Precise timekeeping is very important for the CloudGen Firewall and Control Center. HA synchronization, data accounting, Control Center configuration updates, logging, event notification, and other time-based services rely on a correct time system. The NTP daemon can be configured to listen on the management IP, additional local IP addresses, and, if remote managed, the VIP address of the managed firewall on port UDP/123. Connections to the NTP daemon are handled by the host firewall. Two synchronization methods are supported:
NTP Servers – The firewall acts as a client and retrieves and sets the time according to the time retrieved from the NTP server. You can use multiple NTP servers. The time deviation between the NTP server and the firewall must be less than 1000 seconds for the synchronization to succeed. To continuously synchronize the time with a NTP server, you must enable the NTP daemon. If multiple time servers are used, the time server with the lower stratum value is preferred.
NTP Peers – To keep the time in your network synchronized when the NTP servers are unavailable, use the two-way NTP peer synchronization. NTP peers will converge toward a median time in multiple steps. No synchronization step can exceed two minutes. This means that two systems might take some time to synchronize. You can use MD5, SHA, SHA1, Ripe-MD160, and autokey authentication.
When using a Firewall Control Center for multiple systems in different time zones, consider using UTC for all your systems.
Using the Control Center as a Timer Server for Managed Firewalls – For managed firewalls, you can configure the Control Center as a time server. On the Control Center, set Start NTPd to Yes and sync with external NTP servers. On the managed firewalls, set Start NTPd to Yes and enter the IP address of the Control Center into the list of time servers. NTPd then uses the host rule BOX-NTP-OUT-T and will receive time information from the Control Center.
Before You Begin
(optional) To use an FQDN or hostname as the NTP server, the firewall must be able to resolve the hostname. For more information, see How to Configure DNS Settings.
Step 1. Configure Time Settings
Go to CONFIGURATION > Configuration Tree > Box > Administrative Settings.
In the left menu, click Time Settings / NTP.
Click Lock.
Select your Timezone in the form country/city.
Click Send Changes and Activate.
Step 2. Configure the Time Server
Configure the NTP servers you are using to set and synchronize the time for your Barracuda CloudGen Firewall. NTP servers must be reachable from the management IP address of the firewall or Control Center for stand-alone systems. For managed firewalls, the NTP server must be reachable through the remote management tunnel.
Go to CONFIGURATION > Configuration Tree > Box > Administrative Settings.
In the left menu, click Time Settings / NTP.
Click Lock.
Enable NTP sync on Startup to synchronize with an NTP server via ntpdate when starting. (You can also run an NTP daemon on the system for continuous time synchronization.)
In the Time Server IP or Name table, add the IP address or hostname of the NTP time server(s).
For example, you can add one or all of the following time servers to the list:0.barracuda.pool.ntp.org, ... , 3.barracuda.pool.ntp.org.
A remote, managed CloudGen Firewall as an NTP server can be used by entering its VIP address.Enable Start NTPd to synchronize the NTP daemon with the NTP time server(s).
Set the Local Clock Stratum value for the NTPd. If you are configuring a Control Center, make sure to use a stratum value lower than the default stratum (10) of the CloudGen Firewall.
(optional) Select the events that you want to be notified about (Event-IDs 2070-2073) in Event on NTPd:
start-failure (default)
+stop-failure
++start-success
+++stop-success
The list is additive. Events further down the list automatically include all the events that are listed before them.
Click Send Changes and Activate.
Step 3. (optional) Configure NTP Peers
Configure the NTP peers in your network. NTP peers should be on the same stratum. To authenticate NTP peers, you can choose between passphrase/MD5 and NTP autokey authentication. NTP peers must be reachable from the management IP address of the CloudGen Firewall.
Go to CONFIGURATION > Configuration Tree > Box > Administrative Settings.
In the left menu, click Time Settings / NTP.
Click Lock.
In the Time Peers section, click + to add your NTP peers. The Time Peers window opens.
Specify the following settings for each peer:
Peer IP Address – Enter the IP address for the NTP peer.
Peer Authentication Type – Select None, MD5, SHA, SHA1, Ripe-MD160 or Autokey authentication.
(MD5,SHA,SHA1, RipeMD160 authentication only) Peer Authentication ID – Enter a number between 0 and 1000000. You must use the same Peer Authentication ID on all peers.
(MD5,SHA,SHA1, RipeMD160 authentication only) Peer Authentication – Enter the NTP peer authentication string.
(Autokey authentication only) Peer Host Name – Enter the FQDN for the trusted NTP peer.
(Autokey authentication only) Trusted Public Key – Import the public key for the NTP peer.
Click OK.
If you are using NTP autokey authentication, click Set next to NTP Autokey Configuration. The NTP Autokey Configuration window opens.
Enter the NTP Key Password which is used to encrypt the private key.
Click Create New NTP Key.
Click OK. The NTP certificate is created.
Click Ex/Import and select Export to File. Use the public key to authenticate to other NTP peers.
Click Send Changes and Activate.
Event Processing
The event setting only pertains to NTPd behavior during controlled start or stop sequences. You will not be notified when NTPd is killed manually or just dies unexpectedly. Events are also triggered when the NTPd is restarted on the Box page with the following options:
Restart NTP – The control daemon restarts the NTPd.
Sync – Starts the synchronization processes with the ctrltime script, which stops the NTPd and then executes ntpdate on port 123.
NTP Troubleshooting
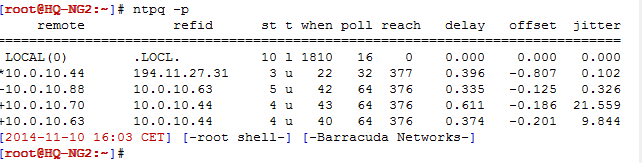
On the command line, enter: ntpq -p to check which NTP servers and peers your Barracuda CloudGen Firewall is using. See below for an example of an CloudGen Firewall using one NTP server (10.0.10.44) and three NTP peers. For more information, see http://ntp.org