Before you install the XDR Collector, you must configure advanced policy logging to make sure the relevant event logs are sent to XDR.
You have two options to set up Advanced Policy Logging:
Run two scripts on your environment to set up Advanced Policy Logging. This is the recommended option.
Set up each server manually using the steps below. However, this option takes longer and is more error-prone. This method is useful if you can’t run a Powershell script for any reason.
Setting Up Advanced Policy Logging Using Scripts (Recommended)
These scripts set up your entire Windows environment at the same time.
Also, the following scripts limit the log storage capacity to 1 GB before being overwritten. Setting up servers manually doesn’t limit log storage capacity.


Videolink:
https://campus.barracuda.com/To run these scripts, you must be an Administrator of the server or domain.
Download the XDR Mass Configuration script and one of the following:
As Administrator of the server or domain, run these scripts on any Windows device that has access to your entire network.
Setting Up Advanced Policy Logging Manually
These settings ensure that relevant events are logged in the Security log. You don’t need to follow these steps if you use the above scripts to set up policy logging.
Follow these steps to complete the configuration:
Configure Advanced Audit Policy Settings
Enable PowerShell Module and Script Block Logging
Enable the PowerShell Operational Log
Apply and Update the Group Policy
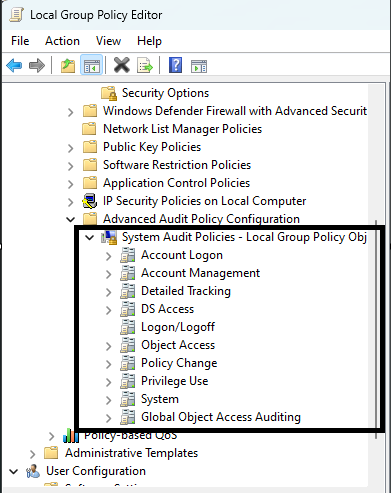
Configuring advanced audit policy settings
On each Windows server you want to collect data from, press the Windows button and the R key at the same time to start the Run tool.
At the prompt, type
gpedit.mscand click OK.
In the Group Policy Management Editor, enable the following options:
Account Logon | |
|---|---|
Audit Credential Validation | Enable for both Success and Failure events. |
Account Management | |
Audit User Account Management | Enable for both Success and Failure events. |
Audit Security Group Management | Enable for both Success and Failure events. |
Audit Computer Account Management | Enable for both Success and Failure events. |
Detailed Tracking | |
Audit Process Creation | Enable for Success events. |
Audit Process Termination | Enable for Success events. |
Logon/Logoff | |
Audit Logon | Enable for both Success and Failure events. |
Audit Logoff | Enable for Success events. |
Audit Special Logon | Enable for Success events. |
Object Access | |
Audit File System | Enable for both Success and Failure events. |
Audit Registry | Enable for both Success and Failure events. |
Audit Other Object Access Events | Enable for both Success and Failure events. |
Policy Change | |
Audit Audit Policy Change: | Enable for both Success and Failure events. |
Audit Authentication Policy Change | Enable for both Success and Failure events. |
Privilege Use | |
Audit Sensitive Privilege Use | Enable for both Success and Failure events. |
System | |
Audit System Events | Enable for both Success and Failure events. |
Audit Security State Change | Enable for Success events. |
Audit Security System Extension | Enable for both Success and Failure events. |
Audit System Integrity | Enable for both Success and Failure events. |
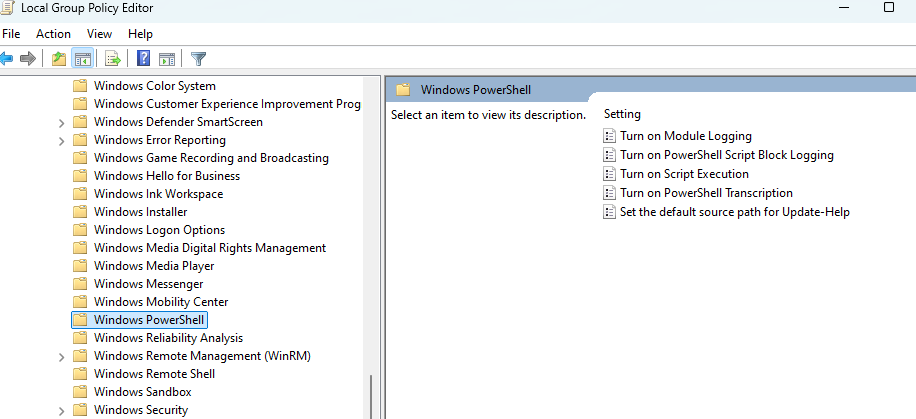
Enable PowerShell Module and Script Block Logging
In the Group Policy Management Editor, navigate to Computer Configuration > Policies > Administrative Templates > Windows Components > Windows PowerShell.
Enable the following settings:
Turn on Module Logging: Enable this setting and specify the modules to log (e.g., Microsoft.PowerShell.* for all core modules).
Turn on PowerShell Script Block Logging: Enable this setting to log all script blocks processed by PowerShell.
Enable PowerShell Operational Log
On a Windows system, press the Windows button and the R key at the same time to start the Run tool
At the prompt, type
eventvwr.mscand click OK.
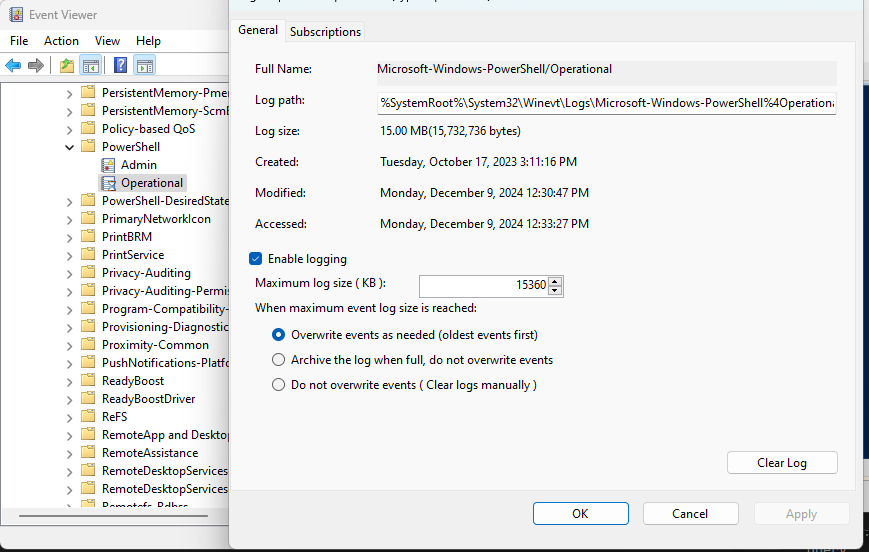
In the Event Viewer, navigate to Applications and Services Logs > Microsoft > Windows > PowerShell.
Right-click Operational and select Properties.
Ensure that Enable logging is enabled.
If Enable logging is not enabled, select it.Click OK.
Apply and Update Group Policy
On a target Windows server, open the Start menu and type
cmd.Click Command Prompt.
At the prompt, type
gpupdate /forceand click OK.Repeat steps 1-2 for each server in the environment.
