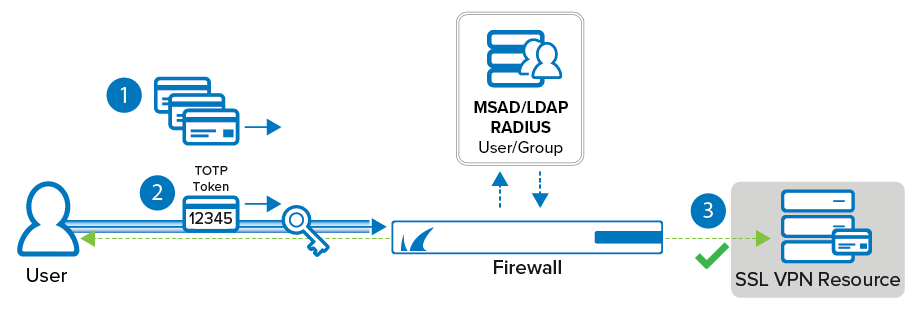
TOTP authenticators, such as Google Authenticator or Microsoft Authenticator, use Time-Based One-Time Passwords (TOTP) generated by an app on your mobile device to authenticate the user. The app generates temporary six-digit numbers calculated from a shared secret and the current time. To be able to use this on the CloudGen Firewall, the TOTP app must be enrolled by the user in a two-step process. To associate TOTP authentication with user and group information, a helper scheme such as MSAD or LDAP must be configured. TOTP authentication is supported for CudaLaunch, the SSL VPN web portal, and the Barracuda VPN Client. For SSL VPN users to be able to self-enroll, they must be able to access the SSL VPN through an Access Control Policy that is not using TOTP as an authentication method. After all users are enrolled, the admin can then switch to an Access Control Policy requiring TOTP authentication. To be able to share the linked accounts over managed firewalls in a single HA cluster, use a repository entry.
Enrolling Mobile Devices
- Create an SSL VPN Access Control Policy that allows users to log in without TOTP authentication.
- Instruct users to log into CudaLaunch or the SSL VPN web portal to enroll their devices. For more information, see How to Self-Enroll for Time-Based One-Time Passwords (TOTP) Using CudaLaunch or the SSL VPN Web Portal.
- Deactivate the original Access Control Policy and enable an Access Control Policy using TOTP.
Before You Begin
- Enable SSL VPN. For more information, see How to Configure the SSL VPN Service.
- Configure an authentication scheme with user/group information such as MSAD or LDAP to be used as the User Info Helper Scheme. For more information, see Authentication.
- Configure time-based OTP as authentication scheme and enable self-enrollment for Users and Groups. For more information, see How to Configure Multi-Factor Authentication Using Time-based One-time Password (TOTP).
Step 1. Configure an MFA Access Control Policy for TOTP Authentication
Configure an Access Control Policy using TOTP as the secondary authentication scheme.
- Go to CONFIGURATION > Configuration Tree > Box > Assigned Services > VPN-Service > SSL-VPN.
- In the left menu, click Access Control Policies.
- Click Lock.
- Click + to add an Access Control Policy. The Access Control Policies window opens.
- Enter a Name and click OK.
- In the Access Control Policy section, select the Active check box.

- (optional) Add Allowed Groups and Blocked Groups.
- (optional) To use multi-factor authentication, add the primary authentication scheme:
- Click + to add the primary authentication scheme to the Authentication Scheme table. The Authentication Scheme window opens.

- From the Authentication Scheme drop-down list, select the primary authentication scheme. E.g., MS Active Directory, or LDAP
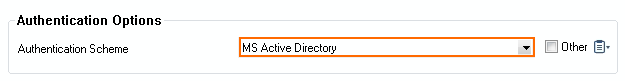
- Click OK.
- Click + to add the primary authentication scheme to the Authentication Scheme table. The Authentication Scheme window opens.
- Click + to add TOTP to the Authentication Scheme table. The Authentication Scheme window opens.
- In the Authentication Schemes window, set Authentication Scheme to Time-based_OTP.
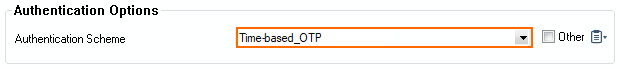
- Click OK.
- (optional) Click + to add Network Access Control criteria to the NAC Criteria table.
- Click OK.
- Click Send Changes and Activate.
