Migrating the Old 3-Layer Server-Service Architecture to the New 2-Layer Assigned Services Architecture
With firmware version 8.0.5, you have the option to migrate the former 3-layer server-service architecture to the new 2-layer Assigned Services architecture. While this is optional in all 8.0.x releases, it will be mandatory in the next upcoming major release.
AutoVPN
For Barracuda-only environments, setting up a site-to-site VPN tunnel has been greatly improved. The new AutoVPN feature provides robust VPN connections through TINA tunnels that are automatically set up with dynamic routing between local networks. AutoVPN is suited for creating multiple boxes in the cloud and connecting them with a TINA site-to-site VPN tunnel.
The automatic setup of VPN tunnels is initiated via the command-line interface (CLI) and REST API.
For more information, see AutoVPN for CloudGen Firewall Devices 8.0.1 or Higher.
Barracuda Control Center License Activation
When a Control Center is started for the first time, the CC Wizard will prompt you to enter a username and a password that will be used to automatically download licenses.
For more information, see Getting Started - Control Center.
Barracuda Firewall Insights
The Barracuda Reporting Server has been replaced by Barracuda Firewall Insights. Barracuda Firewall Insights is an advanced reporting and analytics platform that ingests, aggregates, and analyzes data automatically from any CloudGen Firewall deployed across your organizational network, including public cloud deployments. Analytics by Firewall Insights provide actionable information for the entire WAN, including dynamic availability information on SD-WAN connections, transport data, security, and web and network traffic details.
For more information, see Firewall Insights.
Disk Encryption
To achieve higher protection for your data on your firewall, it is possible to encrypt the hard disk. For this, it is necessary to set a parameter in the corresponding configuration window of NGInstall and then re-install your firewall from scratch.
For more information, see How to Deploy a CloudGen Firewall Vx using Firewall Install on a VMware Hypervisor.
To download the newest version of NGInstall that includes the updates, go to https://dlportal.barracudanetworks.com/#/packages/5238/NGInstall_8.0.5-10.exe.
KTINA FIPS Crypto Module
FIPS 140-2 revalidation for the Barracuda KTINA FIPS Crypto Module is in progress with firmware version 8.0.5.
For more information, see https://csrc.nist.gov/Projects/cryptographic-module-validation-program/modules-in-process/Modules-In-Process-List.
Along with the Barracuda Cryptographic Software Module, the VPN server will be FIPS 140-2 compliant again.
For more information, see https://csrc.nist.gov/projects/cryptographic-module-validation-program/certificate/2458.
IPv6 for Client-to-Site Payload
Client-to-Site VPN TINA tunnels now support the configuration of IPv6 client networks.
Microsoft Azure Market Place Improvements
The Microsoft Azure Marketplace supports the deployment of High Availability clusters. High Availability ensures that the services running on the CloudGen Firewall are always available even if one unit is unavailable. It is therefore highly recommended. The deployment of a CloudGen Firewall in Microsoft Azure is easy thanks to the web interface that guides you through the process.
Microsoft Azure Virtual WAN
The Barracuda CloudGen Firewall supports up to four Internet Service Provider (ISP) links to Microsoft Azure Virtual WAN. You must have a static IPv4 public IP address with similar bandwidth and latency. For each link, two active-active IPsec IKEv2 VPN tunnels are automatically created if you use automated connectivity. BGP multi-path routing is used to route the traffic, and the configuration of BGP multi-path routing is likewise set up automatically when using automated connectivity. The firewall learns path information as set by the Virtual WAN hub, which results in better path affinity. In addition, BGP-based load balancing and automatic path failover are used for the best connection results.
For more information, see Azure Virtual WAN.
Multi-Factor Authentication with Time-Based One-Time Password (TOTP)
With the release of firmware version 8.0.1, the Barracuda CloudGen Firewall supports multi-factor authentication for user accounts on an individual basis, using a Time-based One-time Password (TOTP) as a secondary authentication method. Multi-factor authentication can be enabled for client-to-site VPN (TINA protocol only), SSL VPN, CudaLaunch, and the Barracuda VPN Client for Windows. Multi-factor authentication using TOTP requires an Advanced Remote Access subscription.
