Overview
Cloud-hosted deployment of the Barracuda Web Application Firewall for Azure currently supports One-Arm Proxy Mode. For more information, see Configuring One-Arm Proxy Mode.
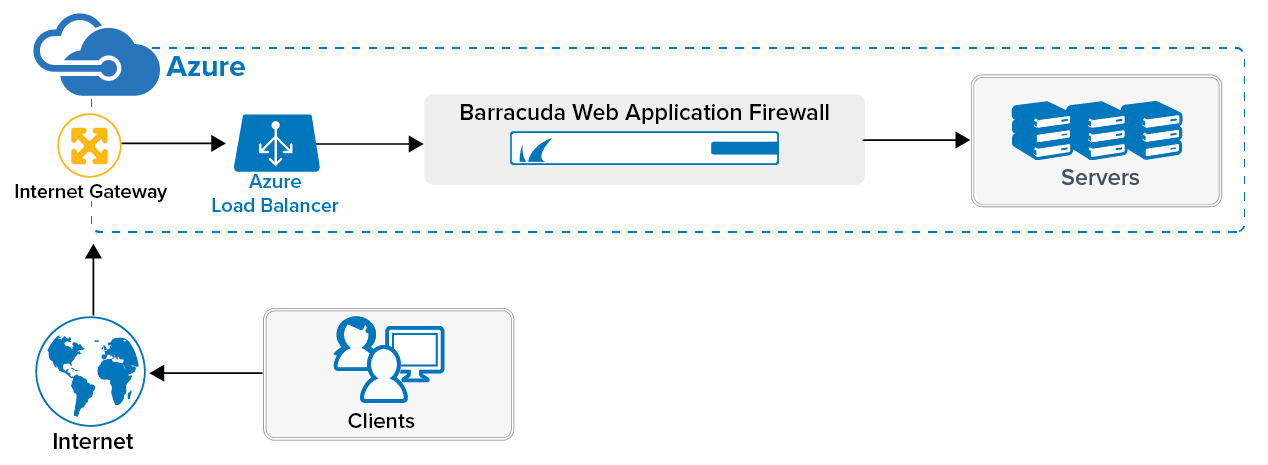
To meet a variety of performance requirements, different VM sizes are supported by the Barracuda Web Application Firewall. Depending on the VM size, you can have:
Up to 8 vCPU.
Up to 64 GB of memory.
See Supported Virtual Machine Size.
Licensing Options
The Barracuda Web Application Firewall for Azure is available with the Bring Your Own License (BYOL) and Hourly / Metered options.
Bring Your Own License (BYOL)
With the Bring Your Own License (BYOL) option, you are required to get the Barracuda Web Application Firewall license token, either by:
Providing the required information for a free evaluation at https://www.barracuda.com/purchase/evaluation OR
Purchasing online at https://www.barracuda.com/purchase.
With this license option, there will be no Barracuda Web Application Firewall software charges; however, Microsoft Azure usage charges on Microsoft will apply.
BYOL Models and Instance Types
For BYOL, Barracuda Networks offers four models. The table below lists each model and the number of cores supported.
If you want to increase the performance of a license that you have already purchased, you can buy a license with more cores from Barracuda Networks and reconfigure your instance.
Barracuda Web Application Firewall for Azure Model | Number of vCPUs Supported |
|---|---|
Level 1 | 1 |
Level 5 | 2 |
Level 10 | 4 |
Level 15 | 8 |
Supported Virtual Machine (VM) Size
The table below lists the VM sizes that are supported by the Barracuda Web Application Firewall.
Virtual Machine Size | vCPU | Memory |
|---|---|---|
Standard_B1ms | 1 | 2 |
Standard_B2ms | 2 | 8 |
Standard_B4ms | 4 | 16 |
Standard_B8ms | 8 | 32 |
Standard_D2s_v3 | 2 | 8 |
Standard_D4s_v3 | 4 | 16 |
Standard_D8s_v3 | 8 | 32 |
Standard_D2_v3 | 2 | 8 |
Standard_D4_v3 | 4 | 16 |
Standard_D8_v3 | 8 | 32 |
Standard_DS1_v2 | 1 | 3.5 |
Standard_DS2_v2 | 2 | 7 |
Standard_DS3_v2 | 4 | 14 |
Standard_DS4_v2 | 8 | 28 |
Standard_D1_v2 | 1 | 3.5 |
Standard_D2_v2 | 2 | 7 |
Standard_D3_v2 | 4 | 14 |
Standard_D4_v2 | 8 | 28 |
Standard_A1_v2 | 1 | 2 |
Standard_A2_v2 | 2 | 4 |
Standard_A4_v2 | 4 | 8 |
Standard_A8_v2 | 8 | 16 |
Standard_A2m_v2 | 2 | 16 |
Standard_A4m_v2 | 4 | 32 |
Standard_A8m_v2 | 8 | 64 |
Standard_D2s_v3 | 2 | 8 |
Standard_D4s_v3 | 4 | 16 |
Standard_D8s_v3 | 8 | 32 |
Standard_D2_v3 | 2 | 4 |
Standard_D4_v3 | 4 | 16 |
Standard_D8_v3 | 8 | 32 |
Standard D4as_v4 | 4 | 16 |
Standard D2as_v4 | 2 | 8 |
Standard D2as_v5 | 2 | 8 |
You can add multiple Barracuda Web Application Firewall instances under one cloud service and load balance the traffic between the deployed instances to increase the throughput. For more information on load balancing, see the Load Balancing For Clustered Barracuda Web Application Firewall Instances in the Old Microsoft Azure Management Portal article.
Pay As You Go (PAYG)
With the Pay As You Go (PAYG) licensing option, you complete the purchase or evaluation of the Barracuda Web Application Firewall entirely within the Microsoft Azure gallery. After the instance is launched, it is provisioned automatically. You are charged hourly for both the Barracuda Web Application Firewall software and Microsoft Azure usage on Microsoft.
PAYG Model and Instance Types
For more information on supported instance types, and default vCPU, default memory and hourly pricing, see Barracuda Web Application Firewall Pricing Details.
If you want to increase the performance of an existing VM, configure it with a larger instance type on Microsoft Azure, and you will be charged accordingly by Microsoft. The VM will automatically be reconfigured by Microsoft with the resources and capabilities of the larger instance type.
