Important Announcements and Notes
Outdated technical features are subject to removal to keep the CloudGen Firewall up to date and performing properly. See the following two paragraphs for the features that will be removed in this release and the features that are subject to removal in upcoming releases.
Certain features will be removed completely because they have become technically obsolete; other features have become outdated and will be replaced by improved technology.
Features No Longer Supported as of the 8.3.3 Release
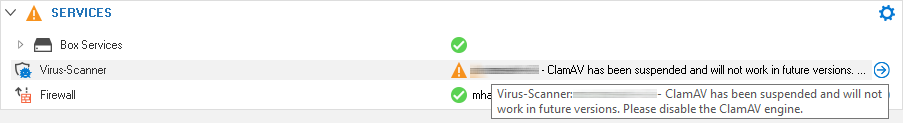
Virus Scanning with ClamAV
The firewall will start the service, however, the service will be highlighted with a warning notifying the customer about the deprecation.
Features that Will Become Obsolete in an Upcoming Release
- FWAudit
- WAN Optimization
- CloudGen Firewall Web UI
- PKI
- Reset SMS Counter
- SMS Control
Precautionary Security Measures for Control Centers
Use the Appropriate Firewall Admin Release
Generally, Barracuda Networks recommends using the latest version of Firewall Admin for a new firmware release.
As of the public availability of this firmware 8.3.3, Barracuda Networks recommends using at least Firewall Admin version 8.3.3-xx. You can download this version here: https://dlportal.barracudanetworks.com/#/packages/5770/FirewallAdmin_8.3.3-21.exe
Release Notes
Firmware version 8.3.3 is a minor release.
Proxy Server Certificates
The proxy server no longer supports SHA1 signed certificates and requires SHA256 certificates instead.
EoL and EoS Status
For more information on which devices and services have reached Eol or EoS status, see the following:
- Barracuda NextGen and CloudGen Firewall Appliances - EoS / EoL Definitions
- End-of-Support for CloudGen Firewall Firmware
What's New in Version 8.3.3
New Data Field for Telemetry
New fields have been added to the telemetry data set. These new fields can be found in the categories Control Center and Events at the end of the table.
For more information, see Telemetry Data.
General Term Replacement of SSL Inspection to TLS Inspection
The term SSL has been replaced by the more appropriate term TLS at all relevant places in the user interface.
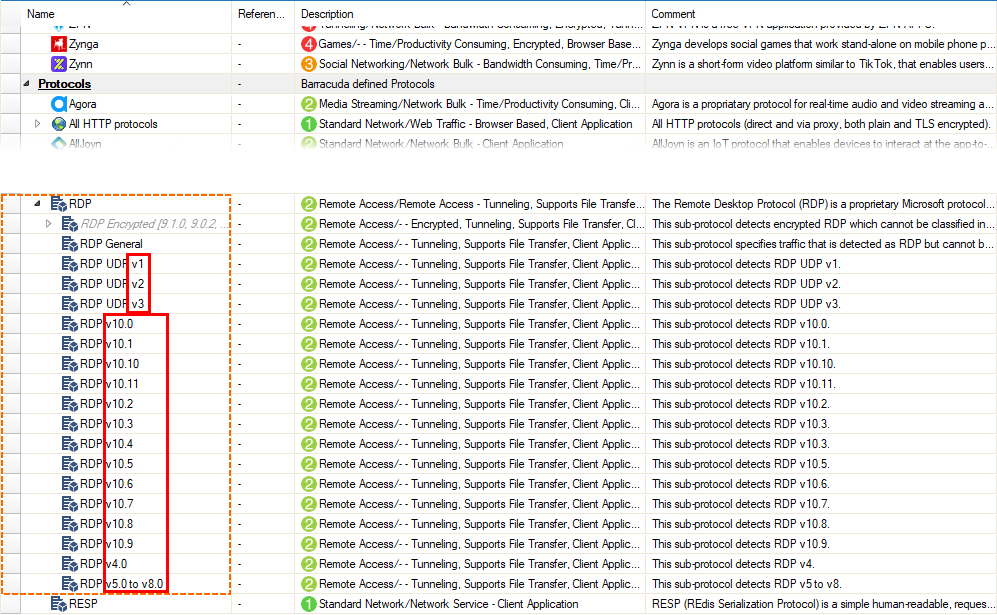
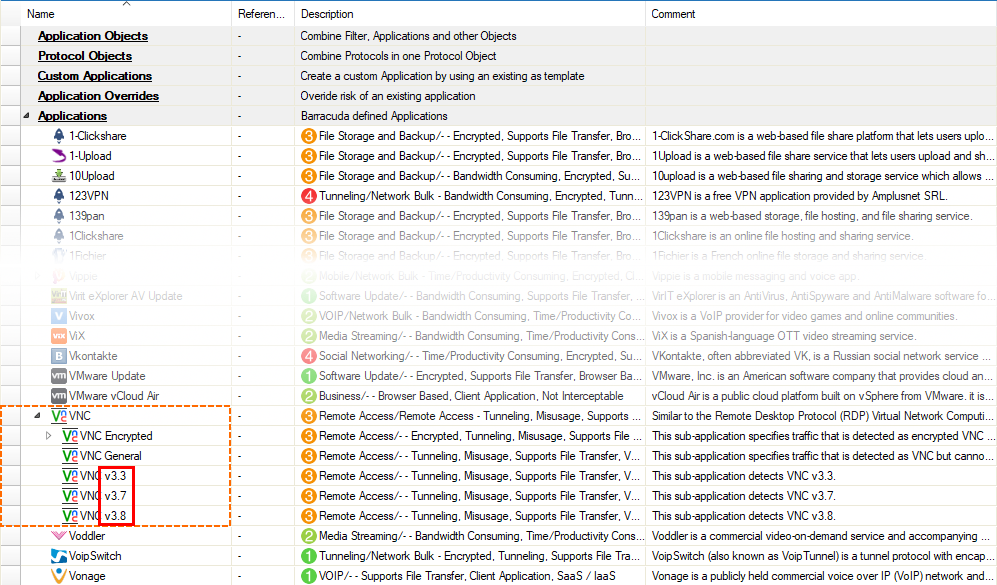
Version Information for Protocols RDP and VNC
The display of the protocols RDP and VNC now includes information on the protocol version.
| RDP | VNC |
|---|---|
|
|
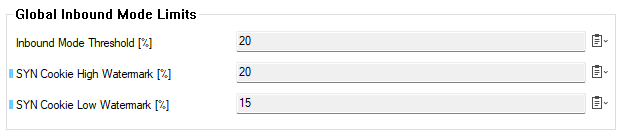
Dedicated Configuration Section for Global Inbound Mode Limits
Because the global inbound mode settings do not need a firmware or service restart to take effect, the configuration section can now be accessed via the path CONFIGURATION > Configuration Tree > Infrastructure Services > General Firewall Settings.
| Former Section for Settings | New Section for Settings |
|---|---|
|
|
Improvements Included in Version 8.3.3
Authentication
- Usernames in TOTP are no longer case-sensitive. [BNNGF-82953]
fwauthdno longer uses 100% of CPU time in certain situations. [BNNGF-86657]- In the authentication system, groups are now handled correctly for usernames containing special characters. [BNNGF-87929]
- SAML authentication now works as expected. [BNNGF-89482]
- Using Explicit Groups in authentication now works as expected. [BNNGF-90056]
