Overview
Software Management life-cycle has drastically changed with the advent of Public Cloud Platforms and DevOps Environment. With these latest technologies, system administrators will now need an easy and elegant way to dynamically configure the system to keep up with the ever changing network and security requirements.
To make the DevOps task easier for the system and network administrators, the Barracuda Web Application Firewall delivers a simplistic solution by providing a file-based configuration management approach.
The following are the key highlights of the file-based configuration management approach:
- Simplify the overall configuration management on the Barracuda Web Application firewall.
- Simplistic yet comprehensive and robust solution which covers all the configuration objects on the Barracuda Web Application Firewall.
- Organizes and maintains the Infrastructure as a code that can then be used for versioning, reviewing, and easy auditing.
- Internally, it directly maps to the comprehensive Barracuda Web Application Firewall Version 3 REST API’s
- In Cloud Platforms, this can be seamlessly used for system bootstrapping.
This approach uses the JSON based text configuration file to define all the configuration that are installed on the Barracuda Web Application Firewall.
The JSON configuration file is manually created by the administrator and is used to specify all the required configuration objects and the desired operations. The JSON file is then validated and installed on the Barracuda Web Application Firewall using the Graphical User Interface. In Cloud Platforms, the JSON file is also used for bootstrapping the system. The contents of the file are easily modified and the configuration is replicated to suit your requirements.
Using the JSON-Based Configuration File
The JSON-based configuration file can be used in the following ways:
- Importing the Configuration on an Operational Barracuda WAF Instance: On a WAF that is already operational, JSON configuration files can be used to make an update to the WAF configuration. This is very similar to making a configuration change using the web interface (GUI) or through the WAF’s REST API. The JSON file import can be validated before applying the change.
- Used for Bootstrapping a WAF Instance: In this case, the JSON configuration file can be used for loading the configuration into the Barracuda WAF instance when it is first provisioned. This is useful to implement a Continuous Integration (CI)/Continuous Delivery (CD) pipeline around WAF. This type of provisioning is very common in public cloud deployments where the instance is launched along with bootstrapping information.
To use the JSON configuration file in an Auto Scaling deployment of the Barracuda WAF on AWS, see Auto Scaling of Barracuda Web Application Firewall using CloudFormation Template on Amazon Web Services.
To use the JSON configuration file in VMSS deployments of the Barracuda WAF on Microsoft Azure, see Auto Scaling the Barracuda Web Application Firewall Instances in Microsoft Azure.
Configuration File Anatomy
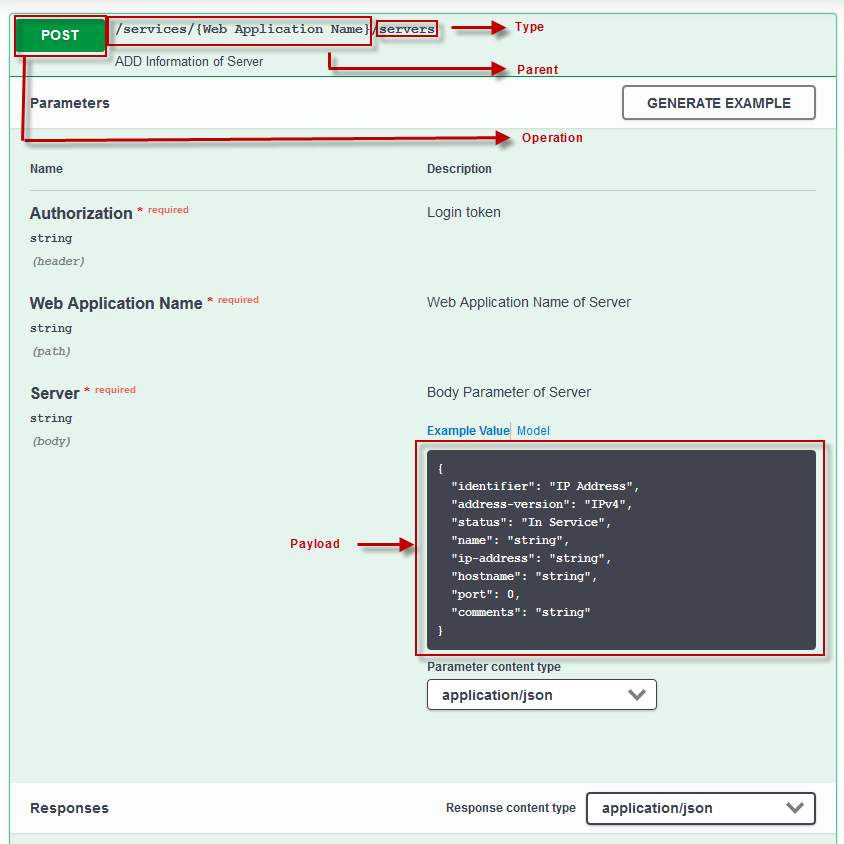
The Barracuda Web Application Firewall configuration file is a JSON file with one major section “Config”. It includes parameters and attributes for the overall configuration. An example of the JSON configuration file structure is shown below.