Step 2. Activate the Access Control Policy for TOTP Authentication
- Go to CONFIGURATION > Configuration Tree > Box > Assigned Services > VPN-Service > SSL-VPN.
- In the left menu pane, click SSL VPN Settings.
- Click Lock.
- In the Access section, click + and select the Access Control Policy created in Step 2.
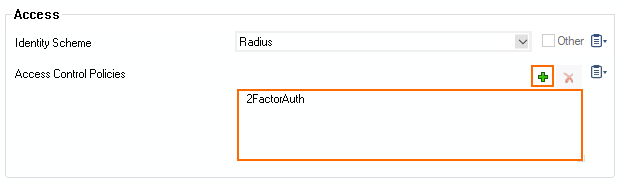
- Click Send Changes and Activate.
Step 3. (Single HA Cluster Only) Create a Repository Entry and Link
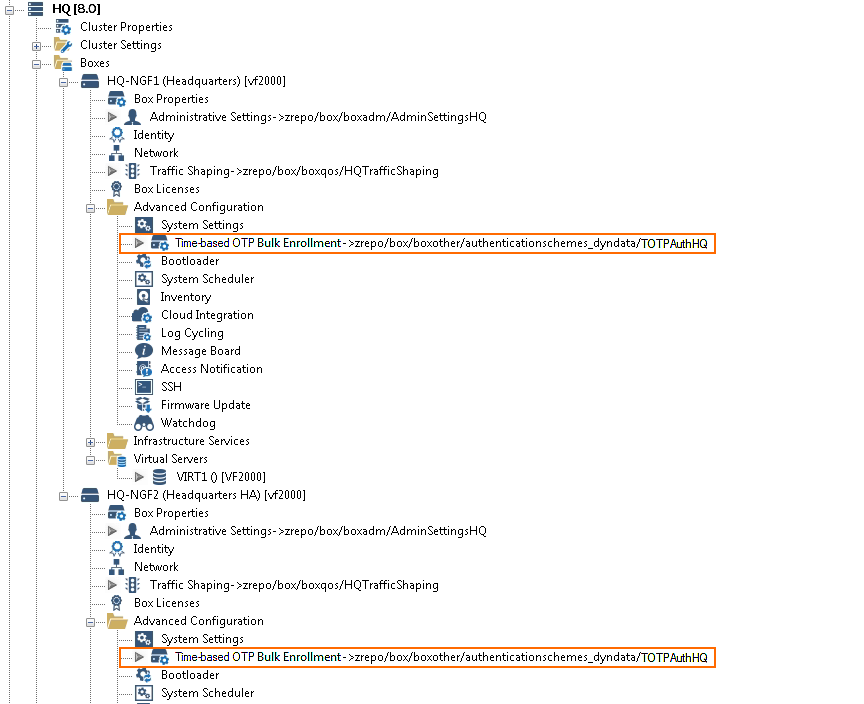
To be able to share the linked TOTP authentication accounts over managed firewalls in a high availability cluster, use a repository entry and create repository links. The primary and secondary firewall must use the repository entry.
- Log into the Control Center.
- Go to Your Managed Firewall > Infrastructure Services.
- Expand the configuration node, right-click Time-based OTP Bulk Enrollment and click Copy To Repository. The Select Object window opens.
- Enter a Name for the new object.
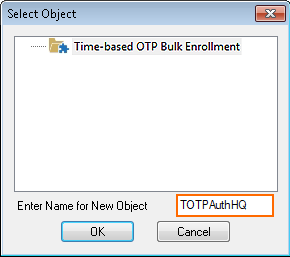
- Click OK.
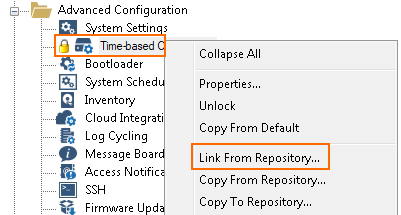
- Right-click Time-based OTP Bulk Enrollment again and click Lock.
- Right-click Time-based Bulk Enrollment again and click Link From Repository.
- Select the Repository entry you just created.
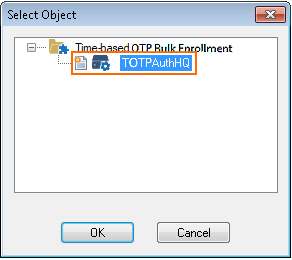
- Click OK.
- Click Activate.
You can now link this repository entry to the secondary firewall in your HA cluster.