The Barracuda Log Analytics Daemon allows streaming logs from the Barracuda CloudGen Firewall or Control Center to an Azure Log Analytics Workspace. The daemon supports all CloudGen appliances: Cloud, virtual, and hardware boxes, all starting with firmware version 9.0.4.
The Barracuda Log Analystics Daemon provides the same functionality as its deprecated predecessors and therefore replaces the OMS Agent and the Azure Monitor Agent. Thus, third-party extensions no longer have to be installed, and on-premise boxes no longer must be imported into Azure.
Data Formats for Syslog Streaming
By using the syslog format, the Barracuda Log Analytics Daemon streams all CGF/CGCC logs to the Azure Log Analytics syslog table. Alternatively, a few logs can be streamed to the Azure Common Security Log table using the common event format (CEF).
Data Categories Streamed to Azure Log Analytics
You can stream all logs using the syslog format.
The only two logs that a CloudGen firewall can stream in CEF format are:
Firewall Activity Log
Firewall Threat Log
In this example, the following data categories will be streamed to Azure Log Analytics for the Firewall Activity Log and the Firewall Threat Log:
Firewall Activity Log
Action taken
Source IP
Source port
Destination IP
Destination port
Firewall Threat Log
Threat description
Action taken
Source IP
Destination IP
Destination port
Protocol
User name
Each of these streams is related to certain event IDs:
Log File Type | Log File (on file-system) | Event ID |
|---|---|---|
Firewall Activity Log | box_Firewall_activity.log | 100 |
Firewall Threat Log | box_Firewall_threat.log | 200 |
The Barracuda Log Analytics Daemon uses the Azure log ingestion API. For this, one or more data collection rule(s) must be configured in the same region as the target Log Analytics Workspace.
Templates
Barracuda provides ARM templates that can be used to create the necessary data collection rule(s).
For the syslog, download the template (
bn-azure-log-analytics-dcr-syslog.json):
For the security log table, download the template (
bn-azure-log-analytics-dcr-cef.json):
Create Data Collection Rules
Data collection rules are required both for each log analytics workspace and for streaming the logs to the syslog and the common security log tables. Note that alongside each data collection rule, a data collection endpoint is also created.
For creating data collection rules, you have two options:
Option #1: To create data collection rules via the Azure UI, perform the following steps:
To stream the logs in the common event format (CEF), Azure Sentinel must be added to the corresponding Log Analytics Workspace.
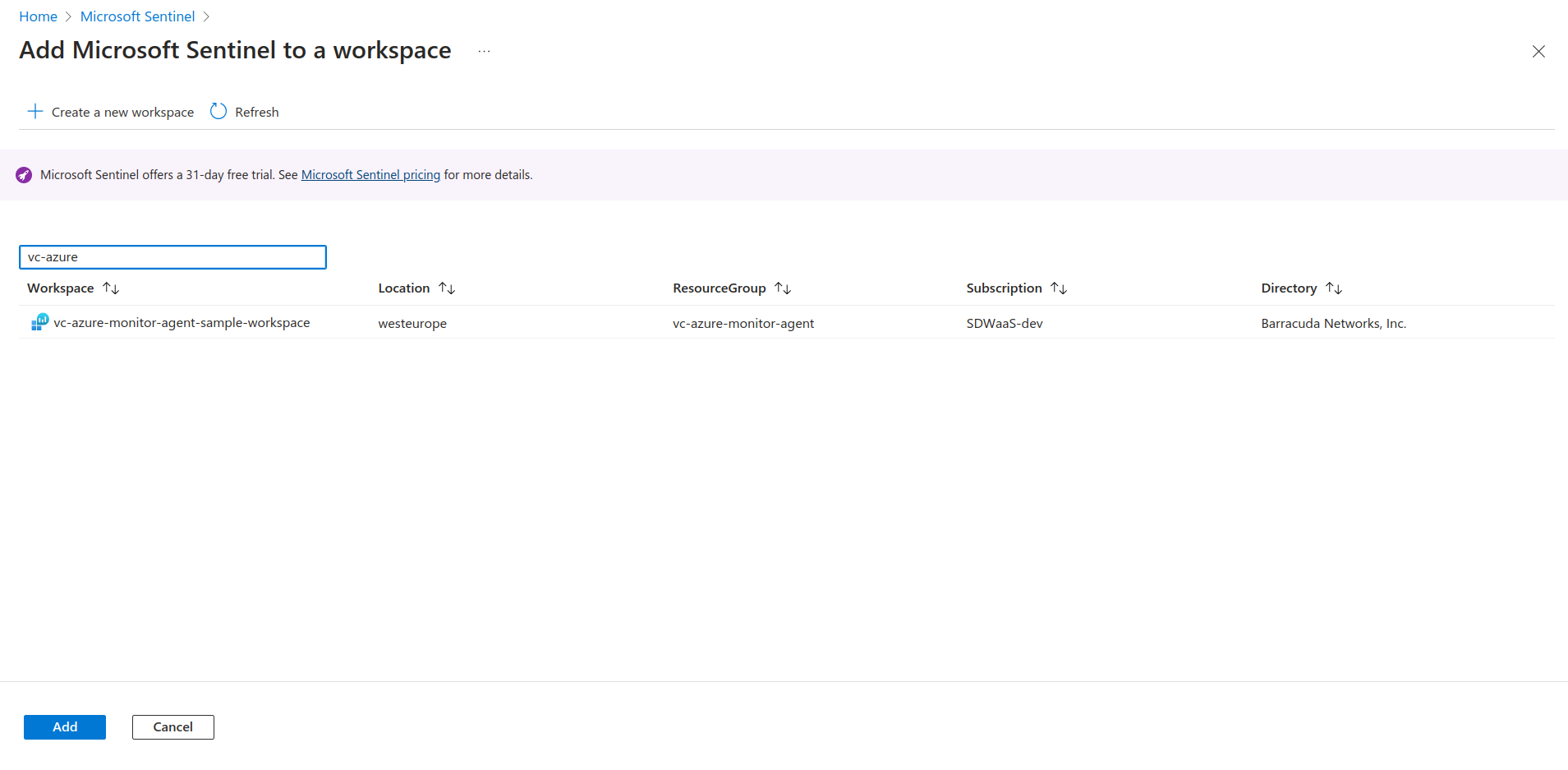
Ensure that you have downloaded the required templates.
Unless you have done so, expand the two forms in the paragraph templates and save the code-content of each template into a separate file with the mentioned filename.
Open the Azure Web Portal, search for “Deploy a custom template” in the search bar at the top of the page, and open the corresponding page.
On the “Custom deployment” page that opens, select Build your own template in the editor.