{
"config": [
{
"type": “…”,
"operation": “…”,
"payload": {
"param1": “…”,
"param2": “…”,
}
},
{
"type": “…”,
"operation": “…”,
"payload": {
"param1": “…”,
"param2": “…”,
}
},
.
.
.
]
}
Attribute | Description |
| Example | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
Operation | Defines the actions to be performed on the configuration objects. | Create, Edit and Delete are the operations supported in the Barracuda Web Application Firewall configuration management. See the table below to understand the mapping of each operation to the respective API type.
| performs an operation of creating a certificate
| ||||||||
| Type | Specifies the type of the object defined by the configuration file | The type “certificates” can be created | |||||||||
Parent (OPTIONAL) | Identifies the configuration hierarchy | A parameter profile is configured for URL policy “url1” under services “Prod_App” | |||||||||
Payload | Parameters that define the configuration object. Refer to example value of an object in REST API guide to know about the parameters. | Refer to example value of an object in REST API guide to know about the parameters. | | ||||||||
 | |||||||||||
Special Macros
SYSTEM_IP Macro - When SYSTEM_IP is specified for the ip-address parameter, the Barracuda Web Application Firewall will automatically use the system ip address while creating a service.
The following example payload shows the usage of the SYSTEM_IP macro while creating a service.{ "type": "services", "operation" : "CREATE", "payload": { "name":"Prod_App", "type":"https", "ip-address":"bwaf::SYSTEM_IP", "port":"443", "certificate":"testcert", "group":"default", "vsite":"default", "status":"On", "address-version":"IPv4", "comments":"This is the production service for the lab" } },
Getting started with the configuration file-based approach
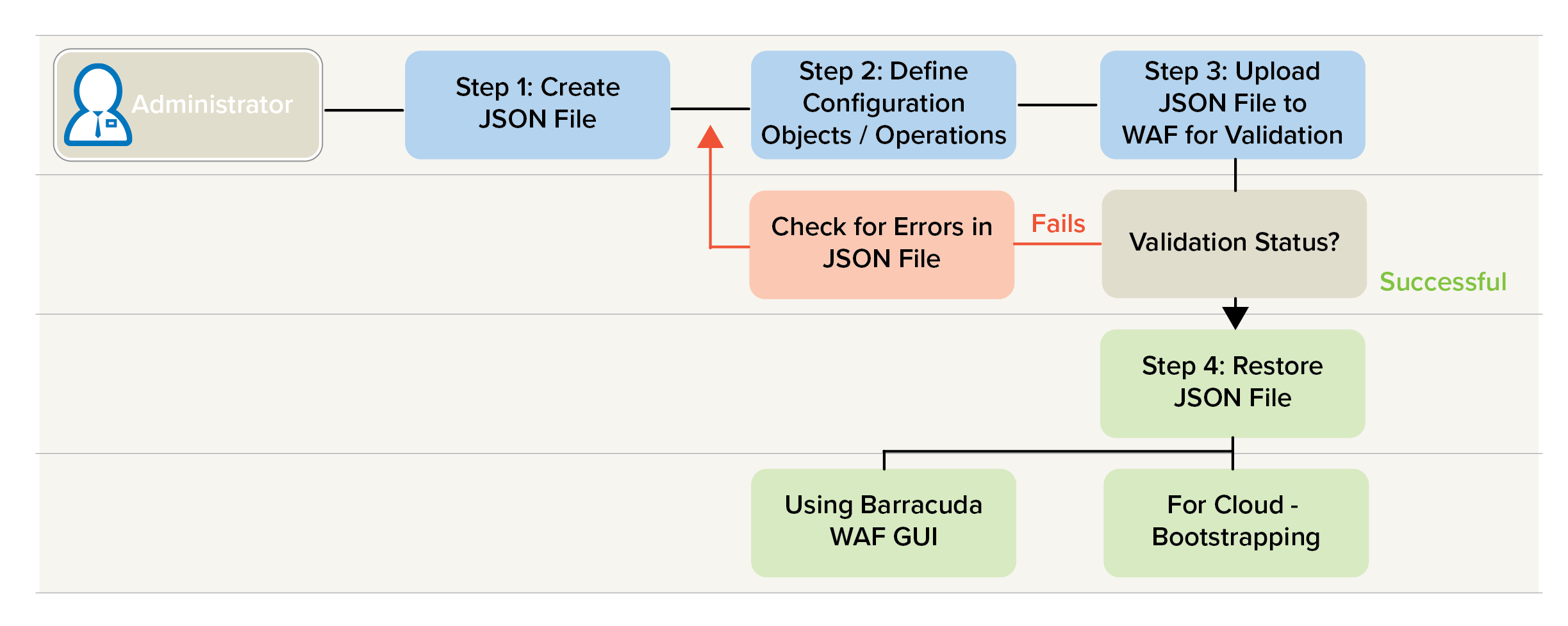
The JSON Configuration file is manually created by specifying the configuration objects and operations. This file is then used while configuring Barracuda Web Application Firewall. The flowchart visualizes the steps involved in manually creating a configuration file:
- Creating a file - <filename>.json
- Creating Objects for the JSON Configuration File
- Validating the Configuration File
- Bootstrapping using the Config.json file
Creating a file - <filename>.json
The JSON file is created or edited using any text editor. You can specify any name to your configuration file, but Barracuda Networks recommends you to save the file with a “.json” file extension only.
Creating Objects for the JSON Configuration File
The configuration objects of the JSON file is created by referring to the Barracuda Web Application Firewall REST API documentation. Perform the following steps to include the configuration objects and operations.
- Click the Barracuda Web Application Firewall REST API documentation link to navigate to the list of APIs.
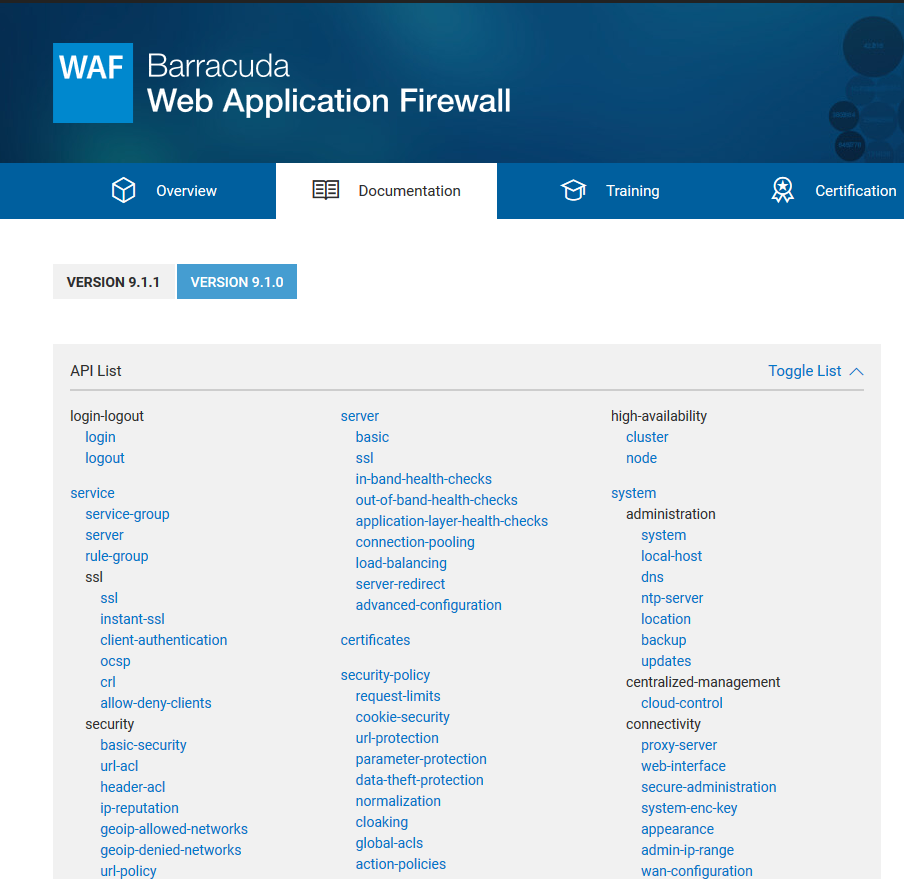
- Select the object you intend to include in the JSON file. For example - Services, Server, and so on.
