You can deploy the Barracuda CloudGen Firewall to the Google Cloud as a gateway or remote connectivity device. The firewall is deployed in a dedicated subnet (public subnet) in the Google Cloud network, and the instances for your cloud-based applications are deployed in backend or private subnets of the network. Each subnet is automatically assigned a dedicated gateway IP address and default route that allow the instances to connect to the Internet via the default Google Cloud gateway. An additional tag-based Google Cloud route is introduced to use the firewall as the default gateway. This route is applied automatically to all backend instances with this tag. Google Cloud firewall rules must be created to allow traffic between the firewall and the backend instances, as well as from the Internet to the firewall. By default, the Google Cloud firewall blocks all traffic, even between two instances in a subnet. The firewall has only a single DHCP network interface with a private IP address. Assign a static or ephemeral (dynamic) external IP address to your firewall to be able to connect to the Google Cloud network, even from outside the network.
Before you Begin
- A Google Cloud account is required.
- Download the Google Cloud firewall image from the Barracuda Download portal.
Step 1. Create a Network in the Google Cloud
Create the virtual network you are deploying your firewall to.
- Go to https://console.cloud.google.com.
- Click the hamburger menu in the upper left corner.
- In the Networking section, click VPC Network.
- In the main area, click Create Network.
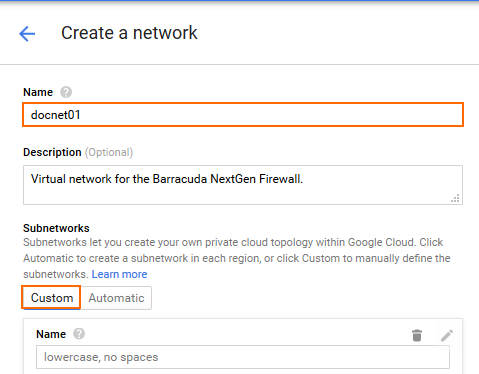
- Enter the Name.
- In the Subnetworks section, click Custom.
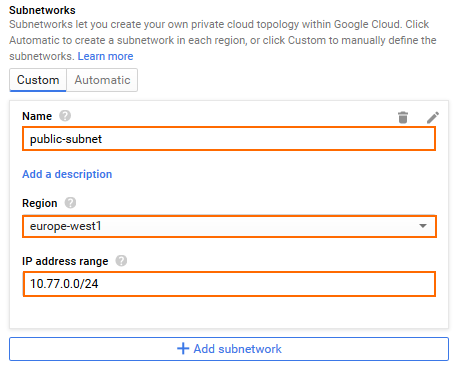
- Create the public subnet:
- Name – Enter
public-subnet - Region – Select your region.
- IP address range – Enter the network in CIDR format. If possible, do not use a network that overlaps with your on-premises network.
- Name – Enter
- Click Add subnetwork and create the private subnet:
- Name – Enter
private-subnet - Region – Select your region.
- IP address range – Enter the network in CIDR format. If possible, do not use a network that overlaps with your on-premises network.
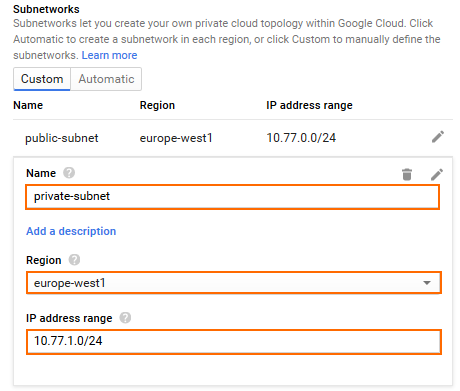
- Name – Enter
- Click Create.
The network is now listed.
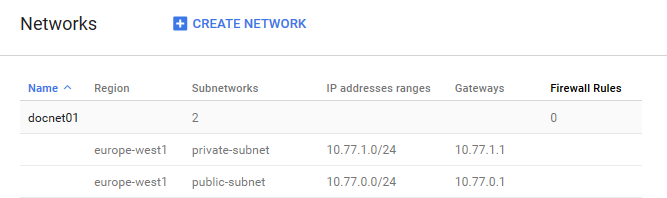
Step 2. Create an External IP Address
Create a static external IP address for your firewall. You can also skip this step and use an ephemeral IP address when creating the firewall instance.