For more information, see How to Configure Multi-Factor Authentication Using Time-based One-time Password (TOTP).
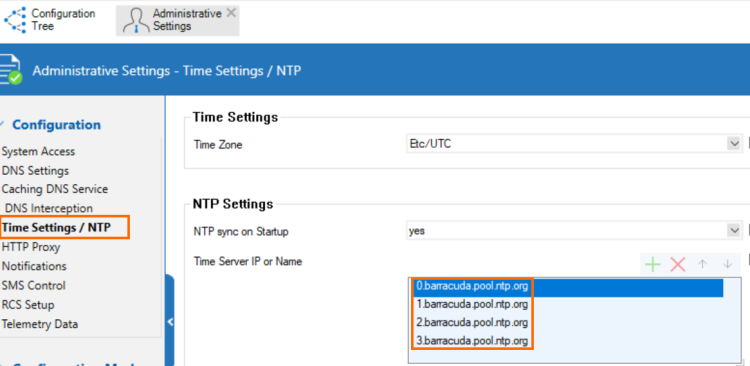
NTP Servers for the Barracuda Zones
The NTP default configuration now displays 4 NTP servers for the Barracuda zone in CONFIGURATION > Configuration Tree > Box > Administrative Settings.
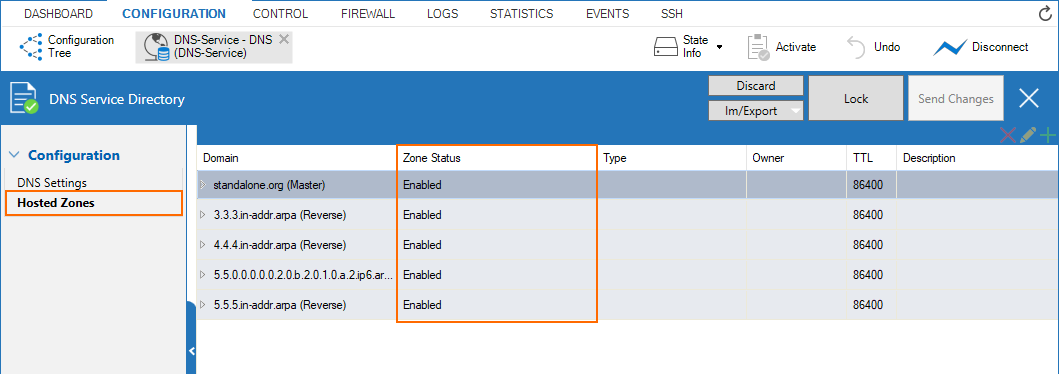
New DNS User Interface and Advanced DNS Features
The DNS service has been refactored and now offers a new user interface. This user interface is now tightly incorporated into new features that extend the DNS by various advanced options. The feature set of the new DNS service now includes:
- Stand-alone and distributed DNS service
- Primary / Secondary / Forward DNS zones
- Split DNS
- Health probing
Replacement of Virtual Servers by a New 2-Layer Architecture
The former 3-layer server-service architecture has been replaced by a 2-layer architecture in which services are now operated on top of the box layer. With firmware 8.0.1, services are subordinated to the Assigned Services node and allow a simpler administration of services and reduce error-prone issues by limiting services to run only on the box they are initially created on.
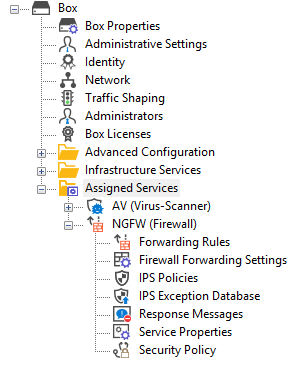
For more information, see Assigned Services and Understanding Assigned Services.
