Perform the steps below to import the Barracuda Web Application Firewall for AWS Pay-As-You-Go CloudFormation Template and deploy the instance:
- Go to the AWS Marketplace, type Barracuda Web Application Firewall for AWS in the Search AWS Marketplace text box and click GO.
- Select Barracuda Web Application Firewall for AWS
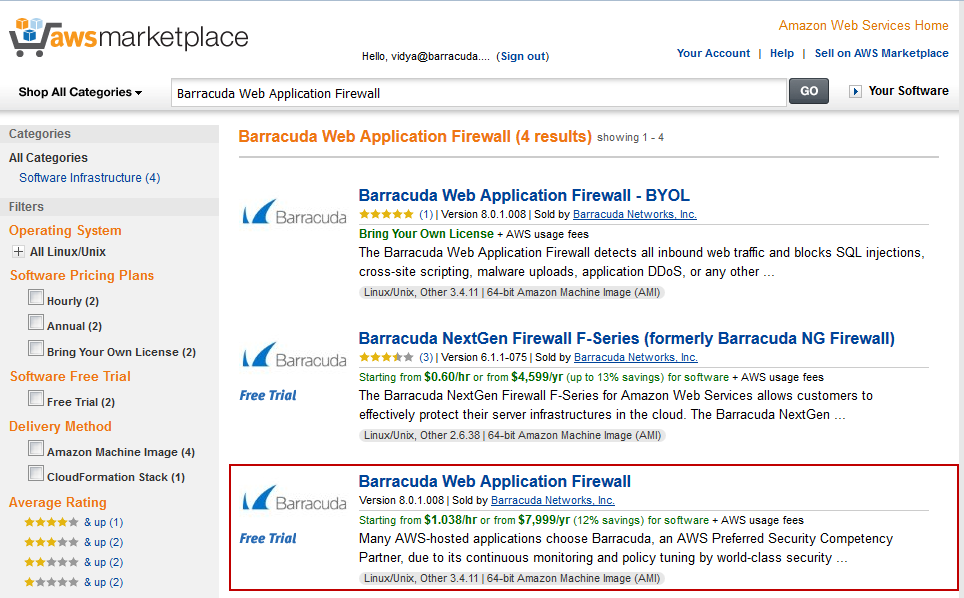
- The Barracuda Web Application Firewall page appears on the AWS Marketplace.
- In the Pricing Details panel:
- Select the region for the instance to be deployed from the “For region” drop-down list.
- Select Barracuda Web Application Firewall for AWS as Delivery Methods.
- Click Continue.
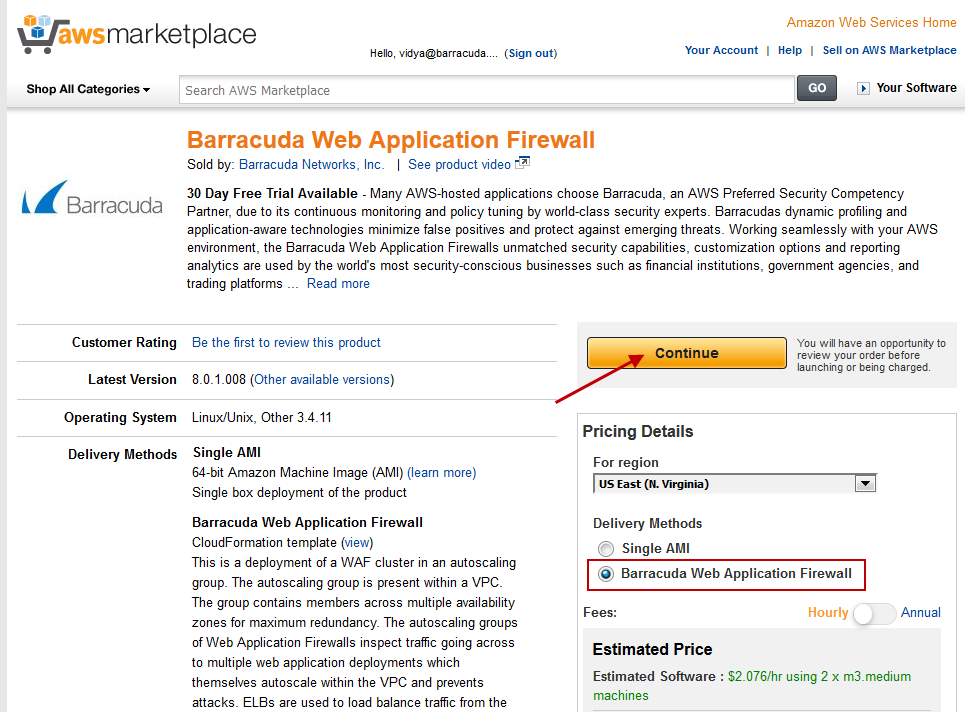
- In the Launch on EC2 page:
- Select the Barracuda Web Application Firewallversion that you want to deploy on AWS.
