Some network environments require higher security levels to authenticate users when they access specific high-risk resources. YubiKey offers an effective method to additionally protect your company network from unwanted access. The tool, when enrolled and configured, adds an additional layer of authentication and works as part of an MFA process, based on a security token. All the end user has to do in order to access a resource is enter their self-configured pin during the authentication process and then touch the YubiKey inserted into their device. To configure YubiKey authentication for CloudGen Firewall administrators, follow the instructions in this guide.
Before You Begin
Before implementing YubiKey in your network, consider the following steps:
Determine the users / user groups who should receive a YubiKey for authentication.
Distribute YubiKeys to the intended user group.
Download and install YubiKey Manager. You can manage certificates via YubiKey Manager > PIV and import them into the Firewall Control Center.
Download YubiKey Manager: Go to https://www.yubico.com/support/download/yubikey-manager and select the applicable version under Downloads.
Install YubiKey Manager on your operating system.
Set Up a YubiKey Certificate
Launch YubiKey Manager on your desktop.
Click Applications and select PIV.
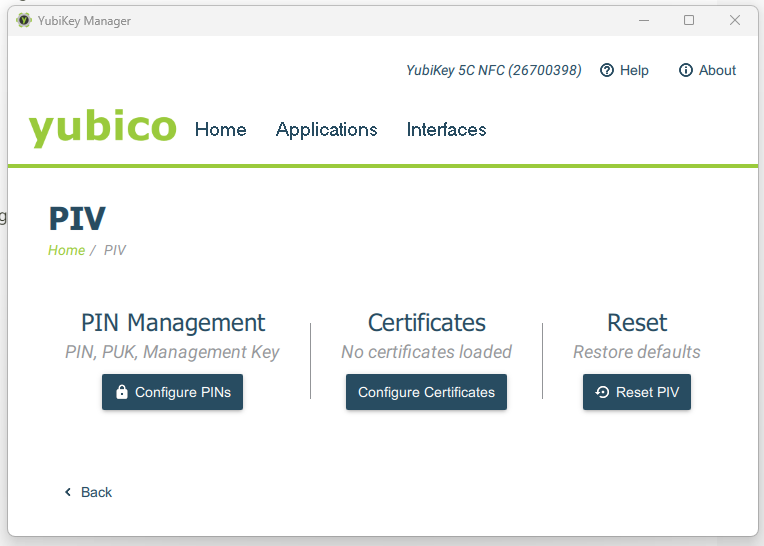
Select Configure Certificates.
Select Key Management, and click Generate to create the certificate.
Select Self-signed certificate.
Adjust the settings according to your requirements and click Generate.
Define a management key, or select Use default, and enter the PIN provided by YubiKey.
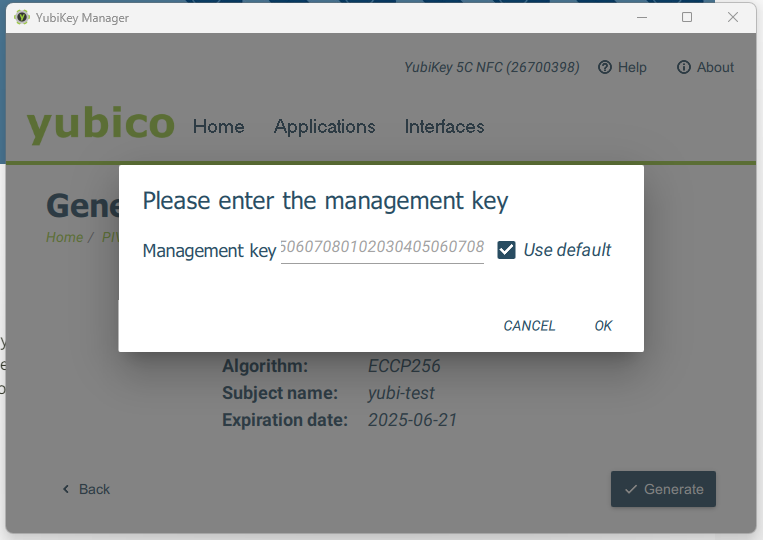
Generate the certificate.
