Introduction
The Barracuda Web Application Firewall enables administrators to configure security rules with varying degrees of granularity. A security policy, comprised of security settings, is shared by multiple applications.
A newly configured service originally uses the default security policy, so all URLs and parameters are compared to the default security policy settings. The Barracuda Web Application Firewall applies rules to traffic and generates a log of rule violations viewable in the BASIC > Web Firewall Logs page.
You can use the Web Firewall Logs to evaluate rule violations and, when warranted, to create exceptions to the rule violated. Exceptions can apply globally if they modify the security policy, which affects all services using that policy. Or, you can apply an exception locally that only applies to a specific website or URL. To create a fine-grained exception, use the WEBSITES > Allow/Deny or WEBSITES > Website Profiles pages.
The default security policy associated with a service can sometimes block genuine requests, which are called false positives. To reduce false positives, you can enable Exception Profiling for desired websites on the WEBSITES tab. Exception profiling uses heuristics displayed on the WEBSITES > Exception Heuristics page to identify false positives. You can set the exception profiler to automatically refine security policy rules for the respective site section by setting Request Violation Handling to Auto on the Exception Heuristics page; alternatively, set Request Violation Handling to Manual if you want the profiler to generate policy recommendations under Pending Recommendation on WEBSITES > Exception Profiling. In this case, the administrator must review the violations, and manually apply desired fixes. See Using Exception Profiling to Generate Recommendations for Tuning.
Creating Exceptions Using the Web Firewall Logs
Once logged in to the unit, select Web Firewall Logs from the BASIC tab to search for a log entry believed to be a false positive. These log entries are in red and have an action of DENY (active mode) or LOG (passive mode).
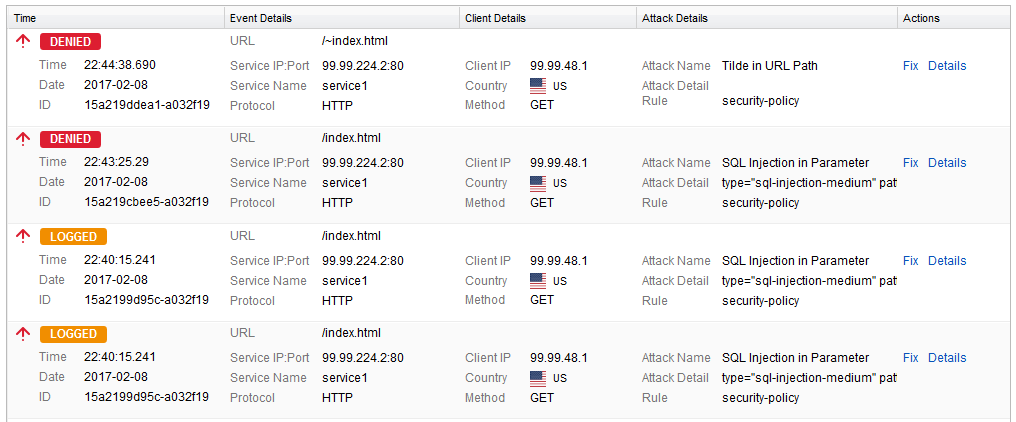
Scroll over to the right of the selected log and click Fix. A Policy Fix window appears.
The fix recommended by the Barracuda Web Application Firewall may be localized or global, depending upon which rule was violated. Accepting a recommendation can have the following impact:
- Web site profile (localized) modification: As the most fine-grained security, changes impact only a given URL or parameter.
- Security Policy (global) modification: As a policy shared by multiple applications, changes impact all applications using the security policy.
Examples of Fixes Suggested by the Barracuda Web Application Firewall
Example 1: Recommendation to Configure a Fine-Grained Rule.
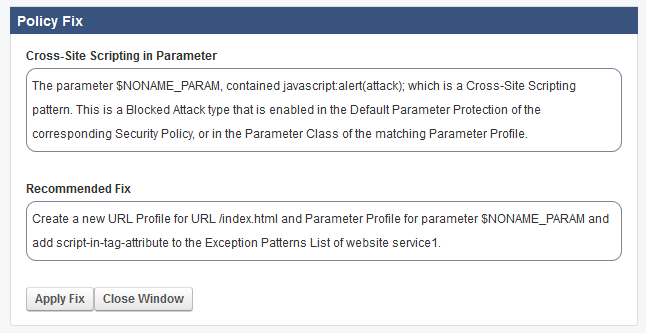
Following the recommendation to create a URL profile for /modules.php creates an exception only for that particular page.
Example 2: Recommendation to Change the Configuration in Security Policy.