Optimized Command-Line Tool for Configuring an HA Pair of Firewalls in the Cloud
The command-line tool create-dha for creating an HA pair of firewalls in the cloud has been optimized. The command no longer requires you to configure the parameter of a netmask because both firewalls must be configured in a subnet of the same size.
REST API Extensions
- REST calls for logins, logout, and authentication for endpoints
- REST for all common access rule operations: create / delete / list / change
- REST calls for network objects (stand-alone + CC (global cluster firewall objects))
- REST calls for service objects (CC + stand-alone)
- REST calls for enabling and activating IPS
- REST calls to allow you to manage box administrators
- REST calls to allow you to manage tokens
- CLI tool to enable REST by default on cloud firewalls (place in user data)
For more information, see https://campus.barracuda.com/product/cloudgenfirewall/api/8.0
SNMP
SNMP now provides the option to monitor license status, the number of days until a license expires, and the current number of protected IPs.
Also, there is now the option to monitor certificates and their expiration date.
SSL VPN
The new TOTP portal provides self-enrollment and self-service of the TOTP authentication scheme.
SSL VPN resources can now be configured as dynamic apps. If configured as a dynamic app, Super Users can enable, disable, or time-enable a resource. Dynamic access can be configured for web apps, native apps, generic tunnels, and network places.
For more information, see SSL VPN.
Usage of DHCP on a VLAN Interface
Requesting an IP address from a DHCP server for a VLAN interface is supported by a feature called Header Reordering and can be found in the VLANs Window accessible in CONFIGURATION > Configuration Tree > Network > Virtual LANs.
For correct usage of the user interface item Header Reordering, see the following table:
| User Action | User Interface Item | Description |
|---|---|---|
| Default state: header reordering is off. |  | No header reordering is done for DHCP on a VLAN interface. |
| Select the check box in case the assignment of an IP address from a DHCP server fails. |  | Header reordering for DHCP on a VLAN interface is now activated. |
VPN IPv6 Payloads
With the exception of SD-WAN, IPv6 payloads in VPN tunnels are supported and now work for TINA site-to-site and client-to-site tunnels.
What's new in version 8.0.5
Custom Box Descriptors
When managing a large number of firewalls in the Control Center, the naming scheme of the CloudGen firewall proved to be insufficient. The Control Center now has received additional functionality to extend the standard naming scheme for CloudGen firewalls. This functionality includes the option to enter additional fields for a more distinctive naming scheme of managed CloudGen firewalls.
For more information, see How to Configure Custom Box Descriptors and Filter Managed Firewalls in Different Data Views.
Control Centers operating in a Parent-to-Child Relation
In the past, the configuration of Control Centers operating in a parent-to-child relation required modifying the host firewall ruleset of the firewall. As of release 8.0.5, this is no longer necessary. Firmware release 8.0.5 now covers all necessary steps that require the user to perform a minimum of configuration steps to set up split Control Centers without having to modify the host firewall ruleset.
In case you are already running split Control Centers, some steps must be performed before upgrading to firmware 8.0.5.
For more information, see 8.0.5 Migration Notes and its subordinated migration articles that relate to you running firmware versions, paragraph Important Notes Before Migrating.