You can now import this certificate on your Barracuda CloudGen Firewall.
Install the YubiKey Certificate on the Firewall
Log into the Barracuda CloudGen Firewall as CC- or box administrator and import the YubiKey certificate using Barracuda Firewall Admin.
Go to CONFIGURATION > Configuration Tree > Box > Administrative Settings.
From the Configuration Mode menu, select Switch to Advanced View.
In the left navigation pane, click Advanced System Access.
Click Lock.
Next to Root Public RSA, click Ex/Import.
Select Import from Microsoft Certificate Management.
The Certificate Selector window opens.
From the Current Store drop-down list, select MY.
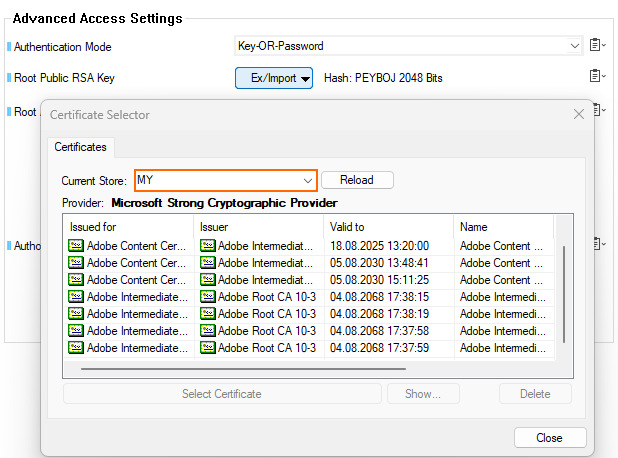
Locate your YubiKey certificate in the list and select the entry.
Click Select Certificate to import the certificate.
Click Send Changes and Activate.
You can now enroll yourself for YubiKey authentication on the Barracuda CloudGen Firewall.
Enrolling YubiKey in Your Network
To configure YubiKey on end user devices, make sure a YubiKey certificate is installed for the user. The following example explains how to add YubiKey as an additional authentication layer.
Log into the My Sign-Ins portal: https://mysignins.microsoft.com/security-info
Select + Add sign-in method.
From drop down, select Security key.
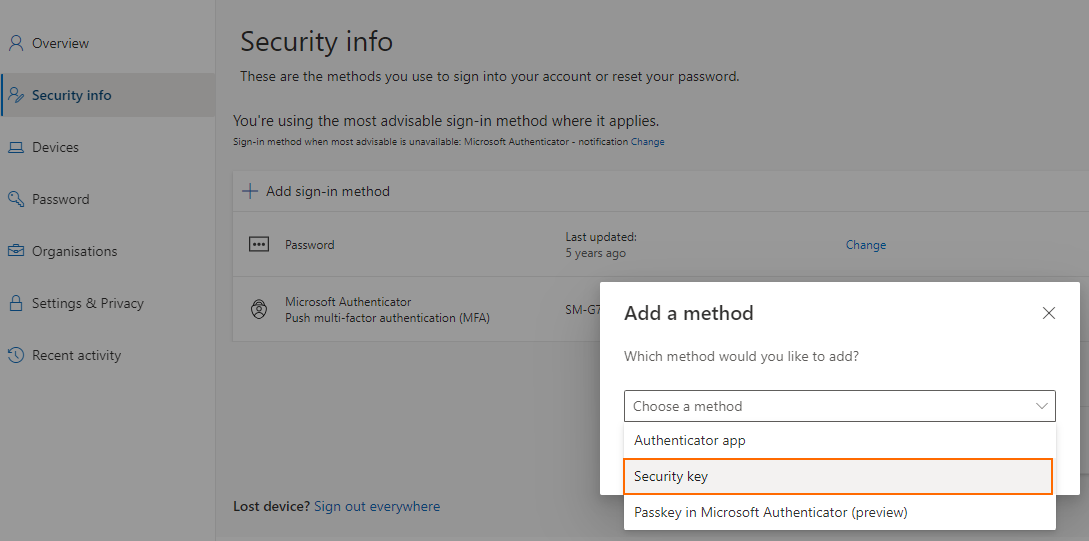
Click Add.