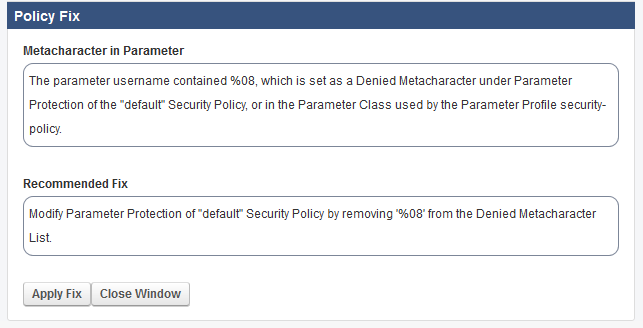
The suggested change to the Parameter Protection sub-policy of the default Security Policy would allow the meta-character (%08) in any parameter for any application using this security policy. To avoid an exception that applies globally, you can add an exception that only applies to the URL or parameter noted in the log.
Manually Configuring a Fine-Grained Rule
When you want to apply a local exception instead of a recommended global fix, you need to manually do a two-step process.
Step 1: Figure Out the Exception Specifics from Web Firewall Logs.
- Scroll over to the selected log in the Web Firewall Logs and click Details.
- Select the URL.
- Note the parameter name in the Query String.
- Close the Web Firewall log Details window.
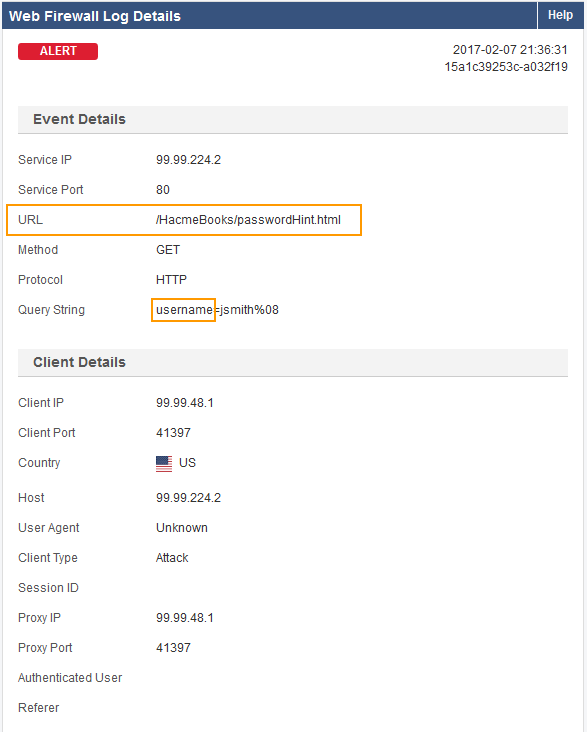
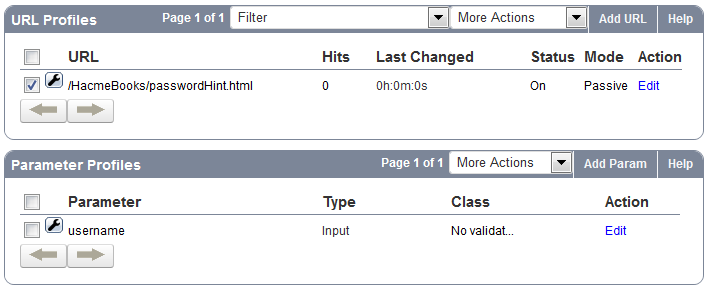
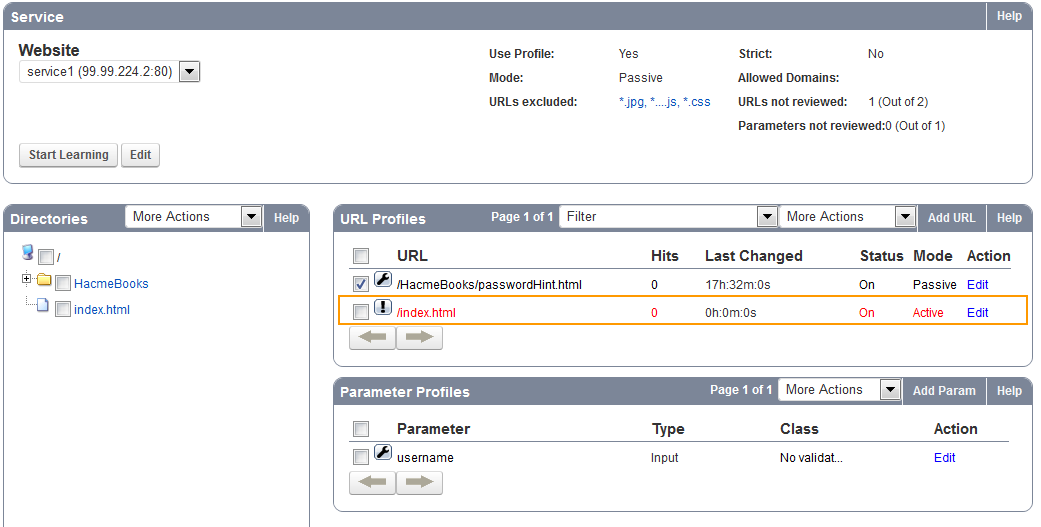
Example: For the log shown above – VIP is 192.168.9.96 – Port 80. The URL is /HacmeBooks/passwordHint.html and the URL has a parameter called ‘username’.
