Barracuda SecureEdge combines the benefits of next-generation firewalls, secure SD-WAN, and cloud integration and automation to deliver a practical SASE solution. The SecureEdge dashboard provides a comprehensive overview of SD-WAN connections, SD-WAN tunnels, network activity, web and network traffic details, as well as the actionable status and security information of your deployed Barracuda Networks products.
Barracuda SecureEdge Dashboard
Barracuda SecureEdge provides fast and actionable in-product status information and is designed to allow internal and external reporting to stakeholders who do not require access to the web interface. The dashboard provides a customizable status overview with information on SD-WAN connections, security, and transport and traffic details.
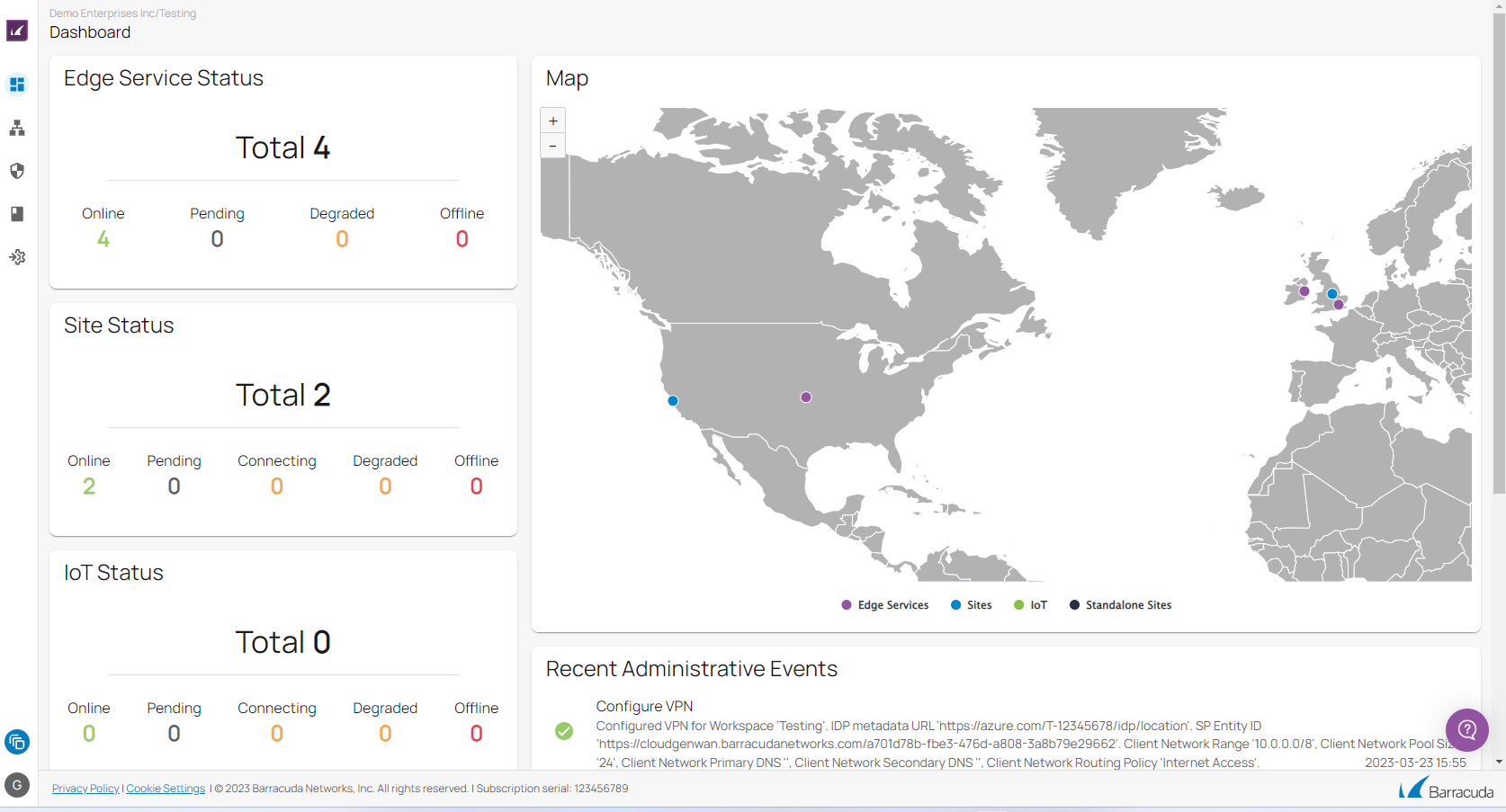
You can deploy virtual WANs with multiple edge services and site appliances. Each site is connected to the edge service using TINA, the Barracuda Networks VPN protocol. TINA is a proprietary extension of the IPsec protocol developed to improve VPN connectivity and availability over the standard IPsec protocol, and uses AES256 cipher for the VPN encryption. Barracuda SecureEdge uses BGP for routing.
Barracuda SecureEdge provides the following:
An aggregate view of data for multiple connected devices
Information on details and availability of SD-WAN connections
Drill-down capabilities for a subset of connected devices to see aggregate statistics
Customizable dashboard monitoring for a quick overview of filtering statistics aggregated across all connected devices
Barracuda SecureEdge Manager
The Barracuda SecureEdge Manager is the cloud-based central management portal. From here, you can manage all your edge services, sites, tunnels, and appliances, and perform various configuration and maintenance actions.
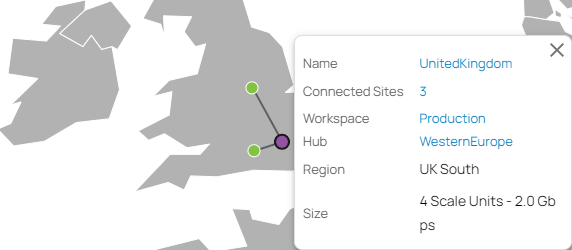
The SecureEdge Manager summarizes information with respect to your selected workspace or tenant and displays details on the status of your associated edge services, sites, tunnels, and configured appliances. Aggregated information on recent system and administrative events can be monitored. In addition, the dashboard provides an active tunnel map, a graphical view that shows where all sites and edge services are being deployed based on their geolocation. Click on a site or edge service in the map to see where it is connected to.
Barracuda CloudGen Firewall Integration
Barracuda CloudGen Firewall appliances can be enrolled with Barracuda SecureEdge as a point of enforcement for resource access policies. The firewall appliances can be either stand-alone or Control Center-managed units. Registration of CloudGen Firewalls on Barracuda SecureEdge is token based. After completing the registration process, the appliance gets enrolled and automatically appears in Barracuda SecureEdge, which indicates that the connection is established. The appliance details can be verified with respect to host name and serial number, using Barracuda Firewall Admin. On Barracuda CloudGen Firewall High Availability (HA) boxes, enrollment is required only on the primary unit.
For more information, see How to Configure a Barracuda CloudGen Firewall in Barracuda SecureEdge.
Ingress NAT Rules
Ingress traffic can be any form of network traffic whose source lies in an external network, in other words, in the public Internet, to destinations residing inside the host network. You must configure a security policy rule to allow the NAT traffic. In the Barracuda SecureEdge network policies configuration, you can define new ingress NAT rules for sites and on-premises edge services by specifying source, destination, and target criteria.
