For the firewall to authenticate to the Azure Virtual WAN APIs that enable automated connectivity, a registered app must be created. The registered app requires the following information:
- Tenant ID
- Subscription ID
- User ID / Application ID / Client ID
- Key / Client Password
Before You Begin
- Create a resource group in Microsoft Azure. This resource group must contain your virtual WAN later. Otherwise, the firewall will not have sufficient permissions to authenticate to Azure Virtual WAN APIs that enable automated connectivity.
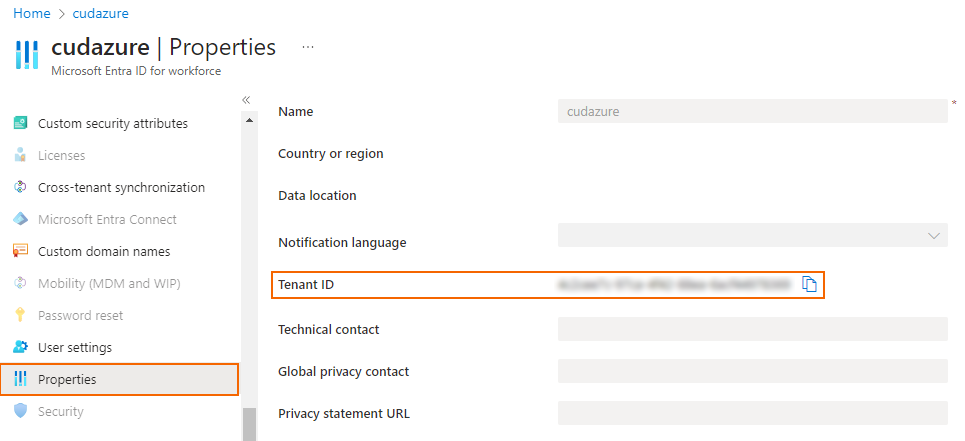
Step 1. Get the Tenant ID
- Log into the Azure portal: https://portal.azure.com
- Expand the All services menu on the left, or search for Microsoft Entra ID.
- Select Microsoft Entra ID.
- In the left menu of the Microsoft Entra ID blade, click Properties.
- Copy the Tenant ID. This is the Tenant ID of your service principal.
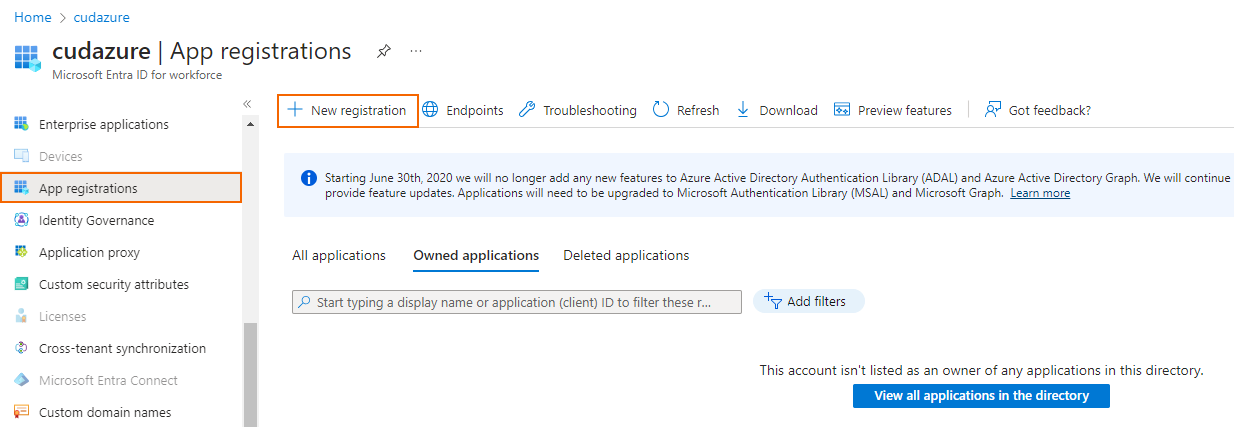
Step 2. Create New App Registration
- Log into the Azure portal: https://portal.azure.com
- In the left menu of the Microsoft Entra ID blade, click App registrations.