Step 2: Configure the Exception.
- From the WEBSITES > Website Profiles page, select the appropriate service from the Website drop-down list (192.168.9.96 : 80).
- In the URL Profiles section, click Add URL.
- The Create URL Profile window appears.
- Enter a name in the URL Profile Name field.
- Paste the URL into the URL field (/HacmeBooks/passwordHint.html).
- Click Add.
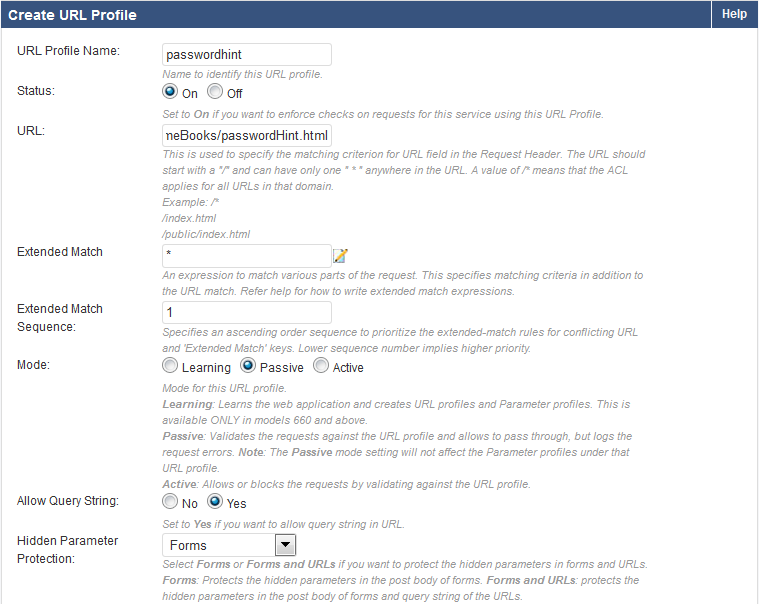
You should now see the new URL profile in the URL Profile section. Click Edit to make the necessary security exceptions to the URL. Click Save when done.
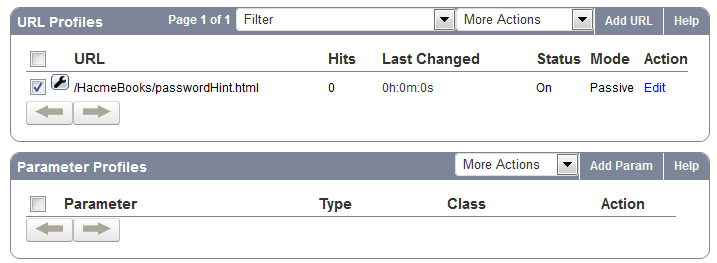
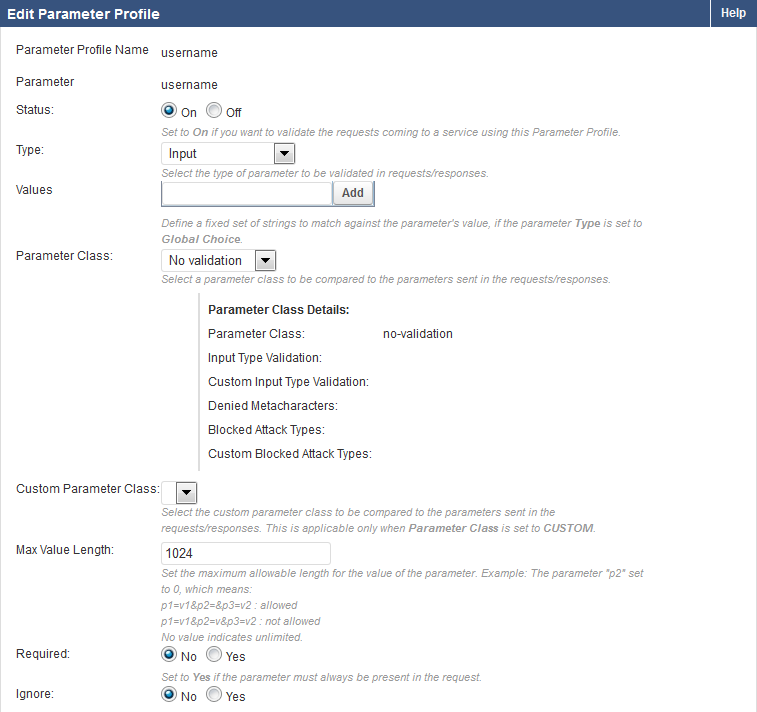
To specify parameter settings, you need to configure parameter profiles for the relevant URL Profile (Example: passwordHint).