- Select the region for the instance.
- Ensure the Deployment Options is set to Barracuda Web Application Firewall for AWS.
- Check the software pricing for subscription term (Hourly or Annual).
- Click Launch with CloudFormation Console.
- In the Create A New Stack page, click Next:
- On the Specify Details page, do the following configuration:
- In the Specify Details section:
- Enter a name for the CloudFormation stack in the Stack Name field.
In the Parameters section, specify values for the following:
Network Configuration Parameter Name Description Which VPC should this be deployed to? Select the VPC that you wish to deploy the Barracuda Web Application Firewall instance(s) from the drop-down list. Availability Zone(s) Select the availability zones from the multi-select drop-down list. The VPC you choose to deploy in must be available across these availability zones. Note: It is recommended to deploy the instances in multiple availability zones. Subnet ID(s) Select the subnet ID(s) associated with the availability zone(s) where the Barracuda Web Application Firewall instance(s) needs to be deployed. Note that these subnets must be part of the VPC that you choose. Elastic Load Balancer(s) Enter the name of the elastic load balancer(s) (ELB) that needs to be used to load balance/distribute the traffic between the Barracuda Web Application Firewall(s). The ELB(s) should be connected to all the subnets that are used for this deployment and be part of the VPC that is chosen for this deployment.
Auto Scaling Configuration Parameter Name Description Instance Type Select an instance type depending on your requirement. Minimum Instances Enter the minimum number of Barracuda Web Application Firewall instance(s) that needs to be up and running continuously in the Auto Scaling group. Default: 1
Maximum Instances Enter the maximum number of Barracuda Web Application Firewall instance(s) to be deployed in the Auto Scaling group. Default: 4
Notification Email Enter the email address(es) to which you want Amazon SNS to send email notifications. Barracuda Web Application Firewall Bootstrapping Configuration Parameter Name Description Service Name Enter a name for the service that needs to be created on the Barracuda Web Application Firewall(s). Service Port Enter the port number on which the service is listening to.
Server IP/FQDN Enter the IP address of the server, or Fully Qualified Domain Name (FQDN) of the ELB front-ending the servers that needs to be protected by the Barracuda Web Application Firewall(s) .