Improvements Included in Version 8.0.5
Authentication
- HA clusters in conjunction with RSA servers are now working as expected in case of a failover. [BNNGF-32212]
- In case of a group of RADIUS servers, authentication requests are no longer sent to other RADIUS servers if the first server has rejected the request. [BNNGF-67177]
- Authentication with TACACS+ now works as expected. [BNNGF-67386]
- TS agent authentication now works reliably with more than 1024 terminal servers. [BNNGF-67667]
- The SSH service no longer unexpectedly dies when updating configurations. [BNNGF-68109]
- The TACACS+ authentication no longer crashes after an update. [BNNGF-68147]
- Authenticating with an OTP on the VPN client no longer reports errors on the first login. [BNNGF-69229]
- Authentication redirect now works as expected. [BNNGF-69280]
- The menu list in CC > Config > Global Settings > Administrative Roles > External Admins now includes an entry for redirecting authentication. [BNNGF-69312]
- RADIUS authentication now works as expected. [BNNGF-70048]
- TOTP usernames with an underscore are now correctly displayed in CONFIGURATION > Configuration Tree > Box > Infrastructure Services > Time-based OTP Bulk Enrollment, section User Bulk Enrollment. [BNNGF-70094]
- TOTP users no longer show up after being deleted. [BNNGF-70741]
- Changes to authentication configurations now work as expected. [BNNGF-70775]
- Radius authentication now accepts up to 99 simultaneous authentications. [BNNGF-70953]
- The firewall authentication daemon no longer needs to be killed manually when doing changes to Inline Authentication settings. [BNNGF-71363]
- After exceeding the maximum permitted login attempts, no AD server within the same group gets queried within the configured timeout period. [BNNGF-71966]
Azure Cloud
- The deployment no longer breaks in conjunction with the Microsoft Azure Linux Agent. [BNNGF-68889]
Barracuda Firewall Admin
- Administrator accounts can now be cloned for CC Admins. [BNNGF-55604]
- When executing an Emergency Override, notification dialog windows will also be displayed to inform the user. [BNNGF-63969]
- The usage of a session and one-time passwords in Firewall Admin > Settings > Client Settings can now be configured in the section Authentication. [BNNGF-64612]
- Statistic entries for managed boxes running with the new 2-layer service architecture now contain the appropriate Assigned Services name. [BNNGF-65765]
- CRL checks for sub-certificates now work as expected. [BNNGF-66252]
- BGP route map entries no longer accept '0' as a sequence number in CONFIGURATION > Configuration Tree > Box > Assigned Services > OSPF/RIP/BGP Routing > Filter Setup IPv4, section BGP Specific Conditions, window Route Map Entry, edit field Sequence Number. [BNNGF-66293]
- DNS record data for the TXT record type are now correctly displayed in CONFIGURATION > Configuration Tree > Box > Assigned Services > DNS > DNS Service > Hosted Zones. [BNNGF-67107]
- The '#' character is now allowed in the SMTP password field. [BNNGF-69024]
- New keys are now assigned to certificates as expected. [BNNGF-69065]
- Opening DNS records no longer cause issues in certain situations. [BNNGF-69222]
- In case of a network activation in CONTROL > Box > Network > Activate new network configuration, the firewall checks and highlights the "Soft" button in case a soft activation is adequate for the preceding changes. [BNNGF-69235]
- Overrides of linked repositories for HTTP certificates in CONFIGURATION > Configuration Tree > Box > Assigned Services > Firewall > Firewall Forwarding Settings > Authentication, section Authentication Server Configuration, are now working as expected. [BNNGF-69342]
- The two columns Authentication Level and Last Password Change have been added to be selectable for the CC Admin view. [BNNGF-69527]
- The DASHBOARD > Status Map is now capable to display all corresponding states for the telemetry system. [BNNGF-69596]
- When importing an invalid certificate chain, Firewall Admin now reports this with an error message. [BNNGF-70093]
- Firewall Admin no longer sets the values of SOA records to zero. [BNNGF-70320]
- Firewall Admin now displays all licenses correctly on a Control Center in CONTROL > Barracuda Activation. [BNNGF-70793]
