Important Note for Users Operating Firmware 7.2.5 or 7.2.6
Before You Begin
Barracuda Firewall Admin
After updating a system, you must also download Firewall Admin with the same version. Firewall Admin is backward-compatible. That means you can manage 7.x and 8.x F-Series Firewalls and Control Centers with Firewall Admin 8.x.
Important Note Before Migrating
With firmware release 8.0.2, Barracuda introduced a new 2-layer service architecture that makes the former server node in the configuration tree obsolete. As already announced in previous migration notes, converting the former 3-layer server-service architecture to the new 2-layer service architecture was optional within the period of firmware version 8.0.2 to 8.0.4
Supported Models for Firmware Version 8.2.1
The following models are capable of running firmware version 8.2.1:
Barracuda CloudGen F-Series and Control Center Models | ||
|---|---|---|
Hardware Systems | F12 Rev A, F18 Rev A/B, F80 Rev A/B, F82 Rev A, F93 Rev A, F180 Rev A/B, F183 Rev A, F183R Rev A, F193 Rev A, F280 Rev B/C, F380 Rev A/B, F400 Rev B/C (8/12 ports), F600 Rev C/D, F800 Rev B/C, F900 Rev A (only fresh install), F900 Rev B, F1000 Rev A, F1000 Rev B, C400 Rev A, C610 Rev A | |
| Virtual Systems | VF10, VF25, VF50, VF100, VF250, VF500, VF1000, VF2000, VF4000, VF8000, VC400, VC610, VC820, Proxmox running with KVM images | |
| Public Cloud | AWS, Azure, Google Cloud | |
Standard Hardware Systems | ||
|---|---|---|
| Standard Hardware | A standard hardware system is a Barracuda CloudGen Firewall F-Series running on 3rd-party server hardware using an SF license. Consult the Barracuda Networks Technical Support to find out if your specific standard hardware is supported. | |
Disk Space Requirements
Upgrading to version 8.2.1 requires your disk partitions to have enough free disk space. Firmware 8.2.1 requires the following partition spaces:
Disk Space Requirements FIREWALL:
| Hard Drive Partition | Disk Space Required |
|---|---|
| Swap | 2 GB |
| Boot | 1 GB |
| / | 8 GB |
| /phion0 | 4 GB |
| /art | 3 GB |
Disk Space Requirements CONTROL CENTER:
| Hard Drive Partition | Disk Space Required |
|---|---|
| Swap | 2 GB |
| Boot | 1 GB |
| / | 10 GB |
| /phion0 | 4 GB |
| /art | 10 GB |
Migration Path
All users who have not yet performed the 3-layer to 2-layer architecture transformation must do the following:
- First, upgrade to firmware 8.0.5.
- Perform the 3-layer to 2-layer architecture transformation (also for clusters!).
- Then install firmware release 8.2.1 on top of 8.0.5.
Depending on the firmware release your firewall is currently operating, this migration requires 3 steps:
Step 1. Upgrade Your Firewall to Firmware Release 8.0.5
| Current Version | Via | Follow Migration Instructions |
|---|---|---|
| 8.0.5 | For more information on how to migrate
|
| 8.0.5 | For more information on how to migrate from your current version 8.0.1 - 8.0.3 to 8.0.4, see Migration from Migration from 8.0.1/8.0.2/8.0.3/8.0.4 to 8.0.5. |
Step 2. Transform the Former 3-Layer Server-Service Architecture to the New 2-Layer Assigned-Services Architecture
If you have not already done so in previous firmware upgrades, follow the steps in the article Server Node to Assigned Services Node Migration.
Your firewall is now prepared to upgrade to firmware version 8.2.1.
Migration Instructions for 8.2.1
Before upgrading to firmware version 8.2.1, you may first need to complete a few additional steps. Check the following topic(s) and, if applicable, complete the migration steps listed below:
1. Upgrade of Virtual Machines for Forward Error Correction (FEC)
Firmware version 8.2.1 now contains the new VPN feature Forward Error Correction (FEC). In order for this feature to work as expected on virtual deployments, the virtual hardware must be upgraded to the newest version to work on the ESXi hypervisor directly after the deployment of the virtual machine. For using FEC, the supported version of your hypervisor must be greater than or equal to version 6.5.
For more information, see Step 2 in How to Deploy a CloudGen Firewall Vx OVA on VMware Hypervisors.
2. VPN, Usage of VPN Next Hop IPs
Before firmware version 8.2.1, certain VPN scenarios required you to configure next-hop interface IP addresses for the shared networks. Due to the new 2-layer service architecture, which is represented through the Assigned Services node in the configuration tree, it is no longer necessary to explicitly configure these IP addresses.
However, in this special case, it is necessary to apply some additions to the host firewall ruleset.
