If the search term you want to block is not covered by the SafeSearch feature (because it does not represent adult content), you can still block specific search terms or queries by creating a custom application. Custom search applications are supported for Google, Yahoo, Bing, and YouTube. These custom application objects can then be selected in the matching application rule. Custom search applications do not override the SafeSearch settings of the matching access rule.
Before You Begin
- Define the search terms you wish to block. Wildcard characters (* and ?) are allowed. E.g., *searchterm?searchterm*
- (optional) Enable TLS Inspection. To use TLS Inspection the Feature Level of the Forwarding Firewall must be set to 7.2 or higher. For more information, see TLS Inspection in the Firewall.
Step 1. Create a Custom Application Object
Create a custom application object for each search engine provider.
- Go to CONFIGURATION > Configuration Tree > Box > Assigned Services > Firewall > Forwarding Rules.
- In the left menu, click Applications.
- Right-click in the main area, and select New > Custom Application. The Select Application to customize window opens.
- Select the search engine provider. E.g. Bing Search
- Click OK. The Custom Application window opens.
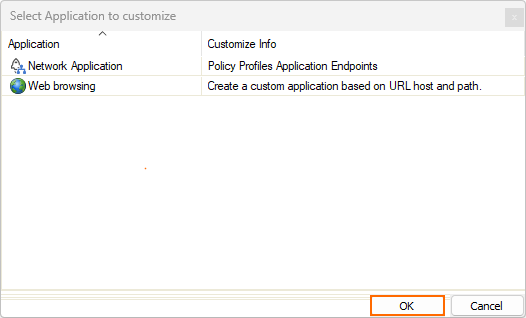
- Enter a Name.
- Select a Category.
- Click the edit icon to select the Risk factor.
- Select the Properties.
- Click + to add a Search String. Wildcards * and ? are allowed. Multiple search entries are combined with a logic OR.
- Click Save.
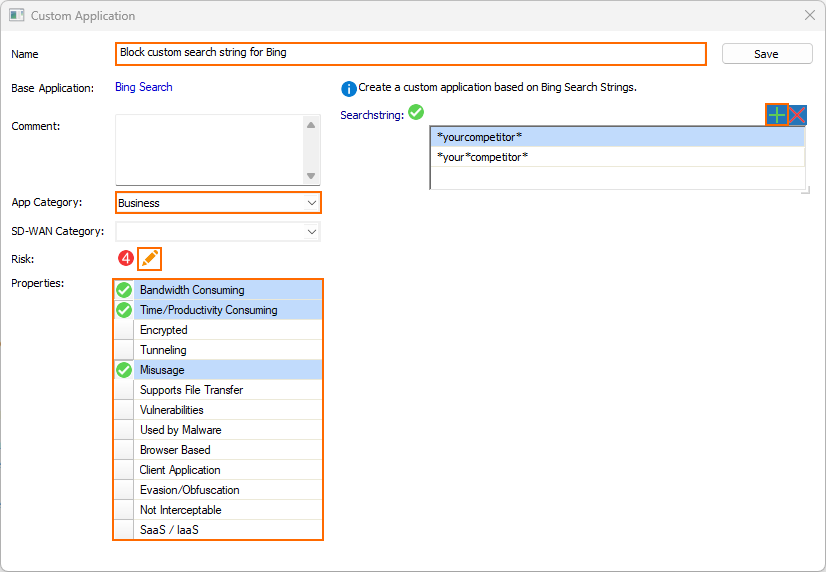
- Click Send Changes and Activate.
To block this search term for all supported search engine providers, repeat this step for each search engine.
Step 2. Create a PASS Access Rule
Create a PASS access rule that matches outgoing HTTP and HTTPS traffic. Because most search engines use HTTPS, using TLS Inspection is recommended.
- Go to CONFIGURATION > Configuration Tree > Box > Assigned Services > Firewall > Forwarding Rules.
- Double-click to edit the access rule matching outgoing web traffic generated by your users.
- Verify that the access rule matches both HTTP and HTTPS traffic.
- Click on the Application Policy link and enable the following Application Control features:
- Application Control
- (optional) TLS Inspection
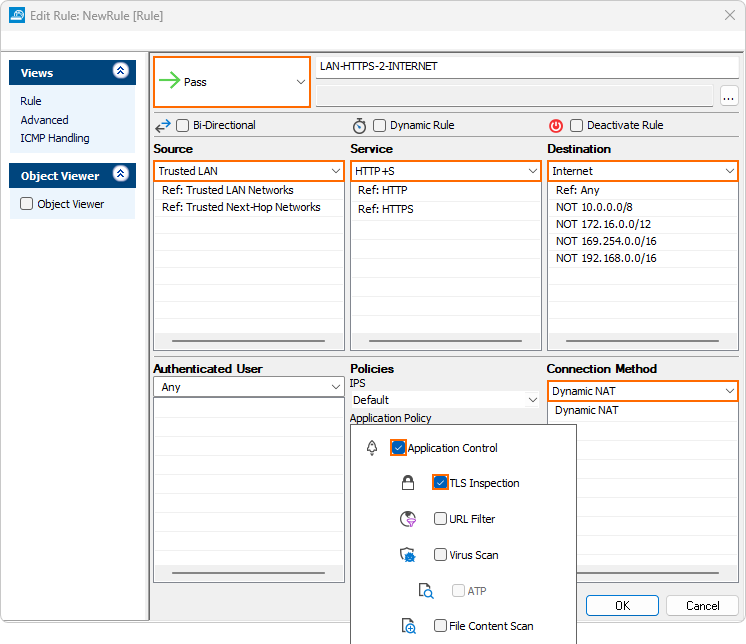
- If configured, select a policy from the TLS Inspection Policy drop-down list. For more information, see TLS Inspection in the Firewall.
- Click OK.
- Click Send Changes and Activate.
Step 3. Create an Application Rule Using the Custom Application Objects
Create an application rule matching the same traffic that matches the access rule created in Step 2.
- Go to CONFIGURATION > Configuration Tree > Box > Assigned Services > Firewall > Forwarding Rules.
- In the left menu, click Application Rules.
- Click Lock.
- Create a DENY application rule. For more information, see How to Create an Application Rule.
- Source – Select the same source used in the matching access rule.
- Application – Select the custom application objects created in Step1.
- Destination – Select the same destination used in the matching access rule.
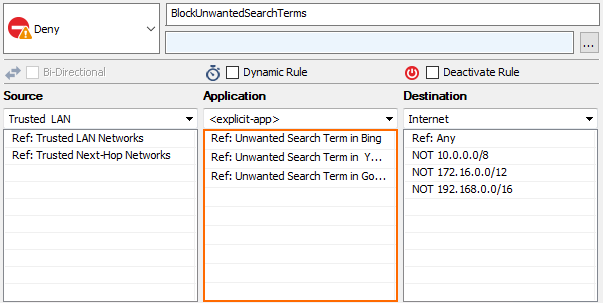
- Click OK.
- Place the application rule so that no application rule above it matches the same traffic.
- Click Send Changes and Activate.
You are now blocking searches for the unwanted search terms listed in the custom application objects. Users searching for these terms are redirected to the customizable block page. For more information, see How to Configure Custom Block Pages and Texts.
