As an administrator, ensuring robust email security is vital in protecting your organization from threats such as display name spoofing. Attackers manipulate the "From" field to make emails appear to come from trusted sources, putting your organization at risk. By implementing effective content filters on your email gateway, you can block display name spoofing attempts and enhance your email security.
By following the steps outlined in this article, you can effectively safeguard your organization from domain display name spoofing attacks. Regularly review and update your content filtering rules to stay ahead of emerging threats, maintaining a robust defense against display name spoofing and bolstering your organization's email security.
Understanding Display Name Spoofing
Display name spoofing deceives recipients by making emails appear to come from trusted sources within your organization. Awareness of this technique is crucial to combat such attacks effectively.
Identifying Display Name Spoofing Patterns
Analyze past instances of display name spoofing within your organization by looking for common patterns such as domain variations or recognizable internal names used in display name spoofing attempts.
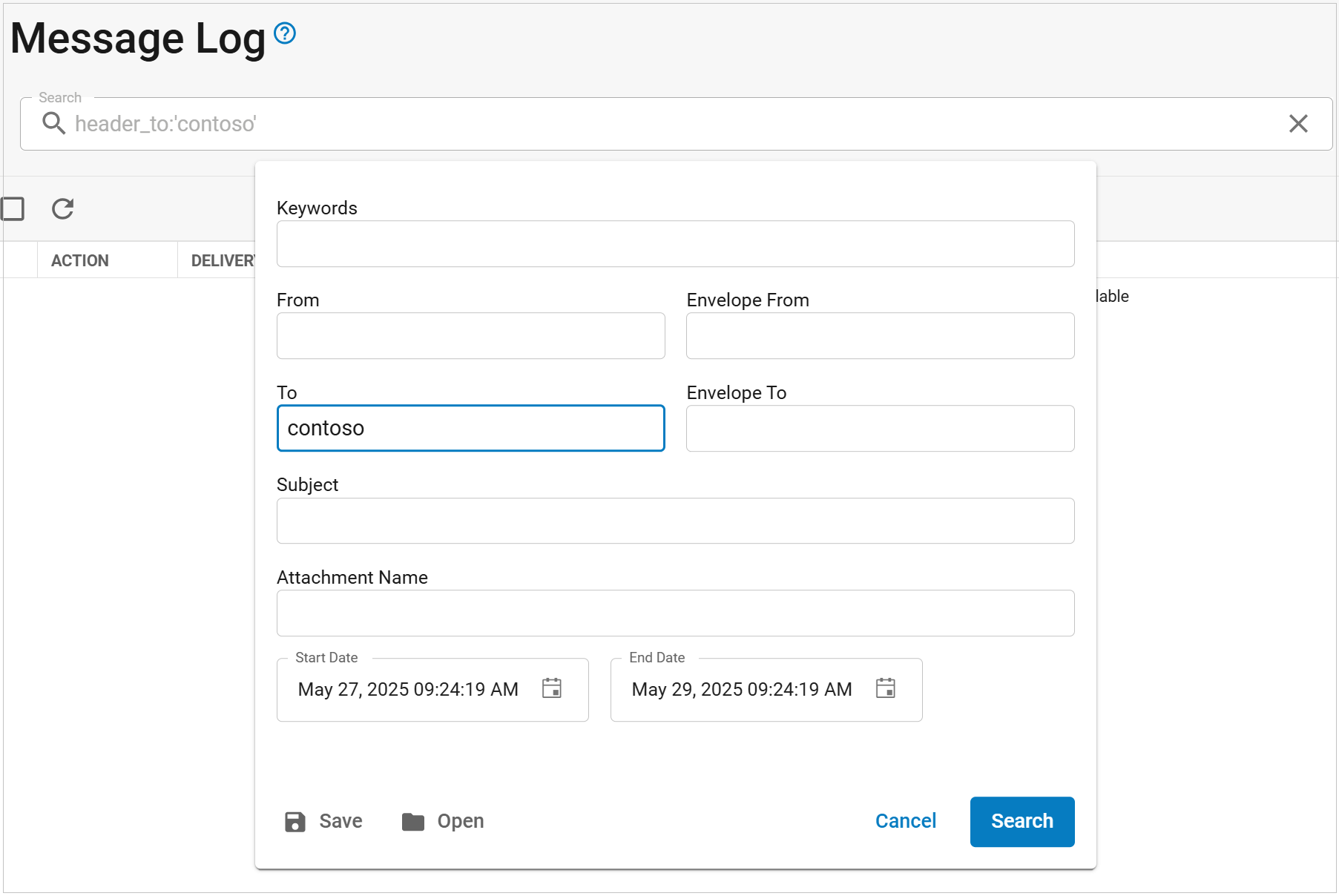
Leverage the available Message Log in Email Gateway Defense to search for emails that may match the content filtering policy. For example, searching for contoso in the From field helps identify emails with contoso in the display name.
Configuring Policies
Create an Allow List
Create an allow list of trusted domains and email addresses that use your company’s domain in the display name to prevent legitimate emails from being blocked. Use the Inbound Settings > Sender Policies page to exempt, quarantine, or block messages based on username, domain, or email address.
Implement Filtering Rules
Configure content filtering rules on your email gateway to identify and block emails that match domain spoofing display name patterns.
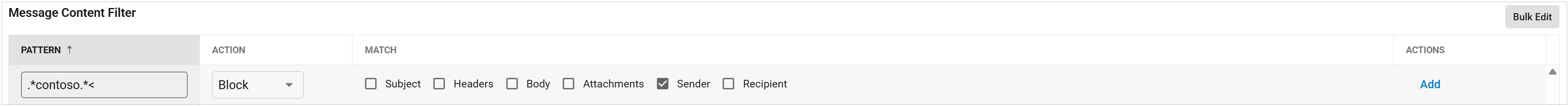
For example, if the customer's domain is "contoso.com", a regex content filter of .*contoso.*< can be created to identify emails such as:
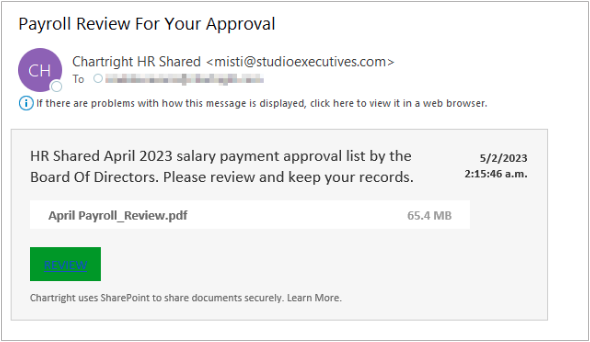
From: Contoso IT Support <badactor@gmail.com>
This filter pattern searches for any occurrence of "contoso" within the email's display name, followed by the "<" character, which is commonly used to separate the email address and display name. Emails that match this pattern are likely spoofed attempts and can be blocked.
It is important to note that this filter will not block legitimate emails such as:
From: IT Support <support@contoso.com>
Use the Inbound Settings > Content Policies page to set custom content filters, such as the one below, replacing contoso with your own domain.
Monitor the Message Log
Monitoring the message log is a crucial aspect of maintaining effective content filters. By regularly reviewing the message log on your email gateway, you can proactively identify any emails that may match the content filtering policy for display name spoofing.
In the Message Log, select the From Address as the Reason to show all emails being stopped by the new content policy.