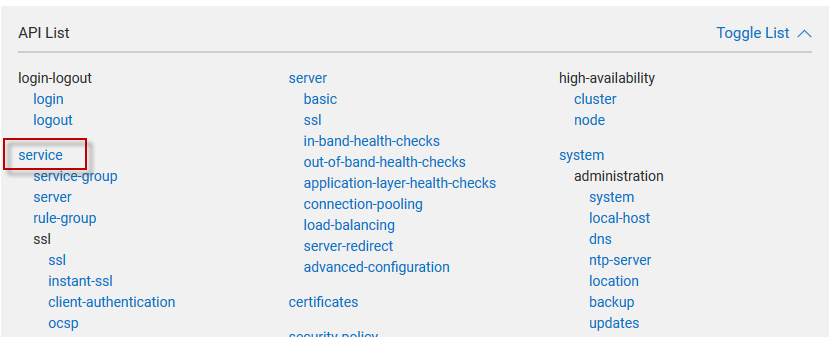
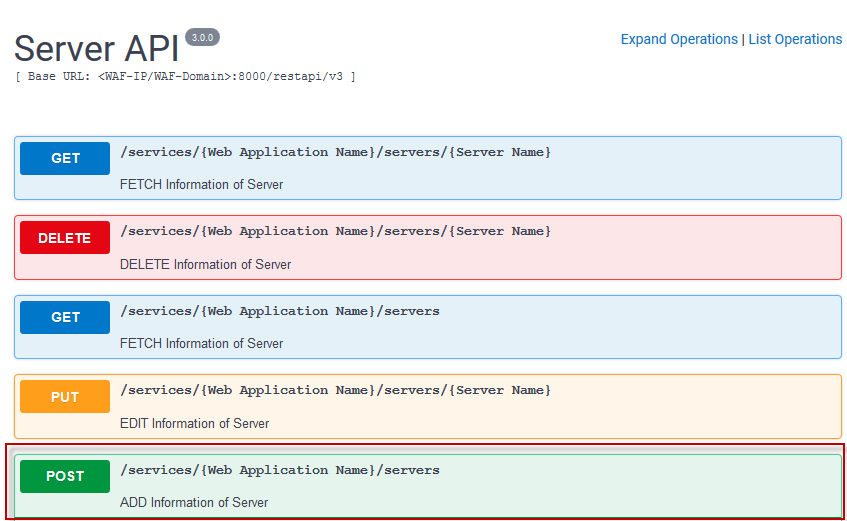
- Select the operation you intend to perform. For Example - POST. Refer to the Anatomy section to know more about API request types that you must select to perform the operation.
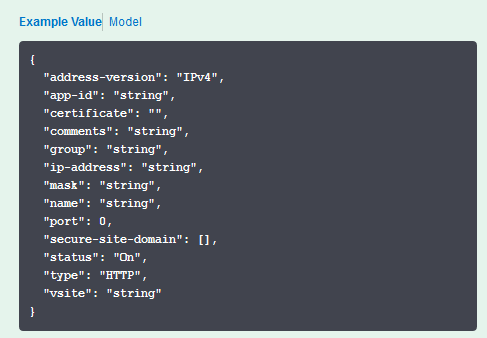
- Copy the JSON content and paste it in the configuration file.
Validating the Configuration File
After creating the configuration JSON file, you should validate the file by uploading this in the Barracuda Web Application Firewall User interface. The Restore WAF Configuration File section allows you to upload the JSON file for validation and for restoring the configurations.
Perform the following steps to validate and restore the configurations of the JSON file:
- Log in to the Barracuda Web Application Firewall.
- Navigate to ADVANCED > Backups > Restore WAF Configuration File.
- Click Browse and select the JSON file that you created.
- From Action Type, specify the option that you want to perform on the JSON configuration file.
