Overview
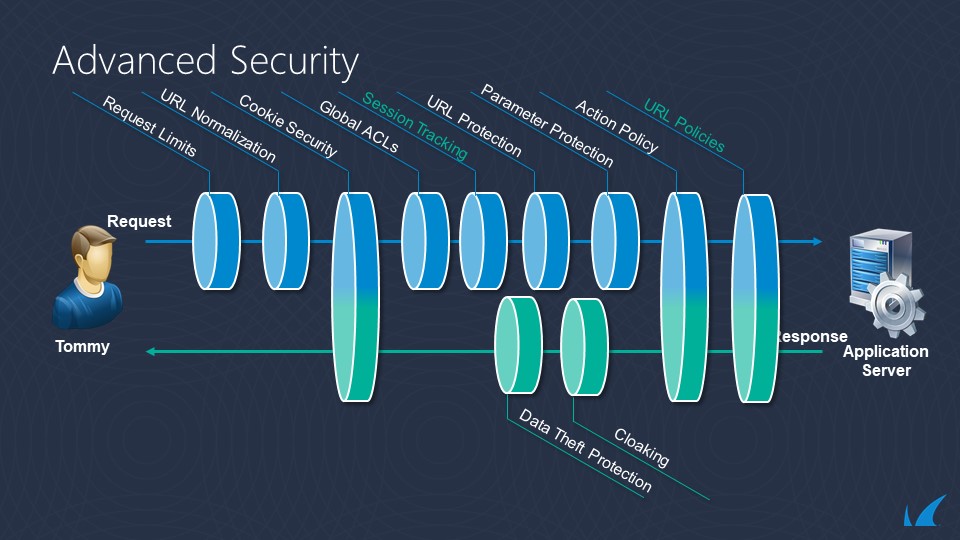
The following diagram shows the location of enforcement of advanced security policies in the request/response evaluation flow.
Barracuda Campus is getting an upgrade!
We are excited to announce that Barracuda Campus will migrate to a new platform around mid-January 2026. Please see the announcement on the Campus Dashboard to find out more.
The following diagram shows the location of enforcement of advanced security policies in the request/response evaluation flow.