- The user interface for the new CC Admin dialog now contains the help information. [BNNGF-70922]
- As of the 6.0 release, FW Admin can be migrated to any newer version. [BNNGF-71053]
- An icon has been added to CONTROL to indicate the status of the CloudGen Access service. [BNNGF-71394]
- The list view at CONFIGURATION > Configuration Tree > Box > Assigned Services > VPN > VPN Settings > Root Certificates now displays the issuer of the certificate in the column Issued By. [BNNGF-71701]
- In case of a bulk server migration from the older 3-layer to the new 2-layer service architecture on a Control Center, hotfixes are now announced in an information window to let the user chose whether to install the hotfix. [BNNGF-71718]
- Firewall Admin now correctly displays the value for IPsec Timeout in VPN Settings. [BNNGF-72815]
- CloudGen Access icons are now correctly displayed in the tab bar. [BNNGF-72848]
- TLS v1.3 can now be selected in case Feature Level is greater than or equal to 8.0. [BNNGF-73200]
- The ACL edit field in the edit window for CC Admins in CC > ADMINS, tab General now processes the IP addresses in CIDR notation. [BNNGF-73700]
- A new information field Firmware Version has been added to the CONTROL view in Firewall Admin. [BNNGF-74324]
- Session reconnects are now much more responsive. [BNNGF-74644]
- In Firewall Admin, filtering strings in columns now also works with strings in quotation marks. [BNNGF-74785]
- Firewall Admin no longer displays 3-layer server-service nodes for boxes running with the 2-layer assigned services node in certain situations. [BNNGF-75611]
Barracuda OS
- The connection statistics for application rules have been completely removed. [BNNGF-27651]
- The agent string limit has been increased to now accept 192 characters. [BNNGF-35986]
- The retrieval of metadata for the firmware update of managed boxes now works as expected. [BNNGF-54555]
- Configuring IPv6 subnets for IPv6 DHCP addresses in CONFIGURATION > Configuration Tree > Box > Assigned Services > DHCP > Operation Setup IPv6, configuration window Subnets > Network Address Field, now works as expected. [BNNGF-56665]
- Browser agent Opera will now be blocked on request as expected. [BNNGF-60719]
- The firewall operates at its maximum throughput when interface offloading is disabled. [BNNGF-61644]
- When applying a BLOCK rule, erroneous events no longer occur in certain cases. [BNNGF-63275]
- Firewalls can now be configured to send authentication requests for admin accounts to a Control Center that then acts as an authentication proxy forwarding these requests to another centralized authentication service, e.g., MSAD. [BNNGF-63916]
- The status of pool licenses no longer gets corrupted in certain situations. [BNNGF-64716]
- An automatically generated RCS report now contains the RCS message field/info. [BNNGF-65509]
- WAagent now creates the swap partition as expected and no longer takes away storage space from the root partition. [BNNGF-66051]
- CC event notifications are now sent correctly if the StartTLS option is activated in CC > Box > Administrative Settings > Notifications, section Email Notifications. [BNNGF-66456]
- If a VLAN is configured for the first time on the firewall, the option for Header Reordering is by default set to On in CONFIGURATION > Configuration Tree > Network > Virtual VLAN. [BNNGF-66582]
- The dot character (' . ') is no longer allowed to be used in bridge names. [BNNGF-66666]
- A successful installation with NGInstall is now also indicated with a sound on F380b, F400c, and T400. [BNNGF-66777]
- The SNMPd no longer crashes after a failover. [BNNGF-66792]
- The SNMP trap uses the correct IP as agent address and correctly handles the event. [BNNGF-66793]
- File uploads from on-premises boxes to GCP via a TINA tunnel now work as expected due to a fix for the VirtIO driver. [BNNGF-66954]
- Certificates with empty subject but with valid subject alternative names are now supported according to RFC5280, section 4.1.2.6. [BNNGF-67778]
- Authenticating via DC Agent if a large number of user accounts is configured now works as expected. [BNNGF-67861]
- If connections to an external bind IP on LTE- and XDSL-equipped firewalls break, active sessions for TINA tunnels are now actively terminated and therefore no longer cause trouble for other types of traffic. [BNNGF-68021]
