Rule
Microsoft 365 Suspicious New Inbox Rule Created
Purpose
This detection monitors Microsoft 365 accounts for new suspicious inbox rule creation. After gaining access to a victim's account, threat actors will often create an inbox rule inside their mailbox to maintain stealthy access. This inbox rule can do anything a normal inbox rule could, but is usually used to forward emails matching sensitive keywords, like ‘invoice’ or ‘payment’, to an external email address controlled by the attacker. It is also usually created as a hidden inbox rule. These tactics allow the threat actor to intercept financial information pertaining to the compromised user/organization and their contacts, all without the impacted user’s knowledge.
Objective
Test detection of a suspicious hidden inbox rule creation.
Test workflow
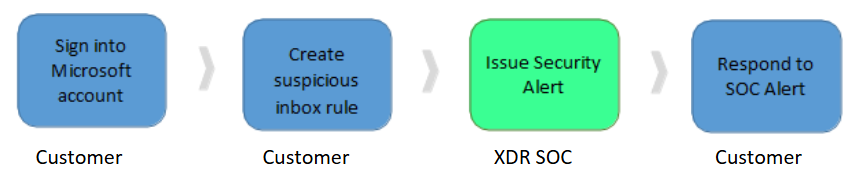
Navigate to Microsoft Outlook.com and sign in.
Click the gear icon in the top right corner.
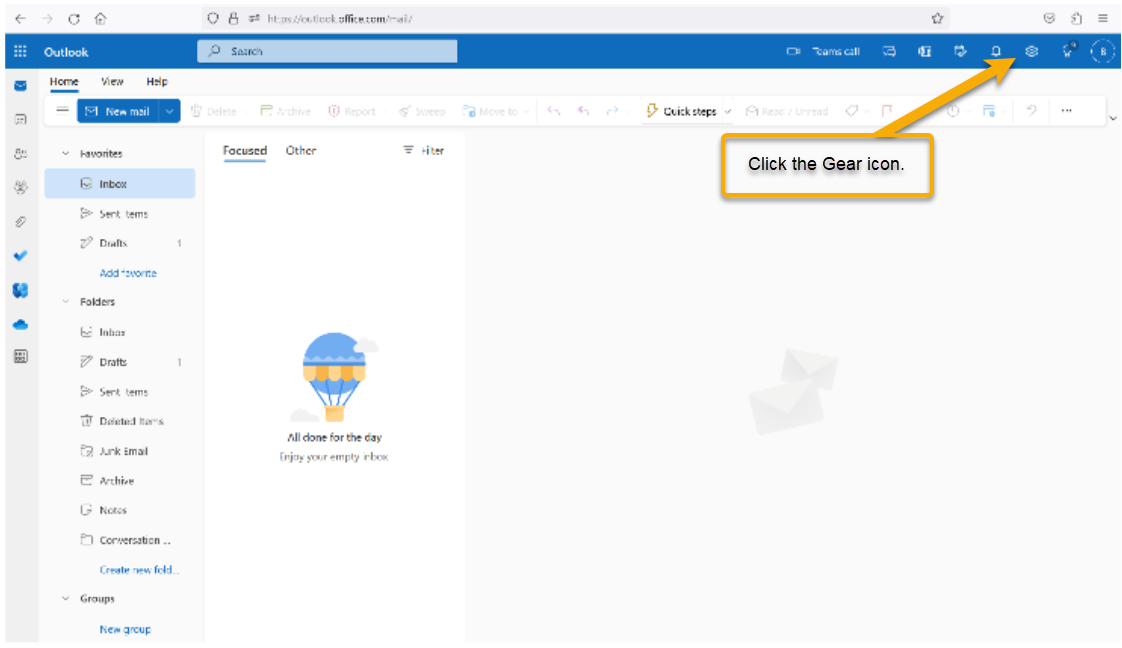
Click Mail in the navigation menu, then click Rules.
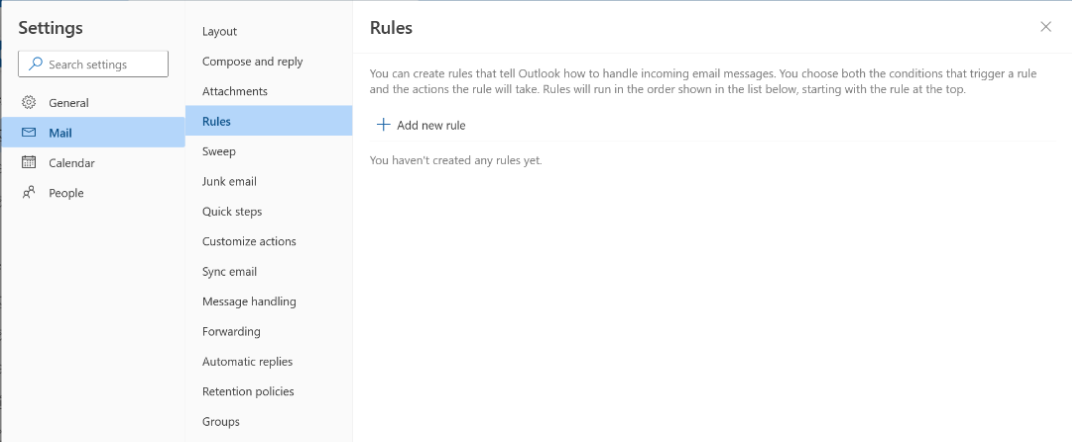
Click + Add new rule.
Do the following:
Give your rule a name, such as “.” to make this a hidden inbox rule.
Set the conditions for your rule to look for messages containing keywords such as “payment”.
Specify the actions to be performed on matched emails, such as forwarding to another account.
Click Save.
A Barracuda XDR alert triggers from the SOC describing this impossible travel scenario. You can view the alert via the Barracuda XDR Security Dashboard.
We request that you reply to the security alert stating that the reported activity was associated with authorized security testing.
The SOC team closes the incident, marking the conclusion of this threat simulation test.