As Security key type, select USB device.
You will be prompted to have your key ready, click Next. You will be redirected to a new window to complete setup.
Beneath the QR code that appears, select Use a different device.
When prompted to Create a passkey, select USB security key.
Plug in your YubiKey and then touch the logo circle.
Set up a new PIN. A PIN may be as simple as a 4-digit numeric value. Choose a strong and memorable value that includes both letters and digits. The PIN should be distinct, and should not be a password that is reused on any site or service.
When prompted, touch the logo circle on your YubiKey again to complete the request.
When prompted with Allow this site to see your security key?, select Allow.
When prompted to Set up a security key, sign in with two-factor authentication, select Next.
Choose USB device at the next prompt.
You will be asked to name your security key.
After setting your name, you can now close the window. You will now see your security key listed underneath Security info.
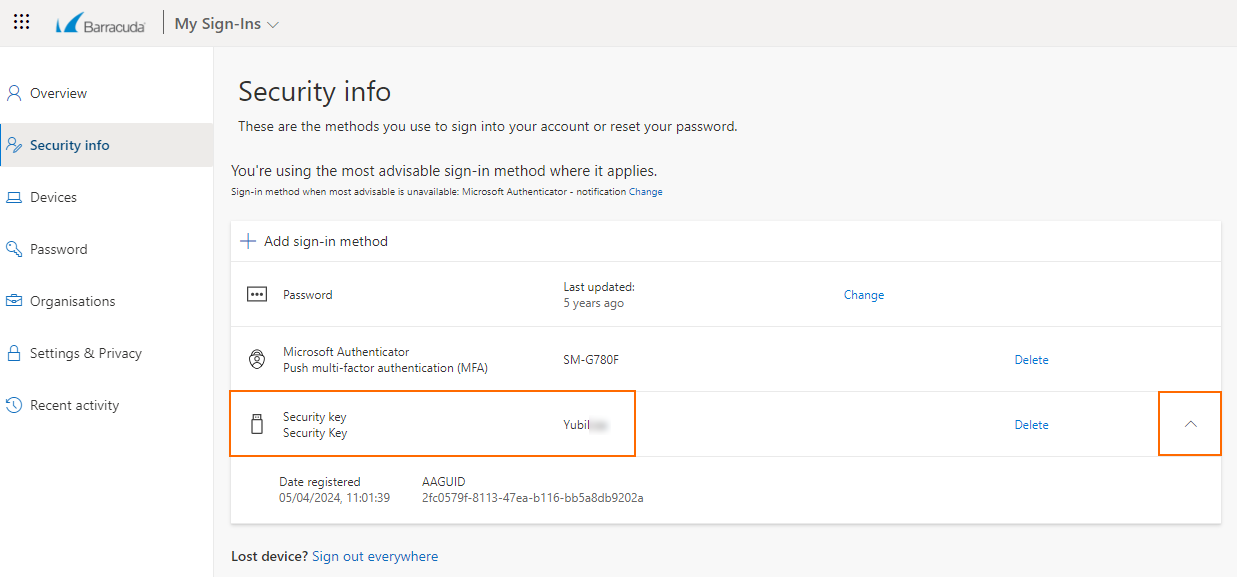
To authenticate using YubiKey, go to the security settings of a supported service and select two-factor authentication. When prompted, insert the YubiKey into a port on your device and touch it.
To configure FIDO2, OTP, and PIV on your YubiKey, use the YubiKey Manager. For more information, see https://www.yubico.com/support/download/yubikey-manager/