- Validate- creates a sandbox environment on the Barracuda Web Application Firewall to test and validate the configurations specified in the JSON file. The validation process might take few minutes for completion depending on the size of the configuration. However, the progress of completion is indicated on the User Interface. A Success/Failure message is displayed at the end of the validation process.
- Apply Configuration- applies the configurations specified in the JSON file. The process might take few minutes for completion depending on the size of the configuration. However, the progress of completion is indicated on the User Interface. A Success/Failure message is displayed at the end of the installation process. In case if there is an error, the configuration on the system is automatically reverted to the state prior to the config restore. Also, you can view the details of the error by clicking the link displayed on the User Interface.
- Click Upload Now to upload the JSON file.
Bootstrapping using the Config.json file
Amazon Web Services
Upload the config json file in the bootstrapping S3 bucket.
- Launch the cloudformation stack and specify the JSON filename. Note that with this parameter, you can either specify the backup filename or the config.json file.
At the time of bootstrapping the instance picks up the configurations from the JSON, frames REST v3 requests internally and executes them on the WAF.
Microsoft Azure
- Upload the config json file in the bootstrapping blob.
- Launch the cloudformation stack and specify the JSON filename. Note that with this parameter, you can either specify the backup filename or the config.json file.
At the time of bootstrapping the instance picks up the configurations from the JSON, frames REST v3 requests internally and executes them on the WAF.
Example - JSON file
The Barracuda Web Application Firewall in particular uses the config.json file to configure applications. One example of the JSON file that covers the following operations is summarized below.
- Create certificate with name "testcert"
- Create HTTPS service with name "Prod_App" by binding certificate "testcert"
- EDIT service "ProdApp"
- Create Server "ALB_backend"
- Create Server "ALB_backend2"
- Delete Server "ALB_backend2"
- Create URL profile "url1" for service "ProdApp"
- Create Param Profile for URL profile "url1"
{
"config":[
{
"type": "certificates",
"operation" : "CREATE",
"payload":
{
"name":"testcert",
"allow_private_key_export":"yes",
"city":"san_franscisco",
"common_name":"prod.barracuda.com",
"country_code":"US",
"curve_type":"secp256r1",
"key_size":"1024",
"key_type":"rsa",
"organization_name":"techkaizen.net",
"organization_unit":"devops",
"state":"california"
}
},
{
"type": "certificates",
"operation" : "CREATE",
"payload" :
{
"name":"testcert2",
"allow_private_key_export":"yes",
"city":"san_franscisco",
"common_name":"labs.barracuda.com",
"country_code":"US",
"curve_type":"secp256r1",
"key_size":"1024",
"key_type":"rsa",
"organization_name":"internal.net",
"organization_unit":"dev",
"state":"california"
}
},
{
"type": "services",
"operation" : "CREATE",
"payload":
{
"name":"Prod_App",
"type":"https",
"ip-address":"bwaf::SYSTEM_IP",
"port":"443",
"certificate":"testcert",
"group":"default",
"vsite":"default",
"status":"On",
"address-version":"IPv4",
"comments":"This
is the production service for the lab"
}
},
{
"type": "basic-security",
"parent": "/services/Prod_App",
"operation" : "EDIT",
"payload" :
{
"rate-control-status": "Off",
"mode": "Active",
"ignore-case": "Yes",
"web-firewall-log-level": "5-Notice",
"trusted-hosts-action": "Default",
"rate-control-pool": "NONE",
"web-firewall-policy": "default"
}
},
{
"type": "servers",
"parent" : "/services/Prod_App",
"operation" : "CREATE",
"payload" :
{
"name":"ALB_backend",
"identifier":"IP
Address",
"address-version":"IPv4",
"status":"In
Service",
"ip-address":"10.2.4.18",
"port":"80",
"comments":"Creating
the server"
}
},
{
"type": "servers",
"parent": "/services/Prod_App",
"operation" : "CREATE",
"payload" :
{
"name":"ALB_backend2",
"identifier":"IP
Address",
"address-version":"IPv4",
"status":"In
Service",
"ip-address":"10.2.4.18",
"port":"80",
"comments":"Creating
the server"
}
},
{
"type": "servers",
"parent" : "/services/Prod_App",
"name" : "ALB_backend2",
"operation" : "DELETE"
},
{
"type": "url-profiles",
"parent": "/services/Prod_App",
"operation" : "CREATE",
"payload" :
{
"name":"url1",
"status": "On",
"extended-match": "*",
"exception-patterns":
[],
"url": "/public/index.html",
"allow-query-string": "Yes",
"maximum-upload-files": "5",
"comment":
"",