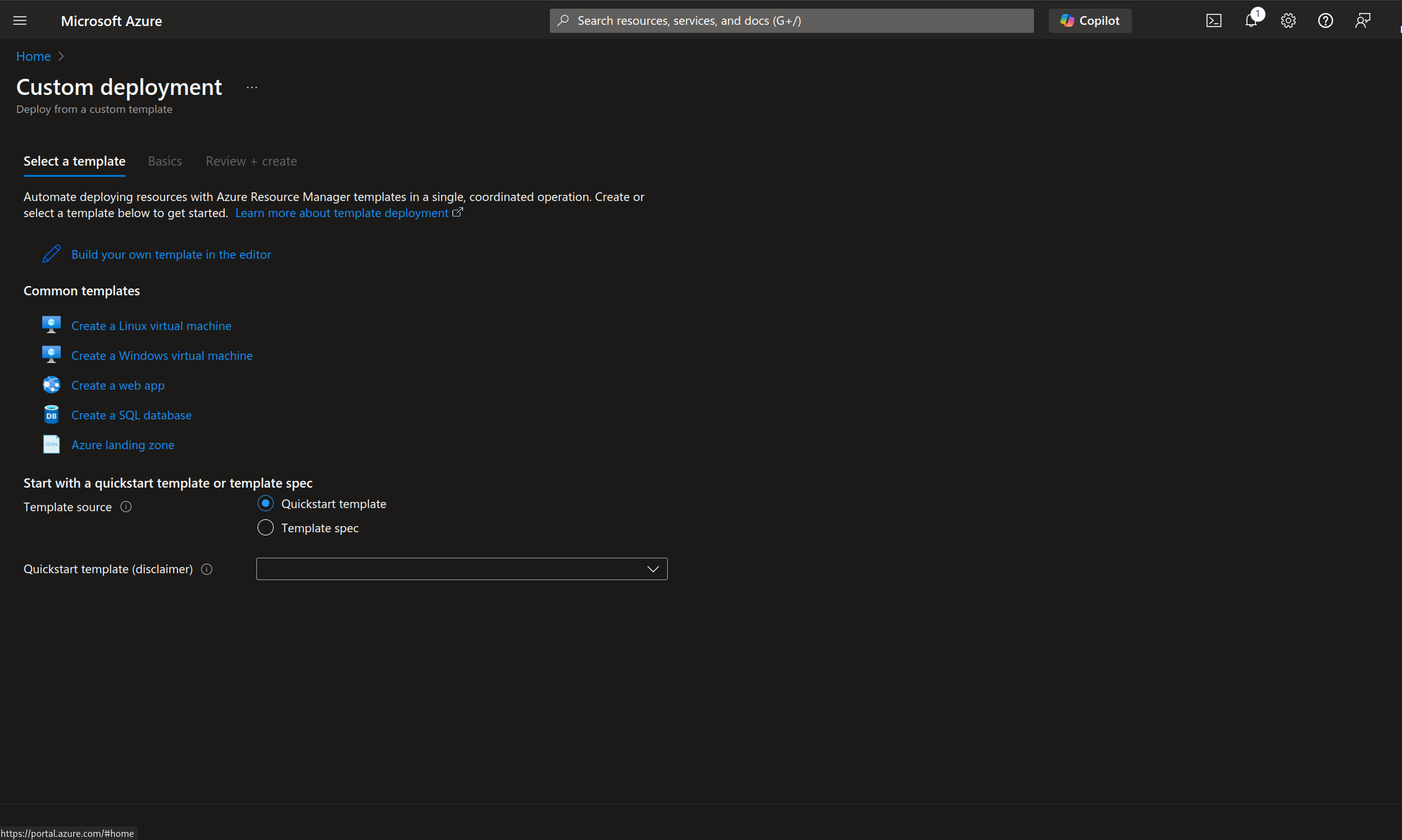
Replace the sample template in the editor with the contents of the template that you saved before and which you want to deploy.
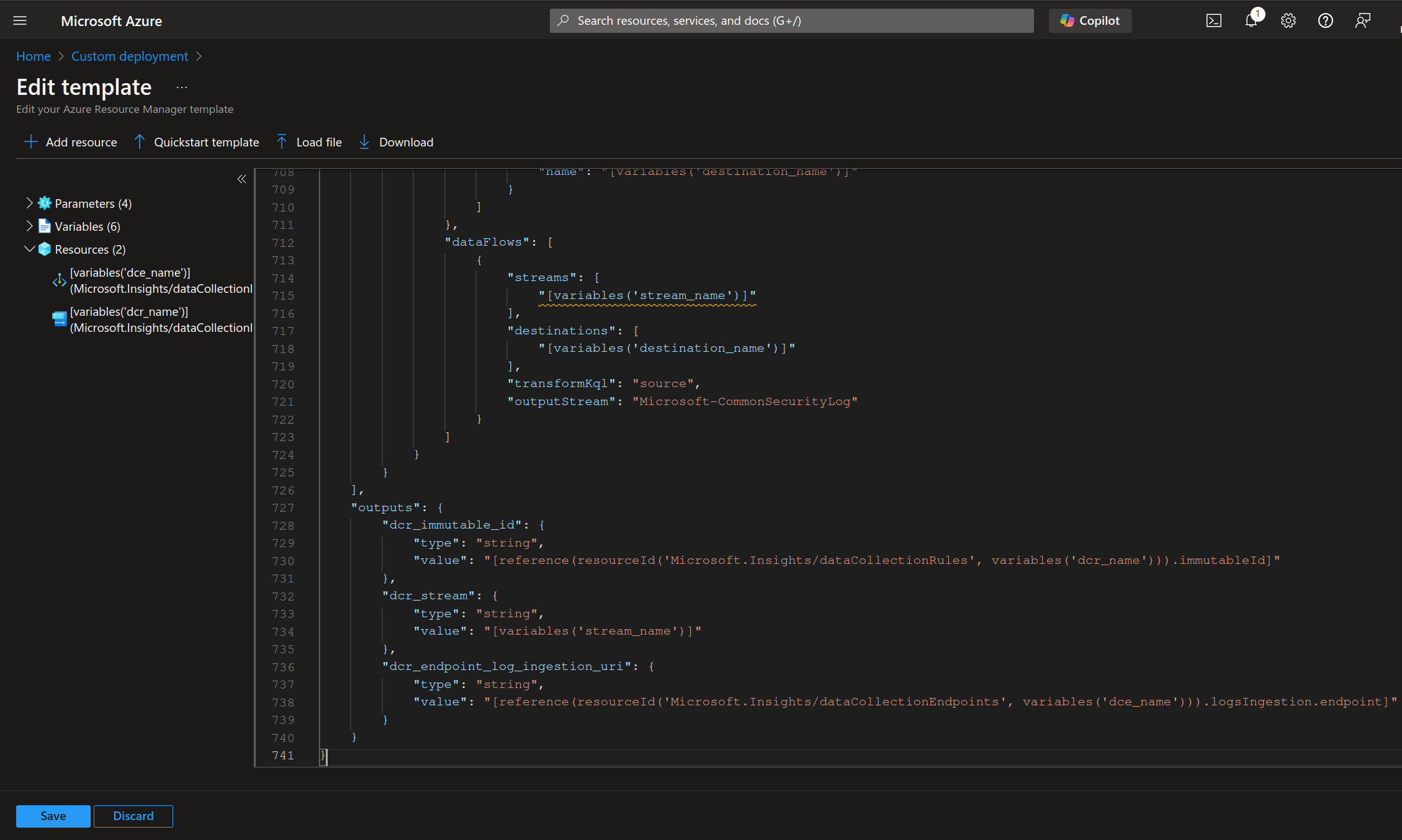
Save the template and fill in the parameters for the deployment.