- Go to https://console.cloud.google.com.
- Click the hamburger menu in the upper-left corner.
- In the Networking section, click VPC Network.
- In the left menu, click External IP addresses.
- In the main area, click Reserve static address.
- Reserve a static address:
- Name – Enter a unique name for the external IP address.
- Type – Select Regional
- Region – Select the same region you selected for the public subnet of the network.
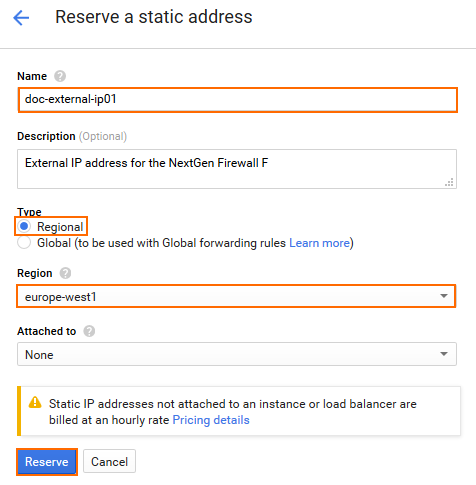
- Click Reserve.
Step 3. Create a Storage Bucket and Upload the Image
Upload the image to Google Cloud. If the upload through the browser does not work, you can instead use Google SDK to upload the image.
- Go to https://console.cloud.google.com.
- Click the hamburger menu in the upper-left corner.
- In the Storage section, click Storage.
- In the main area, click Create bucket.
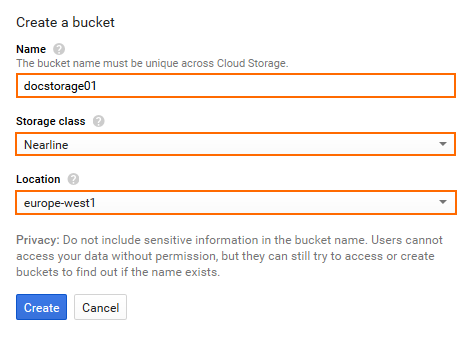
- Create a storage bucket:
- Name – Enter a unique name.
- Storage class – Select a storage class depending on your preferences.
- Location – Select the location matching the region you are deploying in.
- Click Create.
- Click on the storage bucket you just created.

- Click Upload Files and select the firewall image you previously downloaded from the Barracuda Download Portal.
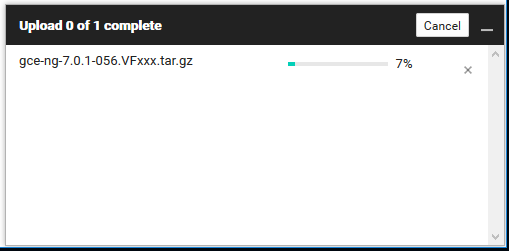
- The upload window is displayed in the lower-right corner.
The image is now listed in the file list of the storage bucket.
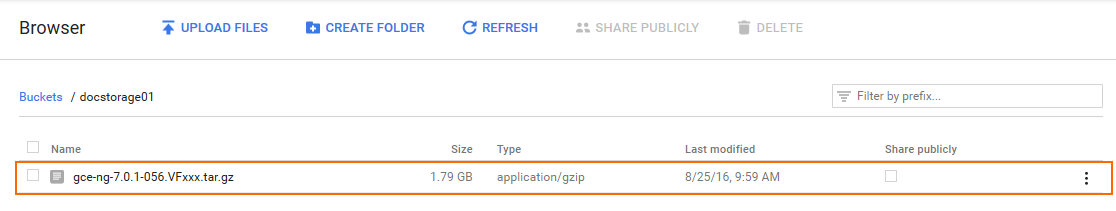
Step 4. Create a Compute Engine Image from the Uploaded Disk Image
To be able to deploy a firewall from the disk image uploaded in Step 3, you must create a Google Compute Engine image. The firewall is created with one DHCP interface. DHCP reservation can be done manually (static) or automatically by Google during deployment. Once assigned, the internal IP address does not change.
