To adjust resources used by your firewall service, you can change the sizing parameters in the General Firewall Configuration (CONFIGURATION > Configuration Tree > Box > Infrastructure Services) section of the Barracuda CloudGen Firewall. After changing general firewall configuration settings, perform a Firmware Restart (CONTROL > Box) for the changes to take effect. Default values vary depending on the model.
Firewall Sizing
Maximum Number of Connections
Max Session Slots – Set the maximum number of session slots allowed. The amount of memory consumed by the firewall is updated when this value is changed and displayed in the Firewall Memory [MB] field. (When set to the default value, the firewall service will consume about 150 MB RAM).
Max UDP [%] – (advanced) Defines the percentage of the Max Session Slots allowed to be UDP sessions.
This setting can be overridden with the Resource Protection settings in the advanced section of a forwarding firewall rule. Private IPv4 addresses are exempted completely.
Max Echo [%] – (advanced) Defines the percentage of the Max Session Slots allowed to be ICMP sessions.
This setting can be overridden with the Resource Protection settings in the advanced section of a forwarding firewall rule. Private IPv4 addresses are exempted completely.
Max Other [%] – (advanced) Defines the percentage of the Max Session Slots allowed to be an IP protocol type, except TCP, UDP, or ICMP.
This setting can be overridden with the Resource Protection settings in the advanced section of a forwarding firewall rule. Private IPv4 addresses are exempted completely.
Firewall Memory [MB] – Displays the estimated memory requirement according to the current firewall configuration settings. If the value exceeds 200 MB, an additional bootloader parameter may be required. On i686-based CloudGen Firewalls with more than 768 MB RAM requiring additional vmalloc space to satisfy the increased memory demand of non-default firewall settings, we recommend increasing the vmalloc area in steps of 128 MB, starting at 384 MB. For more information, see How to Configure the Bootloader.
Global Limits 1
Max DNS Entries – Defines the maximum number of DNS queries that may be triggered by the use of network objects containing hostnames. 75% of the queries are reserved for the forwarding firewall and 25% for the host firewall. Network objects used in both forwarding and host firewall rulesets will trigger two DNS queries and be counted twice.
Max Acceptors – (advanced) Maximum number of pending accepts for inbound rules. An acceptor is a dynamic implicit rule that is generated by plugins handling dynamic connection requests. The FTP protocol, for example, uses a data connection in addition to the control connection on TCP port 21 to perform the actual file transfer. By analyzing the FTP protocol, the firewall knows when such data connections occur and creates an acceptor to allow the corresponding data transfer session.
Max Pending Inbounds – Maximum number of pending TCP inbound requests. This parameter comes into effect only when the TCP accept policy is set to inbound for the access rule.
Max BARPs – (advanced) Defines the maximum number of bridging ARPs allowed. A bridging ARP entry (BARP) stores the information that specifies which bridge interface corresponds to a certain MAC address. Additionally, associated IP addresses are stored along with the BARP entry. Modifying this value may be useful for large bridging setups.
Max Plugins – (advanced) Maximum number of rules using plugins.
Dyn Service Names (RPC) – Maximum number of dynamic service name entries.
Global Limits 2
Max. Dynamic Rules – Maximum number of dynamically activated rules. The default preset value is 128.
Max. Multiple Redirect IPs – Maximum number of IP addresses in rules with multiple redirect target IPs. The default preset value is 128.
Global Inbound Mode Limits
To establish a TCP connection, the TCP three-way handshake must be completed. You can use different accept policies to change how incoming and outgoing TCP connections are handled on a per-rule basis.
For more information, see Best Practice - Protect Against TCP SYN Flooding Attacks with TCP Accept Policies.
Inbound Mode Threshold [%] – The default preset value is 20.