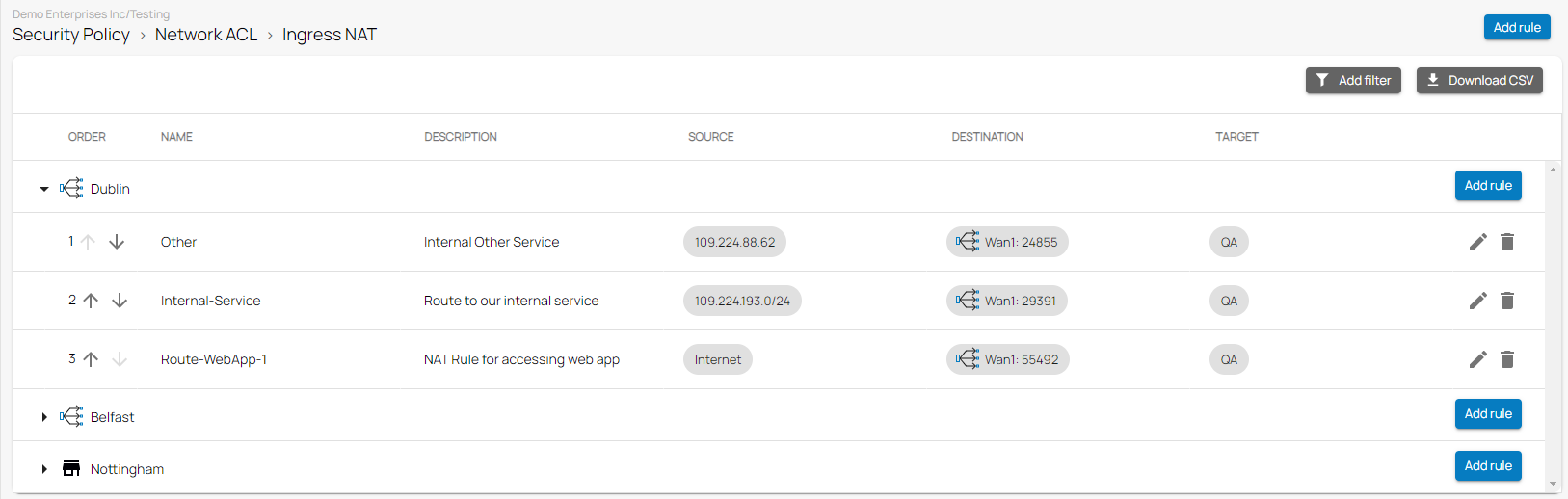
For more information, see How to Create Ingress NAT Rules.
Barracuda SecureEdge Agent
Barracuda SecureEdge allows administrators to enroll users with their respective devices. The Barracuda SecureEdge Agent is a Zero Trust Network Access (ZTNA) agent running on the client that connects to the services offered by Barracuda SecureEdge. The SecureEdge Agent allows users or groups to connect to different resource types, including custom apps or public endpoints such as SaaS services. A single user can enroll multiple devices on the same token. After the enterprise enrollment process is completed, your device protection gets enabled automatically. The Barracuda SecureEdge Agent for Windows, MacOS, iOS, and Android is available from their respective app stores.
For more information, see How to Enroll Users in Barracuda SecureEdge.
Remote Access Policies
Remote access policies are (pre-)defined rules for handling network traffic and are centrally managed through Barracuda SecureEdge. Remote access policies define resources made available to end users of the SecureEdge Agent as well as the associated access criteria. Barracuda SecureEdge allows administrators to create new remote access policies for users or groups that specify access requirements associated with various types of internal and external resources. These policies also define security attributes such as the device posture. When these policies are enabled, you can either enforce compliance or log violations. Certain security features (such as security inspection, firewall enabled, antivirus enabled, block jailbroken devices, and screen lock enabled) can be enabled or disabled with a switch; other update features for the operating system and the SecureEdge Agent can also be enabled/disabled. This action is disabled by default.