- Go to https://console.cloud.google.com.
- Click the hamburger menu in the upper-left corner.
- In the Compute section, click Compute Engine.
- In the left menu, click Images.
- In the main area, click Create Images.
- Create an image using the disk image uploaded in Step 3.
- Name – Enter a name for the firewall image.
- Encryption – Select Automatic (recommended).
- Source – Select Cloud Storage file.
- Cloud Storage File – Click Browse and select the disk image in the storage bucket created in Step 3.
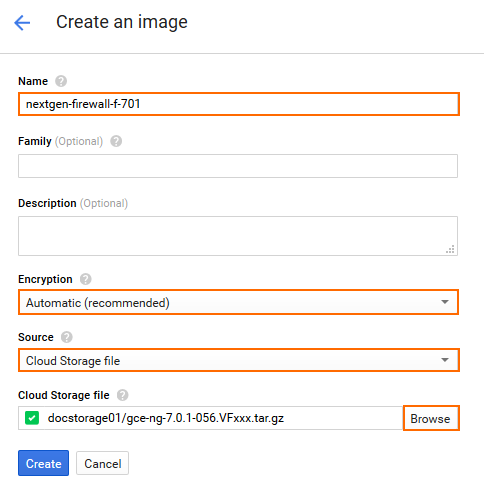
- Click Create.
The firewall image is now listed in the Images list.
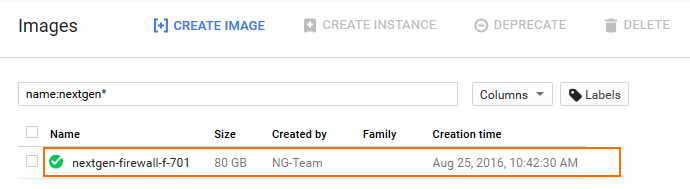
Step 5. Create the Firewall Instance
Create the firewall instance using the image created in Step 4.
- Go to https://console.cloud.google.com.
- Click the hamburger menu in the upper-left corner.
- In the Compute section, click Compute Engine.
- In the main area, click Create instance.

Enter a lowercase Name for the firewall instance.
- Select the Zone. The zone must be in the same region as the public subnet in the network created in Step 1.
- Select Machine type. Verify that the number of vCPU matches the number of cores included in your CloudGen Firewall license.
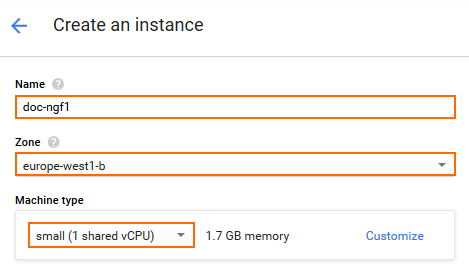
- In the Boot disk section, click Change.
- Click the Your Images tab.
- Select the image you created in Step 4.
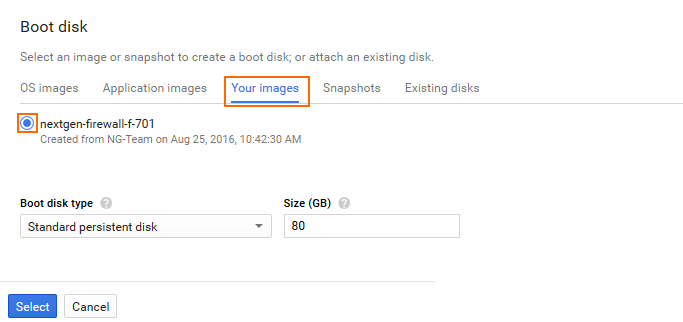
- Click Select.
- Below the Firewall section, click Management, disk, networking, SSH keys.
- Click on the Management tab, enter a Tag for the firewall, and press ENTER. This tag is later used to identify the firewall instance in the Google Cloud firewall rules and routes.
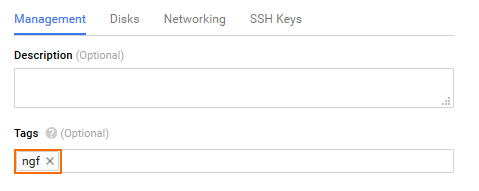
- Click on the Networking tab and configure the following networking settings:
- Network – Select the network created in Step 1.