- Click New registration.
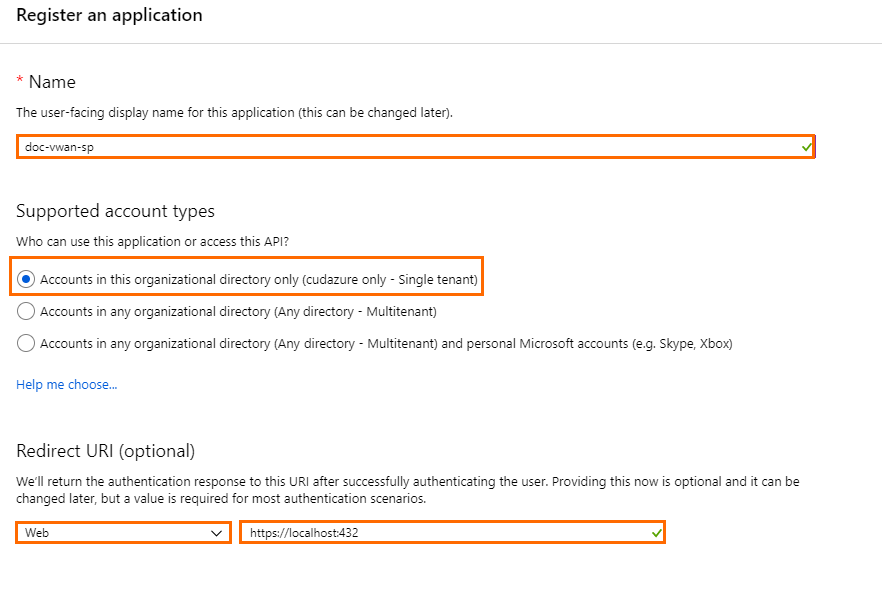
- The Register an application blade opens.
- Name – Enter a name for the application registration.
- Supported account types – Select Accounts in this organizational directory only (<your_directory_name> only - Single tenant).
- Redirect URI (optional) – Select Web from the drop-down menu and enter a random, unique URI. E.g.,
https://localhost:432
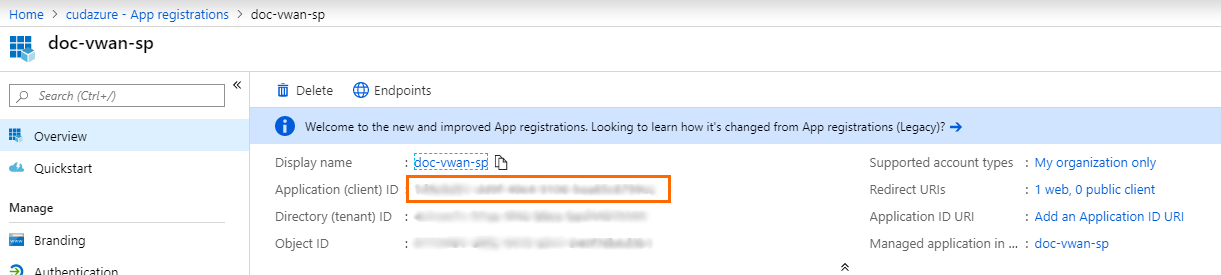
- Click Register.
Copy the Application (client) ID: This is the Client ID for your service principal information.
Step 3. Create the Service Principal Key
For the app registration, create a service principal key to authenticate.
- Log into the Azure portal: https://portal.azure.com
- Expand the All services menu on the left, or search for Microsoft Entra ID.
- Select Microsoft Entra ID.
- In the left menu of the Microsoft Entra ID blade, click App registrations.
- Click on the registered app created in Step 2. The Registered app blade opens.
- Click Certificates & secrets. The Certificates & secrets blade opens.
- In the Client secrets section, click New client secret.