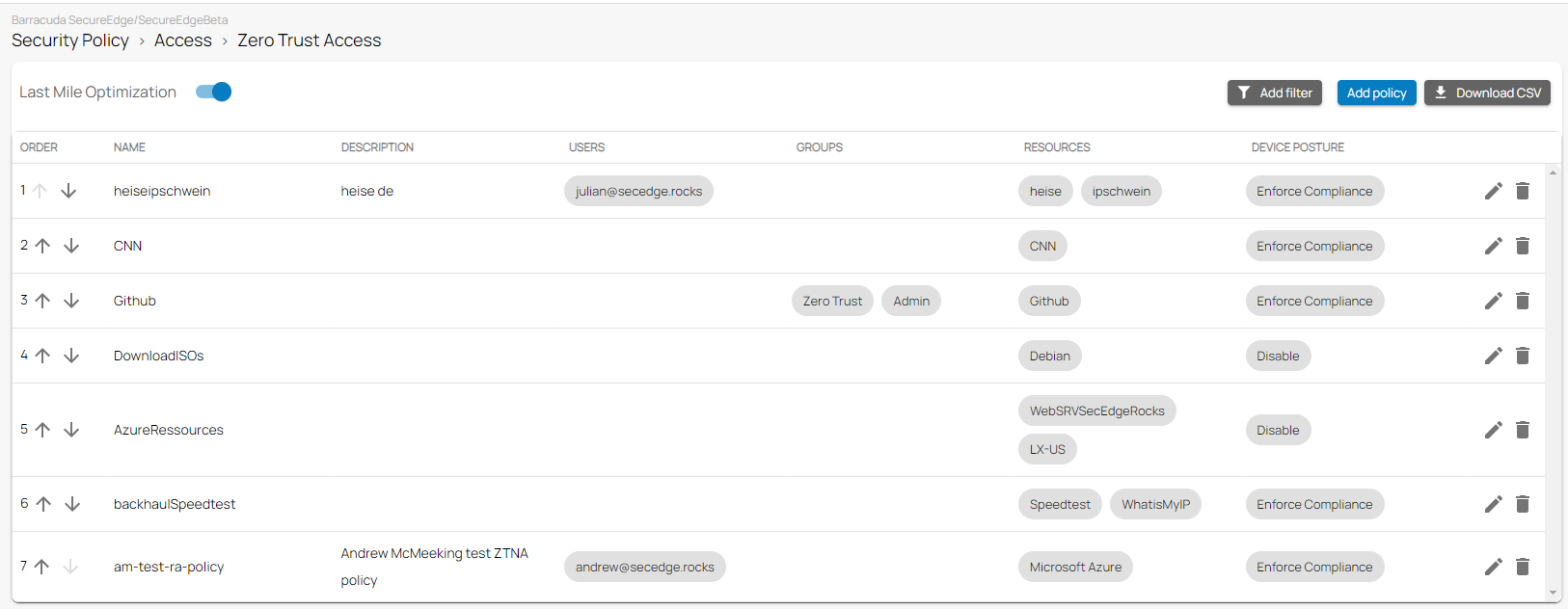
For more information, see Zero Trust Access Policies.
Barracuda SecureEdge Access
Barracuda SecureEdge Access lets you implement secure access to internal and external enterprise resources, whether they are on-premises or in the cloud, by using a Zero Trust Network Access (ZTNA) solution. Zero Trust builds upon the assumption that the network is hostile. As a result, network locality is not sufficient for establishing trust, and every flow must be authenticated and authorized in a dynamic fashion. This creates an effective separation between the control plane – the supporting system that implements the flow authentication and authorization according to the defined policies – and the data plane.
For more information, see ZTNA.
SecureEdge Integration with IoT Devices
The Barracuda SecureEdge Manager allows administrators to enroll the Barracuda Secure Connector, an IoT device, with the unified cloud service entity known as SecureEdge. Barracuda Secure Connector is a hardware device that offers large-scale remote access capabilities and allows the ever-growing number of IoT devices and micro-networks to securely connect to the corporate data center via VPN.
For more information, see How to Configure IoT Devices in Barracuda SecureEdge.
Barracuda SecureEdge SD-WAN Connector
The Barracuda SecureEdge SD-WAN Connector establishes a connection between the service and a resource that cannot be reached via routing. Registration of the SecureEdge SD-WAN Connector is token based. After retrieving the token from SecureEdge, you can select the edge service or site the device should connect to. Once registered, each SecureEdge SD-WAN Connector will be assigned a single static IP address within the SecureEdge environment. It also provides a feature in which the admin can configure a list of resources that the SecureEdge SD-WAN Connector can connect to, and each resource can be reached via the Barracuda SecureEdge Agent if a policy for it exists.
For more information, see How to Configure the SecureEdge Connector.
Known Issues 9.0.0
General Known Issues
SIP – The use of a SIP proxy with SecureEdge still might require manual adjustments in configuration files depending on the SIP setup. [BNNGF-95603]
Known Issues Related to Azure Log Analytics (OMS)
On boxes with Azure Log Analytics (OMS) activated, the phibs service does not restart automatically after update. To get the service running, a reboot is required.