If the percentage value of the maximum number of sessions in the pending accept state is exceeded, the firewall will apply the inbound accept policy for SYN flood protection for all incoming TCP sessions, regardless of what is configured on the Access Rule level, i.e.:
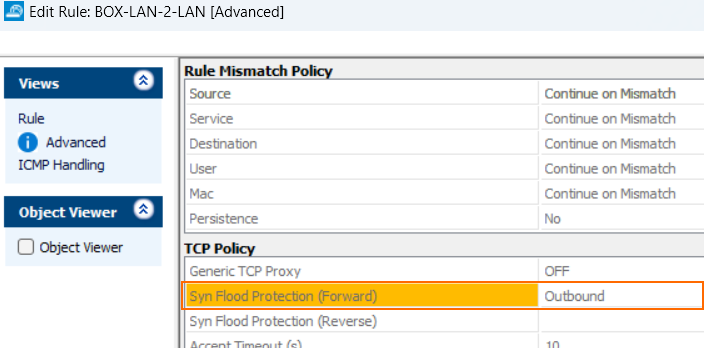
When the firewall switches into inbound mode, a related message will be written into the security log and an event 4004 with a related information text will be created.
When the firewall terminates this mode, it will be written into the security log, and an event 4004 with a related information text will be created.
SYN Cookie High Watermark [%] – This is the percentage (of the maximum number of pending inbounds) of pending inbound accepts to switch to TCP SYN cookie usage for enhanced SYN flooding protection. The default preset value is 20.
SYN Cookie Low Watermark [%] – This is the percentage (of the maximum number of pending inbounds) of pending inbound accepts to go back to ordinary SYN handling. The default preset value is 15.
Source-Based Session Limits
Max Local-On Session/Src – (advanced) Maximum number of sessions per source IP address. Cannot be set to more than Max Session Slots.
Max Local-In UDP/Src – (advanced) Maximum number of UDP sessions per source IP address.
Max Local-In Echo/Src – (advanced) Maximum number of ICMP Echo sessions per source IP.
Max Local-In Other/Src – (advanced) Maximum number of sessions for all other IP protocols (not TCP, UDP, ICMP) per source IP address.
Max Pending Local Accepts/Src – (advanced) Maximum number of pending accepts per source IP address.
Firewall History
The firewall history stores connection information for troubleshooting purposes. You can configure how many and how long connections are stored in the General Firewall Configuration settings. Use the Advanced View to configure these settings.
Max. Access Entries – Determines the size of the visualization caches.
Max. Block Entries – Determines the maximum number of block entries.
Max. Drop Entries – Determines the maximum number of drop entries.
Max. Fail Entries – Determines the maximum number of fail entries.
Max. Scan Entries – Determines the maximum number of scan entries.
Max. ARP Entries – Determines the maximum number of ARP entries.
DNS Resolve IPs – Setting this parameter to yes will resolve IPs to hostnames on the firewall history. This may cause excessive load on the DNS servers.
Operational
Ruleset-Related Settings
Rule Matching Policy – Selects the way in which a rule lookup is performed.
Kernel space - linear lookup – Adequate for small rulesets.
Kernel space - tree lookup (fastest) – Preferred option for large rulesets with hundreds of rules.
As a rule of thumb, for about 1000 session/s the Kernel space should be enabled for better firewall performance. Additionally, if many firewall objects (> 200) are used, the Kernel space - tree option is recommended.
Rule Change Behavior – This setting applies only to the forwarding firewall and not to the host firewall because the host firewall generally does not allow re-evaluation of a session upon a rule-change. The setting specifies whether an existing connection is terminated (Terminate-on-change or not (Keep-on-change) if the ruleset changes and the session is no longer allowed by the new ruleset.
No Rule Update Time Range – This option allows you to define a time range during which access rules may not be updated. Use international time format. For example, to disallow rule update from 14:00 through 22:00, insert
14-22.On-demand network objects update – This option allows you to enable on-demand network objects.
Network objects update interval – Update interval in minutes for on-demand network objects.
IPv6 Settings
Block Type 0 Routing Headers – This option allows you to block type 0 routing headers according to rfc5095.
Default TCP Policy
Syn Flood Protection – Defines the default behavior of the firewall with regard to the TCP three-way handshake.
Outbound – Passes on the SYN to the target address.
Inbound – The firewall completes the handshake and only then performs a handshake with the actual target. This helps to protect the target from SYN flood attacks. Disabling will cause an overhead in packet transmission, but may speed up interactive protocols like SSH.
Nagle Algorithm – This parameter enables/disables the Nagle algorithm. This option is only available when using stream forwarding.
