Azure Cloud Integration allows the firewall to connect directly to the Azure service fabric in order to rewrite Azure user-defined routes and to monitor the IP forwarding setting of the NIC of your firewall VM.
There are two methods available for Cloud Integration. The recommended method is Managed Identity because it is easier to maintain and configure.
- Managed Identity – For more information, see Barracuda CloudGen Firewall Managed Identities in Microsoft Azure.
- Service Principal (User Identity) – Certificate authentication is used to authenticate the firewall when accessing the Azure API endpoints. The certificate must be valid for at least 1 year. The end date of the certificate is used by the setup script to also determine the end date for the Microsoft Entra ID application. When the certificate or the Entra ID application expires, the firewall can no longer use Azure Cloud Integration features until the Entra ID application and the corresponding certificate have been replaced. If a global HTTP proxy is configured, all calls to the Azure REST API are sent via the proxy.
Cloud Integration is required for the following features:
- Barracuda Firewall Admin dashboard Cloud Information element.
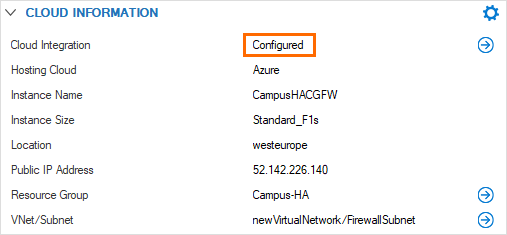
- UDR route rewriting for CloudGen Firewall high availability clusters
- IP forward protection
Before You Begin
- You need sufficient permissions in Microsoft Azure to create a service principal in Microsoft Entegra ID.
- You need sufficient permissions in Microsoft Azure to assign permissions.
- You need a CloudGen Firewall deployed in the Microsoft Azure cloud. For more information, see Microsoft Azure Deployment.
Step 1. Create the Azure Management Certificate
For the firewall to be able to connect to the Azure backend, you must create and upload a management certificate. The certificate must be valid for at least two years.
You can create such a certificate either in Barracuda Firewall Admin or on the CLI using SSH. Follow Step 1.1 to create in Firewall Admin or Step 1.2 to create on the CLI.
Step 1.1 Create the Azure Management Certificate in Barracuda Firewall Admin
Follow this step to create the management certificate in Barracuda Firewall Admin.
- Log into the firewall via Firewall Admin.
- Go to CONFIGURATION > Configuration Tree > Advanced Configuration > Certificate Store.
- Click Lock.
- Right-click in the Certificate Store section.
- Select Create Self Signed Certificate.
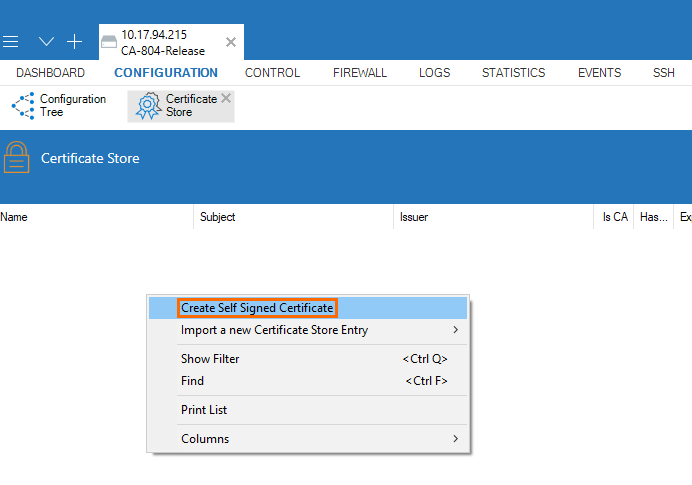
- The Create Self Signed Certificate window opens.
- Enter a name and click Create.