- When configuring a remote management tunnel on a Control Center in CONFIGURATION > Configuration Tree > Multi-Range > your range > your cluster > your managed CloudGen firewall > Network, the Suggest VIP button now also works in conjunction with repositories. [BNNGF-68056]
- Recovering a CC using a box.par file now works as expected. [BNNGF-68097]
- HA repository links are now supported. [BNNGF-68143]
- Local authentication is now enabled for the command-line tool cctool. [BNNGF-68548]
- Boxserver bulk migration is working as expected. [BNNGF-68648]
- Update from 7.2.6 to 8.0.3 or 8.0.4 now works as expected. [BNNGF-68689]
- Client-to-site VPN networks are now announced by OSPF. [BNNGF-68731]
- On an 8.2.0 Control Center, 8.0 box network repositories can no longer be created. [BNNGF-68952]
- Non-managed HA clusters can now be migrated in a single step. [BNNGF-69060]
- Migration of boxes no longer fails if the box name is identical to the server name when uniqueness is set to global. [BNNGF-69199]
- Downloading a PAR file with cctool to HA firewalls operating the 2-level service architecture now works as expected. [BNNGF-69232]
- When configuring routing tables in CONFIGURATION > Configuration Tree > Box > Network > Advanced Routing, and Configuration Mode is set to Advanced, it is now possible to configure a source IP address for source-based routing. [BNNGF-69345]
- PHION-MIB OID for BGP now works as expected. [BNNGF-69558]
- After logging into SSH as an Admin on box level of a CC, the command ulimit now runs under the correct permissions. [BNNGF-69603]
- The firewall no longer crashes in conjunction with TFTP. [BNNGF-69849]
- DNS objects now work as expected on F900 units after upgrading from 7.2.6 to 8.0.4. [BNNGF-69994]
- When blocking a service from Firewall Admin, the CloudGen Access proxy service is stopped as expected. [BNNGF-70000]
- Intensive configuration updates on an HA pair with configured DNS Server service no longer run into a timeout when the changes are synced to the secondary firewall. [BNNGF-70089]
- The configuration of auto-negotiation, speed, and duplex now works as expected for the SFP slots. [BNNGF-70146]
- When migrating from the former 3-layer server-service architecture to the new 2-layer service architecture, the secondary box is not created if it was already configured before the migration. [BNNGF-70197]
- When using an additional private HA uplink, the correct HA partner status is displayed for both boxes in Firewall Admin. [BNNGF-70198]
- Hardware detection for port-labeling now works as expected and creates an appropriate log entry. [BNNGF-70223]
- After a complete configuration update of a box from the Control Center, the configuration status is now in synch after a reboot of the box. [BNNGF-70307]
- A complete update no longer leads to two secondary boxes. [BNNGF-70328]
- After migrating from 7.2.6 to 8.0.4, syslog streaming now works as expected. [BNNGF-70432]
- The GEO IP database has been updated. [BNNGF-70442] [BNNGF-71808] [BNNGF-72503]
- The URL Filter no longer looks up categories for private IP addresses. [BNNGF-70465]
- The firewall now always boots and correctly honors the configured log storage location. [BNNGF-70493]
- Firewalls running in an HA cluster now also support pool licenses even if there is only one license in the pool available. [BNNGF-70645]
- Unsupported offloading settings are automatically disabled on the interfaces. [BNNGF-70739]
- The firewall no longer crashes in certain situations when operating OSP/RIP/BGP. [BNNGF-70862]
- Expired QuoVadis trusted CA intermediate certificates have been updated and no longer break SSL Interception. [BNNGF-70864]
- It is now possible to configure more than 16 bridge groups. [BNNGF-70894]
- The Linux command
sudohas been updated to cover CVE-2021-3156. [BNNGF-70994] - Loglines are now displayed correctly in the Web UI. [BNNGF-71011]
- IPMI for HA can now be configured, and config entries are stored accordingly. [BNNGF-71087]
- The system-wide limit of open files has been increased for certain appliances. [BNNGF-71114]
- The SNMP path is now available for the PHION-MIB OID for hardware sensors on F280 boxes as expected. [BNNGF-71159]
- Hostnames are now consistent in version 8. [BNNGF-71190]
