This article provides an update on the recently discovered JSON-based SQL Injection Vulnerability by Team82.
The Claroty T82 research team released a blog last week demonstrating a newly identified SQL injection in JSON-based SQL and how it bypasses many name-brand WAF vendors.
Exploit
The attack technique involves appending JSON syntax to SQL injection payloads. The attack affects only web applications using JSON.
Barracuda Web Application Firewall Mitigation
The Barracuda Web Application Firewall (WAF) protect against this attack with an update in the existing SQL injection category of the Smart Signatures.
The default SQL injection medium and strict checks do not detect this variant, which employs JSON syntax. The new signature detects all identified variants of the JSON syntax-based attacks.
Barracuda Networks has pushed the new signature through Attack Definition Update version 1.222. The Release Notes have been updated to reflect the changelog.
Action Required
- Set Automatic Updates to ON for the WAF devices to receive the latest Attack Definition version 1.222.
- Set the Operating Mode for the new attack pattern "sql-tautology-conditions-json-bypass-string" to Active in the ADVANCED > View Internal Patterns > Attack Types > sql-injection-medium group.
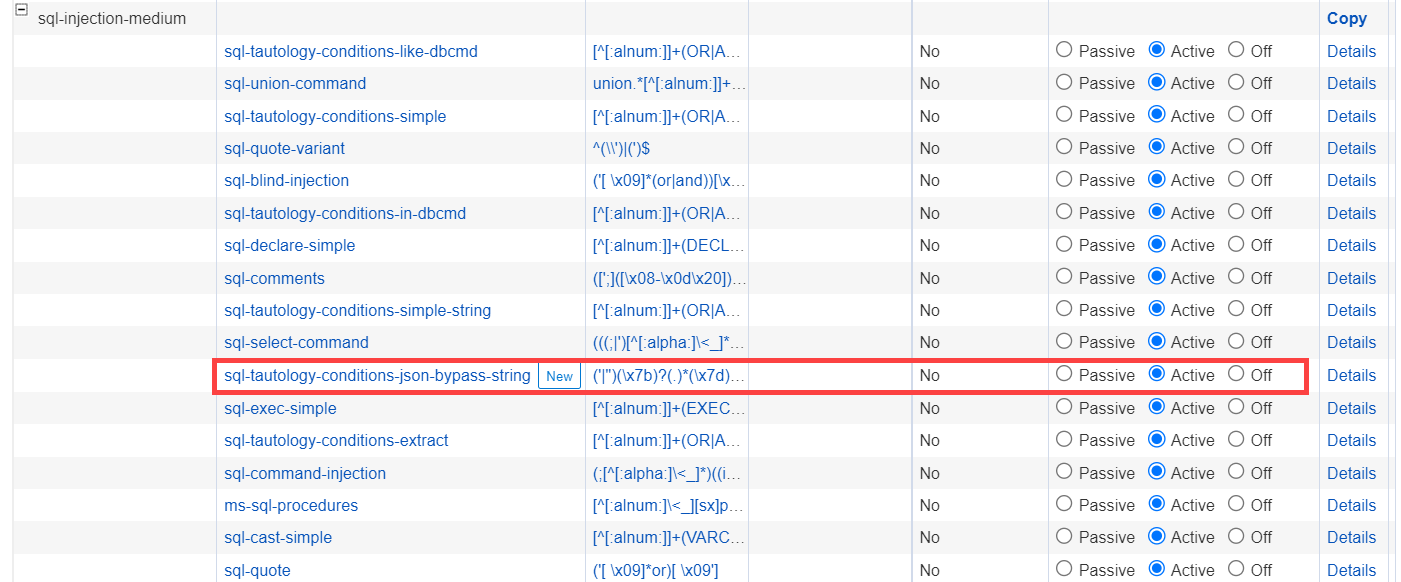
This pattern group category is a default setting for all existing profiles (URL and Parameter protections). It is advised to watch out for false positives from this pattern and to contact Barracuda Networks Technical Support as required.
Related Articles:
- https://claroty.com/team82/research/js-on-security-off-abusing-json-based-sql-to-bypass-waf
- https://securityaffairs.co/wordpress/139445/hacking/web-application-firewalls-waf-bypass.html
- https://www.techtarget.com/searchsecurity/news/252528217/Claroty-unveils-web-application-firewall-bypassing-technique
- https://www.itworldcanada.com/post/claroty-discovers-method-to-bypass-vendors-web-application-firewalls-waf
- https://gbhackers.com/bypass-web-application-firewalls/