- Click Add Param in the Parameter Profiles section.
- The Create Parameter Profile window opens.
- Select the appropriate URL profile from the drop-down list (Example: passwordHint).
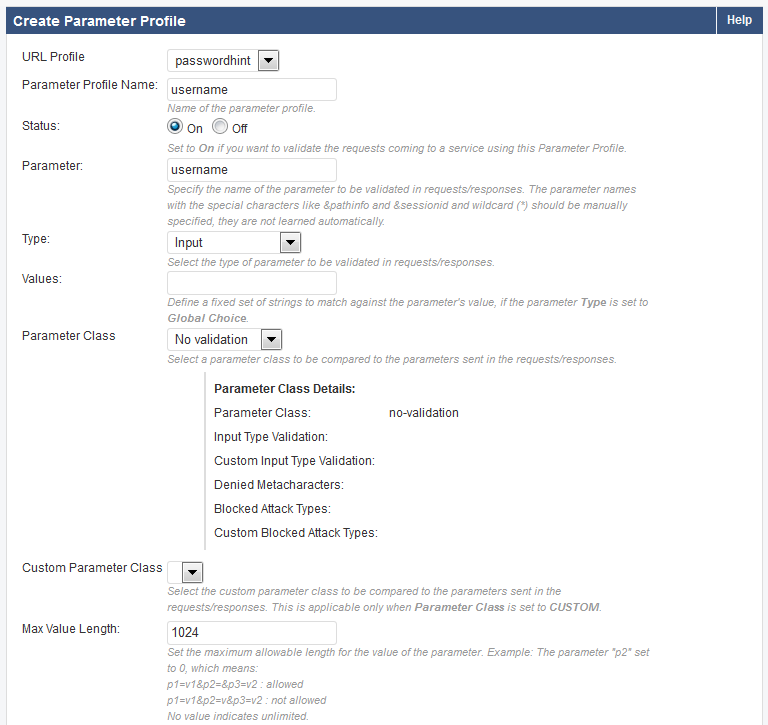
- Enter a name in the Parameter Profile Name field.
- In the Parameter field, enter the parameter that you noted from the details of the Web Firewall Logs.
- Select the appropriate Parameter Class – typically ‘No Validation’ is selected if it is not a specific class.
- Click Add.
You should now see the new parameter profile in the Parameter Profile section. Click Edit to make the necessary exceptions to the Parameter. Click Save when done.
The example below shows the created local exception to allow meta-character %08 in parameter username for URL profile passwordhint.
Using Exception Profiling to Generate Recommendations for Tuning
To configure exception profiling for a service:
- From the WEBSITES > Exception Profiling page, identify the service for which you want exception profiling enabled.
- Click Edit next to that service. The Edit Exception Profiling window appears.
- To learn from a trusted hosts group, select the trusted host group from the Trusted Hosts Group drop-down list and set Learn From Trusted Host Group to Yes. For more information, see Fine Tuning Security Settings for a Trusted Hosts Group using Exception Profiling.
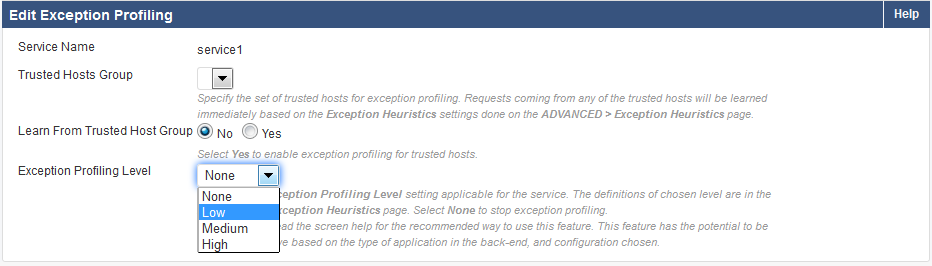
- To learn from untrusted traffic, select the level of tolerance to violations (Low, Medium, or High) from the Exception Profiling Level drop-down list. For more information on Exception Profiling, see How to Configure Exception Profiling .
- Click Save.
The figure below shows the Exception Profiling Level set to Low for untrusted traffic.
Exception profiling provides default settings for each violation type. The settings indicate how exceptions update profiles (Automatically, Manually, or not at all), how the new setting in the profile is generated (for example, increasing the current value, or accepting the observed value), and how many times the logged error needs to be seen before generating an exception (Trigger Count). These default settings for an Exception Profiling Level can be edited and saved on the WEBSITES > Exception Heuristics page.
The figure below displays the default set of heuristics for the Exception Profiling Level: Low.
