Table of contents
New features and updates
Changes to rules
Tuning and bug fixes
New features and updates
Barracuda XDR Automated Threat Response (ATR) for Barracuda SecureEdge
The March 2025 release of Barracuda XDR includes automated threat response (ATR) for Barracuda SecureEdge.
When malicious intent is detected by external services in the Barracuda XDR platform, Barracuda XDR sends ATR requests to block malicious IP addresses to SecureEdge. In SecureEdge, these block requests translate to network ACL rules. By enabling and configuring ATR, malicious traffic can be blocked automatically, thereby reducing the time a threat remains active.
For more information, see Setting up ATR for SecureEdge .
Barracuda XDR Automated Threat Response (ATR) for Sophos XG/XGS Firewall
The March 2025 release of Barracuda XDR includes automated threat response (ATR) for Sophos XG/XGS.
Automating responses to threats found by Sophos XG/XGS reduces the workload, letting you focus on other tasks. The shortened response time reduces the risk of potential threats turning into issues for your customers and increases security for their businesses.
For more information, see Setting up SOAR for Sophos XG and XGS Firewall .
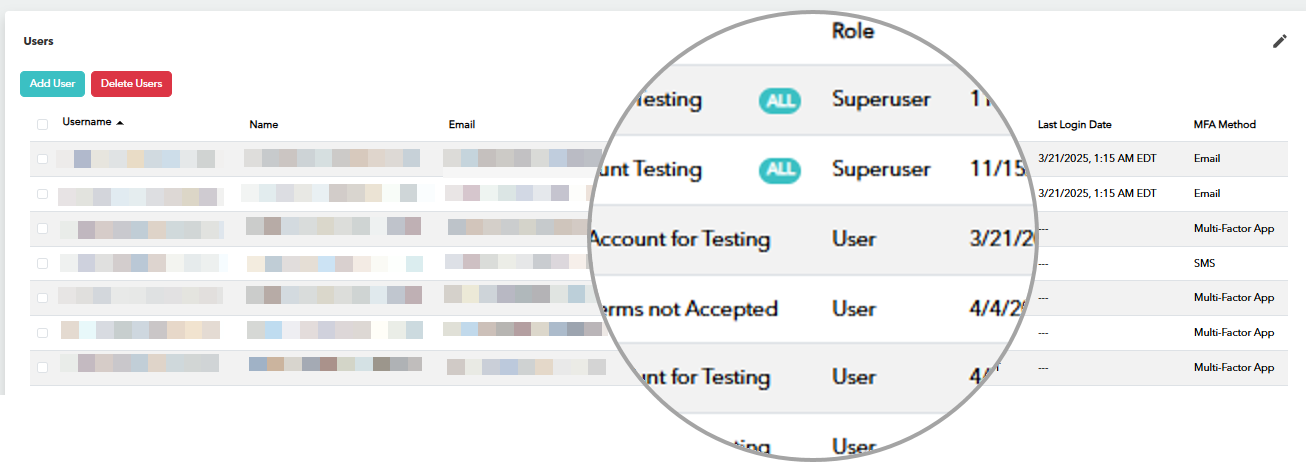
Access level displayed on the User Management page
The User Management page now identifies the users that have All access.
In Barracuda XDR Dashboard, click Administration > User Management.
In the table, users with All access are identified with an icon in the table.
Expanded Threat Intel Sources for IP addresses
Expanded Threat Intel Sources now pull in hundreds of thousands of additional malicious and suspicious IP addresses.
Changes to rules
New Microsoft Office 365 Suspicious SharePoint File Deletion Activity Rule
The new Microsoft Office 365 Suspicious SharePoint File Deletion Activity rule detects if a user has deleted over 1000 files in SharePoint within a 10 minute timeframe.
Rules Enhanced with Automated Threat Response (ATR)
The GLB.AA.CAS Azure Conditional Access Policy Modified rule has been enhanced with ATR.
Retired rules
The following rules have been retired:
Barracuda Incident Response - Potential Incident: Post Delivery Threat
Microsoft Office 365 SharePoint Site Permissions Modified
GLB.ID.EGD Barracuda EGD Distributed Phishing Campaign Detected and Blocked
GLB.ID.ESS Mimecast Distributed Phishing Campaign Detected and Blocked
Tuning and bug fixes
The following have been updated:
Addressed Automated Threat Response bug fixes for certain SonicOS versions for SonicWall.
Reduced the alert volume for Microsoft Office 365 Conditional Access Policy Block from New Geolocation.
Tuned Microsoft Defender for Endpoint Malicious Threat Detected Not Remediated to ignore Low or Informational alerts.
Reduced the number of users added to top 5 for the rule Windows User added to High Risk Security Enabled Group.