The following options are mandatory:
Subscription ID
Resource Group
Region
Log analytics Workspace_name
Log analytics Workspace_id
If you chose to deploy into a different resource group as the one containing the log analytics workspace:
Workspace_resource_group
If you deploy into a resource group differing from the one containing the log analytics workspace, and if the resource group is also in a different region, you must specify the log analytics workspace region:
Workspace_region
Click Review + create and run the deployment.
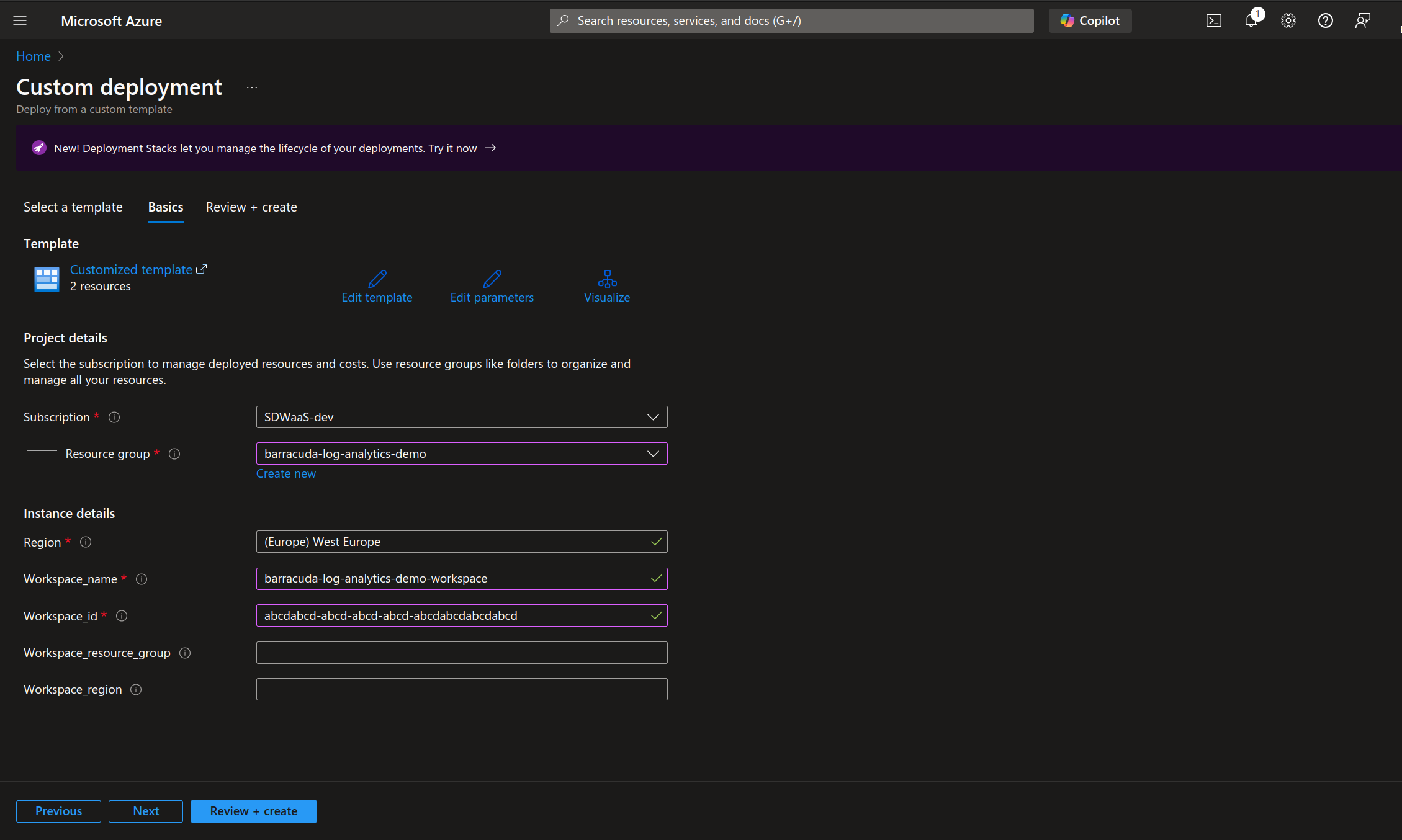
As soon as the deployment is finished, click Outputs in the left column to open the Outputs page.
Because you will need certain values later, write them down from the following edit fields:
dcr_immutable_id
dcr_stream
dcr_endpoint_log_ingestion_uri
Option #2: To create data collection rules via Powershell or CLI, perform the following steps:
Sample command for deploying via PowerShell:
New-AzResourceGroupDeployment -TemplateFile <path_to_template_file> -ResourceGroupName <resource_group_to_deploy_into> -workspace_name <target_log_analytics_ws_name> -workspace_id <target_log_analytics_ws_id> -workspace_resource_group <target_log_analytics_ws_resource_group> -workspace_region <target_log_analytics_ws_region>Sample command for deploying via CLI:
$ az deployment group create --template-file <path_to_template_file> -g <resource_group_to_deploy_into> --parameters workspace_name=<target_log_analytics_ws_name> --parameters workspace_id=<target_log_analytics_ws_id> --parameters workspace_resource_group=<target_log_analytics_ws_resource_group> --parameters workspace_region=<target_log_analytics_ws_region>Configure Streaming in Barracuda Firewall Admin
The syslog streaming configuration is the same as for the Common Security Log tables, except that the log destination is Azure Log Analytics Syslog via CGF Log Daemon.
The following example relates to the configuration for the Common Security Log tables and only covers a smaller subset of the logs.
URL | Note |
|---|---|
https://login.microsoftonline.com/<tenant_id>/oauth2/v2.0/token | Required for authentication. |
<endpoint_logs_ingestion_url>/dataCollectionRules/<dcr_immutable_id>/streams/<stream_name> | Required for sending the log data as configured in the section "Create Data Collection Rules", step 9. above. |
To configure the Common Security Log tables, perform the following steps:
Log into Barracuda Firewall Admin.
Go to CONFIGURATION > Configuration Tree > Box > Infrastructure Services > Syslog Streaming.
In the navigation column, click Logdata Filters.
Click Lock.
Click '+'.
The window Filters is displayed.