- Subnetwork – Select the public subnet created in Step 1.
- (optional) Internal IP – To use a specific static internal IP address, select Custom.
- (Custom internal IP address only) Internal IP address – Enter a free IP address in the public subnet. The first IP address in the subnet is reserved for the gateway.
- External IP – Select the external IP address created in Step 2, or else select Ephemeral to use a dynamic public IP address.
- IP forwarding – Select On.
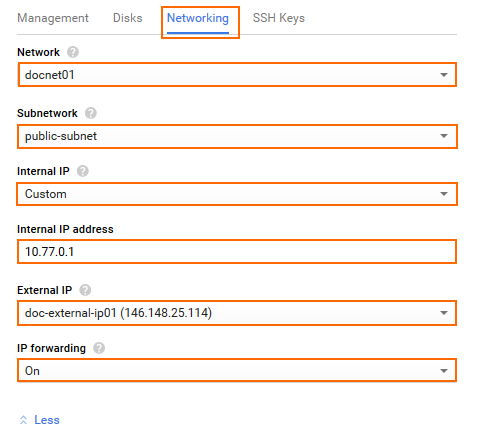
- Click Create.
Step 6. (optional) Create Instances in the Private Subnet
Deploy an instance in the private subnet. The backend instances must be tagged to be able to assign routes and firewall rules to them. Do not assign a public IP address to the backend instances.
Step 7. Create a Default Route for Backend Instances
A default route for each subnet with a metric of 1000 is created for each subnet. For the backend instances to use the firewall as the default gateway, create a default route with a metric lower than 1000. Configure the firewall instance as the next-hop, and add the tags identifying the backend instances. The route is automatically applied to all instances with the same tags as listed in the route.
- Go to https://console.cloud.google.com.
- Click the hamburger menu in the upper-left corner.
- In the Networking section, click VPC Network.
- In the left menu, click Routes.
- Click Create route to create the default route for the backend instances:
- Name – Enter a name for the route.
- Network – Select the network created in Step 1.
- Destination IP range – Enter
0.0.0.0/0. - Priority – Enter a priority lower than 1000. If two routes for the same destination exist, the route with the lower priority is used.
- Instance tags – Enter the tags used for each instance that should be routed over the CloudGen Firewall.
- Next hop – Select Specify and instance.
- Next hop instance – Select the firewall instance created in Step 4 from the list.
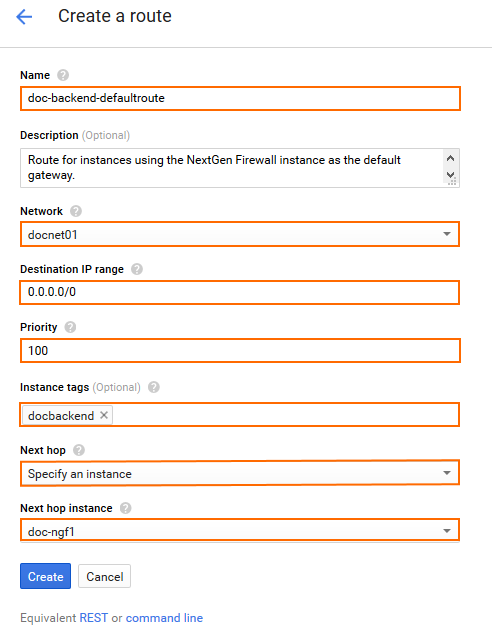
- Click Create.
Step 8. Create a Google Cloud Firewall Rule
Create firewall rules to allow traffic into your virtual network and from the firewall to the backend instances. By default, all traffic is blocked.
- Go to https://console.cloud.google.com.
- Click the hamburger menu in the upper-left corner.
- In the Networking section, click VPC Network.
- In the left menu, click Firewall rules.
- In the main area, click Create firewall rule.
