This article provides a recommended way to deploy a SecureEdge Site device in preparation for replacing a Barracuda Web Security appliance and migrating Web Filter policies from the Barracuda Web Security Gateway to the Barracuda SecureEdge Site device. The Barracuda SecureEdge Site device provides Web Filtering capabilities, including Advanced Threat Protection and deep SSL Inspection, with quick and easy configuration steps for every device.
The following table displays the recommended SecureEdge T appliances with respect to the Web Security Gateway model you are running.
Web Security Gateway Model | SecureEdge T Appliance |
|---|---|
210 (EoS) | T100 |
310 | T100 |
410 | T200 |
610 | T400 |
810 | T600 |
910 | T600 |
1010/1011 | T900 |
Before You Begin
Back everything up locally on your Web Security Gateway.
Ensure that you have the latest firmware installed on your SecureEdge appliances. For more information on the update process, see Updates.
You must have a working SecureEdge account. For more information, see How to Create a Barracuda Cloud Control Account for Barracuda SecureEdge.
You must have Identity Management / User Directories configured for the selected workspace, otherwise user and group-based policies will not work. You must use one of the identity providers that are supported in SecureEdge. Note that the Microsoft Entra ID and LDAP identity providers / user directories are supported on both the Web Security Gateway and SecureEdge. For a typical WSG configuration with a local LDAP directory, follow the instructions in How to Configure the DC Client in Barracuda SecureEdge. For additional information and instructions on other directories, such as the Google workspace or Microsoft Entra ID, see Identity Management.
If you are running 15.X firmware, you must back up everything locally on the Web Security Gateway and send the backup file to support. For more information, see How to Back Up and Restore Your System Configuration.
SecureEdge Site Device Configuration
