Welcome to the Barracuda XDR’s monthly release notes! At XDR, we are committed to protecting Barracuda Managed XDR customers from complex threats. To achieve this, we continuously introduce new features as well as enhance our detection, automation, threat intelligence, and automated response capabilities to combat evolving threats. In May 2025, we’ve introduced a variety of new features, fixes, important updates and enhancements.
What’s New This Month
New features include the release of the Barracuda Managed XDR Collector Appliance hardware, direct SentinelOne console access, and several other small improvements
Major improvements to Office 365 Anomalous Login and Impossible Travel detections
Multiple tuning and suppression enhancements across Suricata, SentinelOne, Google Workspace, and firewalls
SOAR automation expanded for high-fidelity Windows and Azure detections
SentinelOne STAR Rule update for early detection of PLAY ransomware
New features
The Barracuda Managed XDR Collector Appliance hardware is now available!
The BX500 Collector Appliance hardware is a Barracuda Manufacturing purpose-built appliance that replaces the outdated legacy Sensors.
This plug-and-play device makes it easier to manage Barracuda Managed XDR Network Security and monitor the health of hardware, provide support, and manage patching and upgrades.
For more information, contact your Sales Representative.
For technical specifications and details, see the BX500 Collector Appliance Hardware Quick Start Guide.
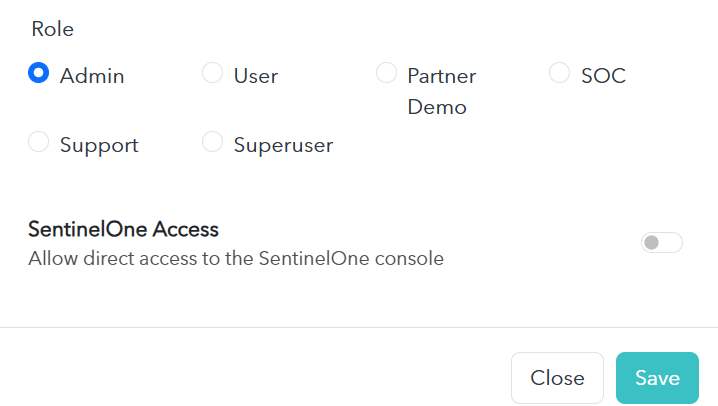
SentinelOne Console Access
The Barracuda Managed XDR Dashboard now provides read-only access to the SentinelOne console, allowing you to see a fuller picture of security events and what is going on in their environment.
To do this, click Infrastructure, User management, then click Edit User. For more details, including prerequisites, see Setting up direct access to SentinelOne for users.
Improvements
Session timeout duration increased
The session timeout duration for the Barracuda Managed XDR Dashboard has been increased to 15 days, so you are automatically logged out of the Barracuda Managed XDR Dashboard if you stay logged in for 15 days. This is more convenient for users while maintaining security standards.
Okta Preview Support
You can now select whether your integration monitors Okta or Okta Preview, Okta’s staging environment.
Improvements to the Email Distribution page
Some small improvements have been made to the Email Distribution page.
Improved focus when viewing alerts in the Dashboard
Focused the ticket when viewing an alert in the Dashboard by removing some unnecessary comments.
Detection Updates
Detection Name | Description |
Office 365 Anomalous Login | Added correlation and suppression for VPNs, known devices, org-shared IPs, and mobile devices. Reduced overall alert volume and refactored customer alert content. |
Office 365 Impossible Travel | Added Suppression for same two device names which the two logins are originating from, org-shared IPs, reoccurring IPs with 30 days and mobile logins. Improved alert logic and content. |
User Added to Global Administrator Role | Added Suppressed if prior similar change occurred from known IP. |
Suricata - External Permitted Malicious Traffic - Repeated | Added Suppressed if from known scanners: Hurricane Electric, Palo Alto, Censys, Shadow Server. |
Firewall - RDP From Internet | Allow-listed specific customers to reduce noise. |
Meraki Threat IP Communication Detected | Allow-listed specific customers to reduce noise. |
SentinelOne - New Threat Not Mitigated/Mitigated | Revised threat matrix to tune alerting. |
Windows Remote File Download via Cmd.exe | Added Suppression window increased to 24 hours. |
Windows Suspicious Scheduled Task Creation | Added Suppression window increased to 24 hours. |
Google Workspace Suspended/Re-Enabled Users | Allow-listed specific customers. |
SOAR Enhancements
Detection Name | Description |
Windows System and Security Logs Cleared | Newly automated |
Windows Suspicious Logon Failures (Legacy) | Newly automated |
Windows User added to High Risk Security Enabled Group | Filtered to top 5 target user data in ticket to reduce template size. |
GLB.AD.CAS User Added as Owner for Azure Application | Added two new fields to ticket: Application added/initiated. |
Palo Alto SOAR Setup | Updated Campus docs to include port translation for 4433 to 443. |
CloudGen CC ATR 500 error | Resolved. |
Managed EDR Updates
Item Name | Description |
S1 Agent Upgrade for Managed EDR | Upgraded to version v24.2 |
New STAR Rule | Early Detection of PLAY Ransomware |
STAR Rule Enhancement | Added additional ransomware file extensions. Ex: .safepay .killsec .Blacklock .incransom .Threeam .threeamtime .devmanv1 .EVEREST .nspire .interlock |