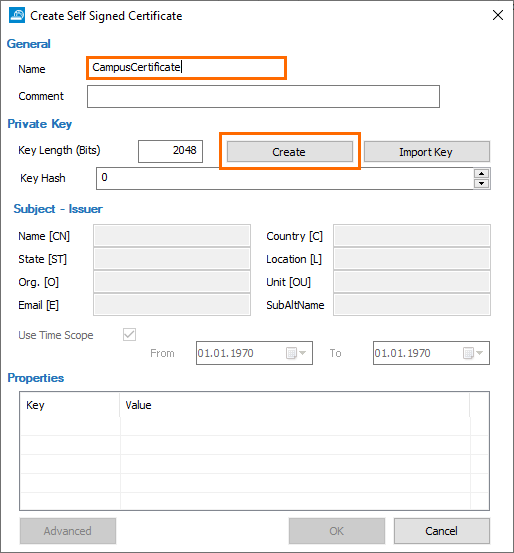
- Specify values for the following:
- Name – Enter a name.
- State – Enter your state.
- Org. – Enter your organization name.
- Email – Enter your email address.
- Country – Enter your country.
- Location – Enter your location.
- Unit – Enter your unit.
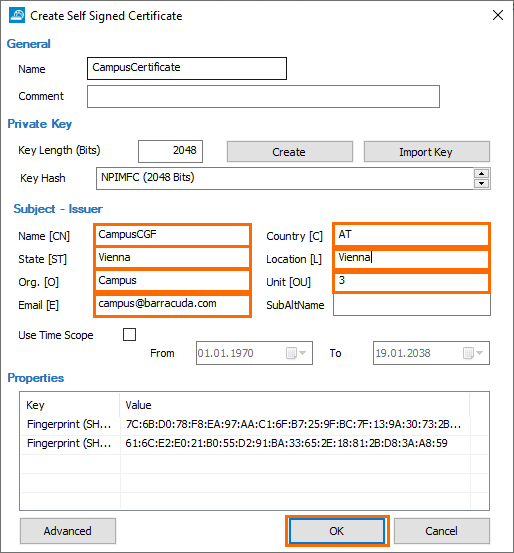
- Click OK. The Certificate Store section opens.
- Click Send Changes and Activate.
- In the Certificate Store section, double-click on the certificate you just created to expand it.
- Select the first entry and right-click it.
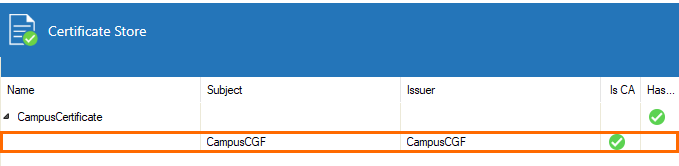
- Select Export the selected Certificate and to File.
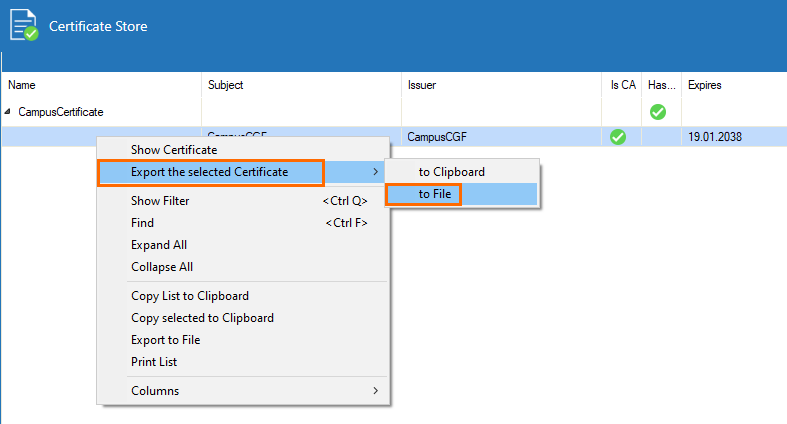
- Save the certificate as a *.cer file.
- Repeat the last step and save the file as *.pem file as well.
Step 1.2 Create the Azure Management Certificate on the CLI via SSH
Follow this step to create the management certificate using the CLI via SSH. Note: Skip this step if you already created a certificate in Barracuda Firewall Admin.
- Log into the firewall via ssh.
Create the certificate:
openssl req -x509 -nodes -days 1095 -newkey rsa:2048 -keyout arm.pem -out arm.pem- Answer the questions at the prompt. The Common Name is used to identify this certificate in the Azure web interface.