To connect the Secure Edge Site device to your network, see Hardware Deployment. In addition, this article shows how to run a high availability cluster with two SecureEdge Site devices.
Deployment Modes
The migration works with both deployment types of the Web Security Gateway, the inline (or bridge) deployment and the forward proxy deployment. However, it is highly recommended to use the inline deployment mode. Despite the distinction between the two setup types, it is possible to add Proxy Connect on top of an inline setup. This lets you run a proxy in addition to the bridge when you are using the bridge configuration.
Inline deployment
Inline deployment provides the highest level of security because the SecureEdge Site device is directly integrated into the network pathway. Consequently, all network traffic is required to pass through the Site device.
The figure below illustrates a basic installation using inline deployment.
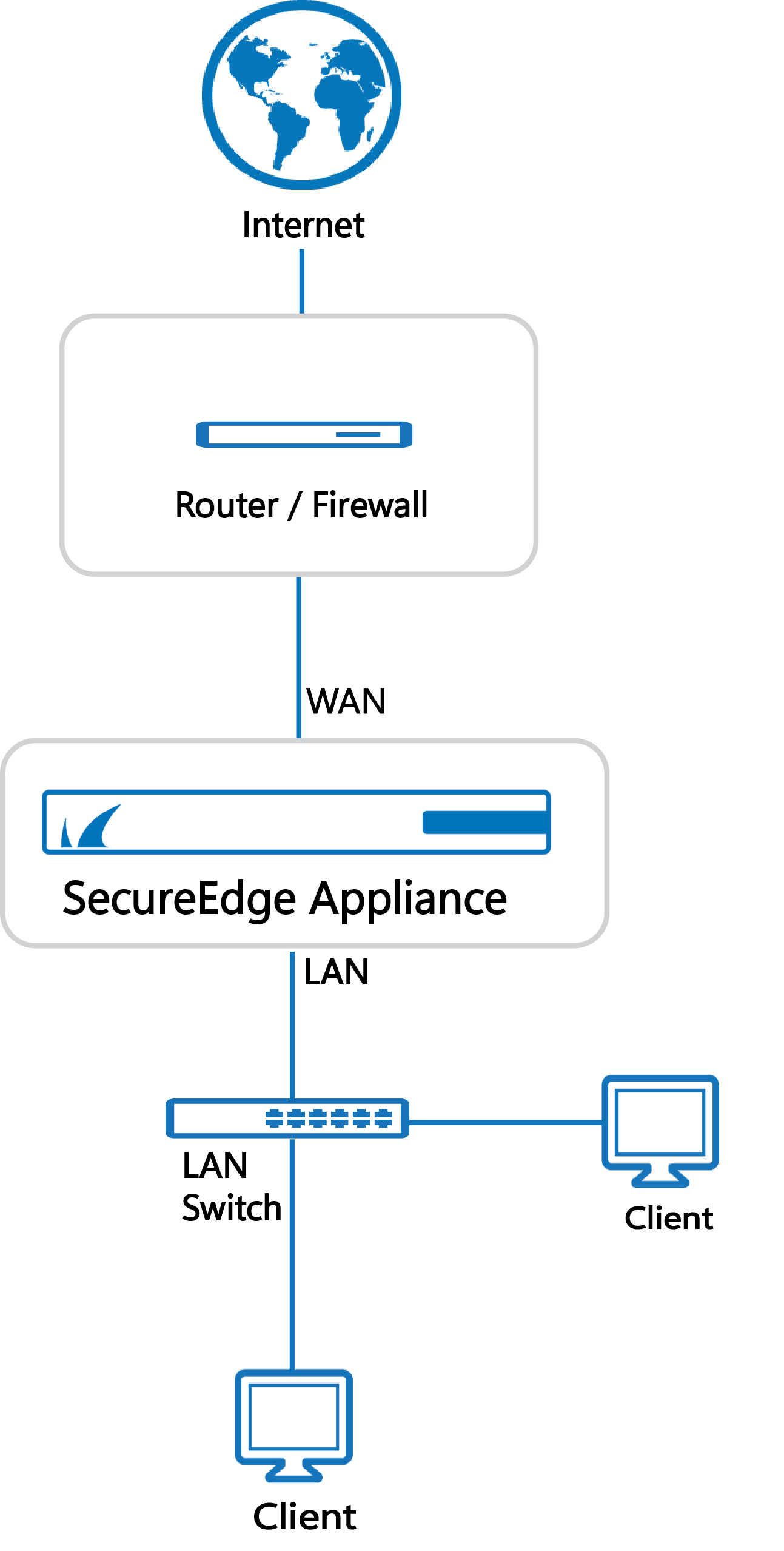
For more information on how to set up your SecureEdge Site device in bridge mode, see How to Create an Inline Bridge on a Stand-Alone Site.
Forward Proxy Deployment
To create a basic Site device configuration, see How to Create a T/VT Site Configuration in Barracuda SecureEdge.
The figure below illustrates a basic installation using the Forward Proxy deployment.
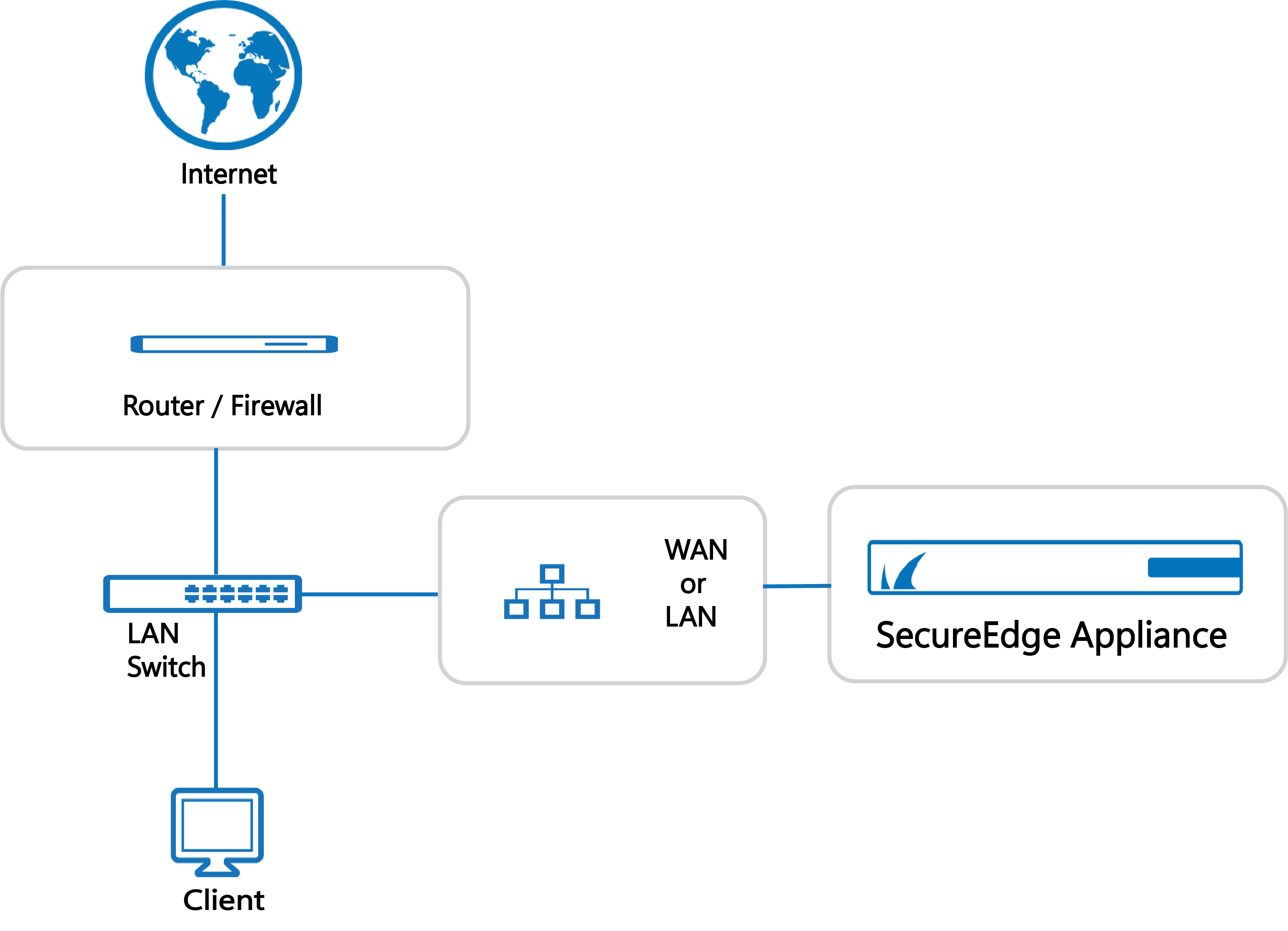
To configure a SecureEdge Site device as a proxy, you need to enable and configure the Proxy Connect feature. For more information on Proxy Connect, see How to Configure Proxy Connect.
For more information, see How to Migrate WSG Forward Proxy Setups.
Policy Migration
Barracuda Networks Technical Support will take care of the migration for you. To contact our technical support, visit the following link: https://www.barracuda.com/support/contact. When transitioning from Web Security Gateway to SecureEdge, the following components will be seamlessly migrated:
BLOCK/ACCEPT > Exceptions – Applications used to set policy exceptions for specific users or groups.
BLOCK/ACCEPT > Content Filter – Used to apply content category filters to control Internet access for users based on the content of the websites they visit.
BLOCK/ACCEPT > Custom Category – Used to create custom categories from selected domains or built-in web content categories.
Users/Groups – IP subnets/groups used to create a group for a range of IP addresses.
Note that sub-categories in SecureEdge might not have the same main category as in the Web Security Gateway (WSG). For example, Dating in WSG is categorized under Adult Material, whereas in SecureEdge it is categorized under Society and Lifestyle. However, if you block Dating in WSG, it will still be blocked in SecureEdge when migrated.
Use Cases
After you have replaced your existing Barracuda Web Security Gateway, you can expand the usage of your SecureEdge Site device at no additional cost to cover the following use cases:
Next-Generation Firewall
Every SecureEdge Site device also includes a powerful next-generation firewall with Application Control, Advanced Threat Protection, and a powerful Intrusion Prevention System (IPS). To set up your SecureEdge Site device as a next-generation firewall, see Policies.
Zero Trust Network Access
Every SecureEdge Site device* includes five licenses for ZTNA access to start your transition from VPN-based remote access to a much more secure and easy-to-use ZTNA-based approach. For more information on using ZTNA with SecureEdge, see ZTNA.
*Does not apply to SecureEdge devices deployed via the MSP licensing model.
SD-WAN
If you have two or more SecureEdge Site devices deployed, you can make use of the built-in SD-WAN functionality for better application performance and enhanced connectivity throughout your organization. For more information, see SD-WAN.
Further Information
For more information on how to configure the modern security features on SecureEdge, see Secure Web Gateway (SWG).