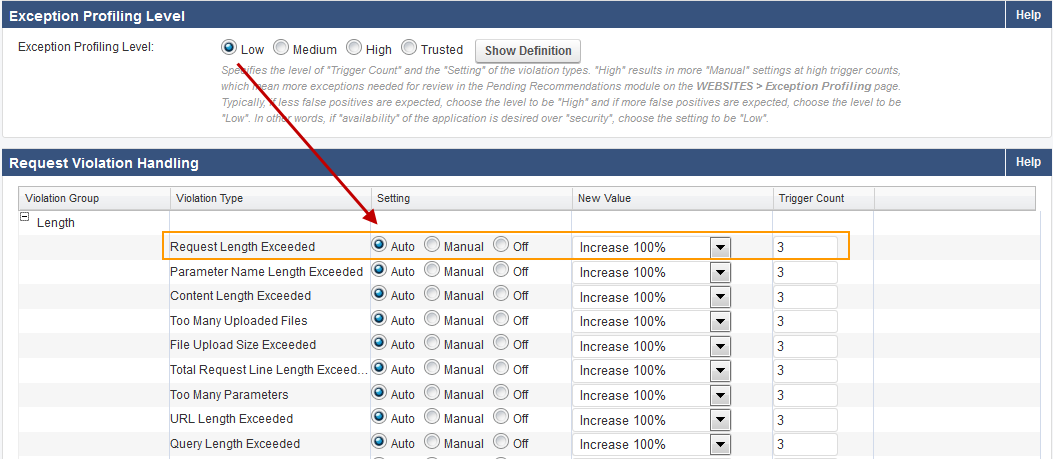
By default, all settings are set to Auto for the Exception profiling levels for untrusted traffic. The Trusted settings are either Auto or Off. For untrusted traffic, the Manual setting requires you to verify the exception before applying it, or you can turn exception profiling Off for a particular violation. If the traffic originates from trusted hosts, the trusted policy heuristics apply. If the traffic originates from non-trusted hosts, the selected Exception Profiling policy applies.
Manually Fine Tuning the Security Policy Using Exception Profiling
By default, each violation type is set to Auto on the WEBSITES > Exception Heuristics page. Therefore, whenever violations from unique sources are encountered the number of times indicated in Trigger Count, the profiles are automatically updated, thereby creating the respective profiles for the service. This applies only when exception profiling is enabled for the service on WEBSITES > Exception Profiling; that is, the Exception Profiling Level for the service is not equal to None.
To view encountered violations and manually apply desired recommended fixes, do the following:
Step 1: The Setting for the Desired Violation Type Should Be Manual.
- From the WEBSITES > Exception Heuristics page, select the Exception Profiling Level (Low, Medium, or High) you want to modify. Note: Trusted does not support Manual exception creation.
- In the Request Violation Handling section, identify the violation type(s) for which you wish to generate recommendations.
- Change Setting to Manual next to the violation type(s). Also, change the settings in New Value and Trigger Count if required.
- Click Save.
Step 2: Select the Recommendation and Apply Fix.
- Go to the WEBSITES > Exception Profiling page.
- In the Pending Recommendations section, view the recommendations for relevant violation type(s).
- Select the check box(es) next to the recommendations you want to fix, and click Apply Fix.
Examples for Tuning the Security Policy Using Exception Profiling
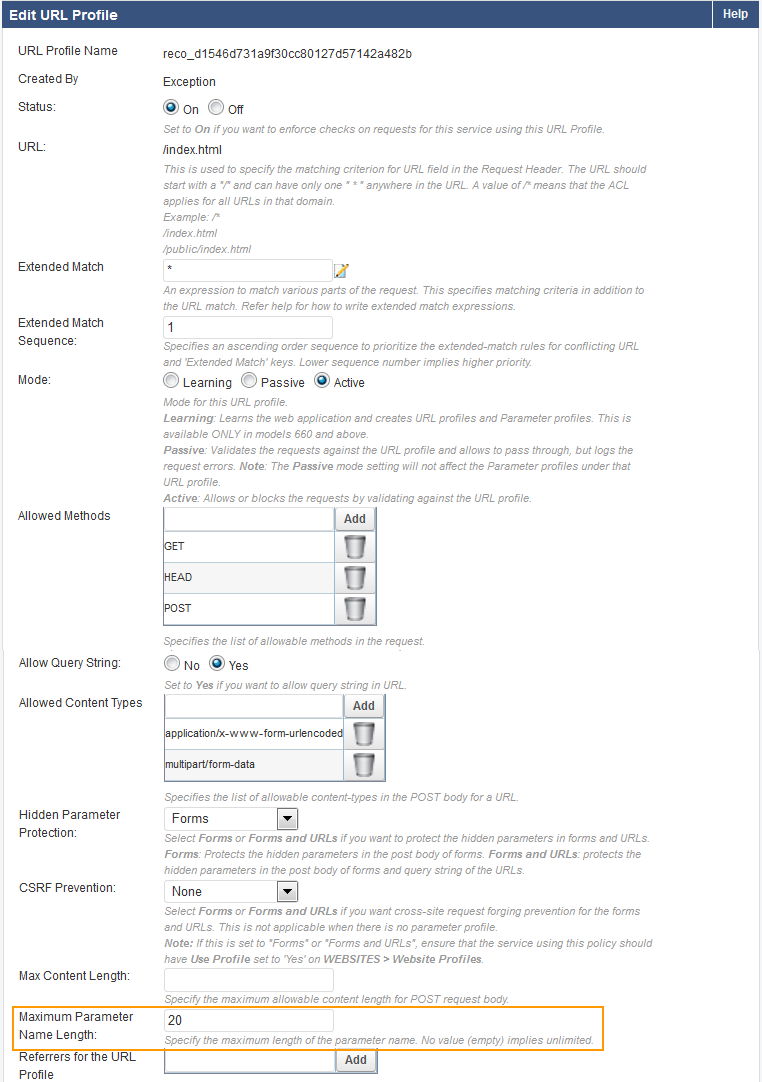
Example 1: Parameter Name Length Exceeded
In this example, the violation type Parameter Name Length exceeded is set to Manual, New Value is set to Increase 100%, and Trigger Count is set to 3 .