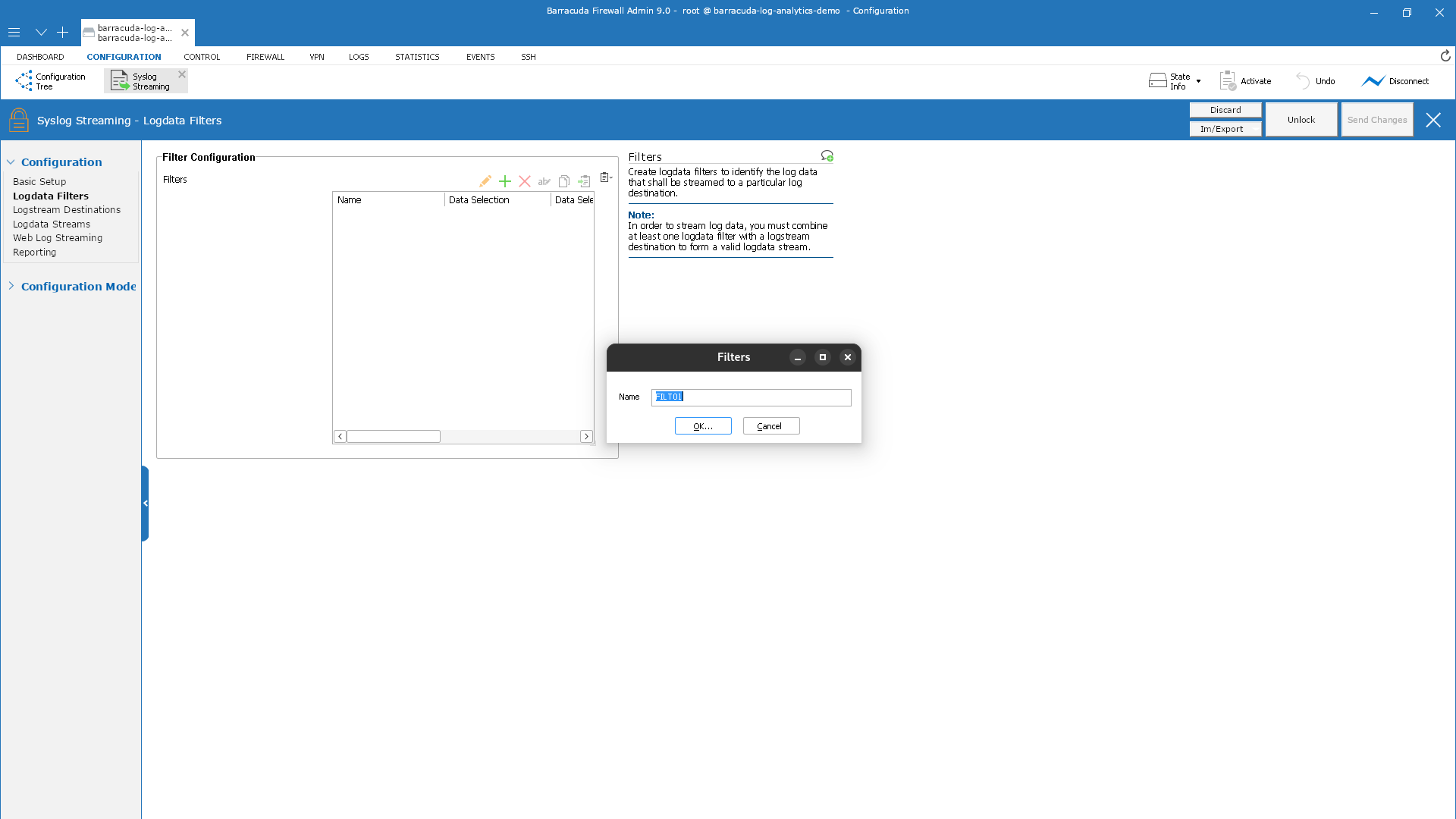
Enter the name of the filter.
Click OK… .
The window Filters is displayed.
In the section Affected Service Logdata, select None for Data Selector.
In the section Affected Box Logdata, select Selection for Data Selector.
Click '+'.
The Data Selection Window is displayed.
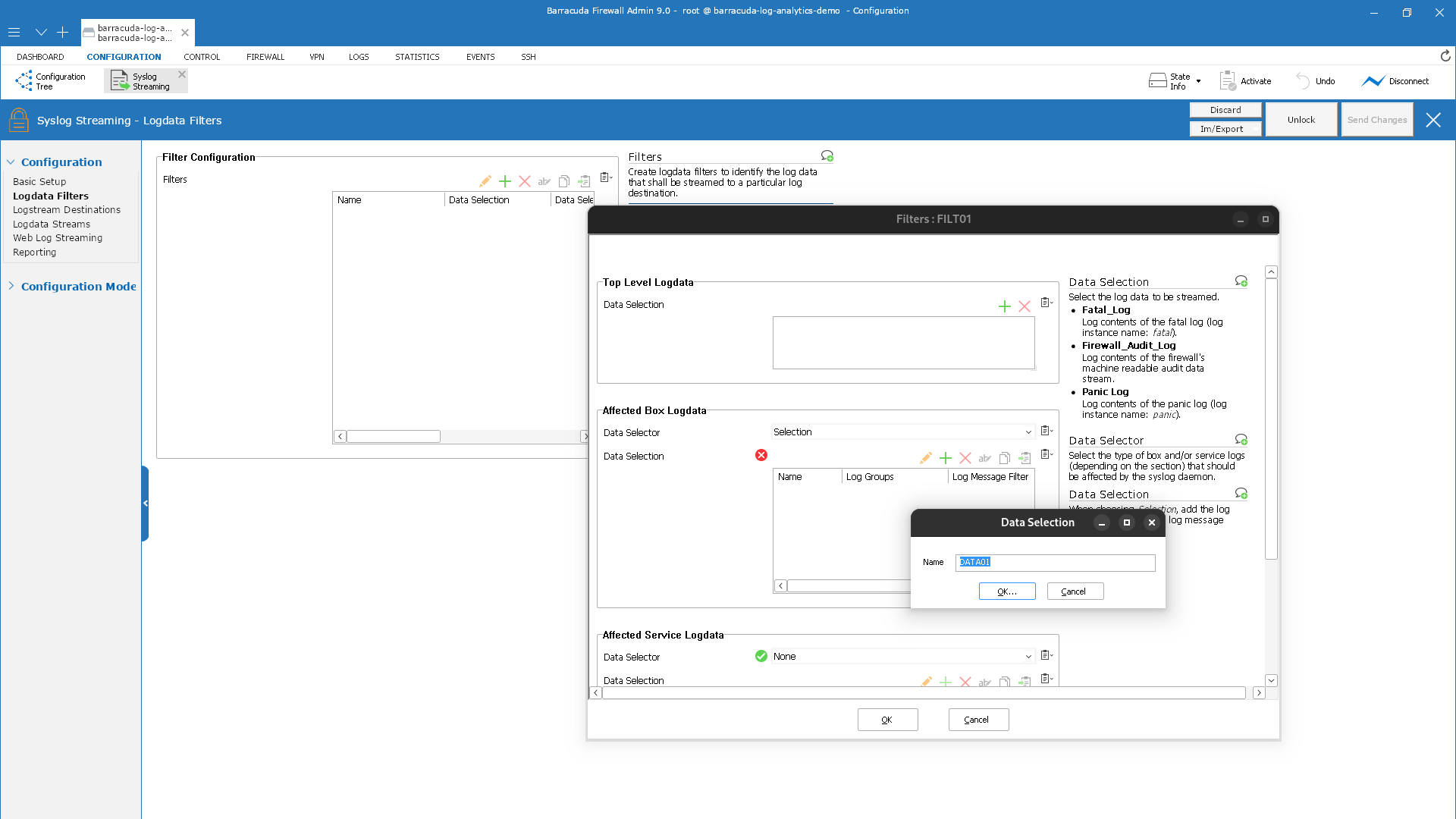
Enter the name for Data Selection.
The window Data Selection is displayed.
Click '+' for Log Groups.
Click the newly created line in the list.
Select Firewall-Activity-Only from the list.
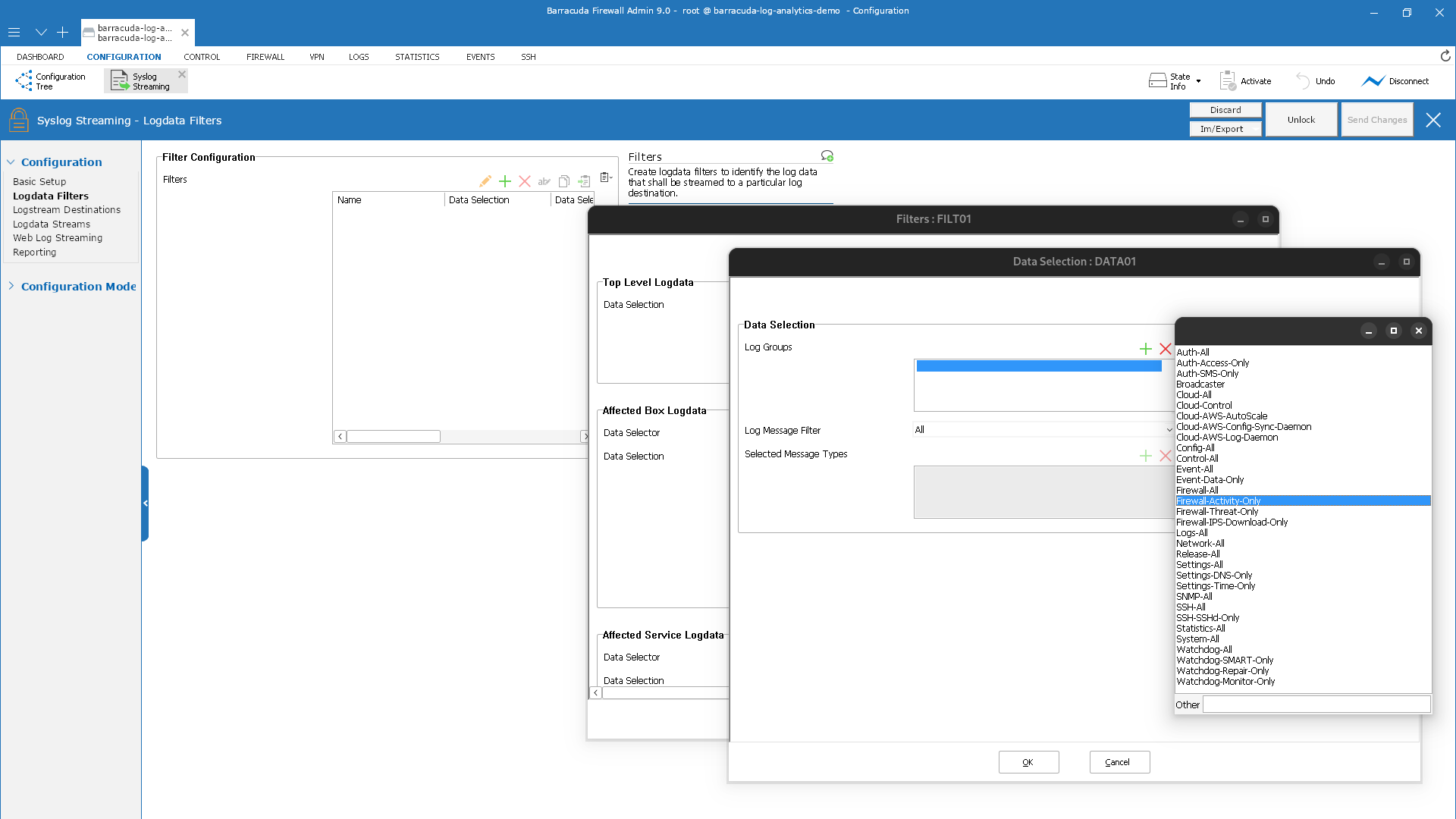
Repeat steps 10 - 18 and add another data selection log group for Firewall-Threat-Only.
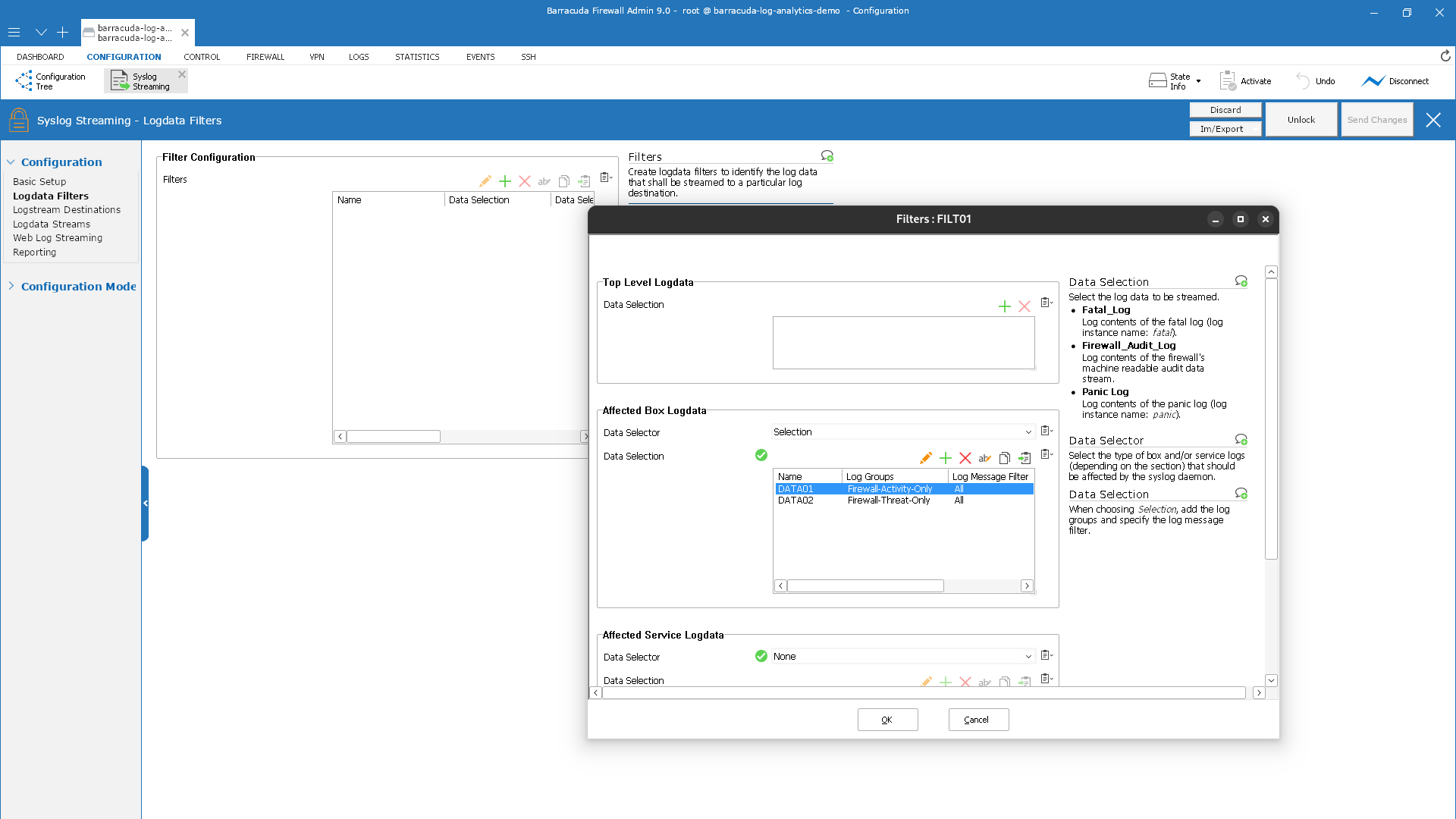
In the left navigation column, click Logstream Destinations.