Perform TCP Sequence Check – This parameter enables/disables TCP sequence checks. You can select one of the following options:
RST-Packets-Only
All Packets
None
TCP Stream Reassembly – (advanced) Reassembles the TCP stream before scanning for vulnerabilities.
Raw TCP Mode Policy
RAW TCP Idle Timeout [s] – Defines the idle timeout value in seconds for RAW TCP mode.
RAW TCP Timeout Policy – Defines the timeout policy that will be used for RAW TCP mode.
Use-global-timeouts – Sets the timeout value that has been configured in the previous sections.
Use-tcp-timeouts – Uses the timeout values from standard TCP set in the matching rule.
Default Anti-Spoofing Policy
ARP Reverse Route Check – Setting this parameter to Yes causes answers to ARP requests to be checked if source IP and interface match.
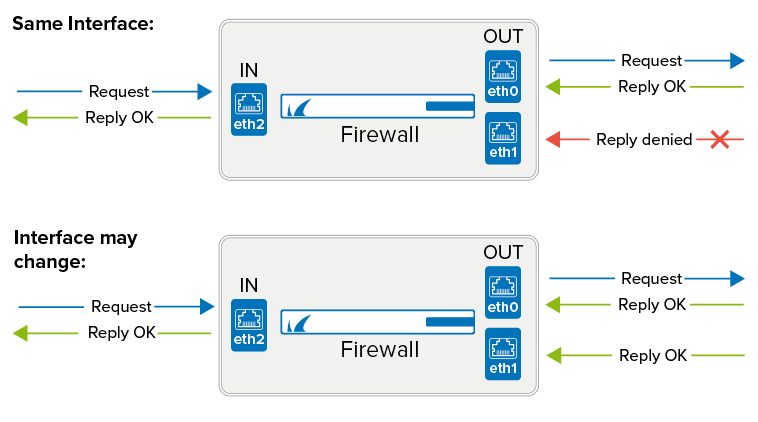
Reverse Interface Policy – The options of this parameter specify whether requests and replies must use the same (outgoing) interface (same-interface or not (interface-may-change).
Port Scan Policy
Port Scan Threshold – When the number of blocked requests exceed the threshold, a port scan is detected and a port scan event is triggered. To not generate an event, see How to Configure Basic, Severity, and Notification Settings for Events.
Port Scan Detection Interval [s] – Detection interval in seconds to check for not allowed activity. In combination with the parameter Port Scan Threshold, it defines the condition when to report a port scan.
Performance-Related Policies
Session Creation CPU Limit [%] – (advanced) Reserves a specific amount of CPU resources for the Barracuda OS to prevent the firewall from becoming unmanageable in case of a high amount of concurrent sessions being initiated. Barracuda Networks recommends to keep the Default value.
Validate TCP Checksum – (advanced) Enables an additional TCP packet consistency check. This will reduce performance.
Validate UDP Checksum – (advanced) Enables an additional UDP packet consistency check. This will reduce performance.
Parallel Shaping Tree Evaluation – (advanced) This option, if enabled, improves shaping tree evaluation.
Disabled – Disables this option.
Enabled – Improves shaping tree evaluation.
Enable-MultiQueue-Only (default) – Enables this feature only for shaping trees built on top of interfaces with multiple hardware-queues or with RPS enabled.
High Availability-Related Policies
Allow Active-Active Mode – (advanced) Active-Active firewall operation mode must be enabled in preparation for operation of multiple active firewalls on one box with a load balancer connected upstream.
Enable Session Sync – (advanced) All currently established sessions will be synced to the HA partner to improve failover performance.
Enable Authentication Sync – (advanced) This option allows you to enable authentication data synchronization between HA partners.
Auto – Automatically detects if a direct synchronization is required, or if synchronization is done over an authentication synchronization zone.
Yes – Enables direct synchronization between HA partners.
No – Disables direct synchronization between HA partners.
Log Synced Sessions – (advanced) This setting determines logging of access cache sessions that have been synchronized between HA partners. Set to No to disable logging. Set to Auto to check if a trustzone synchronization is in place. If yes, the sync is done via trustzone, and direct synchronization gets disabled automatically. If no trustzone sync is configured, Auto will enable direct authentication sync.
Generically Forwarded Networks – (advanced) Traffic between networks inserted into this field will be excluded from firewall monitoring and will be forwarded without source and destination differentiation, even if no forwarding firewall is installed.