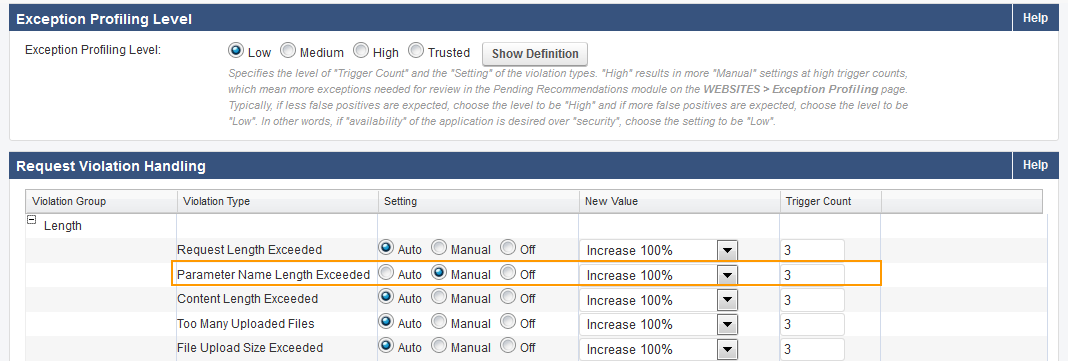
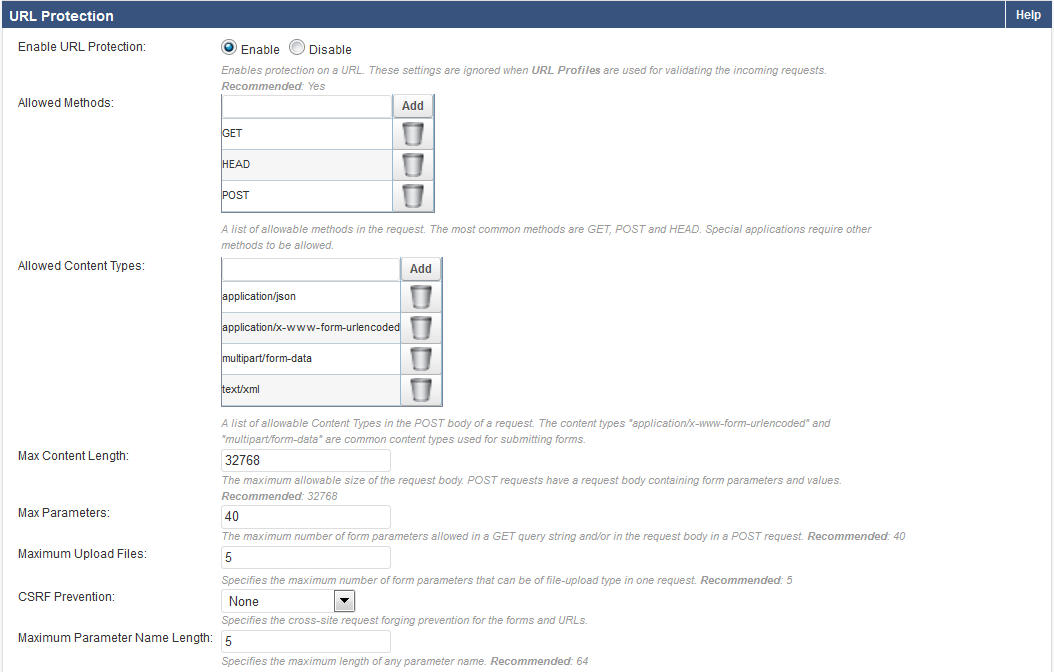
The Max Parameter Name Length, set on SECURITY POLICIES > URL Protection, is 5.
When three unique clients (based on the value set in Trigger Count) send requests with parameter name length 10, the violation is logged under BASIC > Web Firewall Logs.
