The documentation below outlines the requirements for the Barracuda XDR Automated Threat Response. All action items listed under the Customer Requirements must be completed. All required data will need to be uploaded to the Customer Security Dashboard in the SOAR Settings > Firewalls section. Please note that these instructions are only for customers using a Cisco Meraki Firewall.
To set up SOAR for Cisco Meraki Firewall, do the following:
To enable API Access and generate an API Key from the Meraki Dashboard
To collect the Organization ID and the Network ID
To create a Network Group Policy Name
To ensure the IP address can make inbound connections to the firewall
To configure the Barracuda XDR Dashboard
To enable API Access and generate an API Key from the Meraki Dashboard
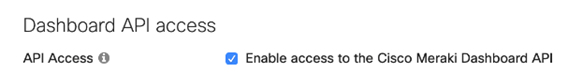
For access to the API, you must first enable the API for your organization.
Log in to the Meraki dashboard: https://dashboard.meraki.com.
Navigate to Organization > Settings.
Ensure the API Access is set to Enable access to the Cisco Meraki Dashboard API.
After enabling the API, navigate to the profile page by clicking on your account email address in the upper right. Then click My profile.
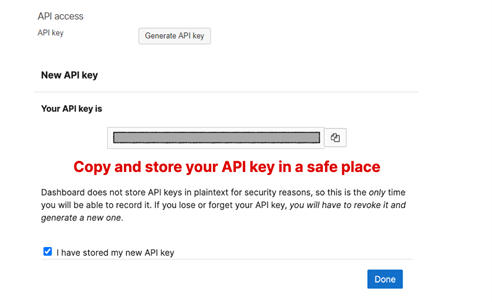
Scroll down to API Access to generate the API key.
Copy, then store the API key in a safe place. Click Done.
To collect the Organization ID and the Network ID
From the Meraki dashboard, from the bottom of the page, copy the Organization ID.

From the Meraki dashboard, copy the ID of the network.
For more information on finding the network ID, see the Meraki documentation.Save these ids for use in the To configure the Barracuda XDR Dashboard procedure.
To create a Network Group Policy Name
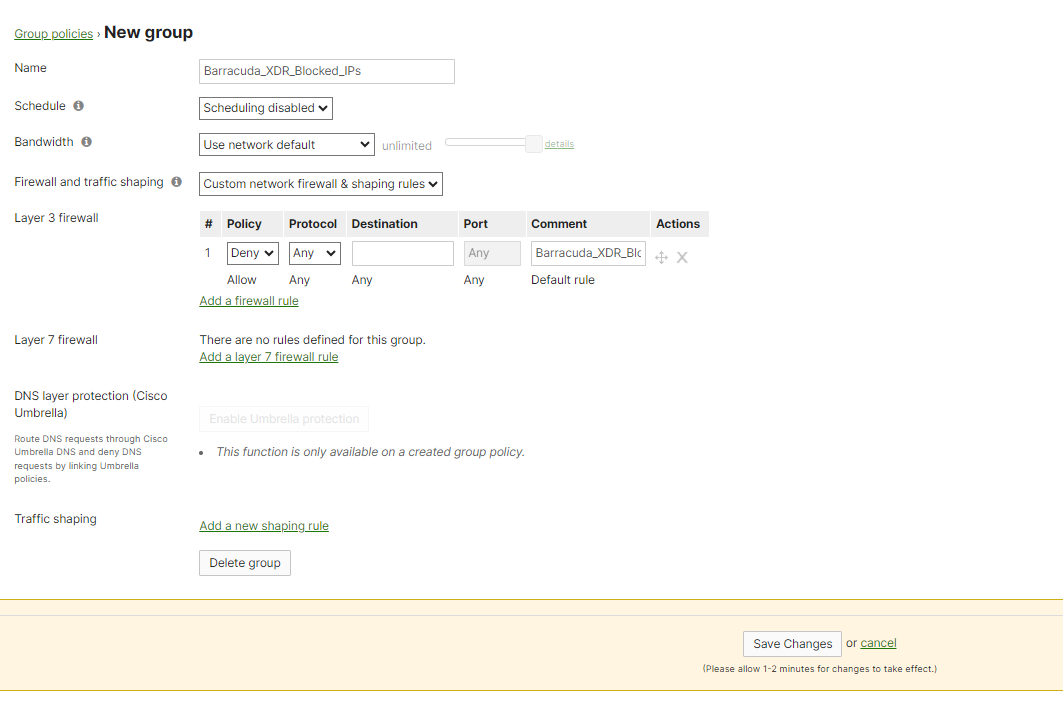
Name the Network Group Policy “Barracuda_XDR_Blocked_IPs”. Barracuda XDR uses the Group Policy to automatically block IPs on the firewall.
NOTE Don’t include a space in the Network Group Policy name or SOAR won’t function properly. We highly recommend using Barracuda_XDR_Blocked_IPs.
In the Meraki dashboard, navigate to Network-wide > Configure > Group policies.
