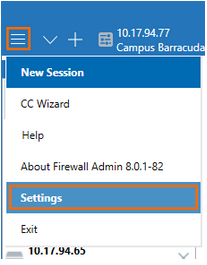
The following sections provide information on how to configure Barracuda Firewall Admin settings using the Firewall Admin User Interface configuration. To access the configuration menu, click the hamburger menu on the top left, and then select Settings.
Client Settings
To configure the connection and display for Firewall Admin, specify the client settings according to your requirements.
Connectivity Options
Socket Connect Timeout – Duration in seconds that a login attempt can last until it is stopped due to failure and an error message is displayed (Default: 6.
Configuration Read Timeout – Duration in seconds that a connection attempt (with the Connect button) can last after a failure until it is stopped and an error message is displayed (default: 30 seconds). In addition, this setting also determines the read timeout of the configuration file on the Box Control > Licenses page. For more information, see Licensing.
Statistic Timeout – Duration in seconds that a statistic view attempt can last until the attempt is stopped and an error message is displayed (Default: 30 seconds). Increase this setting if you expect large statistics files.
Max. Automatic Reconnects – The maximum time Firewall Admin automatically reconnects after a session has been interrupted, e.g., in case of connection attempts during updates.
Cryptography
Click Advanced Cryptographic Settings to edit the following advanced crypto API settings:
Disable Smartcard /Token – Selecting this check box deactivates the advanced cryptographic API settings.
Cryptographic Service Provider – Barracuda Networks supports all cryptographic service providers (CSPs) using the Microsoft crypto API. All CSPs installed on your local workstation are listed.
Key Length – The key length depends on the selected CSP. Minimum, maximum, and default values for key lengths are displayed in the Cryptographic Service Provider list.
Default Store – The default store for certificates (defaults to MY).
Specifies the provider type – Location of the certificate. You can select one of the following settings:
CERT_STORE_PROV_SYSTEM – Certificate available in MS Management Console.
CERT_STORE_PROV_PHYSICAL – Certificate available on eToken/Smartcard.
Flags – Availability of the certificate. Possible values are 'current user only' or 'local workstation', regardless of the logged-in user. You can select one of the following settings:
CERT_SYSTEM_STORE_CURRENT_USE – The certificate is dedicated to this user only.
CERT_SYSTEM_STORE_LOCAL_MACHINE – The certificate is dedicated to the local workstation.
Select Smartcard Reader – If smartcard readers are available, you can select one from this list. If the list is inactive, there are no smartcard readers available.
System
Disable Events System Tray Icon – To disable the icon in the system tray that indicates an active event, select this check box.
Switch tab title order – To invert the labeling of opened tabs, select this check box. Either the system name or the system IP address will be on top.
Print Header – In this field, you can enter a custom header for prints. A header is especially useful for identifying owners when multiple administrators use one printer.
Authentication
Always use Session Password (recommended) – To always use the last-known password when reconnecting to a system after a session has been disconnected, select this check box. The password is only saved until you close Firewall Admin.
All Administrators use One Time Passwords – Forces administrators to always use a one-time password instead of a session password. In an HA setup, the OTP must always be entered a second time for the secondary HA box.
Administrators using One Time Passwords (blank-separated) – Enter a list of blank-character separated administrator names that must authenticate using a one-time password.
Date Format
Specifies how the date and time are formatted in various overview listings (for example, CC Control).
Configuration Settings
Advanced Mode Configuration – To activate Advanced Configuration Mode throughout the client, select this check box.
Enable Configuration Scripting – To enable the functionality to script the configuration, select this check box.
Read Only Colour – To define the background color for configuration files in read-only mode, click Read Only Colour.
FW Rule Editor
Maximum number of network objects to fill into source and destination Combo Box – Defines the maximum number of network objects to be listed for Source and Destination when creating firewall rules. You can leave this setting as default.
Double Click to use Rule Dialog instead of Inplace Edit – Switch between in-place editing and opening the Rule Editor when double-clicking inside a cell in the rule list.
Firewall Live
Session Limit in Firewall Live view (0 for no limit) – Sets the limit to the maximum number of sessions in Firewall LIVE by the given number.
Restore Defaults
Restore Dialog Positions, Restore List Columns, Restore Config Element Sizes – To restore default settings, click the corresponding button.
Custom IP Lookup Link
Disable Custom IP Lookup Link in Firewall Live and History. Takes effect with next opened session! – To disable the custom IP lookup link in the Firewall > Live and History view, select this check box.
IPv4 Lookup URL – In this section, you can enter an HTTP/S URL to perform a custom IP address lookup (for example whatismyipaddress.com). By default, IP addresses are looked up at https://db-ip.com/ .
<ipv4 addr> – The IPv4 address.
External SSH Client
Command to open SSH-Client – In this field, enter the command to open the SSH client. Use %IP address and %user to dynamically insert IP addresses and login names. Format: 'path' parameters. e.g., 'C:\putty.exe' %user@%IP address.
Printing
Anonymize IP Addresses on Printing – When selecting this check box, IP addresses are anonymized by replacing the last 4 digits with xxx. E.g., 80.90.100.xxx when printing lists.
Log in
Save session information – Save the IP address in the recent connection section of the login page.
Save user name – Save the username last used to log into the IP address with the recent connection information.