In the Destination Configuration section, click '+'.
The Destinations window opens.
Enter the name for the destination.
Click OK… .
The Destination window is displayed.
In the Destination Address section, select Azure Log Analytics CEF via Log Daemon.
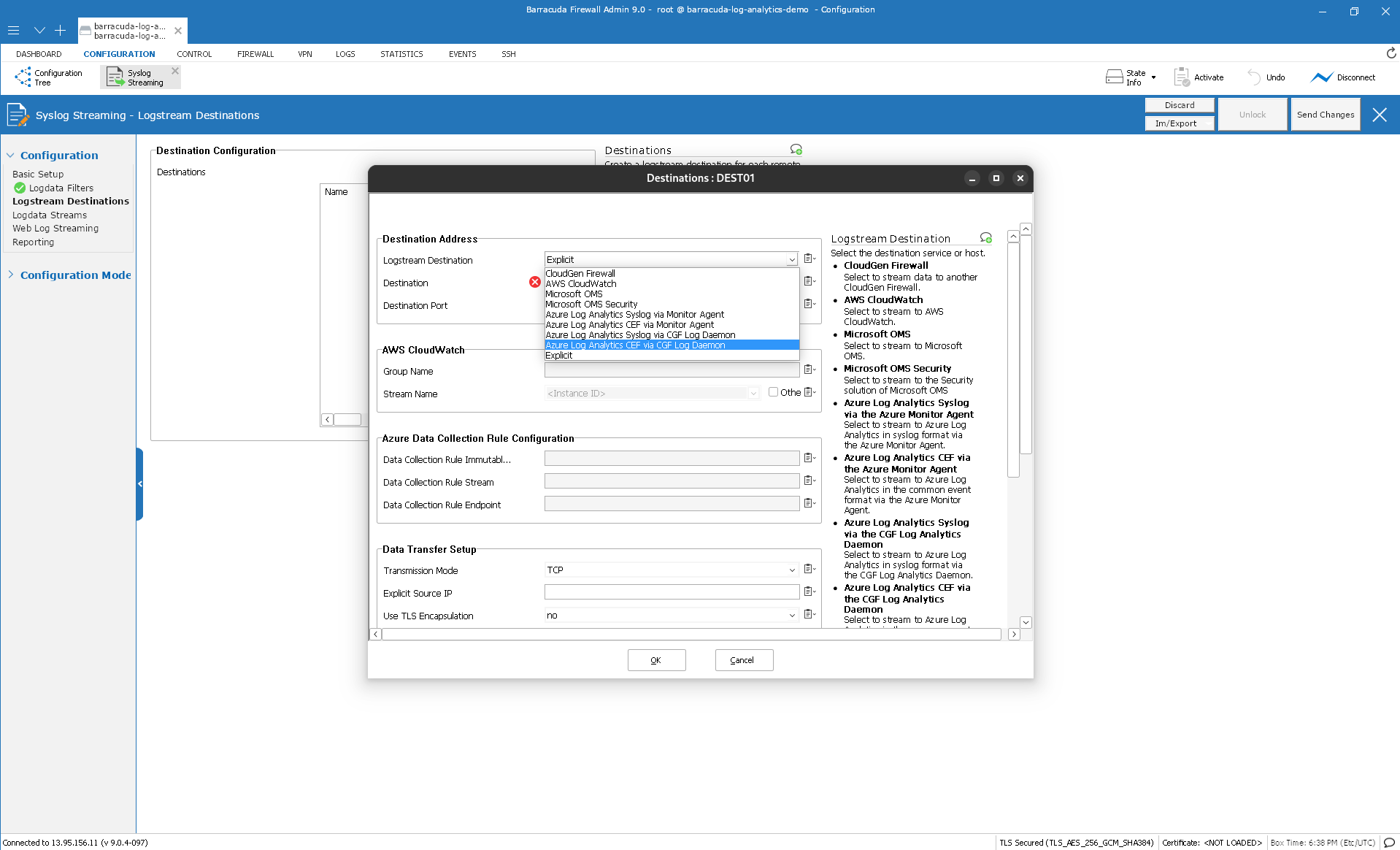
In the Azure Data Collection Rule Configuration section, enter the values from the MS-Template-Outputs in Step 9.