For updating the host firewall ruleset, you have two options:
- Add the missing rules manually
- Update the host firewall ruleset with Copy from Default.
How to Update the Host Firewall Ruleset
Step 1. (optional) In case you have made additions/changes to the host firewall ruleset manually:
Create a copy of all these firewall rules.
Option 2.1 (recommended): Add the missing rules to the host firewall ruleset manually.
For more information on how to create a pass rule, see How to Create a Pass Access Rule.
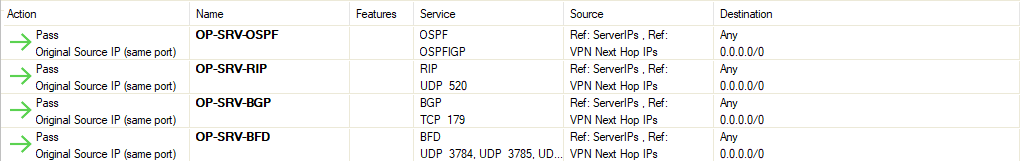
- Go to CONFIGURATION > Configuration Tree > Box > Infrastructure Service > Host Firewall Rules.
- Ensure that Inbound is selected in the top-left corner of the rule list display area.
- Click Lock.
- Add each of the rules in the list to the Inbound Host Firewall Ruleset.
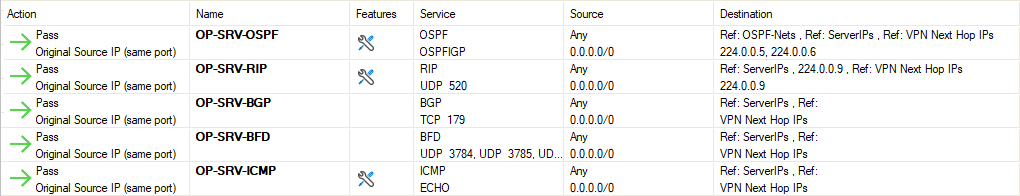
Click Outbound in the top-left corner of the rule list display area.
Add each of the rules in the list to the Outbound Host Firewall Ruleset.
- Click Send Changes.
Option 2.2: (Only if you did not complete Option 2.1) Update the host firewall ruleset with Copy from Default.
After the transformation to the new 2-layer service architecture, the host firewall ruleset can be rebuilt by copying it from the default.
- Log into the firewall.
- Go to CONFIGURATION > Configuration Tree > Box > Infrastructure Services.
- Right-click Host Firewall Rules.
- In the list, click Lock.
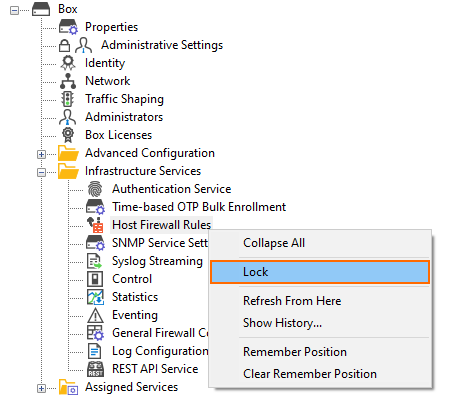
- Right-click Host Firewall Rules.
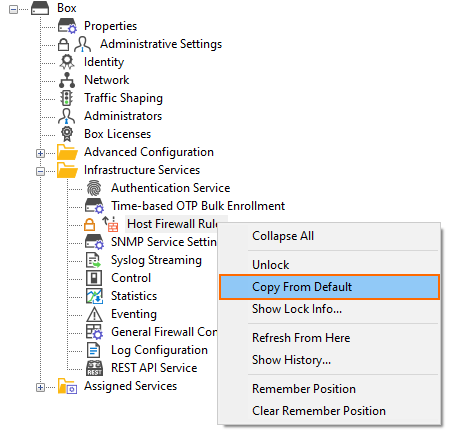
- In the list, click Copy from Default.
- Click Activate in the top-right corner of the window.
Step 3. (optional) In case you have made a copy of individual firewall rules, you must restore them now.
Add your individual firewall rules that you copied before to the host firewall ruleset.
How to Migrate to Version 8.2.1
Download the appropriate download file.
To migrate to version 8.2.1
If You Migrate from Version 8.2.0 to 8.2.1
- Go to the download portal https://dlportal.barracudanetworks.com/#/packages/5330/patch.GWAY-8.2.1-0168+1hotfix.tgz.
- Download the patch package.
If You Migrate from Versions 8.0.0 - 8.2.0 to 8.2.1
- Go to the download portal https://dlportal.barracudanetworks.com/#/packages/5329/update.GWAY-8.2.1-0168+1hotfix.tgz.
- Download the update package.
Start the Update
You can now update the CloudGen Firewall or Control Center.
For more information, see Updating CloudGen Firewalls and Control Centers.