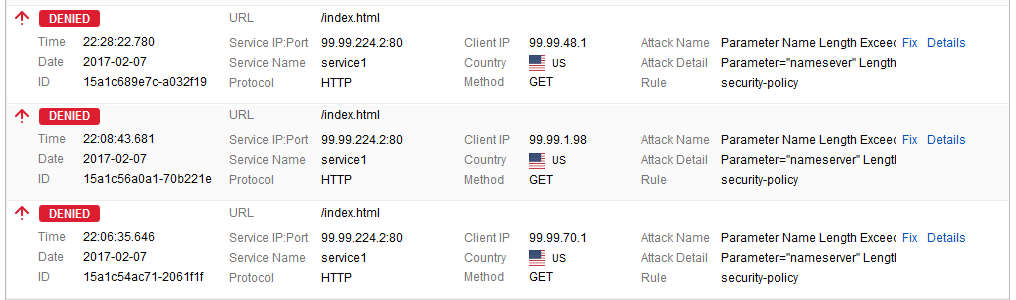
The recommendations are displayed after 600 seconds (10 minutes) on the WEBSITES > Exception Profiling page.
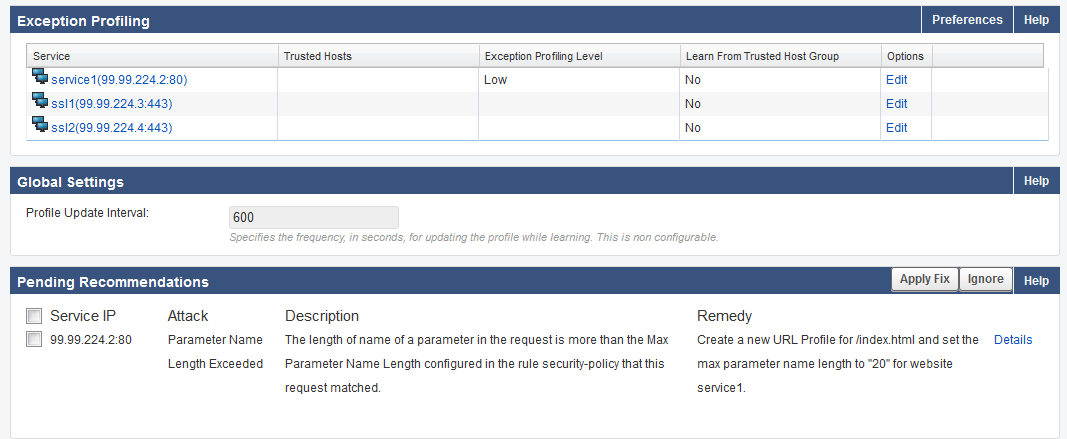
Click Details to see the log information. Select the check box(es) and click Apply Fix to apply the recommended fix.
Since New Value for Parameter Name length exceeded is set to Increase 100% on WEBSITES > Exception Heuristics and the parameter length in the request is 10, a new URL profile is created on the WEBSITES > Website Profiles page with the Max Parameter Name Length set to 20.
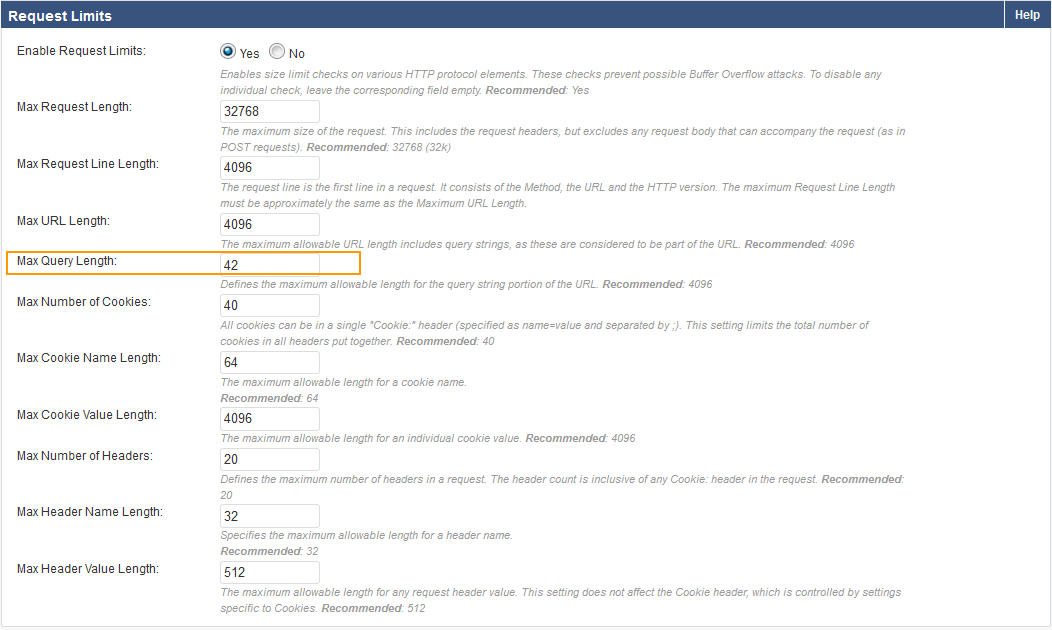
Example 2: Query Length Exceeded.
