The following flowchart explains how the Barracuda CloudFormation Template works:
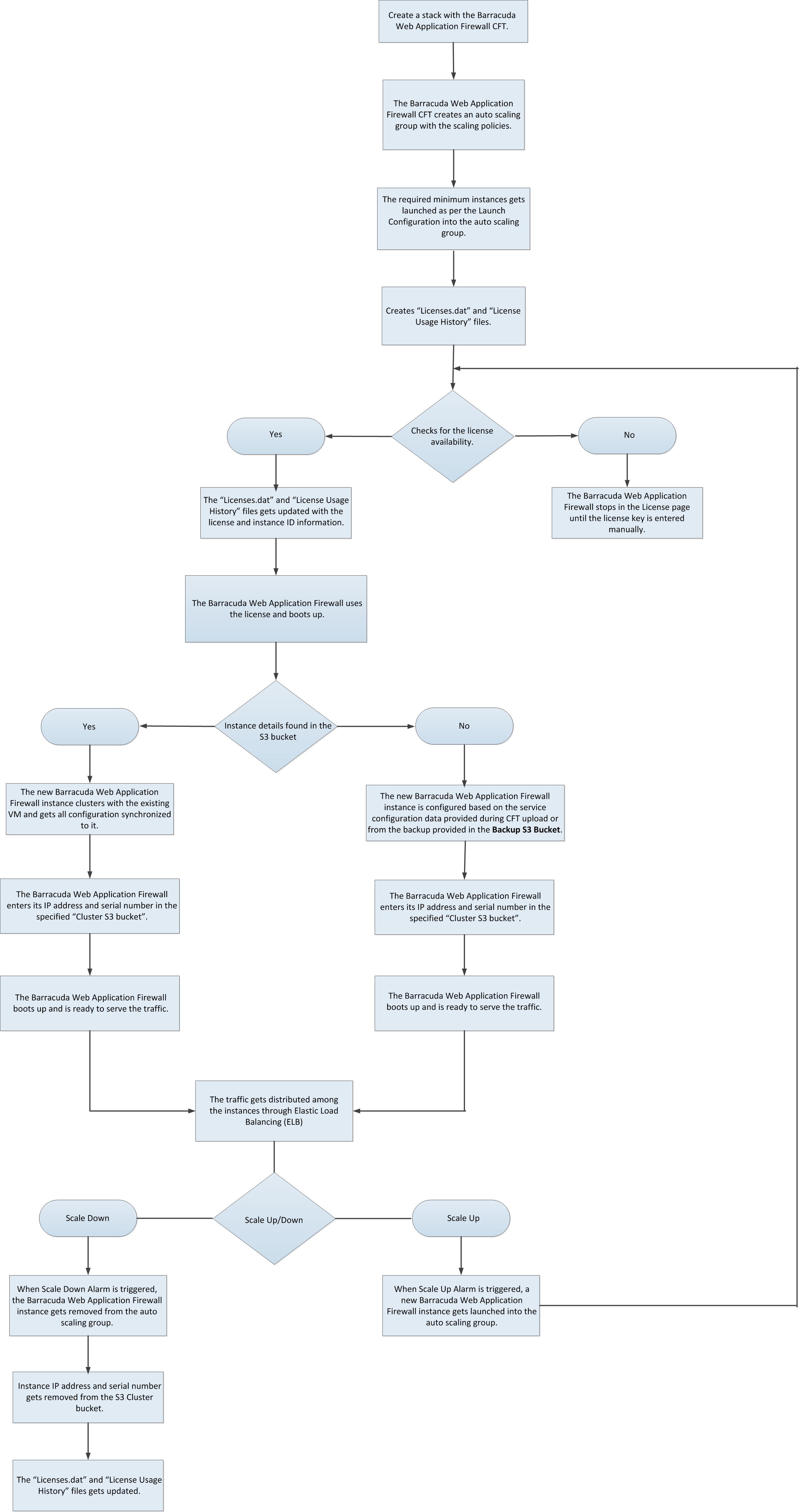
With regard to the flowchart, the following steps describe how a Barracuda CloudFormation Template works:
- A CloudFormation Template (CFT) is uploaded and a stack is created on Amazon Web Services. With this:
- The Barracuda Web Application Firewall instance(s) will be deployed and provisioned in the Virtual Private Cloud (VPC) specified while creating the stack.
- Creates “License.dat” and “License Usage History” files.
- After the Barracuda Web Application Firewall VM(s) is/are up and ready to serve the traffic:
- It checks for license availability,
- If the license file is available with unused licenses:
- The “License.dat” and “License Usage History” files gets updated with the license and instance ID information.
- The instance uses an unused license key and boots up.
- It checks the Cluster S3 bucket for any other existing VM(s) in this Auto Scaling group.
- If there is no VM data available in the Cluster S3 bucket, the VM is configured based on the service configuration data provided during CFT upload or from the backup file provided as the input in the CFT.
- If there is an existing Barracuda Web Application Firewall instance information available in the Cluster S3 bucket, the new instance clusters with the existing instance and gets all configuration synchronized to it.
- Adds its information to the Cluster S3 bucket specified while creating the stack. The Cluster S3 bucket stores instance data, serial number and primary IP address (i.e., WAN IP address) of the deployed Barracuda Web Application Firewall instance(s).
- The Barracuda Web Application Firewall is now ready to serve the traffic to the configured services.
- If the instance encounters high traffic flow and triggers any of the created alarms, such as high bandwidth utilization, CPU usage, etc., then:
- A new Barracuda Web Application Firewall instance gets initiated automatically.
- Looks at the Cluster S3 bucket created in step 1 (a) and clusters with it.
- Adds its information to the Cluster S3 bucket, and is ready to serve the traffic.
- Traffic gets distributed among the instances through ELB.
- If the license file is available with unused licenses:
- If the license file or unused license keys are not available, the Barracuda Web Application Firewall for AWS stops in the license page until the key is manually entered.
- If the traffic flow returns to normal, the Scale Down alarm is triggered.
- The added Barracuda Web Application Firewall instance gets removed from the auto scaling group.
- Instance IP address and serial number details gets removed from the Cluster S3 bucket.
- The License.dat and License Usage History files gets updated.
Next Step
Continue with the Importing the Barracuda Web Application Firewall BYOL CFT and Deploying the Instance article to import the CFT and deploy the instance.