If you are deploying a downstream ELB, specify the FQDN of the ELB to which the Barracuda Web Application Firewall needs to be connected.Server Port Enter the port number associated with the server mentioned in Server IP/FQDN. 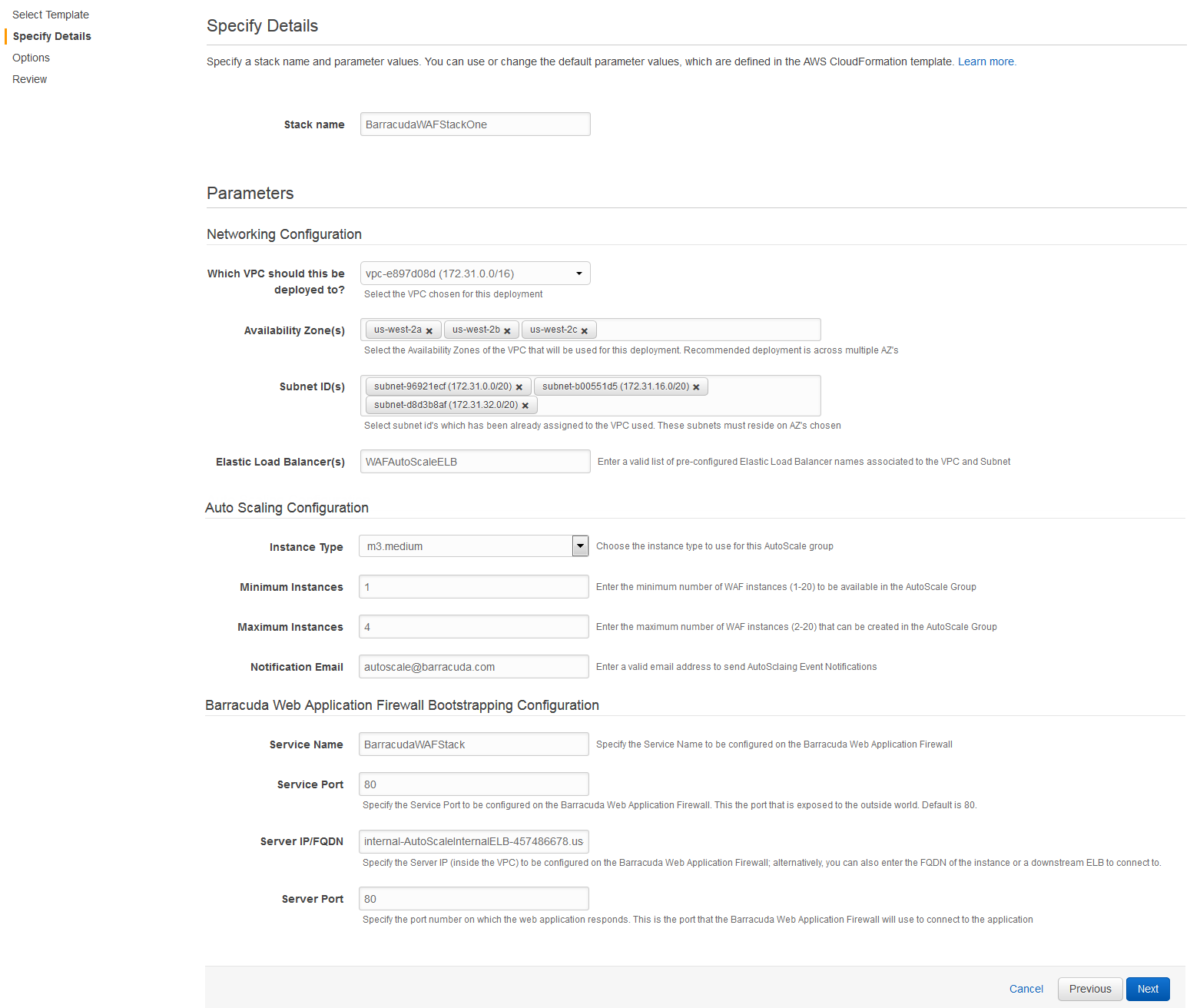
- In the Specify Details section:
- Click Next to continue.
