Barracuda uses techniques such as natural language processing, account statistics, and domain assessment to detect signals to protect you from potential targeted attacks. For example, Barracuda can analyze language patterns and detect language often used in attack emails. It can then send suspicious emails to your Junk Email folder, protecting you from potential attacks.
This article provides a general sense of the signals used by Barracuda for Impersonation Protection. Note that it would be irresponsible to disclose the inner workings of Barracuda Networks' Impersonation Protection.
Barracuda Networks also detects signals to protect you from account takeover (ATO) attacks. See Account Takeover Attacks and their Signals for details.
Types of Phishing Attacks
Barracuda protects against the targeted types of phishing attacks described here.
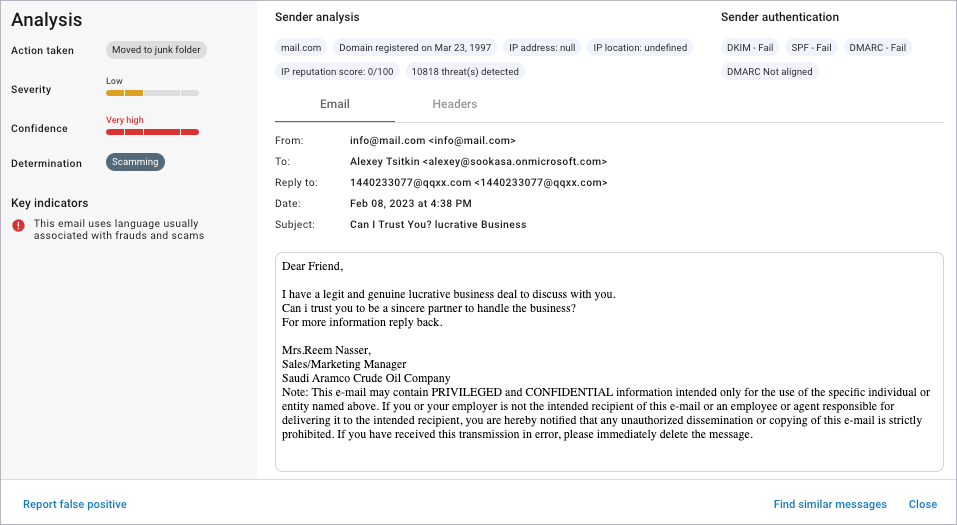
Scamming
In a scam, an unusual request is made of the recipient – like a request from a stranger, asking the target to send a large amount of money in return for a share in some other large sum of money.
The Severity score for Scamming attacks is Low.
For more information, see Getting Started.
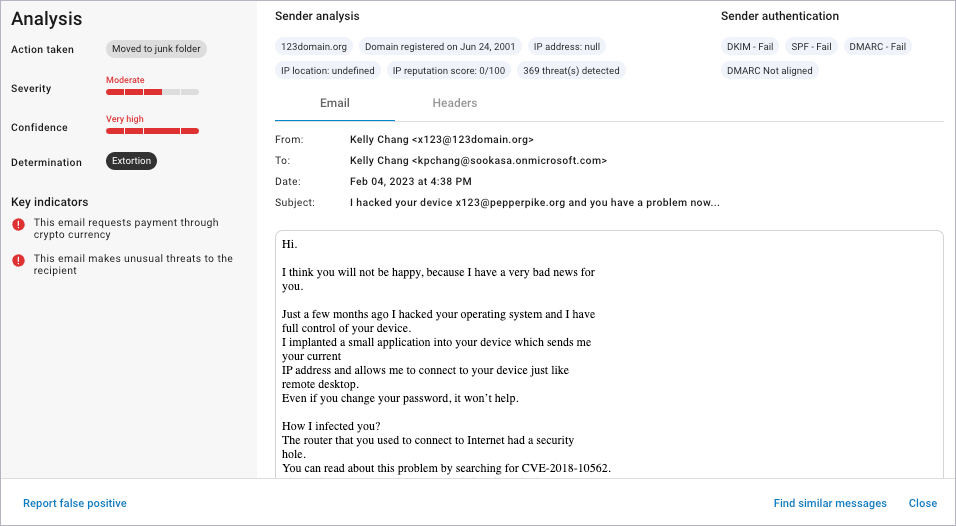
Extortion
Similar to standard extortion, online extortion involves demands for large payments to a stranger in exchange for their not revealing some embarrassing information about the target.
The Severity score for Extortion attacks is Moderate.
For more information, see Getting Started.