"referrers-for-the-url-profile":
["goodf"],
"maximum-parameter-name-length": "64",
"csrf-prevention": "None",
"mode": "Passive",
"max-content-length": "32768",
"extended-match-sequence": "1",
"blocked-attack-types":
[],
"display-name":
"",
"custom-blocked-attack-types":
[],
"hidden-parameter-protection": "Forms"
}
},
{
"type": "parameter-profiles",
"parent": "/services/Prod_App/url-profiles/url1",
"operation": "CREATE",
"payload" :
{
"name":"param_1",
"status": "On",
"allowed-file-upload-type": "Extensions",
"max-value-length": "1000",
"exception-patterns":
[],
"parameter": "test_param",
"validate-parameter-name": "No",
"required": "No",
"parameter-class": "String",
"comments": "test
param profile",
"base64-decode-parameter-value": "No",
"ignore": "No",
"file-upload-mime-types":
[],
"maximum-instances": "1",
"file-upload-extensions":
["*"],
"custom-parameter-class":
"",
"type": "Input",
"values":
["param1"],
"allowed-metachars":
""
}
}
]
}Example - Creating Certificates
You can create/upload certificates to Barracuda Web Application Firewall using the JSON file. For uploading the certificates, you should provide the content of the certificates in the “base64”format.
The following example shows how to upload a trusted server certificate with filename "server_001.cert" to Barracuda Web Application Firewall.
Verify the content of the certificate file.
@root-S:~/certs$ cat server_001.cert -----BEGIN CERTIFICATE----- MIIDBTCCAe2gAwIBAgIJAOM++mrve/8CMA0GCSqGSIb3DQEBCwUAMBkxFzAVBgNV ... MyA3naQCWaPSef65qaCeB/XOAZ0BRviqglnUEreHfmdtUZakmgrdALE9bKGy3nja J1aZxPjc7l8z -----END CERTIFICATE-----Encode the content of the certificate file to "base64" format. You can use the following command in the standard LINUX console:
@root-S:~/certs$ cat server_001.cert | base64 | awk 'BEGIN{ORS="";} {print}' LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUVuVENDQTRVQ0NRQzN1SkRCWXBNejJUQU5CZ2txa...Copy the output of the previous command and paste it in the "content" parameter under payload. For example,
{ "type": "certificates", "operation" : "CREATE", "payload": { "name":"trusted_cert", "category": "trusted_server", "content" : "LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0t..." } }
You can follow the same steps described above for uploading certificates or trusted certificates.
- Create certificates
- Upload certificate
- Upload trusted certificate.
- Upload trusted server certificates.
{
"config": [{
"type": "certificates",
"operation": "CREATE",
"payload": {
"name": "create_certificate",
"allow_private_key_export": "Yes",
"city": "Bengalore",
"common_name": "test45.com",
"country_code": "IN",
"key_size": "2048",
"key_type": "rsa",
"organization_name": "Barracuda.com",
"organization_unit": "operations",
"state": "Karnataka"
}
},
{
"type": "certificates",
"operation": "CREATE",
"payload": {
"name": "trusted_certificate",
"category": "trusted_server",
"content": "LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSURCVENDQWUyZ0F3SUJBZ0lKQU9NKyttcnZl....",
}
},
{
"type": "certificates",
"operation": "CREATE",
"payload": {
"name": "signed-certificate-1",
"category": "signed",
"signed_certificate": "LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUVrakNDQW5vQ0FXVX...",
"key": "LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlFcEFJQkFBS0NBUUVBclVFYlB0OVZ...",
"intermediary_certificate": "LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUVuVENDQTRVQ0NRQz...",
"type": "pem",
"key_type": "rsa",
"allow_private_key_export": "Yes",
"assign_associated_key": "no",
"password": "abcd"
}
},
{
"type": "certificates",
"operation": "CREATE",
"payload": {
"name": "signed-certificate-2",
"category": "signed",
"signed_certificate": "LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tDQpNSUl...",
"key": "LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQ0KTUlJRW93SUJBQUtDQVFFQXJt...",
"intermediary_certificate": "LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tDQpNSUlGdkRDQ0E2U2dBd0lCQWdJQ0VBQXdEUVlKS29aSWh2Y05BUUVM...",
"type": "pem",
"key_type": "rsa",
"allow_private_key_export": "Yes",
"assign_associated_key": "no"
}
}
]
}Parameter Level Encryption Support for JSON File-based Configuration
The Barracuda Web Application Firewall REST API provides the encryption API (Crypt-Service API) support for the JSON Configuration file. With this support, all the sensitive parameters that requires to be stored securely is encrypted. Basically all plain text parameters are converted into encrypted text. For example, the parameter “password” is a sensitive data that is required to be stored securely. Since they cannot be stored in plain text format, they are encrypted.
The Crypt-Service API also provides encryption support of single and multiple strings. In a single string encryption, the parameter that needs encryption is passed as a string with a key:value pair. In case of multiple string encryption, multiple strings are passed for encryption.
Providing Parameter level Encryption support for JSON Configuraation File
Follow the steps to provide parameter level encryption support to JSON Configuration file:
Step 1 : Get Login Token
Request :
curl http://<WAF IP>/restapi/v1/login -X POST -H Content-Type:application/json -d'{"username":"<Username>","password":"<Password>"}'
Response :
{"token":"eyJldCI6IjE1MjY5NzI4OTAiLCJwYXNzd29yZCI6IjZjN2ZmNGVmNzBjNDRmNWJlZTFjNmY0ZTQ3\nYzhlMTEwIiwidXNlciI6ImFkbWluIn0=\n"}Step 2 : Get Encrypted Strings
The parameter that needs to be encrypted is passed as a string with a key:value pair. For example, a request for encrypting the parameter string "bind-password": "XXXXXX" would be:
Request :
curl http://<WAF IP>/restapi/v3/crypt-service -X POST -u "<token>" -H Content-Type:application/json -d'{"encrypt": "true" , "value": {"string1":"XXXXXX"}}'
Response :
{"string1":"c:y0u7Js/fMTGKIEcvxc9UPg==","token":"eyJldCI6IjE1MjY5NzI5NzMiLCJwYXNzd29yZCI6IjBiZDExNmFhZDczNTAwNzIzYjQ2YmQ3M2Ew\nZWUyZmI2IiwidXNlciI6ImFkbWluIn0=\n"}Multiple strings can also be passed for encryption. For example, a request for encrypting string1 "bind-password": "XXXXXX" and string2 "group-filter":"cn=secret@123" would be:
Request :
curl http://<WAF IP>/restapi/v3/crypt-service -X POST -u "<token>" -H Content-Type:application/json -d'{"encrypt": "true" , "value": {"string1":"XXXXXX", "string2":"sceret@123"}}'
Response:
{"string1":"c:y0u7Js/fMTGKIEcvxc9UPg==","token":"eyJldCI6IjE1MjY5NzMwMzgiLCJwYXNzd29yZCI6IjkzZjVkNGU0ODc2MzU0MDdkNDJmOWQ1YjQ3\nMDQ5MTczIiwidXNlciI6ImFkbWluIn0=\n","string2":"c:7zfBO3b90AnPh9EhrX1xIw=="}Step 3 : Replace the JSON parameter that you want to encrypt with the encrypted value in the JSON content
The example below shows a single string encryption only.
{
"type": "external-ldap-services",
"operation": "CREATE",
"payload" : {
"name":"TestLDAP",
"ip-address":"10.11.12.13",
"port":"389",
"uid-attribute":"sAMAccountName",
"search-base":"dc=wafqa-1,dc=cudaindia,dc=local",
"bind-dn":"cn=administrator,cn=users,dc=wafqa-1,dc=cudaindia,dc=local",
"bind-password": {
"encrypted":"true",
"value":"c:y0u7Js/fMTGKIEcvxc9UPg=="
},
"default-role":"admin",
"encryption":"None",
"group-filter":"cn=wafgroup",
"group-member-uid-attribute":"member",
"group-membership-format":"UserDn",
"group-name-attribute":"cn"
}
}Step 4 : Upload the JSON Configuration file into WAF User Interface or Amazon S3 bucket for Test/Restore
For instructions on how to upload the JSON configuration file to WAF interface, refer to Bootstrap using the Config.json file