Microsoft Entra ID (formerly Azure Active Directory)
Configure recipient verification with Microsoft Entra ID to allow end users to sign into Email Gateway Defense using their Microsoft Entra ID credentials. Once logged in, users can view their quarantine messages.
Single Sign-On
You can configure Single Sign-On (SSO) for a domain so that authenticated users can access all or a subset of the restricted resources by authenticating just once using their Microsoft Entra ID credentials. SSO is a mechanism where a single set of user credentials is used for authentication and authorization to access multiple applications across different web servers and platforms, without having to re-authenticate.
The SSO environment protects defined resources (websites and applications) by requiring the following steps before granting access:
- Authentication: Authentication verifies the identity of a user using login credentials.
- Authorization: Authorization applies permissions to determine if this user may access the requested resource.
Set Up Microsoft Entra ID Authorization
Complete the steps in this section for each domain you want to synchronize with your Microsoft Entra ID directory.
- Log into https://login.barracudanetworks.com/ using your account credentials, and click Email Gateway Defense in the left pane.
- Click Domains, and click Edit in the Settings column for the desired domain.
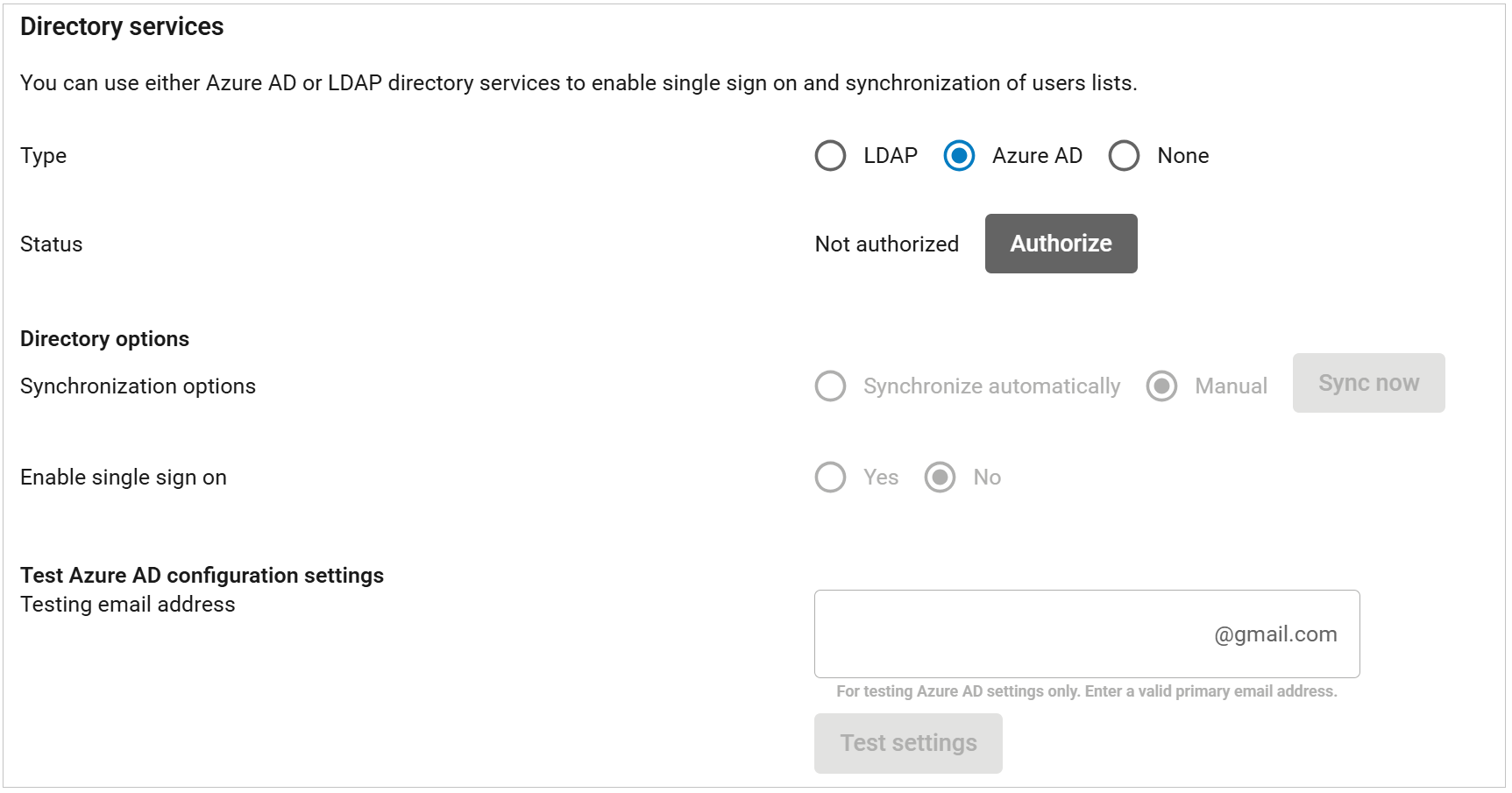
- In the Domains > Domain Settings page, scroll to the Directory Services section, and select Azure AD, and click Save Changes at the top of the page.
- Scroll down to the Status section, and click Authorize.
- The Authorize Azure AD dialog box displays. Click Continue.
- When prompted, log into your Microsoft 365 account as a global administrator.
- In the Authorization page, click Accept to authorize Email Gateway Defense to connect to your Microsoft Entra ID directory.
- In the Domain Settings page, the Status field displays as Active; the Authorized Account and Authorization Date displays the account and date.
In the Synchronization Options section, select Synchronize Automatically. When selected, Email Gateway Defense automatically synchronizes with your Microsoft Entra ID (formerly Azure AD) at regular intervals throughout the day and adds/updates your users.
If you encounter sync issues, such as new users not being properly synced between your Microsoft Entra ID directory and Email Gateway Defense user list, click Sync Now to manually synchronize Email Gateway Defense with your Microsoft Entra directory.
If you select Manual, you must click Sync Now to synchronize Email Gateway Defense with your Microsoft Entra ID directory and add/update users.- To use SSO, click Yes for Enable Single Sign On. Once enabled, users are prompted to log into their Microsoft 365 account when accessing their messages in Email Gateway Defense.
- To use the Test Azure AD Configuration Settings section, enter a valid email address in the Testing email address field to test your Microsoft Entra ID settings.
Click Test Settings.
- Click Save at the top of the page to save your settings and return to the Domains page.
