If you only need to apply block policies by domain and/or domain (content) categories, you can enable HTTPS filtering on the 210 or higher as opposed to using SSL Inspection. Unlike SSL Inspection, HTTPS filtering does not decrypt the encrypted portion of URLs. This prevents monitoring or capturing of social media interactions such as posts, chat, comments, shares, etc. See How to Configure SSL Inspection Version 12 and Above for requirements around using SSL inspection.
HTTPS Filtering and Block Pages
When HTTPS access is denied, the user is only presented with a block page if you also set Enable HTTPS Blockpage to Yes on the BLOCK/ACCEPT > Configuration page. Otherwise, the user is not presented with a block page. Note that the user will get an error message in their browser when attempting to visit blocked domains over HTTPS with the following configuration:
SSL Inspection is disabled, and
The SSL certificate has been removed from / not installed in the user's browser, and
The Enable HTTPS Blockpage feature is set to YES on the BLOCK/ACCEPT > Configuration page.
Visiting a blocked HTTPS website with this configuration will result in the following pages presented to the user:
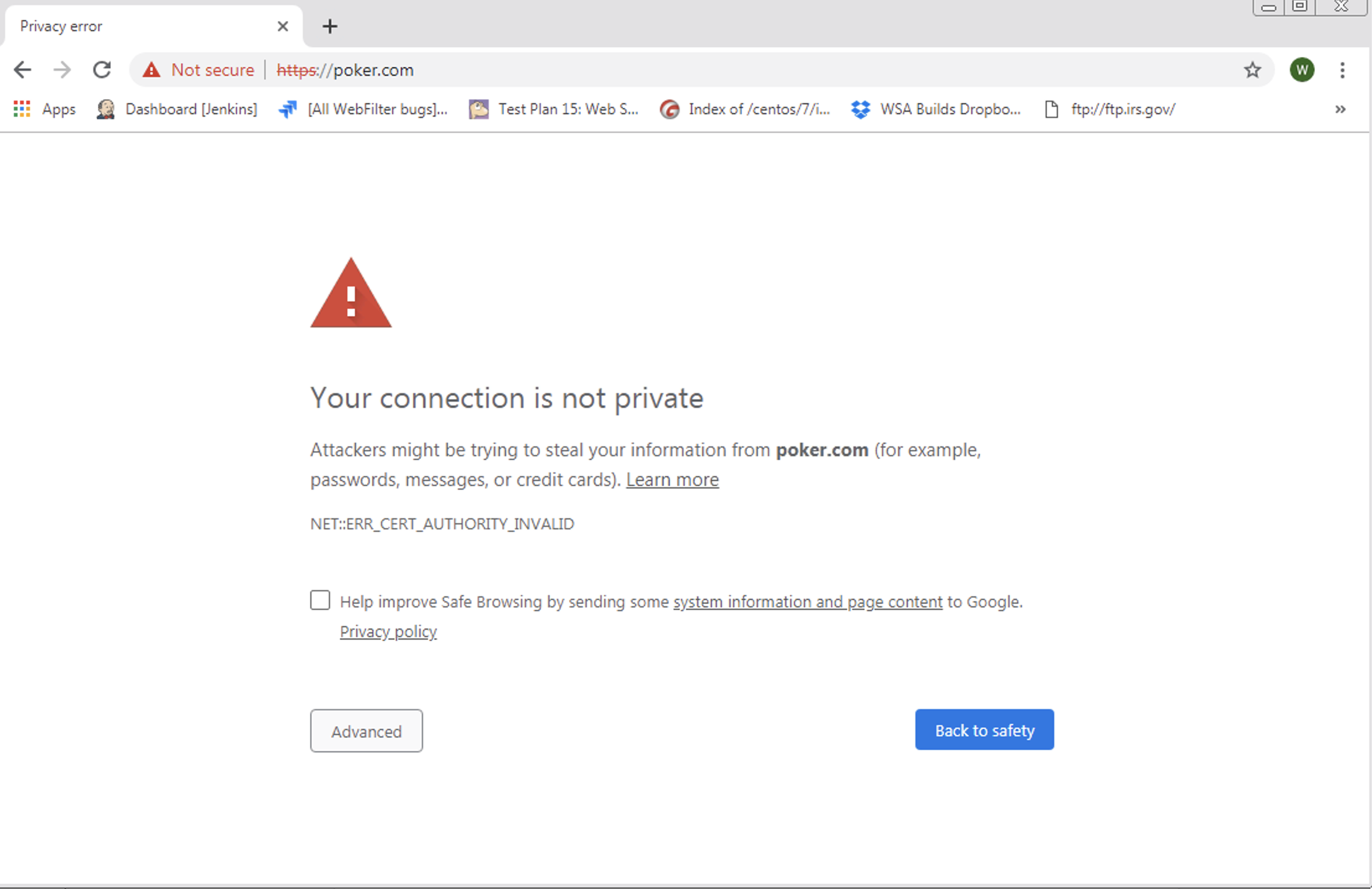
If the user clicks Advanced, the following page is served:
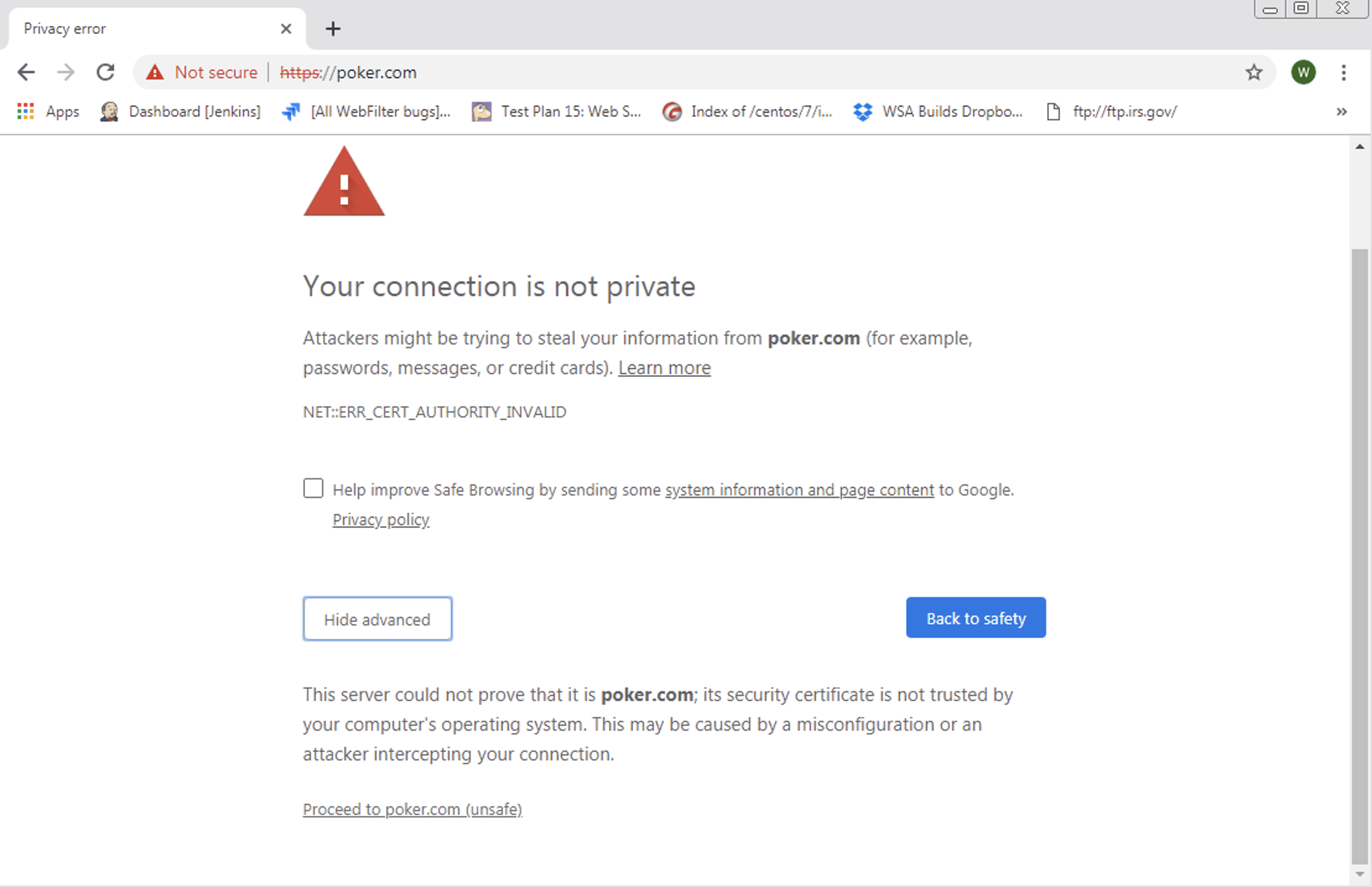
If the user clicked Proceed to <domain name> (unsafe), then the a block page is served:
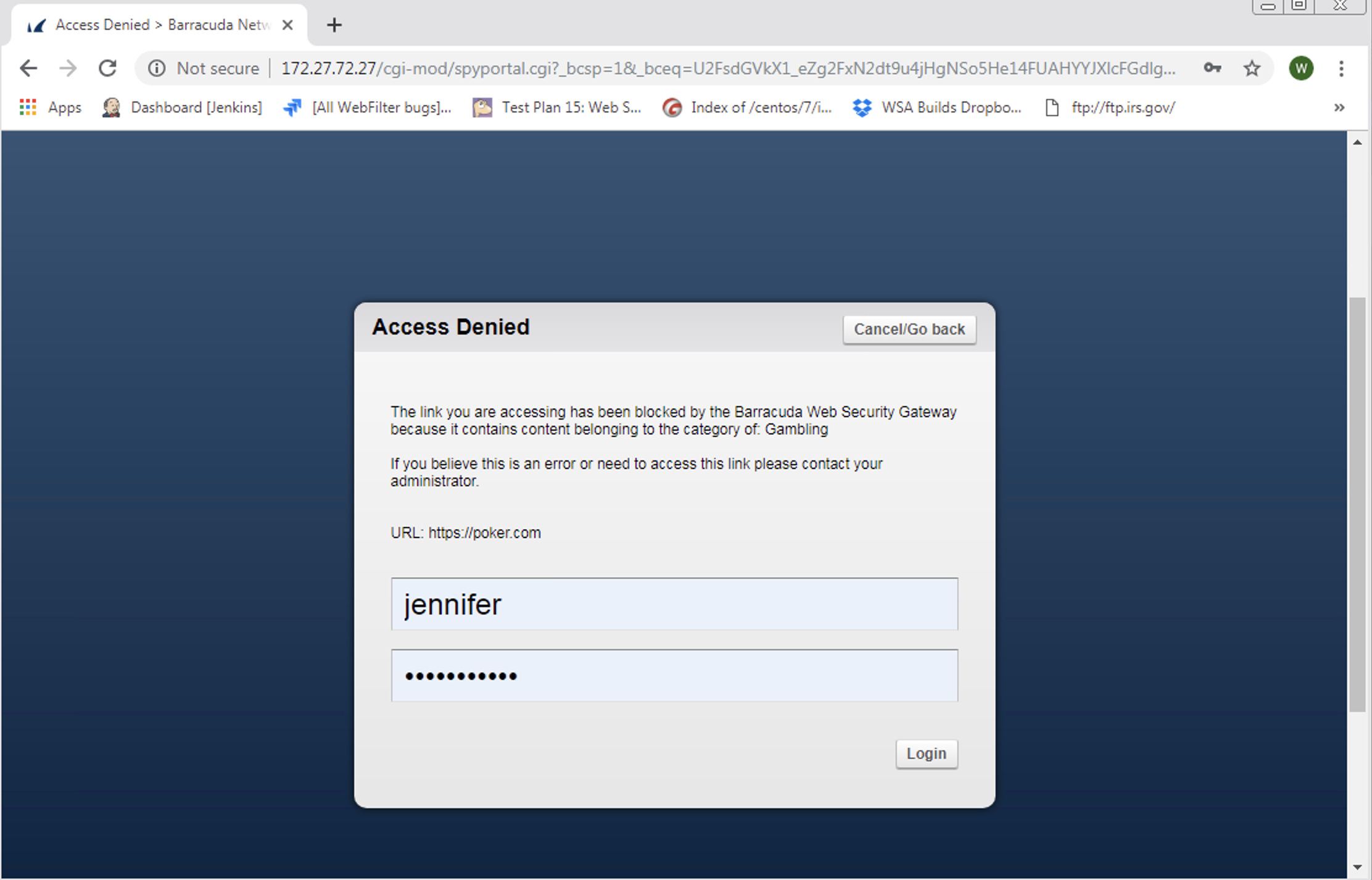
Use cases for this configuration:
Guest user, internet cafe, hotel, etc.
Administrator does not want to install certificates in users' browsers.
Note that, with this configuration, each time users try to visit another domain, they will see the warning again.
See also Block Messages and Using SSL Inspection With the Barracuda Web Security Gateway.