In this example, Query length exceeded is set to Manual, New Value is set to Increase 100% and Trigger Count is set to 3.
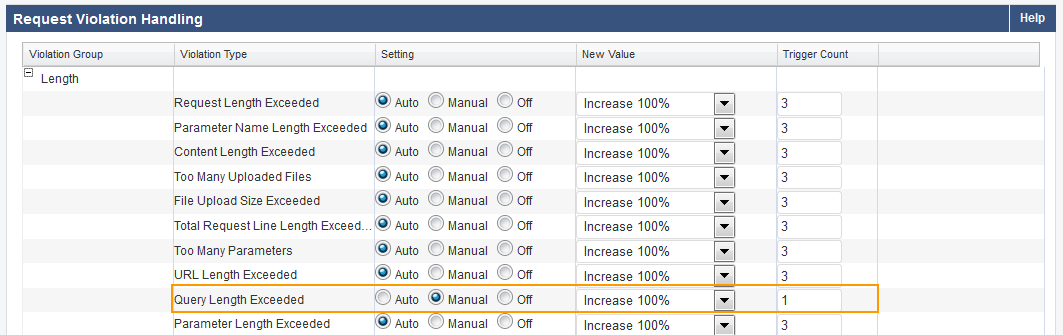
The Max Query Length, specified on the SECURITY POLICIES > Request Limits, is 5.
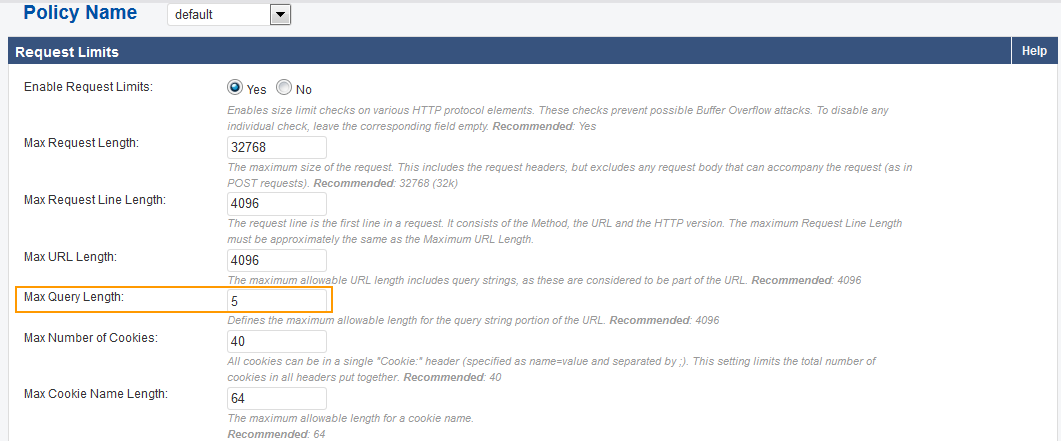
Recommendation generated on WEBSITES > Exception Profiling:
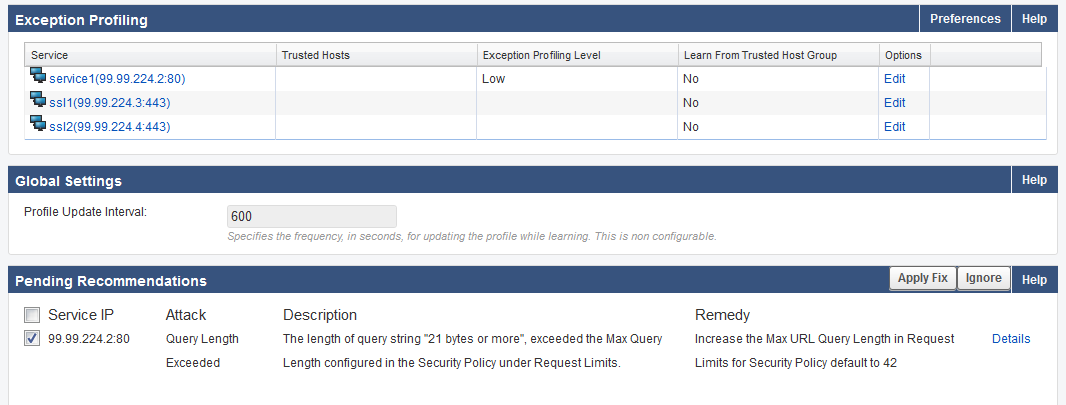
Clicking Apply Fix increases the Max Query length to 24 on SECURITY POLICIES > Request Limits.