- Redirecting authentication now works as expected. [BNNGF-90102]
Barracuda Firewall Admin
- The Access Control Service no longer crashes in certain situations. [BNNGF-87583]
- Barracuda Firewall Admin no longer crashes under a high system load. [BNNGF-88735]
- SSL-inspection will from now on be named as TLS-inspection. [BNNGF-89907]
- The editor window for named networks shows network addresses in CIDR notation as expected. [BNNGF-90305]
- When creating an application object, applications are now listed as expected. [BNNGF-90349]
- The edit field for entering new group names for the pre-authentication scheme now accepts the '.' character for the mapping scheme. [BNNGF-90756]
- The number of configured workspaces and their last modification time (in Unix timestamp format) on the Control Center have been added to the telemetry data set. [BNNGF-90983]
- The configuration settings for inbound mode limits can now be accessed at CONFIGURATION > Configuration Tree > Infrastructure Services > General Firewall Settings. [BNNGF-91136]
Barracuda OS
- Wi-Fi configuration files are now processed correctly. [BNNGF-76329]
- VRF now works as expected on a Bond with VLANs in all types of virtual routers. [BNNGF-84386]
- Entries in the firewall activity log file are now processed and now differentiate correctly between Local Block/Local Deny, and forwarding Block/Deny. [BNNGF-85414]
- The display of the protocols RDP and VNC now includes information on the protocol version. [BNNGF-85434]
- The firewall no longer freezes in the boot phase if more than 1000 routes are configured. [BNNGF-86079]
snmpwalknow matches with the tunnel state as expected. [BNNGF-88542]- The
qedeethernet driver is installed and now works as expected. [BNNGF-88581] - SNMP requests are handled as expected. [BNNGF-89083]
- The tunnel interfaces are being set up in the Shared Networks and IPs section as expected. [BNNGF-89085]
- Spaces and the underscore character are now allowed in user names. [BNNGF-89238]
- The performance of using pool licenses has been improved. [BNNGF-89410]
- The integrity check now works as expected with firmware 9.0.0. [BNNGF-89833]
phionctlservices start as expected. [BNNGF-90078]- The firewall is no longer generating erroneous alert events about the fan and the power supply. [BNNGF-90114]
- WAN connections are no longer disconnected in certain situations. [BNNGF-90177]
- When updating HA systems with CloudGen Access Proxy enabled, you must reconfigure the proxy to generate a new enrollment URL. [BNNGF-90315]
- SNMPv3 is no longer blocked by the default ruleset. [BNNGF-90338]
- OSPF works with 3rd party devices as expected after upgrading from firmware 8.3.1. [BNNGF-90413]
- When in stateless mode, the prefix delegation is now applied on the interface that has been set up when it's being received via router advertisements. [BNNGF-90474]
- The statistics collector now works as expected. [BNNGF-90626]
- Syslog streaming to the Control Center works as expected. [BNNGF-90662]
- The ping command is now supported for IPv6. [BNNGF-90779]
- The log entries for IPv6 management tunnel-probing have been improved. [BNNGF-90780]
- SQL requests now work as expected. [BNNGF-90952]
- SNMPd no longer causes memory leaks. [BNNGF-90956]
