Single Sign-On (SSO) enables users to log into Security Awareness Training using your organization's common authentication service. Note that these are users of Security Awareness Training, not the end users who are on the receiving end of your organization's Security Awareness Training campaigns.
Integrating with Barracuda Cloud Control (BCC)
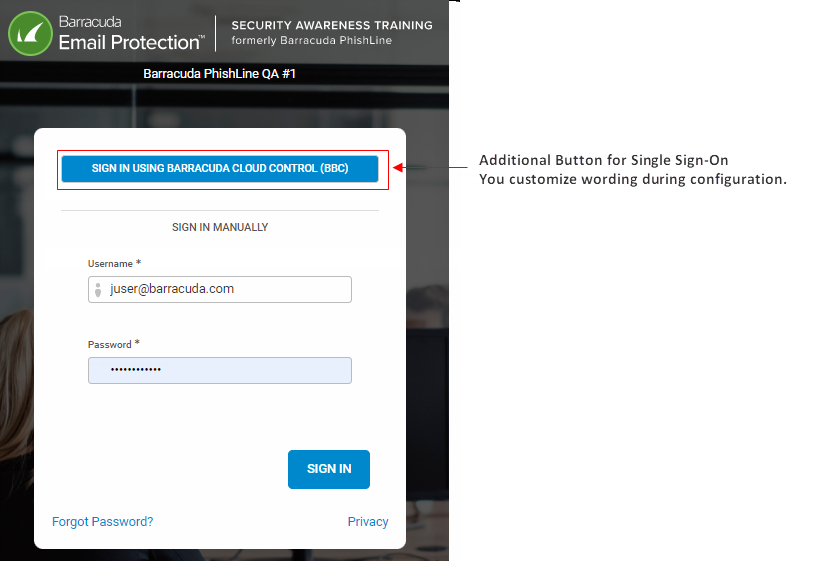
Barracuda Cloud Control is an entry point to most Barracuda functions. When users log into Barracuda Cloud Control, they can move seamlessly to Security Awareness Training. If users are not already logged into BCC, they can log into Security Awareness Training using the customizable button shown below.
General steps to integrate with Barracuda Cloud Control:
- Set up Barracuda Cloud Control for your organization. This might already be done for your organization. For details, see Barracuda Cloud Control documentation.
- In Security Awareness Training, navigate to System > User Manager and create users if needed.
For these users, for the Authorization Type, specify Single Sign-On (OAUTH2).
For details on adding users and specifying Authorization Type, refer to User Management.
Two Options for Single Sign-On
There are two options for implementing SSO with Security Awareness Training. Follow these links to learn how to implement SSO for your organization.
When you configure SSO with Security Awareness Training, users see an additional button on the Security Awareness Training login screen that they can use to authenticate through your organization's identity provider.