The Barracuda Web Application Firewall provides independent routing entities called Network Groups. Network settings such as routes and ACLs are configured individually for each Network Group.
You can configure one Network Group for Management Path and multiple Network Groups for Data Path in the Barracuda Web Application Firewall.
- Management Path is the traffic flow from an administrator’s system or network to the Barracuda Web Application Firewall. A Network Group for the management interface controls management access of the Barracuda Web Application Firewall. Configurations are specific to a unit and are not synchronized with the Peer unit in a High Availability (HA) cluster.
- Data Path is the traffic flow from clients to the back-end server which needs to be secured or routed through the Barracuda Web Application Firewall. Multiple network groups can be configured on the Data Path to provide the routing flexibility required to deploy the appliance in complex networks. A Vsite encompasses one Network Group and its associated Services. Administrators can configure multiple Network Groups by configuring multiple Vsites. A network group is automatically created for the system during the initial configuration of the physical interfaces. Network settings in the network groups of the Vsite are evaluated first and then the network settings under System Network Group is evaluated before a packet routing or filtering decision is made. All configuration for data path network groups is synchronized with the Peer unit in the HA cluster.
The routing decisions for the Management Path and Data Path traffic are based on the respective routing tables. The Data Path traffic is first matched with the set of routes configured for the specific Vsite. If the traffic does not match any Vsite routing entries, it is compared to System routing entries. If it matches neither Vsite nor System routing entries, the packet is dropped.
The Barracuda Web Application Firewall supports the following routing tables:
- Management – Routes to process traffic through the Management interface.
- System - The main routing table used for processing all Data Path traffic. The System table includes WAN (WAN default gateway) and LAN interfaces configured on the BASIC > Administration page.
- Vsites – Routes designated for each Vsite configured on the BASIC > Services page. Each Vsite has its own network routing table to which the incoming/outgoing traffic is compared in order to process the traffic.
Accessing External Servers from the Barracuda Web Application Firewall
External servers can be configured on the following web interface pages:
- Authentication Services on ACCESS CONTROL > Authentication Services.
- SNMP Trap Receivers on BASIC > Administration.
- Email Notification on BASIC > Administration.
- DNS Configuration on BASIC > IP Configuration.
- Proxy Server Configuration on BASIC > IP Configuration.
- Export Logs on ADVANCED > Export Logs.
- External Authentication Servers on ADVANCED > Admin Access Control.
- NTP Servers on ADVANCED > System Configuration.
The Barracuda Web Application Firewall uses Interface for System Services to forward the packets to access any of the external servers mentioned above, whose IP address does not fall within the network of configured virtual interfaces. You can configure Interface for System Services on the BASIC > IP Configuration page.
To override the route, configure a host-specific static route within the network group from which the server is accessible.
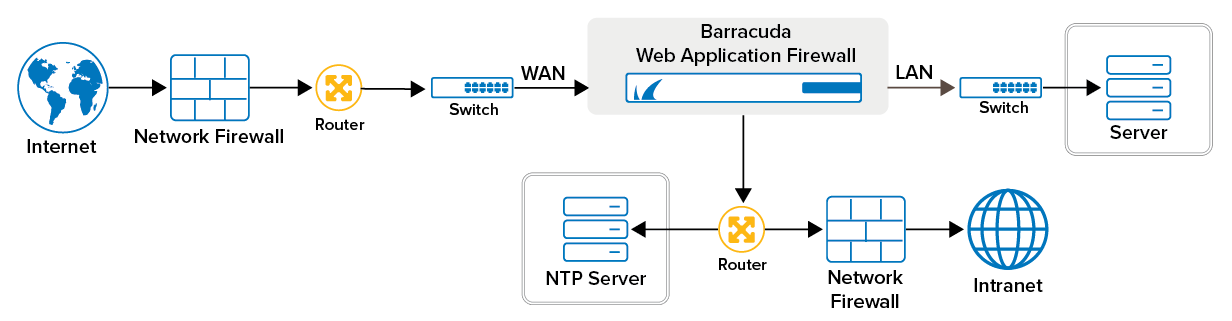
Example: External server reachable through a network group called Management.
In this example, suppose you have an NTP server that is reachable though the Management network group and your Interface for System Services is set to WAN. You can configure a specific static route for the NTP server within the Management network group on the NETWORKS > Routes page. Alternatively you can set your Interface for System Services to Management.
If the Management default gateway is 10.11.25.254 and the NTP server IP address is 10.11.17.40, which is reachable via gateway 10.11.25.254, then you can add a static route on the Management Network Group as host 10.11.17.40 and gateway 10.11.25.254.
You can configure the network components by using the Vsite, Ports, VLAN, Interfaces, NAT, Routes, ACL, and Network Configuration pages in the NETWORKS tab. The network components are:
