Smart Signatures
The Barracuda Web Application Firewall layered processing engine passes traffic through multiple layers of security before validating signatures. The data is first normalized before matching the signature, mainly to reduce the number of patterns required by the system, and to make it more efficient. The normalization engine takes care of case sensitivity and various encoding types before submitting any data to the actual signature match engine.
The Barracuda Web Application Firewall uses Smart Signatures developed internally beyond the processing engine. Signatures are batched in signature groups to allow significant memory optimization and speed of detection when compared to static signatures per attack. Each signature in a signature group has the ability to detect attacks found in 40 standard signatures. This is in contrast with the typical signature-based security available with other web application firewalls where, each signature is specific to a vulnerability or attack, and matching them takes significant time.
When new vulnerabilities are identified, Barracuda security analysts validate the vulnerabilities against the existing signature base. Most of the new vulnerabilities are detected by the signature groups. In many cases, the only change required is turning on the stricter attack type (example: SQL Injection versus SQL Injection strict). When an attack is getting through, relevant signatures are created immediately and are made available to the Barracuda Web Application Firewall through attack definition updates. This is performed on an as-needed basis.
The following diagrams show the evaluation flow for Requests and Responses. Smart Signatures are applied at the relevant parts of the evaluation flow depending on the content of the request.
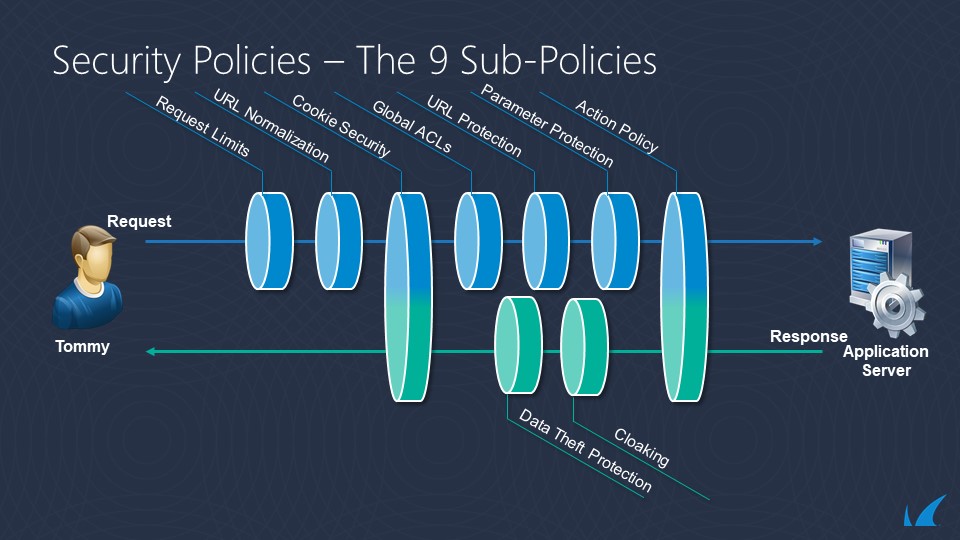
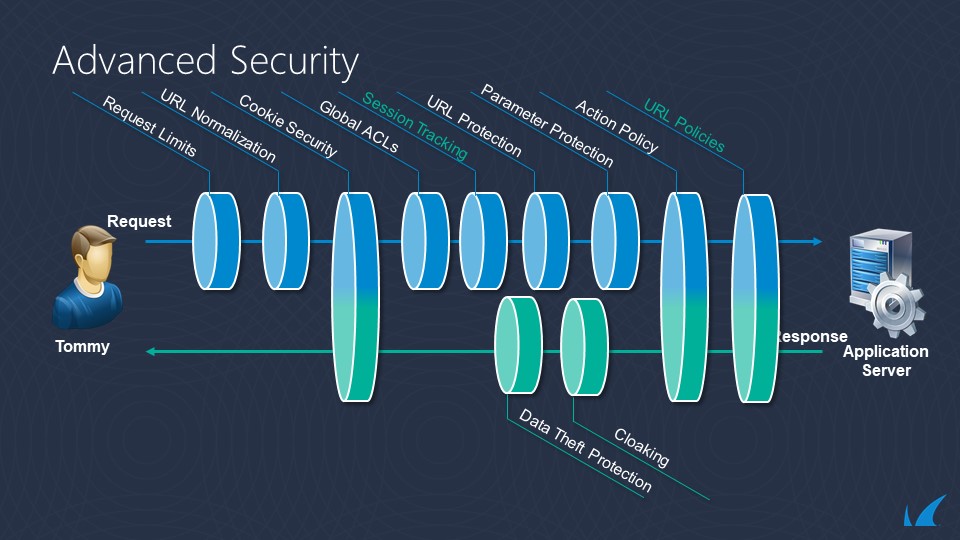
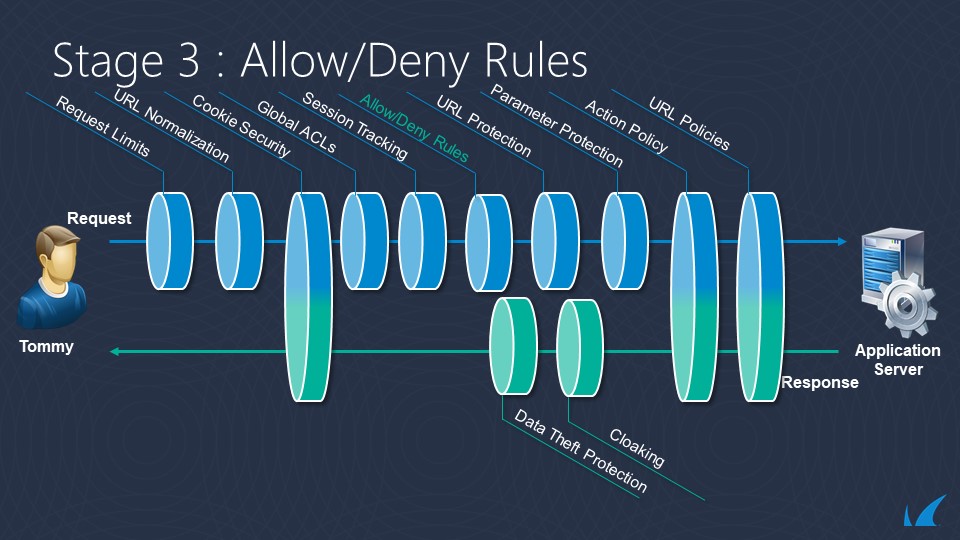
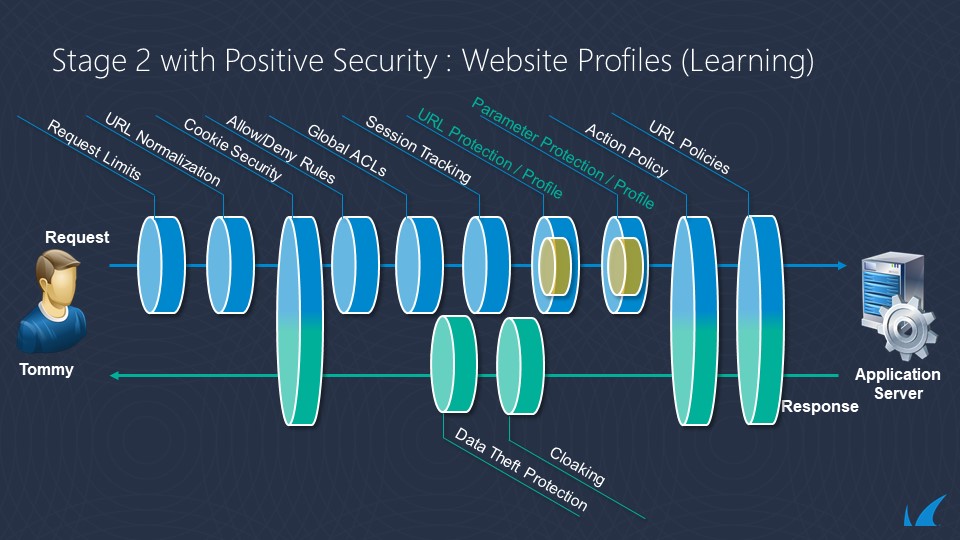
Strict Patterns
The Barracuda Web Application Firewall includes stricter versions of attack pattern groups (with the suffix "-strict") that are designed to aggressively block payloads containing possible malicious content. While these attack pattern groups can successfully stop attack attempts, false positives can be introduced if applied without understanding them. For example, the pattern group "os-command-injection-strict" contains a pattern called "misc-commands-injections" that matches with common Linux commands like "cat" , "echo" and "mount". While these are valid commands, they are also commonly used words in the English language. So, enabling the pattern group "os-command-injection-strict" for a parameter serving a comment field in an application can have undesired effects. It is recommended to enable strict patterns after thorough scrutiny. It's also recommended to enable the strict patterns if penetration testing exercises are done to avoid the noise created due to default test cases in the scanners.