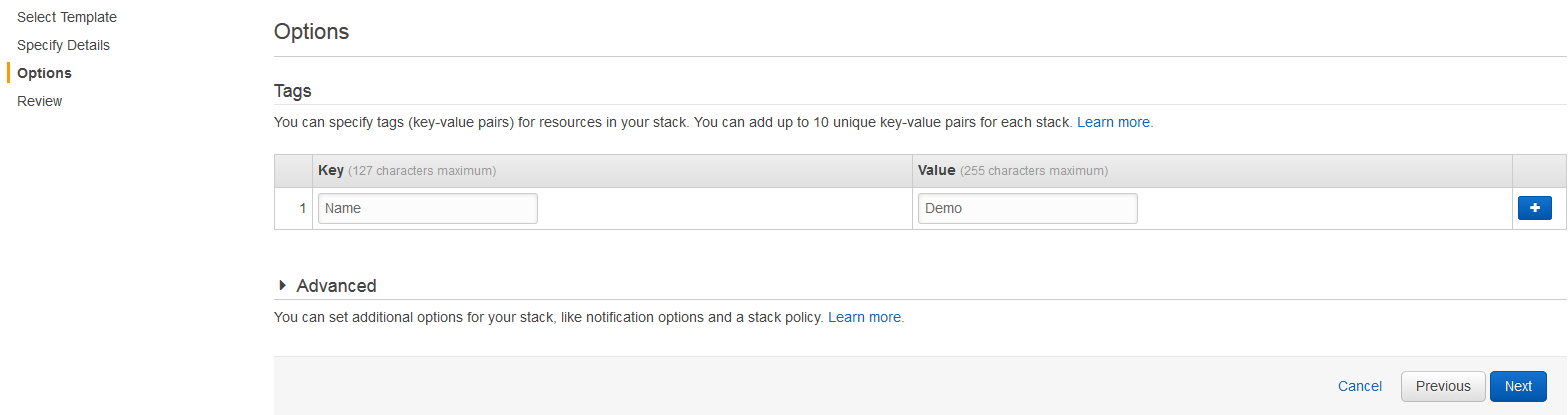
- On the Options page, enter a key-value pair to identify the instance(s) of this stack. Click Next.
On the Review page, verify the values you entered, select the IAM capability check box, and click Create.
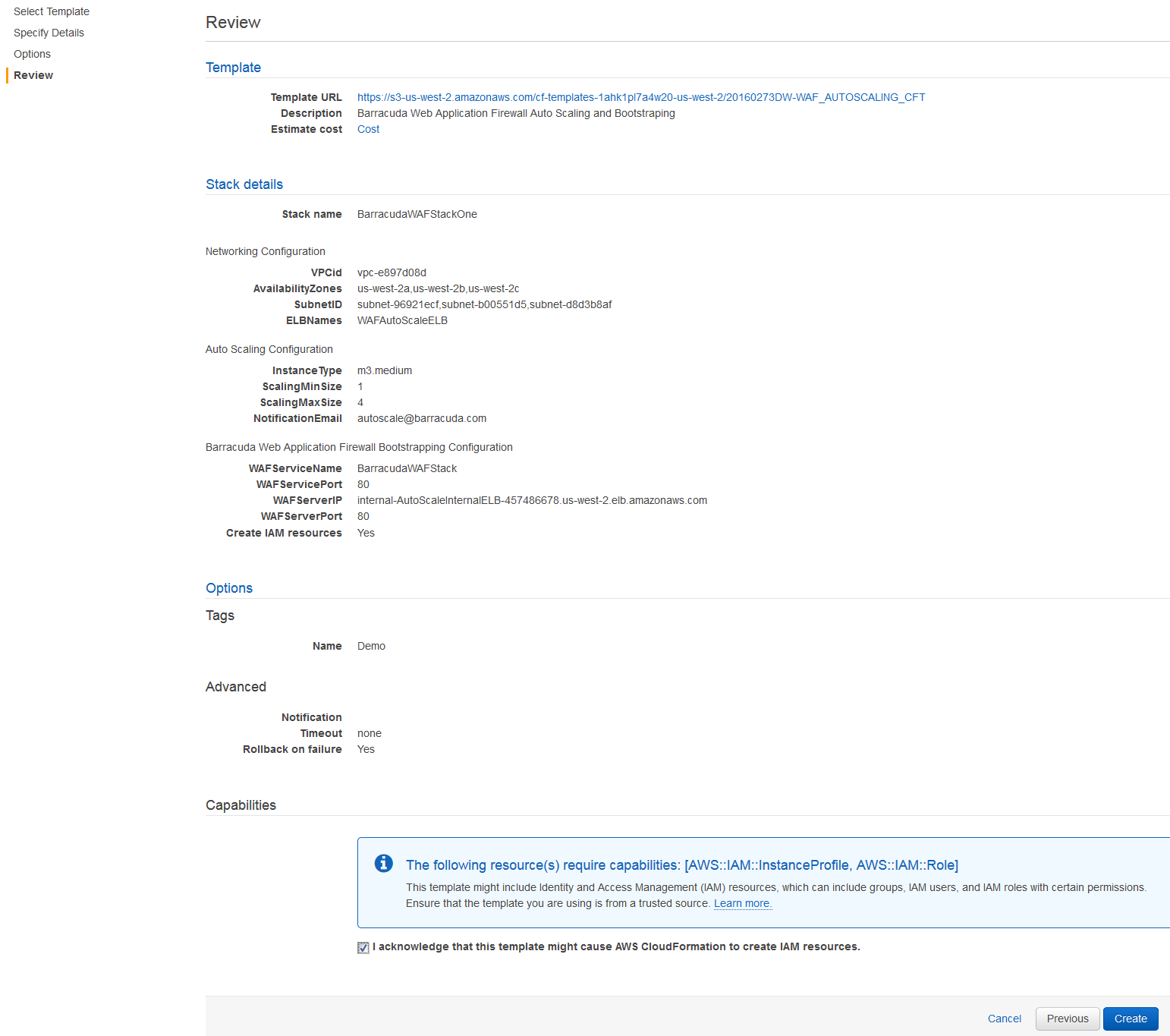
As per the configuration in the CFT above:
1. A stack with the name “BarracudaWAFStackOne” will be created.
2. Deploys one (1) Barracuda Web Application Firewall VM in one of the specified availability zones (us-west-2a/us-west-2b/us-west-2c), and subnets (subnet-b00551d5/subnet-d8d3b8af/subnet-96921wcf ) with instance type as m3.medium, and gets added to the "WAFAutoScaleELB" Elastic Load Balancer.
3. Sends notification to autoscale@barracuda.com.
4. Scales up the instance (up to total of 4) whenever the alarm triggers.
5. Creates a service on the Barracuda Web Application Firewall with port 80 that protects the server(s) (FQDN: internal-AutoScaleInternalELB-457486678.us-west-2.elb.amazonaws.com on port 80). The created service can be accessed over the ELB, i.e., WAFAutoScalELB, using port 80.
6. Creates an IAM role that has explicit access to the created S3 bucket. The IAM role is responsible for storing and retrieving the information of the deployed Barracuda Web Application Firewalls in this stack.