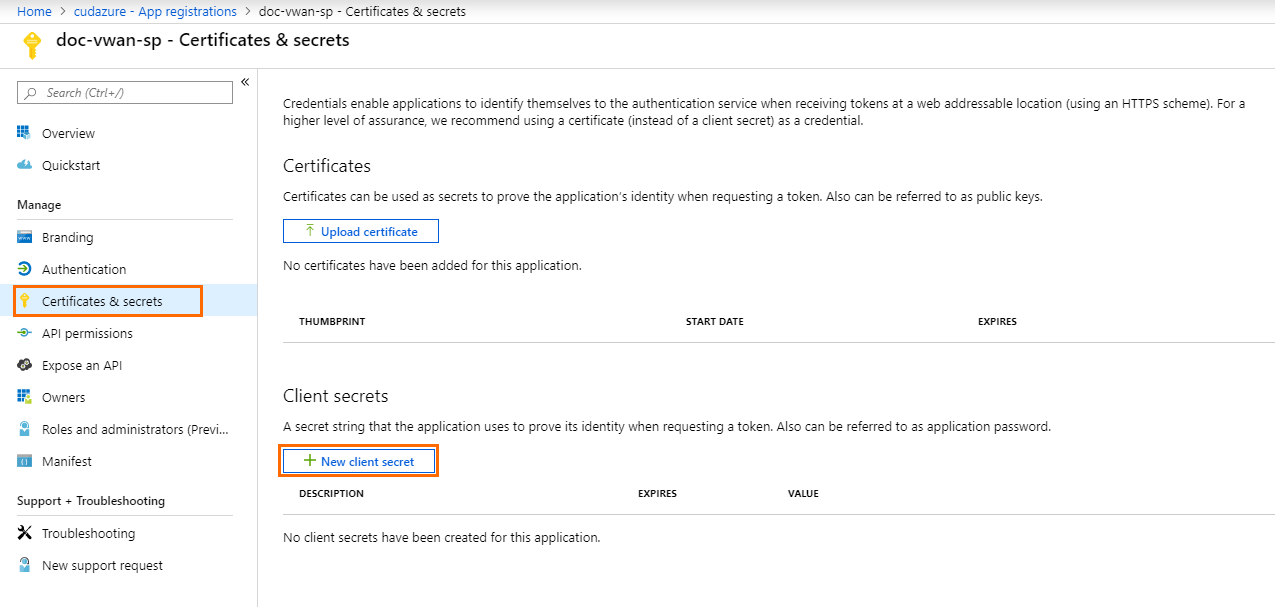
- The Add a client secret blade opens.
- Description – Enter a name for the service principal key.
- Expires – Select Never expires.
- Click Add.
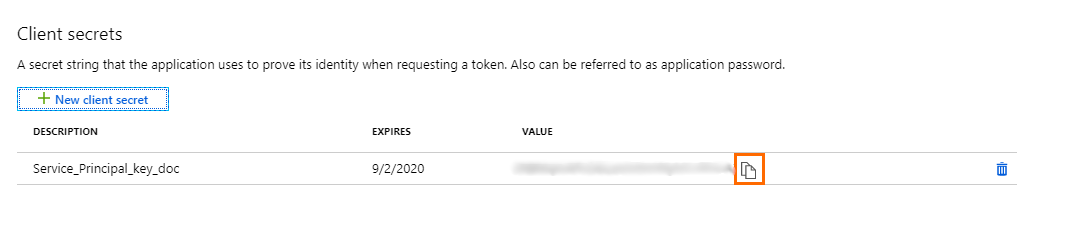
The key is now displayed in the Value column. Click on the copy icon to copy the key to your clipboard. This is your Client Password.
Step 4. Assign the Appropriate Roles to the Registered App
- Log into the Azure portal: https://portal.azure.com
- Expand the All services menu on the left, or search for Resource Groups.
- Click Resource groups.