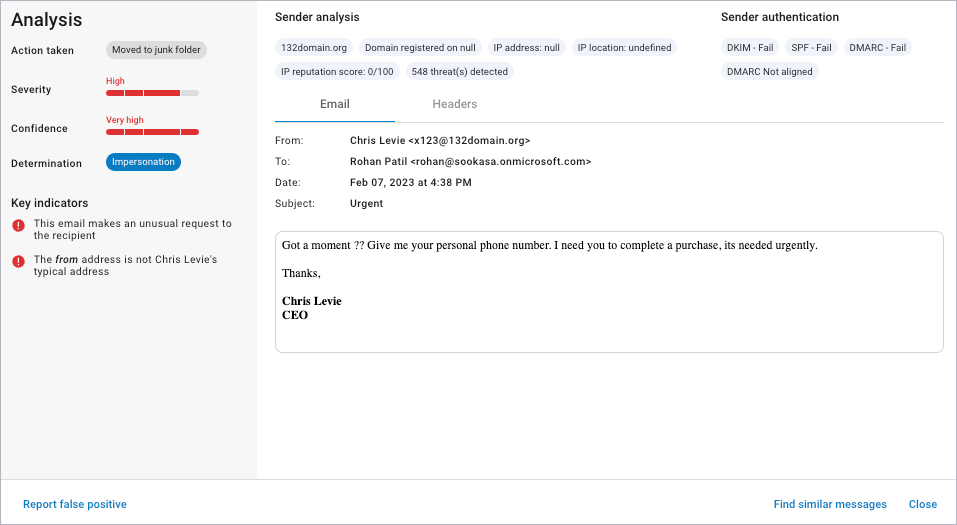
Impersonation
Impersonation attacks might impersonate a domain, an employee, or both.
The sender might purposely misspell the From address, altering it slightly, so the change is barely perceptible. The target might respond to a nefarious request, thinking the request is coming someone they know and trust.
The attacker might also assume the identity of an employee, assuming a position of trust with other employees. With this trust, the attacker can gain access to important corporate information or convince another employee to perform a task, like a bank transfer to a nefarious account.
The Severity score of Impersonation attacks is High.
For more information, see Getting Started.
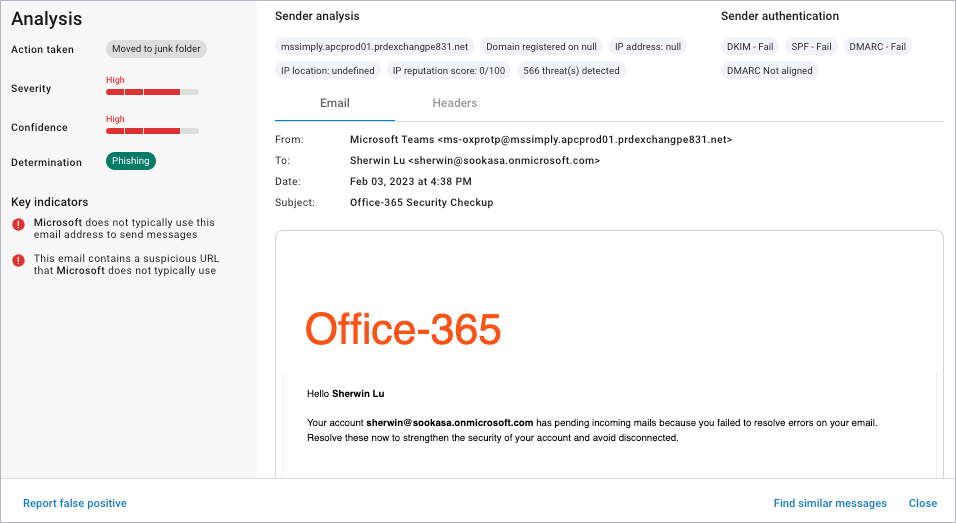
Phishing
The attacker impersonates a well-known service, like a bank or an Internet service provider, and asks the user to click a link and log into their account. The attacker can then steal the user's login credentials.
The Severity score for Phishing attacks is High.
For more information, see Getting Started.
Signals
Here is a sampling of the signals Barracuda uses to detect potential attacks:
- The email:
- uses language usually associated with frauds and scams.
- makes an unusual or urgent request of the recipient.
- requests payment through cryptocurrency.
- makes unusual threats to the recipient.
- contains a link to a URL not usually used by the sender.
- The From address is not the sender’s typical address.
- The Reply To or Sender domain appears to be impersonating another domain.