dcr_immutable_id
dcr_stream
dcr_endpoint_log_ingestion_uri
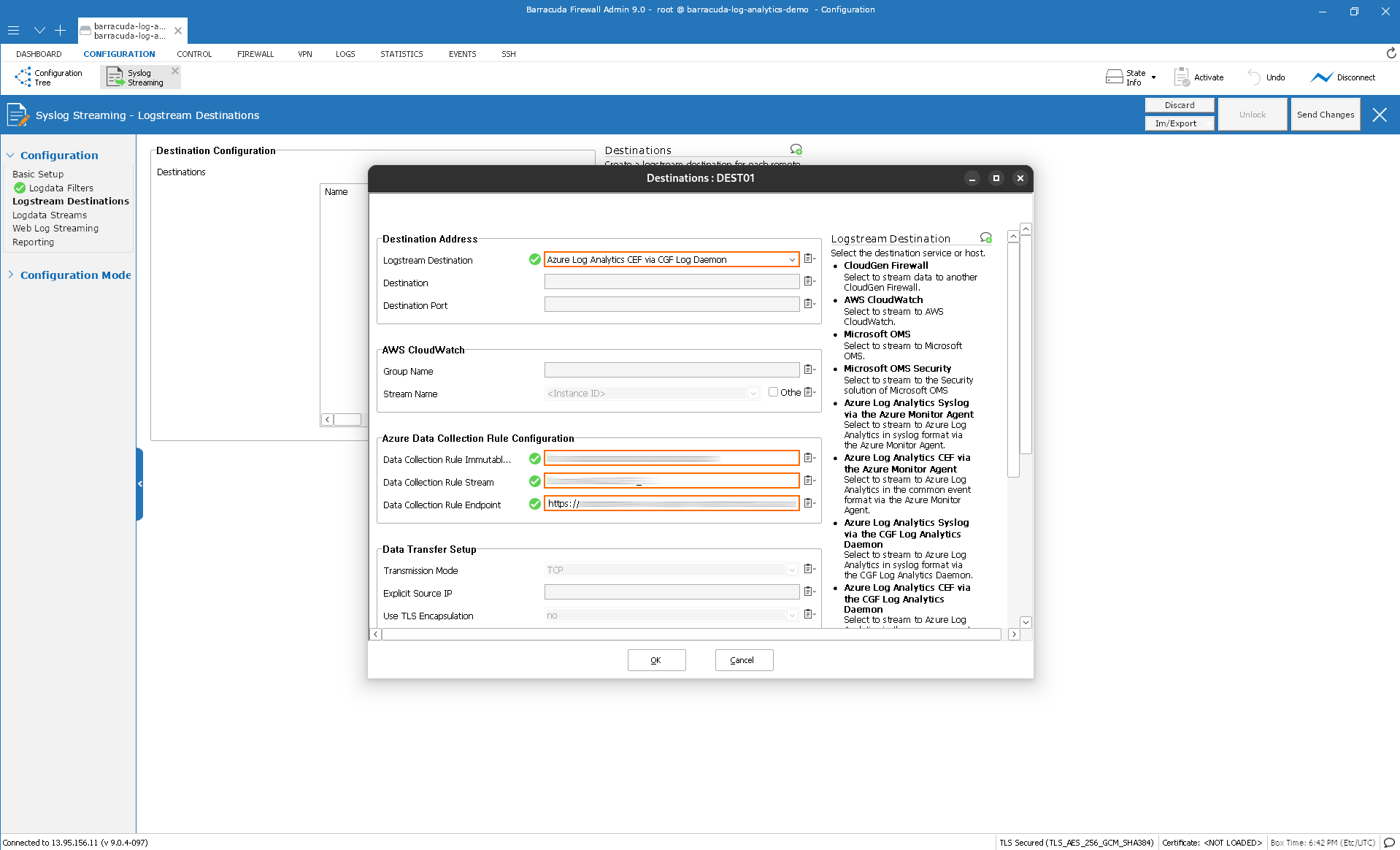
Click OK.
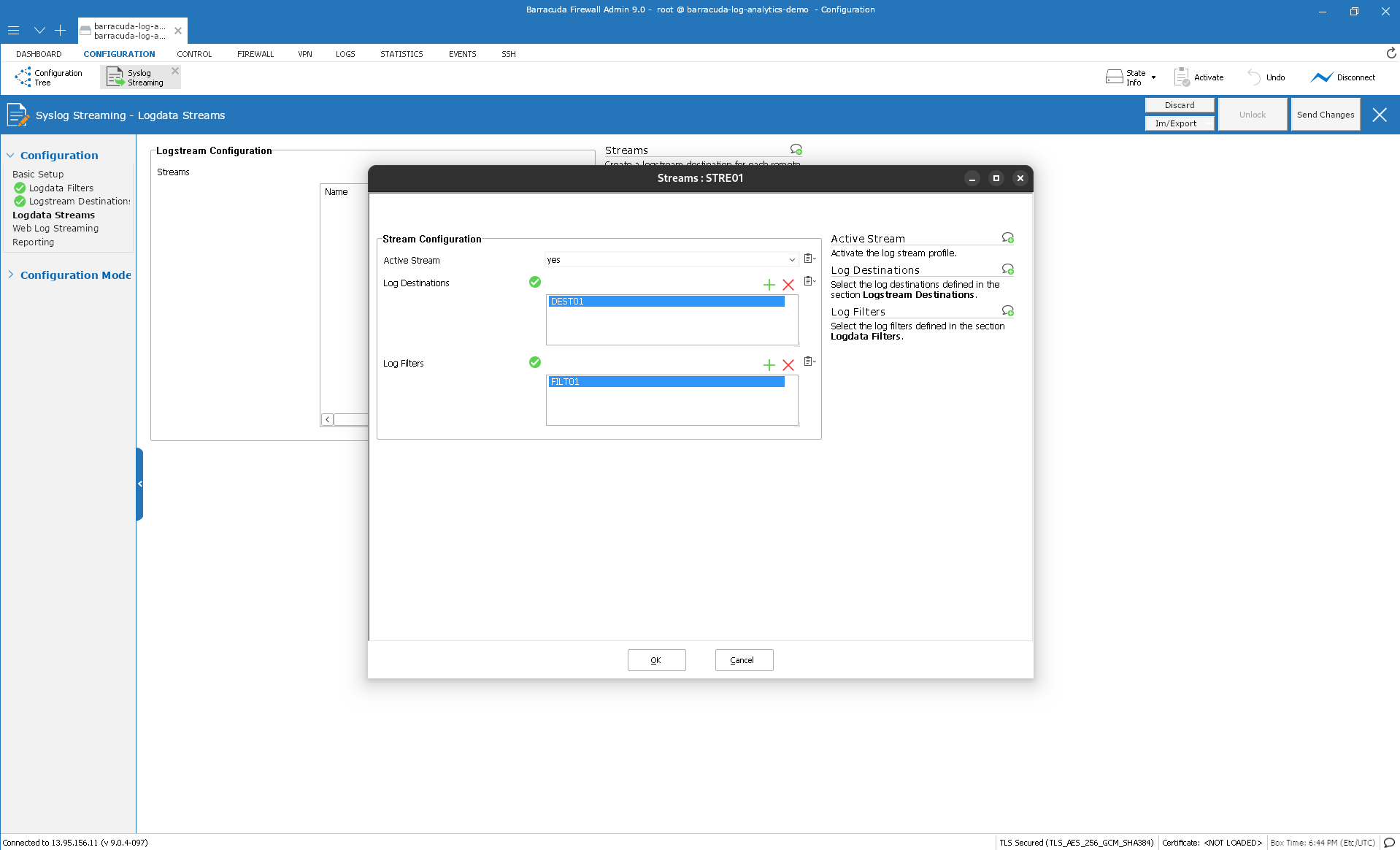
In the left menu column, click Logdata Streams to add a new stream.
In the section Logstream Configuration, click '+'.
The Streams window is displayed.
Enter the name for the new stream.
Click OK… .
The Streams window is displayed.
In the Stream Configuration section, ensure that yes is selected for Active Stream.
For Log Destinations, select Azure Log Analytics Syslog via CGF Log Daemon (analog to Step 26).