7. Tags the deployed Barracuda Web Application Firewall VMs with Name as Demo.
8. If AWS is unable to create the stack based on the inputs you provided, the stack will roll back.
- On the Specify Details page, do the following configuration:
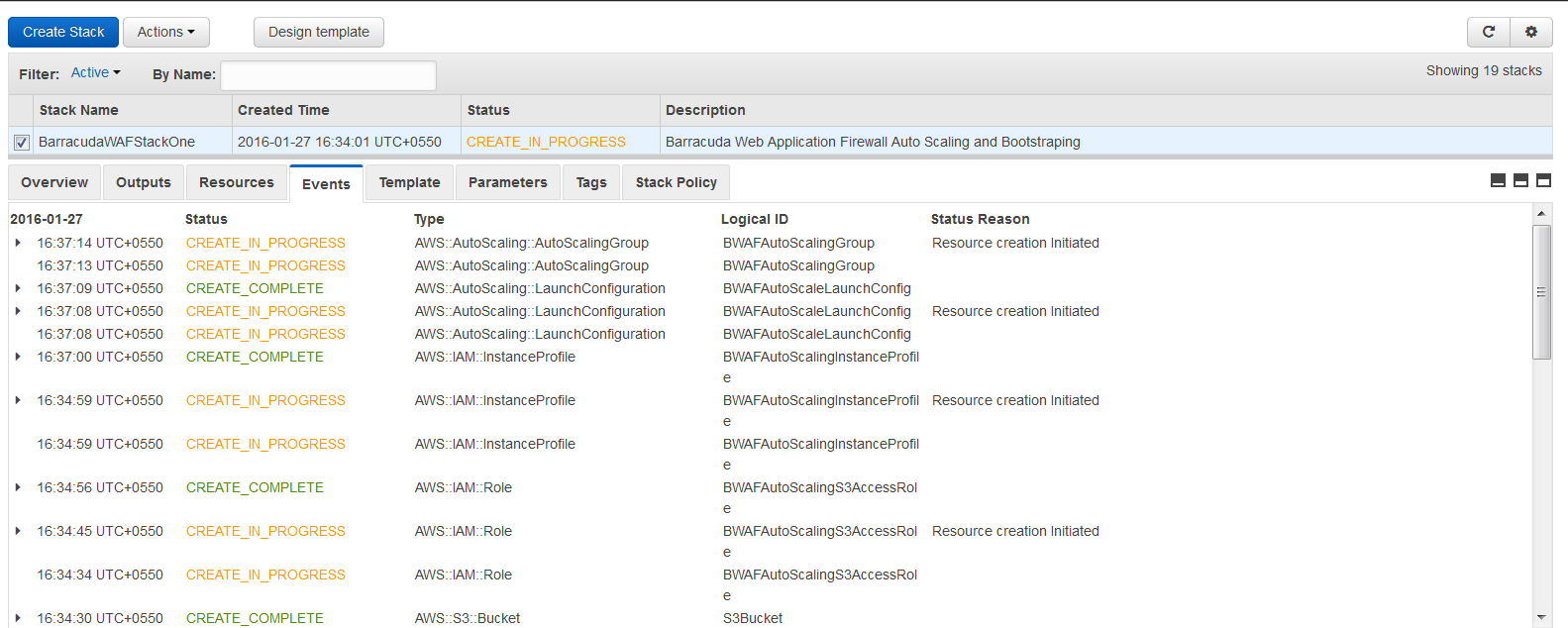
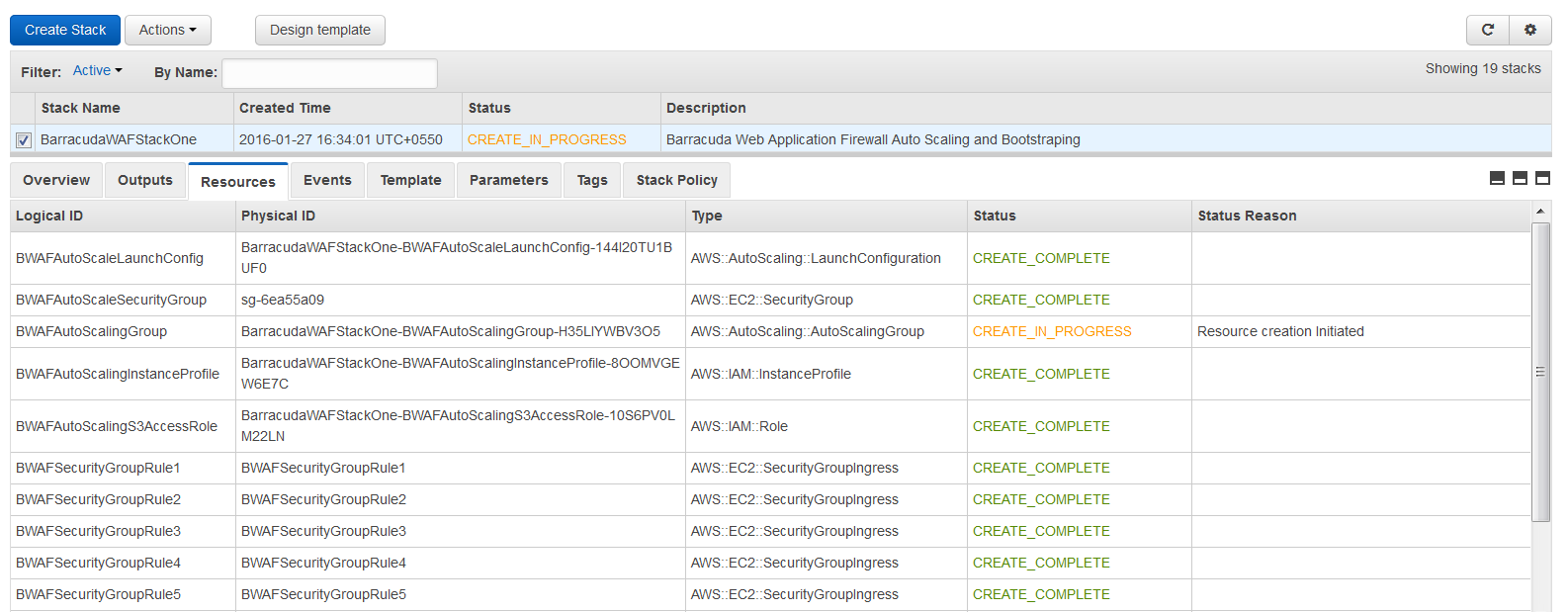
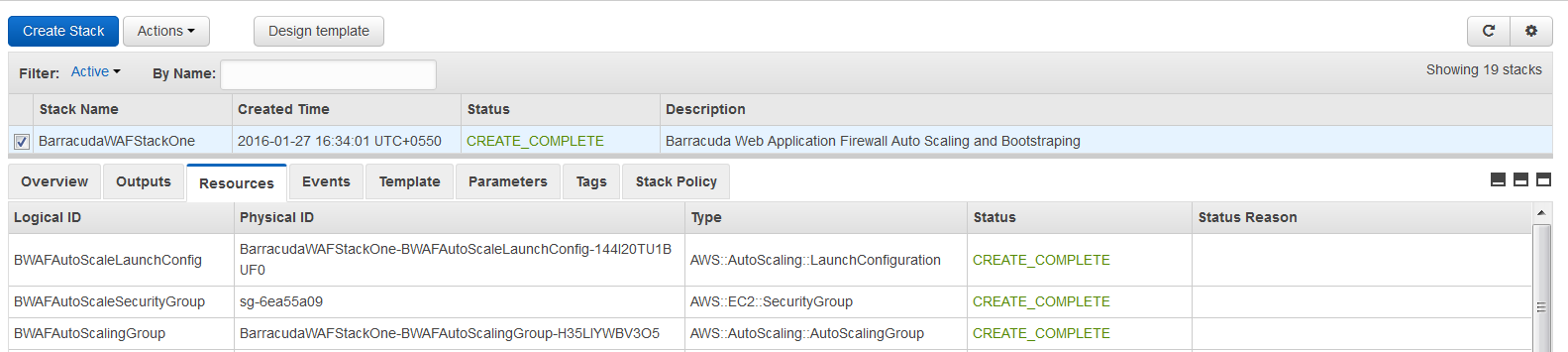
- The CFT now starts its operation. You can see the CREATE_IN_PROGRESS status displayed on the CloudFormation Management Console for the stack. Select the tabs and see the status of events and resources that are being created. An example of the successfully created resources is available in the screenshot below:
Next Step
Continue with the Verify the Instance in the Auto Scaling Group article.