- The assignment of a correct IP address to the LTE modem works as expected. [BNNGF-91157]
- Sessions from dynamic rules are now correctly terminated when the dynamic rule expires or is disabled. [BNNGF-91184]
- The synflood-protection value Server-Default now works as expected. [BNNGF-91455]
- Terminating an existing session on a Schedule object now works as expected. [BNNGF-91568]
- The PPE config file is applied as expected during a box installation. [BNNGF-92437]
- The default minimum version for TLS has been set to 1.2 for inspection policies. [BNNGF-92514]
- After upgrading an AWS instance, the SN is handled correctly. [BNNGF-92887]
Control Center
- In the licensing tab on the Control Center, licenses are now displayed as valid if the base license is valid. [BNNGF-87083]
- Broken VPN/GTI references no longer occur in HA clusters with dedicated HA box configurations. [BNNGF-88141]
- Default nodes can now be linked to a repository as expected. [BNNGF-89387]
- The Access Control Service is available for CC-managed F80 firewalls. [BNNGF-89976]
- ConfTemplate Manager conditions now work as expected. [BNNGF-90584]
- Destination/Redirection with site-specific Global Objects now works as expected. [BNNGF-90615]
- Performing a
ccactivateon a Control Center now updates licenses correctly. [BNNGF-91981]
DHCP
- The DHCP advanced configuration now delivers correct values. [BNNGF-87089]
- Default routes are correctly introduced for DHCPv6 addresses. [BNNGF-89895]
- The DHCP relay starts as expected. [BNNGF-90029]
- When adding or removing an existing interface to the DHCP relay configuration, the service is restarted as expected. [BNNGF-90885]
Firewall
- The memory management for the firewall has been improved. [BNNGF-87842]
- The host firewall access rule for allowing traffic on the DHCP interface now also includes xDSL interfaces in the inbound rule. [BNNGF-88467]
- Unexpected HA failovers no longer occur in certain situations. [BNNGF-88845]
- The traffic for the Teams application is now recognized correctly. [BNNGF-89834]
- The type of service is copied correctly in the case of IFWD, PRX, and IPRX. [BNNGF-90044]
- In case a box has a corrupt ruleset caused by a faulty object reference, an appropriate warning is displayed. [BNNGF-90551]
- All user agents now work as expected. [BNNGF-92802]
HTTP-Proxy
- The proxy server no longer supports SHA1 signed certificates and now requires SHA256 certificates. [BNNGF-89207]
- Emails with attachments from mobile devices are handled as expected if AV is enabled in the reverse proxy. [BNNGF-91199]
NGInstall
- If NGInstall fails to format a USB drive, it will retry several times, and if this also fails, a dialog will give detailed information about the cause. [BNNGF-89602]
Report Creator
- IPS Report now shows intrusions in readable text instead of IDs. [BNNGF-87086]
Virus Scanner
- ATP Scan now works as expected with archives that contain large numbers of PDF files. [BNNGF-91336]
VPN
- IKEv2 phase 2 rekeying is now handled correctly. [BNNGF-86223]
- IPsec tunnels using hostnames do not terminate anymore in certain situations. [BNNGF-89412]
- VPN tunnels no longer cause unexpected loads. [BNNGF-89515]
- Azure vWAN tunnels do not terminate after a certain time in certain situations. [BNNGF-89672]