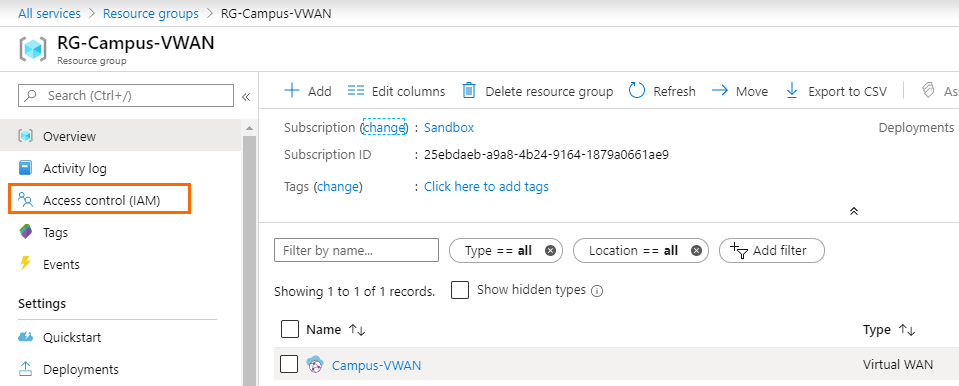
- Select the resource group that will contain your virtual WAN later.
- Click Access control (IAM).
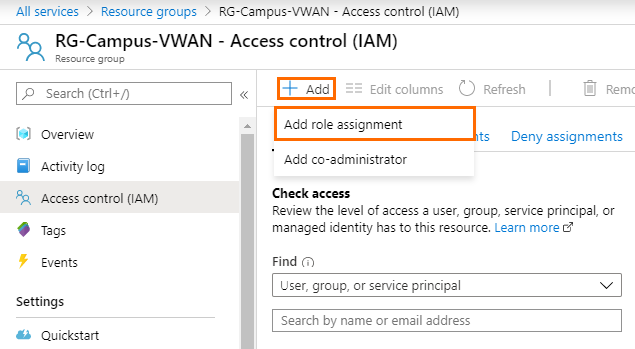
- Click +Add and select Add role assignment from the list.
- For Role, select Storage Blob Data Owner from the list.
- For Assign access to, select User, group, or service principal.
- For Select, enter the name of the registered app created in Step 2 (
doc-vwan-sp) and click on the corresponding entry of the list.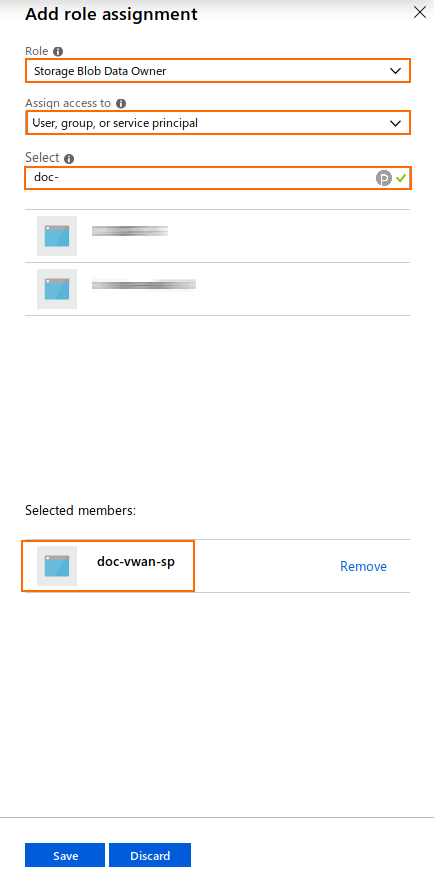
- Click Save to save your configuration.
- Repeat Step 4 and add the following roles:
- Network Contributor
- Storage Account Key Operator Service Role
- Storage Account Contributor
- Continue with Step 5.
Step 5. Get the Subscription ID
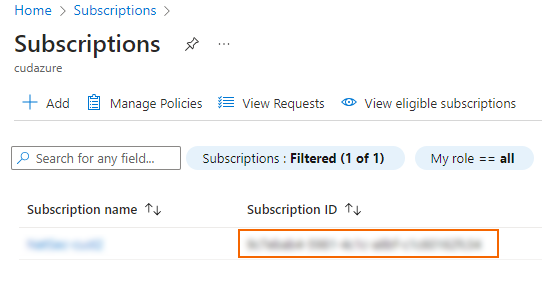
- Log into the Azure portal: https://portal.azure.com
- Select Subscriptions.
- Copy the Subscription ID in the Subscription ID column.
Next Steps
You can now configure automated connectivity for Azure Virtual WAN.
For more information, see How to Configure Automatic Connectivity to Azure Virtual WAN.