Select the required filters for Log Filters from the list.
Click OK and complete all configurations.
Finalize the configuration by clicking Send Changes/Activate.
Configure Authentication and Enable the Log Daemon
The Azure Log Analytics daemon requires a service principal that has the Monitoring Metrics Publisher role enabled for the Data Collection Rule(s) used to stream the logs.
To configure the credentials of this service principal, perform the following steps:
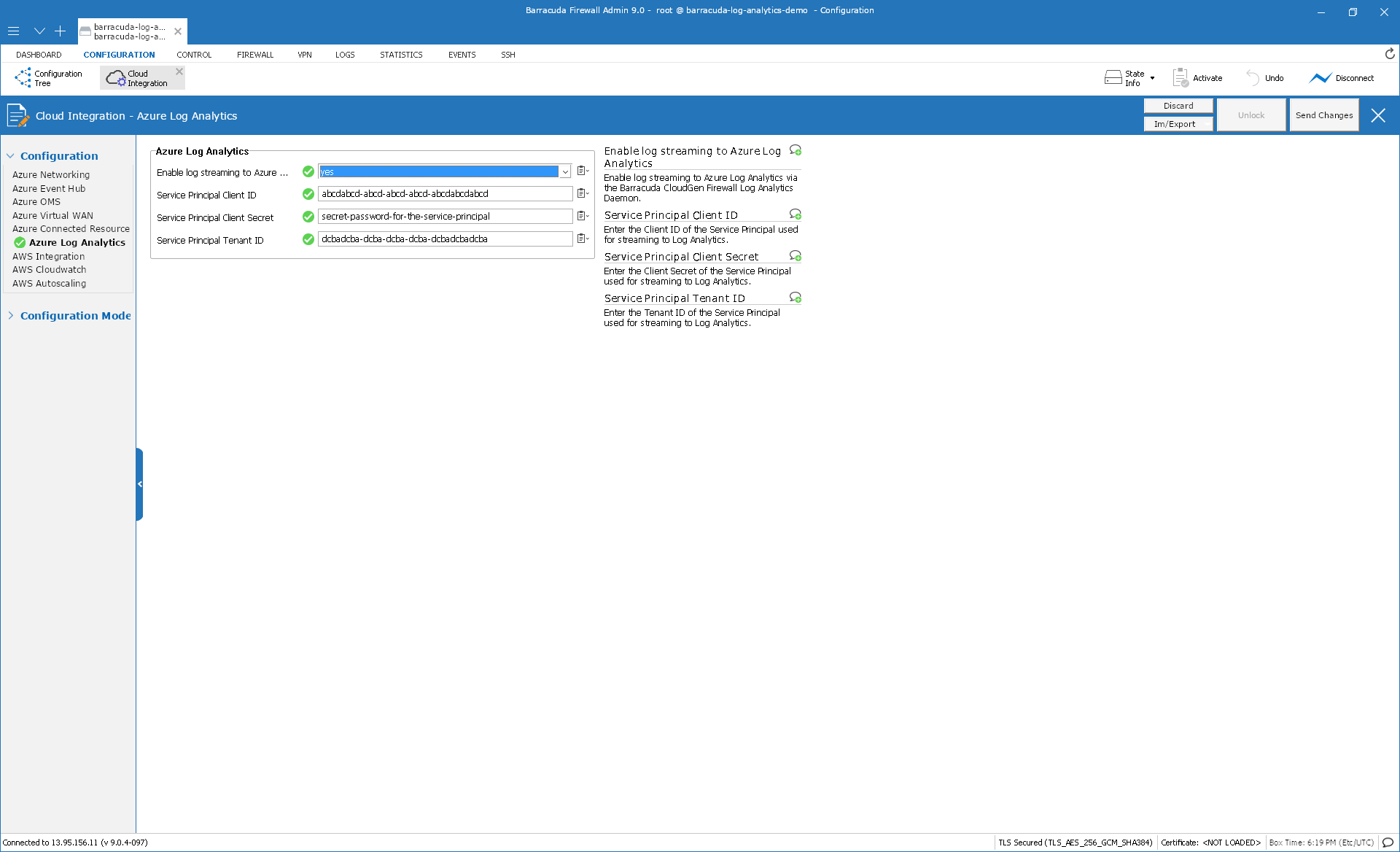
Go to CONFIGURATION > Configuration Tree > Box > Advanced Settings > Cloud Integration > Azure Log Analytics.
In the Azure Log Analytics section:
Enable log streaming to Azure – Select yes to enable streaming.
Enter the Service Principal Client ID.
Enter the Service Principal Client Secret.
Note that the Service Principal Client Secret in that section is the ID and not the value that must be entered when creating the secret for the service principal!Enter the Service Principal Tenant ID.
For more information on how to create a service principal in Azure, see https://learn.microsoft.com/en-us/entra/identity-platform/howto-create-service-principal-portal.
Configure Streaming in the General Firewall Configuration
Go to Configuration Tree > Infrastructure Services > General Firewall Configuration.
Click Lock.
In the left menu, select Audit and Reporting.
Under Log Policy, set the Activity Log Mode to Log-Pipe-Separated-Value-List.
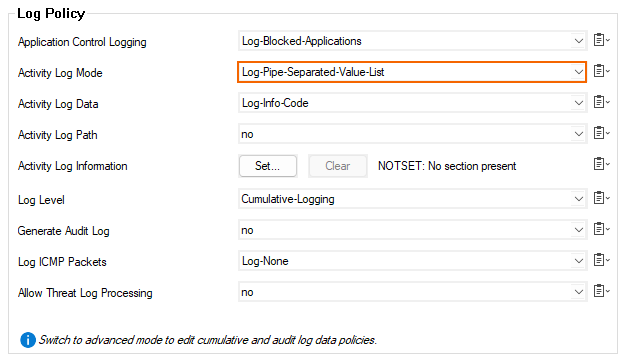
Click Send Changes and Activate.
Note: For streaming logs in syslog format, you can also chose Log-Pipe-Separated-Key-Value-List.
Example output: 2024 05 07 10:02:51 +00:00 Info Allow: type=LOUT|proto=TCP|srcIF=dhcp|srcIP=10.0.0.4|srcPort=47542|srcMAC=00:0d:3a:46:14:a3|dstIP=168.63.129.16|dstPort=32526|dstService=|dstIF=|rule=PASSALL|info=0|srcNAT=10.0.0.4|dstNAT=168.63.129.16|duration=0|count=1|receivedBytes=0|sentBytes=0|receivedPackets=0|sentPackets=0|user=|protocol=|application=|target=|content=|urlcat=
However, for streaming CEF logs (i.e. logs in Common Event Format), the logs must be simple, pipe-separated values since parsing is done for this format.
Example output: 2024 05 07 10:02:57 +00:00 Info Allow: LOUT|TCP|dhcp|10.0.0.4|33848|00:0d:3a:46:14:a3|168.63.129.16|80|http||PASSALL|0|10.0.0.4|168.63.129.16|0|1|0|0|0|0||||||