Convert the certificate to CER, as required by Azure:
openssl x509 -inform pem -in arm.pem -outform der -out arm.cerExtract the RSA key:
openssl rsa -in arm.pem -out arm.key.pem
You now have three certificates: arm.pem, arm.key.pem and arm.cer. Use the download function to save these somewhere safe on your device.
Step 2. Create a Microsoft Azure Service Principal
Create a service principal in Microsoft Azure and configure to authenticate with a certificate.
- Log into the Azure portal: https://portal.azure.com
- In the left menu of the Microsoft Entra ID blade, click App registrations.
- Click New registration.
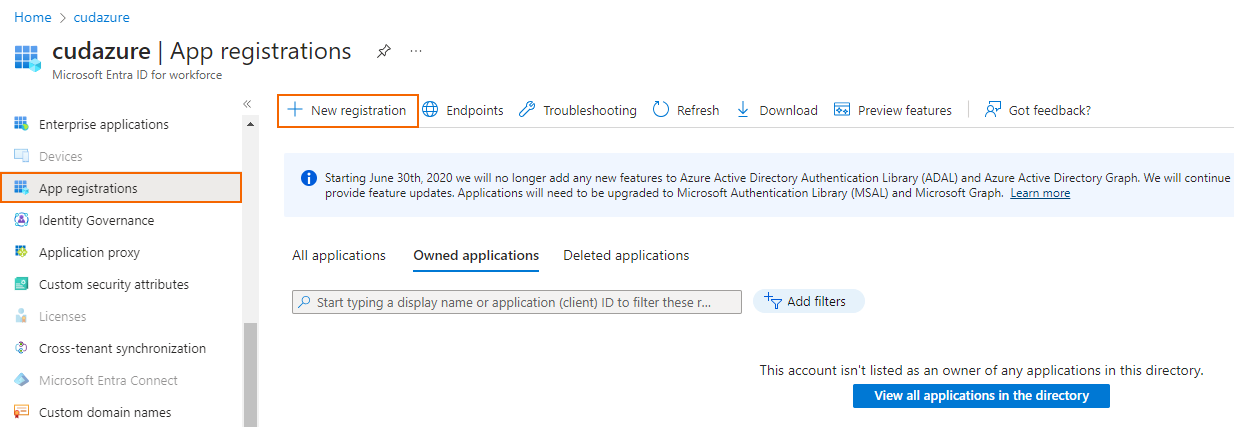
- Th e Register an application blade opens. Specify values for the following:
- Name – Enter a name for the application registration.
- Supported account types – Select Accounts in this organizational directory only (<your_directory_name> only - Single tenant). If you have multiple Microsoft Entegra ID accounts, select Accounts in any organizational directory - Multitenant).
- Redirect URI (optional) – Leave this field blank.
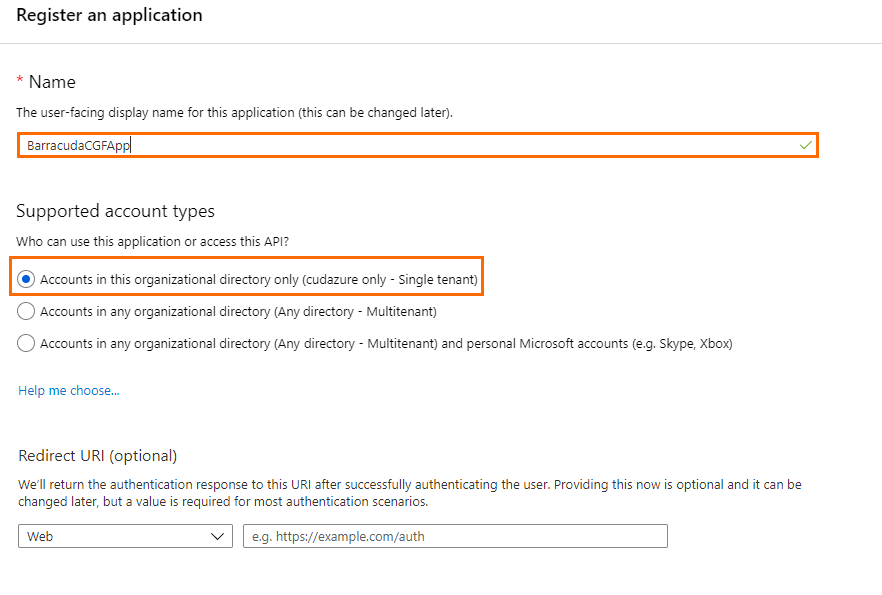
- Click Register.