Import recent sessions – Click to import recently accessed firewalls and Control Centers from the registry.
Proxy Settings
Use Proxy Settings from Internet Explorer – When selected, the settings will be used from Internet Explorer.
Behavior on slow Connection
Do always automatic data refresh on activation and timer intervals – Forces data to be refreshed on activation and timer intervals.
Disable automatic data refresh for Box/CC Connections slower than
XXXLatency in ms – To display the keyboard navigation when you press Alt, select this check box. 'XXX' is a placeholder for any number between 0 and 999.
Keyboard Navigation
Disable Keyboard Navigation by <Alt> Key – Disables the keyboard navigation by pressing the ALT key.
Warning Messages
Show warning when closing the application and multiple tabs are open – When this check box is selected, Firewall Admin will display a window with a warning to the user that there are still tabs open in the main window.
Barracuda Activation
Expanding the Barracuda Activation drop-down menu lets you configure the settings for Barracuda Activation. The settings in this section control the behavior or completely disable the Barracuda Activation process.
Policy for Contact Information – From this drop-down list you can select the following options:
Do not store. Ask every time – Does not store customer information locally. For each license activation, the user information needs to be entered.
Store, but ask for confirmation – Stores customer information locally. The information does not need to be entered for each activation but needs to be confirmed instead.
Store and use always automatically – Stores customer information locally.
CC: Create PAR Files – When the check box is selected, no warning will be displayed on the creation of box PAR files without configured serial numbers.
License Expire Warning – The number of days left until the license expiration warning is shown.
Admin and CC Settings
When expanding the Admin and CC Settings section, you can change default display settings. You can also configure the password and key for administrators of a Firewall Control Center and stand-alone Barracuda CloudGen Firewall.
Show Expert Settings – Selecting this check box displays expert settings in the GUI. (Changing the expert setting is not recommended.)
Use Cluster Description as Cluster Name – Select this check box to hide the lower levels of a node in the configuration tree. Click the node to display the content again.
Configure Stand-Alone Barracuda CloudGen Firewall Admin Settings
To configure the administrator settings for a stand-alone Barracuda CloudGen Firewall:
Select Change Admin Credentials for Local Admin (Single Box).
In the Box IP Address field, enter the IP address of the firewall.
In the Change Administrator Password section, you can change the password.
In the Change Administrator Key section, you can change the keys.
Configure Barracuda Firewall Control Center Admin Settings
To configure the administrator settings for a Barracuda Firewall Control Center:
Select Change Admin Credentials for CC Admin.
In the CC Selection section, select the Firewall Control Center. In the Address field, the IP address of the system appears.
To view the certificate for the system, click Show Certificate.
In the Change Administrator Password section, you can change the password.
In the Change Administrator Key section, you can change the keys.
Certificates and Private Keys
This drop-down menu contains the private key administration. Login and authentication of the administrator on a CloudGen Firewall are processed using a two-factor authentication technique. The authenticity of the admin workstation is verified using a challenge-response method. In addition to this, administrators must authenticate themselves using a personal password.
Creating a Certificate
In order to generate a new certificate/key by using Microsoft Strong Cryptographic Provider v1.0, click Create New Certificate/Key. This opens a window requiring several values to be entered. After confirming your entry, the new certificate will be displayed in the list. The columns within the main tab derive from the information entered while creating the certificate. However, two columns differ:
Hash - Contains short information concerning the key in order to make it easier to verify whether keys are equal.
Key Container - Displays the unique name of the CSP key container.
To delete a certificate, select the required certificate in the list and click Delete Certificate/Key.
Using Keys on a Barracuda CloudGen Firewall
Keys in PEM format cannot be used on CloudGen Firewall systems. However, Firewall Admin enables the conversion of already-existing keys into certificates. If you have older keys sitting in your registry, Firewall Admin provides an additional button within this dialog named Migrate Keys to Cert. Click this button to open a password request for the available keys. After entering the proper password, the keys are converted into certificates. The subsequent dialog (Registry Keys converted to Microsoft Certificate Management - Remove Registry Keys?) offers two options:
Yes – Removes the keys in PEM format from the registry.
No – Keeps the keys in PEM format in the registry.
Public Host Keys
When expanding the Public Host Keys drop-down field, the following sections are available:
Public Keys
This section shows all firewalls that were previously accessed using this computer. The list includes the box IP address, a short hash of the key, and the unique box fingerprint. Use the Remove Selected option for deleting a selected entry from the list. A security request will pop up the next time you log into the box. The Import PEM option allows you to import PEM files. Security is increased by using certificates in this place, at the same time a security request is avoided.
SSH Keys
This section shows all firewalls that were previously accessed using an SSH connection from this computer. The list includes the SSH IP address and the unique SSH fingerprint. In addition to the Remove Selected and Import PEM options (both having the same purpose as described above), the Enter Finger Print option is also available here. Click to enter the unique fingerprint and the corresponding IP address manually into a dialog box.
Barracuda Firewall Admin Maintenance
This drop-down menu offers you an option to install the currently running instance of Firewall Admin into the so-called Global Assembly Cache (GAC), to uninstall it again from there, and to delete further instances that have been detected on the workstation. Usually, there is no need to install Firewall Admin because the executable can simply be copied to and executed on a workstation, thereby fulfilling the hardware and OS requirements without requiring any further preparations.