- Changes made on the firewall by external users with a login name containing the '@' character are now shown in RCS with '(at)'. [BNNGF-71191]
- SNI SSL now works with the correct certificate. [BNNGF-71422]
- References to certificates in the Certificate Store are now created as expected. [BNNGF-71691]
- Archive PAR file creation now works as expected for larger PAR files. [BNNGF-71743]
- PAR files greater than 2 GB are no longer broken when exported with the command line tool cctool. [BNNGF-71814]
- Non-TOR applications no longer get flagged as false-positive TOR applications by the firewall. [BNNGF-71962]
- It is now possible to use certificates from the Certificate Store in the HTTP proxy. [BNNGF-71998]
- When migrating a bridge, a warning will be displayed to inform the user about a necessary boxnet activation. [BNNGF-72003]
- After the migration from the 3-layer server-service architecture to the new 2-layer service architecture, the secondary HA firewall now realizes that there was a migration and works as expected. [BNNGF-72196]
- Offline bridges now receive configuration updates as expected. [BNNGF-72266]
- The UI check box for the option Use Same Port like in the Web UI window Firewall > Connection Objects > Connection Objects > Add Connection Object now works as expected. [BNNGF-72703]
- On firewalls operating under KVM, packets are now evenly distributed between all available CPUs. [BNNGF-72844]
- Apple authentication is not intercepted. [BNNGF-72857]
- When setting Enable BFD to yes in CONFIGURATION > Configuration Tree > Box > Services > OSPF/RIP/BGP Settings > Neighbor Setup IPv4, window Neighbors, section BGP Parameters (in advanced mode), the settings are available immediately after confirming the configuration. [BNNGF-73069]
- The speed test works as expected. [BNNGF-73131]
- SNMP walk for determining the percentage of disk fill is now working as expected. [BNNGF-73290]
- Service objects with port ranges containing only 2 ports no longer cause the firewall to crash. [BNNGF-73649]
- Importing boxes with a virtual server into 8.0 cluster is allowed. [BNNGF-73755]
- On an HA cluster, the session sync now works as expected. [BNNGF-73831]
- The term 'serverIP' has been replaced by 'sharedIP' in the host firewall ruleset. [BNNGF-74310]
- When upgrading a box to the new 2-layer service architecture, correct warnings will be displayed for all cases where server IPs are configured without routes. [BNNGF-75453]
- The firewall no longer terminates sessions after receiving an RST with sequence numbers that are too old. [BNNGF-77035]
Cloud
- All the ports listed in the NGF-VPN service object will be allowed to the DHCP interfaces. The rule OP-SRV-VPN-DHCP is part of the new default ruleset. [BNNGF-70218]
- PAYG licenses are now using the private key from the Barracuda Order System (BOS). [BNNGF-75203]
Control Center
- Handling of locks during minimal PAR-file generation works as expected for zero-touch deployments (ZTD). [BNNGF-68061]
- Creating an archive PAR-file on a Control Center with the cctool now also works across mount points in the hierarchical file system. [BNNGF-69510]
- The CLI command cctool has been extended to support functionality for importing managed boxes on the CC and enabling/disabling managed boxes. [BNNGF-73098]
- A dynamic network object is present in the host firewall for parent-to-child Control Centers (split CC). [BNNGF-75153]
DHCP
- Pool ranges for CONFIGURATION > Configuration Tree > Multi-Range > your range > your cluster > Boxes > Assigned Services > DHCP now work as expected for network masks larger than /24. [BNNGF-69115]
DNS
- After migrating to 8.0.4, the default values in SOA records are no longer set to zero. [BNNGF-69221]
- The BIND system has been updated to fix CVE-2021-25215. [BNNGF-74781]
Google Cloud
- When performing an HA failover in Google Cloud, the HA box no longer runs out of memory. [BNNGF-69915]
HTTP Proxy
- The HTTP proxy has been updated and no longer leaks information. [BNNGF-64698]
- The HTTP proxy has been updated. [BNNGF-72099]
- The HTTP proxy has been updated to version 4.15. [BNNGF-74727]
- URL filter categories are now working as expected in the settings for the HTTP proxy access control. [BNNGF-74895]
IMPORTANT: See also the red note in the article Migration from 8.0.1/8.0.2/8.0.3/8.0.4 to 8.0.5.
