in the console.