Operational IPS
This menu point in General Firewall Configuration is accessible only in Advanced Configuration Mode.
Intrusion Prevention System (IPS) Engine Settings
IPS Scan Mode – (advanced) Select the scanning mode for IPS. You must reboot for the changes to take effect.
Auto – (advanced) The firewall automatically chooses the best suited mode.
Fast-Scan – (advanced) With this option enabled, only the beginning of a session is scanned as most attacks occur within the first few packets regardless of the protocols used (TCP, UDP).
Full-Scan – (advanced) Scan all packets.
Intrusion Prevention System (IPS) Decoder Settings
HTML Parsing for IPS – Toggles HTML obfuscation detection. If this setting is changed, you must reboot for the changes to take effect.
HTML content-encoding decompression – Enables HTTP content-encoding decompression (gzip, deflate). A reboot is required.
HTML content-disposition decompression – Enables HTTP content-disposition decompression (zip). A reboot is required.
PDF decoder – Enables decoding of PDF documents. A reboot is required.
RPC decoder – Enables an RPC decoder. This is used for DCERPC and SMB connections. A reboot is required.
Operational VPN
Enable Assembler Ciphers – (advanced) Using the assembler implementation for AES/SHA/MD5 increases VPN performance significantly.
Enable Intel AVX Extensions – Enables or disables the usage of Intel’s AVX extension (also valid on AMD processors).
Globally clear DF Bit – (advanced) Clears the DF bit for each ipv4 packet routed through a VPN tunnel. For more information on MTU, see Advanced Routing.
Application Detection
Resource Failure Policy
Out of Memory Policy – An Out of Memory condition may disable protocol and application detection. As a consequence, all deeper analysis will be disabled as well.
Fail-Open – Select to continue forwarding.
Fail-Close – Select to terminate the affected sessions.
URL Categorization
Max. Cache Entries – The maximum number of entries in the kernel cache. 0 is auto selection depending on RAM size.
Categorization Timeout [s] – Set the maximum timeout to wait for categorization response.
Cache Entry Expiration [s] – After the configured time, the cached entries category will be updated.
Cache Entry Expiration (no cat.) [s] – After the specified time in seconds, the cached entries' category, with category 'not categorized' will be updated.
Cache Entry Expiration (err cat.) [s] – After the specified time in seconds, the cached entries' category, with category 'assigning error' will be updated.
Log Verbosity – (advanced) The log level of the URL Filter engine.
Application and Port Protocol Detection
Enable Port Detection – Set to yes to use deep packet inspection to enforce the used protocol on a port. For more information, see How to Configure Port Protocol Protection
Application Detection Destination Tracking
Enable Destination Tracking – Set to no unless specifically instructed otherwise by Barracuda Networks Technical Support.
Supervisory Control and Data Acquisition (SCADA)
SCADA Protocol Detection – Enable to detect SCADA protocols.
Disabled – Detection is disabled.
Enable without Parsing Log – Detected SCADA protocols are included in the Firewall Activity log.
Enable with Parsing Log – Enabled with detailed logs (box/SCADA/parsing).
SCADA Dump Size [MB] – (advanced) A value of 0 means disabled. Enable to write a dump file for further analysis if SCADA protocol detection is enabled without parsing log support.
Audit and Reporting
Statistics Policy
Generate Dashboard Information – Enable/disable the firewall dashboard.
Generate Monitor Information – Enable the firewall monitor.
Maximum Storage Size [MB] – Specify the storage size in megabytes to be used to monitor information data. A value of 0 enables automatic assignment based on the device. This parameter relates to the virtual disk size of the APPID_stat database and is set to 'auto' per default. 'Auto' means:
/phion0partition size-dependent calculation.Below 20GB: 10 MB for all database files.
Between 20 GB and 100 GB: 100 MB for all database files.
Greater than 100 GB: 200 MB for all database files.
Statistics for Host Firewall – This option enables statistics for connections passing through the host firewall.
Generate Protocol Statistics – If enabled, protocol and P2P-specific statistics are created and listed within the statistics viewer under .../BOX/proto-stat/...
Use username if available – If set to yes, usernames are used for statistics, if available. Otherwise, the source IP address is used.
