Architecture
The following is the architecture diagram for Barracuda Managed Vulnerability Security:
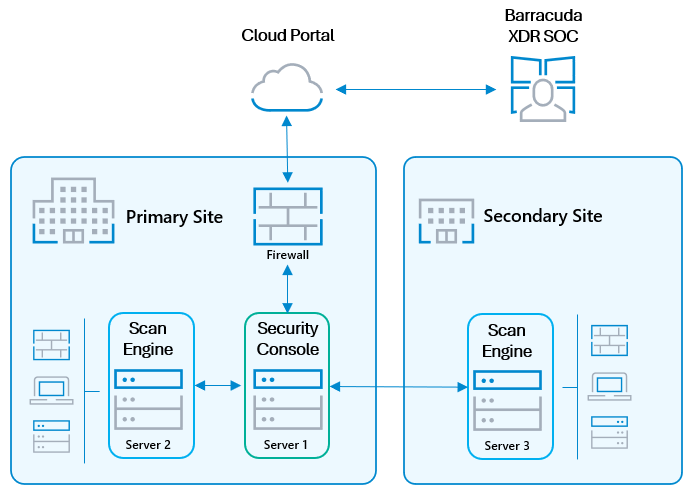
Barracuda Managed Vulnerability Security runs on two servers:
A server acting as the dedicated security console
A server acting as the scan engine
Requirements
Before you install Barracuda Managed Vulnerability Security, you should know the following:
Host System Requirements
Networking Rules
NAT Settings
Host System Requirements
The Rapid7 deployment requires two dedicated hosts; one that runs the security console application, and another that run the scan engine application. Windows servers are recommended.
Recommended System Resources - Security Console
Asset Volume | Processor | Memory | Storage |
|---|---|---|---|
< 5,000 | 4 cores | 16 GB | 1 TB |
Recommended System Resources - Scan Engine
Asset Volume | Processor | Memory | Storage |
|---|---|---|---|
< 5,000 | 2 cores | 8 GB | 100 GB |
Supported Operating Systems
Platform | Versions |
|---|---|
Windows |
|
Linux |
|
RedHat |
|
CentOS |
|
Networking Rules
Source | Destination | Port | Notes |
|---|---|---|---|
Security Console | updates.rapid7.com | TCP 443 | System updates and license activation |
Security Console | support.rapid7.com | TCP 443 | Technical Support |
Security Console | https://us3.api.endpoint.ingress.rapid7.com:443 | TCP 443 | Connectivity to Barracuda XDR SOC Management Platform |
Security Console | us3.deployment.endpoint.ingress.rapid7.com | TCP 443 | Connectivity to Barracuda XDR SOC Management Platform |
Security Console | s3.us-west-2.amazonaws.com | TCP 443 | Connectivity to Barracuda XDR SOC Management Platform |
Security Console | Scan Engine(s) | TCP 40814 | Management of scan activity and retrieval of scan data |
Scan Engine(s) | Security Console | TCP 40815 | Management of scan activity and retrieval of scan data |
Scan Engine(s) | Scan Targets | All TCP & UDP Ports | Scan Engines require unimpeded access to any port that may be open (visible) on your scan targets. |
Security Console | Your internal SMTP relay | TCP 25 or 465 | Reporting |
NAT Settings
A NAT rule is necessary so the Barracuda XDR SOC can reach the Rapid7 Security Console to manage the vulnerability scanning. The steps for creating a NAT rule vary depending on your organization’s networking infrastructure.
Create a NAT policy to allow traffic from the Barracuda XDR SOC IP addresses (listed below) to the internal IP address of running the Security Console application via a public IP assigned to your organization over port 3780.
3.233.123.93
34.232.30.171
Link to Rapid7 Documentation: https://docs.rapid7.com/insightvm/system-requirements
