Employee impersonation is one of many sophisticated email threats organizations encounter. Employee impersonation attacks occur in many different ways, one of the most common being display name spoofing. Display name spoofing attacks attempt to deceive recipients by changing the display name of their email to impersonate an employee. These emails typically come from legitimate email accounts, such as Gmail or Yahoo, and do not contain any links or attachments. They are designed using social engineering.
To protect against these attacks, you should use a combination of gateway defenses with an API based inbox defense, which uses AI to analyze historical email information to stop sophisticated email threats from reaching your users’ inboxes, along with user awareness training. If you are unable to use inbox defense, you can create content policies at the gateway to block unwanted emails.
While content filtering is not foolproof, they do provide a greater level of control than that of unrestricted content.
To create a content policy:
Log into Email Gateway Defense and go to the Inbound Settings > Content Policies page.
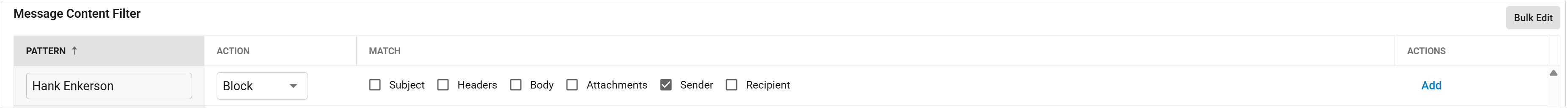
Under Message Content Filter section, type in the name of the employee for the Pattern.
Select Block for the Action.
Select Sender for the Match.
Click Add.
For example, if you want to block display name spoofing attacks for your CEO "Hank Enkerson", your inbound content policy would be similar to this.