Eventing Policy
Generate Events – Enable/Disable event generation.
Event Data – (advanced) Use this section to selectively enable or disable event generation.
Click Edit and define the events data should be generated for.
Log Policy
Application Control Logging – Select the global policy for Application Control logging.
Activity Log Mode – Configure whether the Firewall Activity logs use key-value pairs or only log the values. For more information, see Available Log Files and Structure
Activity Log Data – Configure whether the Firewall Activity logs should use full text or encoded information according to the list below. The encoded format is typically used to reduce the size of the log files. This corresponds to the “Info” column in the Firewall History tab.
Activity Log Path – If enabled, the path of a request is included in the Target column in the Activity Log. This corresponds to the Application Context column in the Firewall Live tab.
Activity Log Information – Click Set/Edit to define what type of information is included in the firewall activity log. Click Clear to reset to factory default values.
Log Level – Decides whether log messages are accumulated to avoid too large log files.
Cumulative Interval [s] – (advanced) Interval in seconds for which cumulative logging is activated for either matching or similar log entries.
Cumulative Maximum – (advanced) Maximum of similar log entries to start cumulative logging.
Generate Audit Log – Enable the generation of structured firewall audit data that can be forwarded.
Audit Log Data – (advanced) Click Set/Edit to selectively enable or disable audit log generation. Click Clear to reset to factory default values.
Log ICMP Packets – Select the logging policy for ICMP packets.
Log-All – Log all ICMP packets except type ECHO.
Log-Unexpected – Log all ICMP packets except ECHO and UNREACHABLE.
Log-None – Disable ICMP logging.
Allow Threat Log Processing – Allow other processes to access threat log information for further processing.
IPFIX Export
Enable IPFIX Export – Set to yes to enable sending of IP flow information using the IP flow information export (IPFIX) protocol.
Enable Intermediate Flow Reports – Enable sending of intermediate reports with delta counters. (Use the Intermediate Reporting Interval [min] option to determine how often intermediate reports are sent)
Intermediate Reporting Interval [min] – Interval in minutes between two intermediate IPFIX flow reports for each active flow.
Template – If set to Extended, includes additional information, such as delta counters, to the IPFIX export. If your collector does not support reverse flows, select Uniflow templates. These templates will duplicate the traffic against the collector.
Custom Templates – If Custom is selected for Template, you can configure your own set of information elements in the window Custom Template after you clicked Edit... .
Collectors – Click + to add external IPFIX collectors.
Report Blocked or Failed Sessions – If set to yes, this option enables sending of flow records for packets that were not forwarded by the firewall, e.g., because they were blocked or the respective session could not be established.
Connection Tracing
Settings – Click Set/Edit to configure connection tracing settings.
Out of Session Packets
This menu point in General Firewall Configuration is accessible only in Advanced Configuration Mode.
Out of Session [OOS] Packet Policy
Interfaces to Send TCP RST – (advanced) The firewall sends TCP RST packets to these network interfaces if it detects packets not belonging to an active session. This is useful to avoid timeouts on certain servers.
IPV4 Networks to Send TCP RST – (advanced) The firewall sends TCP RST packets to these IPv4 networks if it detects packets not belonging to an active session.
IPV6 Networks to Send TCP RST – (advanced) The firewall sends TCP RST packets to these IPv6 networks if it detects packets not belonging to an active session.
Global Safe Search
Search Engine Log
Enable Search Engine Log – (advanced) Set to yes to enable logging of search strings. The log file will be created as soon as the firewall detects a query. You can inspect the log file searchString in your firewall on LOGS > Log Viewer > Assigned Services > NGFW.
Safe Search Settings
You can protect users behind a Barracuda CloudGen Firewall from undesired content in search results. To achieve this, enable the following options:
Enable Youtube Safe Search – Set this option to yes to enable YouTube safe search.
Enable Bing Safe Search – Set this option to yes to enable Bing safe search.
Enable Google Safe Search – Set this option to yes to enable Google safe search.
Enable Yahoo Safe Search – Set this option to yes to enable Yahoo safe search.
Advanced Log Settings
This menu point in General Firewall Configuration is accessible only in Advanced Configuration Mode.
Security Policy Facility Loglevels – (advanced) Specify the general log level for services running on the firewall.