NGInstall
- NGInstall now provides the option to activate disk encryption. [BNNGF-76887]
Virus Scanner
- When configuring ATP Cloud Communication in CONFIGURATION > Configuration Tree > Box > Assigned Services > Virus Scanner > Virus Scanner Settings > ATP, the list for Region in the section ATP Cloud Communication now contains entries that offer a greater range of options for the region. [BNNGF-67209]
- The virus scanner no longer freezes in certain situations, and archives can be downloaded again. [BNNGF-68051]
VPN
- Traffic is now routed correctly to the corresponding VPN tunnels. [BNNGF-63242]
- The AES-CTR encryption has been implemented for VPN TINA tunnels. [BNNGF-64151]
- The VPN service no longer experiences memory issues in certain situations. [BNNGF-65639]
- Performance testing of any encryption method now works as expected. [BNNGF-67031]
- The AES256 cipher key length for VPN TINA tunnels is now logged. [BNNGF-68600]
- UDP transports now work as expected after an update to 8.0.4. [BNNGF-68988]
- BGP routing over IKEv2 tunnels works again as expected [BNNGF-69418]
- When establishing an IPsec tunnel, the IPsec responder now checks for all configured proposals in phase 2 and matches the configuration as expected. [BNNGF-69485]
- The import of PFX files into VPN settings now works as expected. [BNNGF-69741]
- The NAC clients 5.1.2 and 5.2.0 now connect to the VPN server as expected. [BNNGF-70145]
- VPN IPsec IKEv1 client-to-site tunnels no longer crash in certain situations. [BNNGF-70309]
- Several improvements have been made to stabilize TINA tunnels and to prevent connections from unexpectedly closing. [BNNGF-70363]
- VPN log no longer shows C2S cleartext passwords. [BNNGF-70438]
- L2TP tunnels behind a NAT device now work as expected. [BNNGF-70676]
- TINA VPN tunnels running under firmware 8.0.4 no longer experience drop-outs due to memory issues in certain situations. [BNNGF-70825]
- The feature Temporary enable Tunnel for IPsec IKEv1 tunnels has been completely disabled. [BNNGF-71403]
- After migrating from the 3-layer server-service architecture to the new 2-layer service architecture, IKE tunnels work as expected. [BNNGF-71419]
- IKEv1/IPsec tunnels are now stable and work as expected. [BNNGF-72561] [BNNGF-73187]
- The triple-DES encryption will no longer be available if VPN is operating in FIPS 140-2 mode. [BNNGF-73018]
- DynMesh tunnels are now completely removed when no longer needed. [BNNGF-73356]
- The signal handler of the VPN server now works as expected and is no longer terminated unexpectedly in certain situations. [BNNGF-73384]
- After an ISP outage, VPN tunnels are re-established and now work as expected. [BNNGF-73584]
Known Issues
- Currently, no RCS information is logged for Named Networks. [BNNGF-47097]
- The learn-only mode for OSPF is not working as expected. [BNNGF-65299]
- A dynamic network object is present in the host firewall for parent-to-child Control Centers. [BNNGF-75153]
- Barracuda Firewall Admin – FW Admin 8.x fails to configure DNS 7.x correctly. [BNNGF-77636]
- Installing a box with box.pca and/or re-deploying config via /opt/phion/update/box.pca does not work. [BNNGF-77829]
- SSLVPN – RDP connections can terminate after an unspecified amount of time and need to be re-established by the user. In some cases, connections cannot be re-established at all.
For a workaround, manually restart the service on the CLI viakillall sslvpnsrv.
To periodically restart via a cron job and/or script, use/usr/bin/killall sslvpnsrv.
For questions on how to implement automatic restart procedures, contact Barracuda Networks Technical Support for assistance. [BNNGS-3761]