Click Add a group to create a new policy.
Do the following:
In Name, type
Barracuda_XDR_Blocked_IPs.In Schedule, select Scheduling disabled.
In Bandwidth, select Use network default.
In Firewall and traffic shaping, select Custom network & shaping rules.
Click Save Changes.
Copy the Group Policy ID from the URL at the top of the Group Policies page to use in the To configure the Barracuda XDR Dashboard procedure.
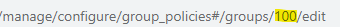
To ensure the IP address can make inbound connections to the firewall
35.155.74.247 and 44.239.173.232 are the static addresses of Barracuda XDR's SOAR platform. Barracuda XDR authenticates from these IPs to remediate threats. Ensure that 35.155.74.247 and 44.239.173.232 can make inbound connections to the firewall.
To configure the Barracuda XDR Dashboard
In Barracuda XDR Dashboard, click SOAR Settings > Firewalls.
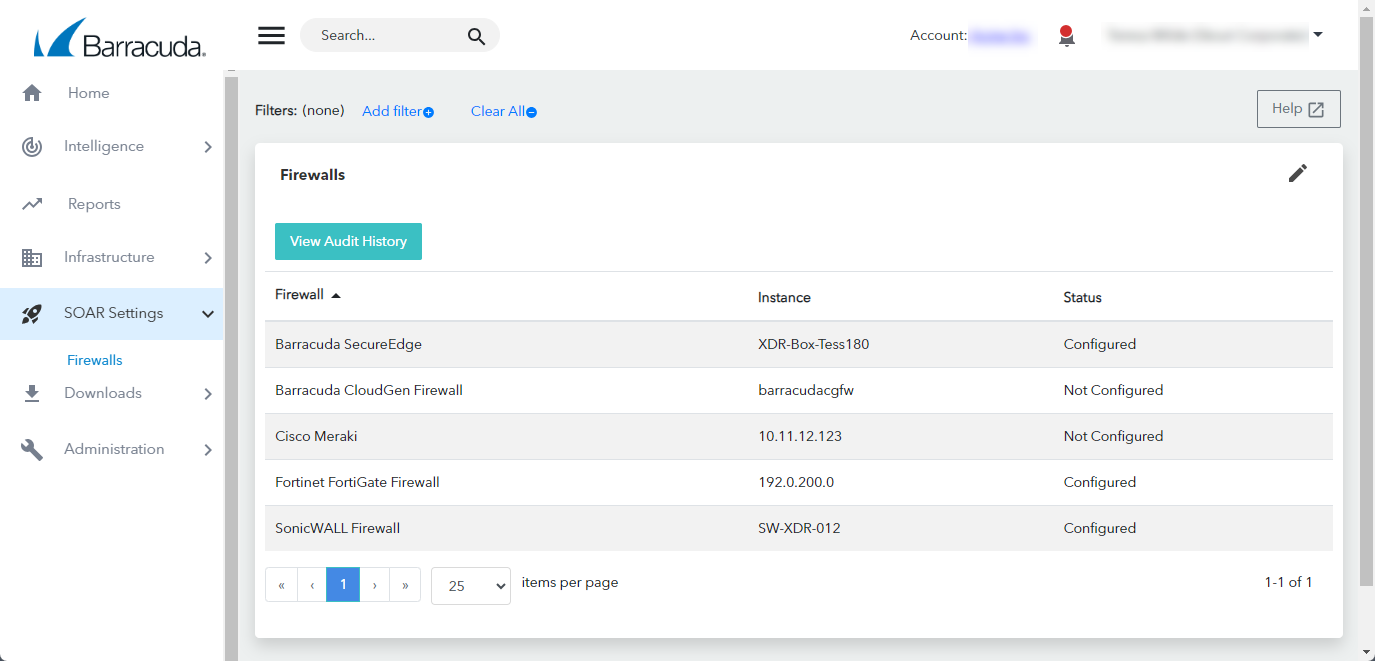
In the Firewalls table, click the Palo Alto Firewall row.
Click Edit Config.
In the Edit Config dialog box, enter the following:
API Access Port
NOTE Unless you have set a custom port for REST API calls, the port is 443.External IP
Network ID
Network Group Name
Network Group ID
Organization ID
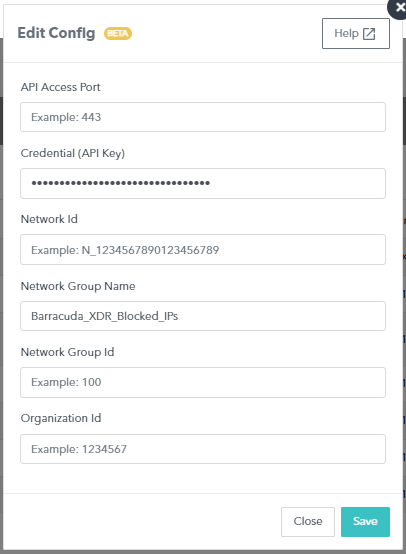
Click Save.