- TINA tunnels no longer terminate due to failing heartbeats. [BNNGF-89808]
- When operating a single VPN tunnel with the option 'One tunnel per subnet', all transports now work as expected after re-activating the tunnel. [BNNGF-90852]
- Routed VPN now uses VPN interfaces as expected. [BNNGF-91115]
- Client-to-Site VPN with RADIUS MFA now works as expected. [BNNGF-92696]
Known Issues
Known Issues Related to CGF Policy Profiles
IMPORTANT – Policy profiles cannot be used on a VPN concentrator or Secure Access Controller!
- Firewall – If a VPN TINA tunnel transport over a specific ISP goes down, the Internet traffic over the same ISP link will not work either. [BNNGF-81749]
- Provider class in boxnet must not be changed "afterward" unless existing VPN tunnels are reconfigured accordingly.
- There is currently no VRF support for policies in 8.3.3.
Known Issues Related to Other Topics
- Status LEDs do not work on the M40b USB LTE modem. [BNNGF-82685]
- Currently, no RCS information is logged for Named Networks. [BNNGF-47097]
- The learn-only mode for OSPF is not working as expected. [BNNGF-65299]
- Firewall – Inspecting traffic for QUIC / UDP 443 is currently not supported. [BNNGF-74540]
Firewall – SSL inspection breaks on Office 365 admin page with TLS 1.3. [BNNGF-83026]
NOTE: If a contacted server does not support at least the configured minimum TLS version, then no connections to that server will be possible. Connections will be reset. This can especially have an impact on embedded frames or Cross-Origin Resource Sharing (CORS) when those servers do not support the same TLS version as the main site.
For troubleshooting:
Turn Box > Infrastructure Services > General Firewall Configuration > Advanced Log Settings > SSL/TLS loglevel to debug.
Look out for "alert protocol version" in SSL logs (Assigned Services > NGFW > SSL), e.g.:11.04.2022 15:36:46 Info firewall: [TAP3Worker] Worker 1: Session 1271: SSL handshake to server failed: ID 2400 192.168.100.95:54525 <=> 104.103.84.247:443 assets.onestore.ms: error in OpenSSL library: error:0A00042E:SSL routines::tlsv1 alert protocol version- Licensing – When a pool license is updated (e.g., due to a validity extension), all licenses that have been activated by Barracuda Activation are removed from the related firewalls. [BNNGF-93258]
A hotfix is already in development and will be provided as soon as possible. - SSL-VPN – SSL VPN may be vulnerable to HTTP request smuggling. [BNNGF-80814]
- Firewall - App-Detection – Initially failing app detection or invalid TLS certificate due to large Client Hello
Certain browsers force the use of Kyber, a post-quantum key agreement algorithm, in TLS. In turn, the Client Hello gets unusually large and initially might cause app detection to fail or an invalid TLS certificate for TLS inspection. After a page refresh in the browser, the app is detected correctly and the TLS certificate is valid.
A workaround is to disable the flag "TLS 1.3 hybridized Kyber support" / X25519Kyber768 in Google Chrome (chrome://flags/), Microsoft Edge (edge://flags/), and "security.tls.enable_kyber" in Firefox (about:config).
For Google Chrome and Chrome OS there is also a policy that can alternatively be used to control this flag. See https://chromeenterprise.google/policies/#PostQuantumKeyAgreementEnabled. [BNNGF-93365]