This use case allows for the ability to detect an administrator role being added to a PIM user. Threat actors might give an account they’ve compromised increased permissions as a means of persistence, just in case they get kicked out of the account they are currently using.


Videolink:
https://campus.barracuda.com/Test Workflow
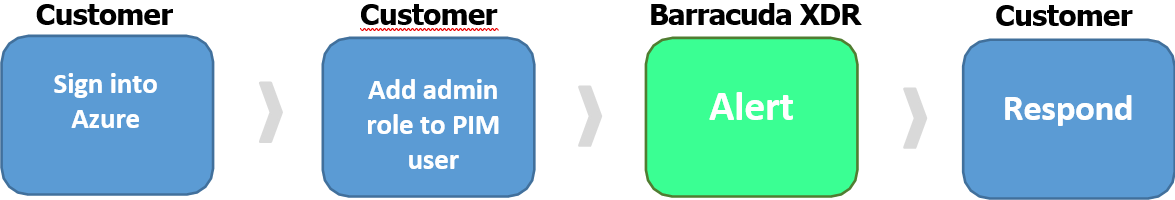
How to Test
Log into Azure using an administrator account.
In the search bar, search for the Users.
Click on the Users service.
Click the name of the user to modify.
On the left side of the screen, under the Manage tab, click Assigned roles.
Click Add Assignments.
Search for the administrator role you want to add, for example, Global Administrator.
Set the conditions for the role assignment.
Click Assign.