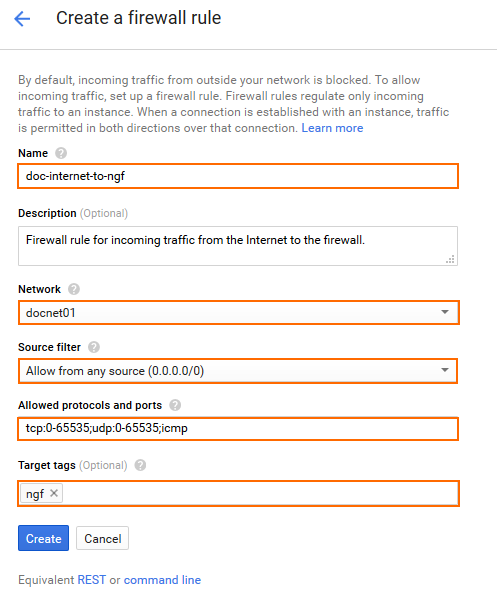
- Create a firewall rule to allow incoming traffic to your firewall Instances:
- Name – Enter the firewall rule name.
- Network – Select the network created in Step 1.
- Source filter – Select Allow from any source (0.0.0.0/0).
Allowed protocols and ports – Enter a semicolon-delimited, lower-case list of protocols and ports in the following format. tcp:807 is required to be able to connect via Barracuda Firewall Admin. E.g., Use
tcp:0-65535;udp:0-65535;icmpto allow all TCP, UDP, and ICMP traffic to the firewall.Target tags – Enter the tag assigned to the firewall in Step 3.
- Create a firewall rule to allow all traffic from selected subnets to the firewall:
- Name – Enter the firewall rule name.
- Network – Select the network created in Step 1.
- Source filter – Select Subnetworks.
- Subnetworks – Select the public subnet and all private subnets with instances that are using the firewall as the default gateway.
- Allowed protocols and ports – Enter a semicolon-delimited, lower-case list of protocols and ports. E.g.,
tcp:0-65535;udp:0-65535;icmpto allow all TCP, UDP, and ICMP traffic between instances in these subnets.
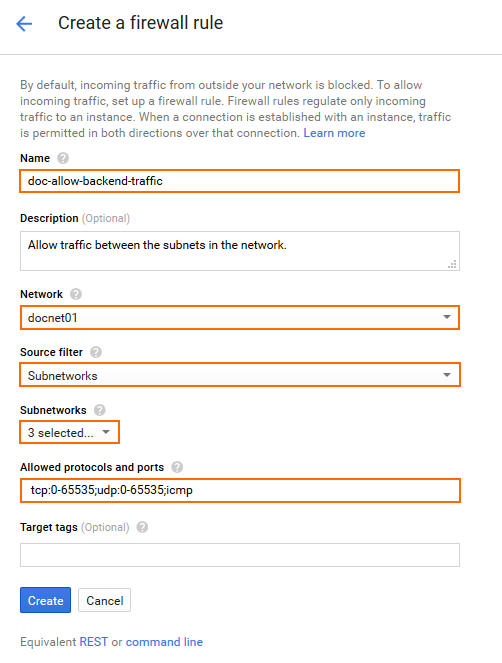
- Click Create.
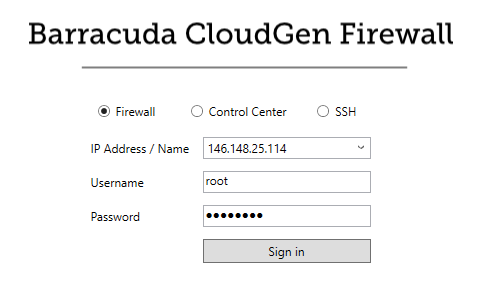
You can now log into your firewall instance running in the Google Cloud using Barracuda Firewall Admin:
- IP address – Enter the external IP address created in Step 2.
- User – Enter
root - Password – Enter the instance Name.
Serial Console
The Google Cloud Platform allows to to enable and connect to the serial port of your firewall instance. This feature allows you to troubleshoot your CloudGen Firewall in case of a misconfiguration in a web-based serial console.
For more information, see How to Access the Serial Console on the CloudGen Firewall in the Google Cloud.
Next Steps
- You can now license and start using your firewall. For more information, see Get Started.