- The newly registered application opens automatically when it is finished.
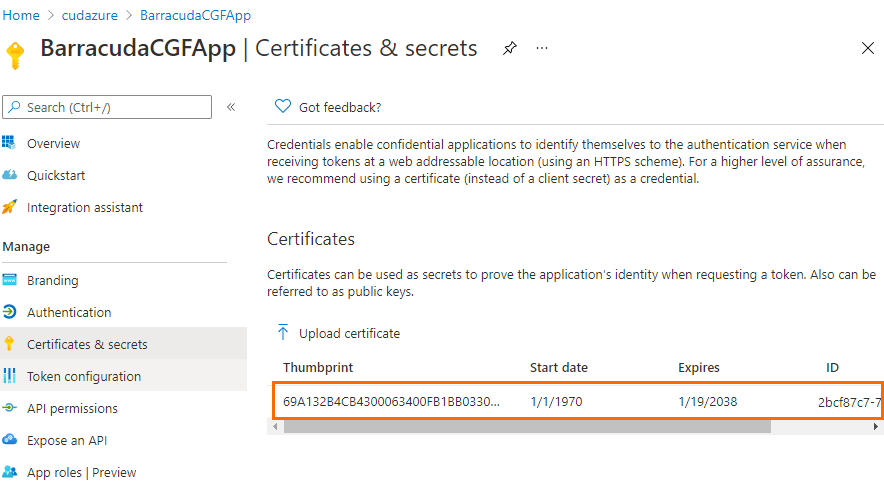
- In the left menu, click Certificates & secrets .
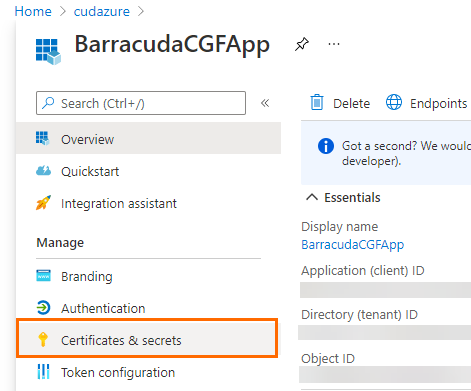
- In the Certificates & secrets blade, click Upload certificate .
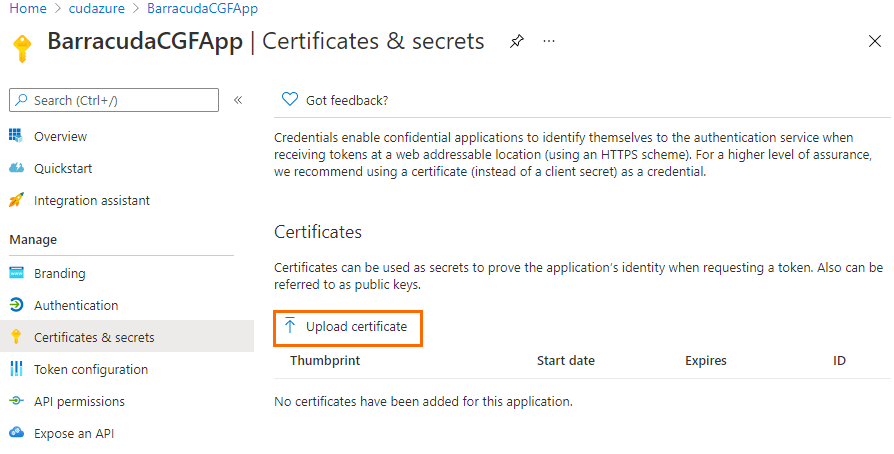
- The Upload Certificate window opens. Select the *.cer file created in Step 1 and click Add .
- After the upload is complete, the certificate is displayed in the list.
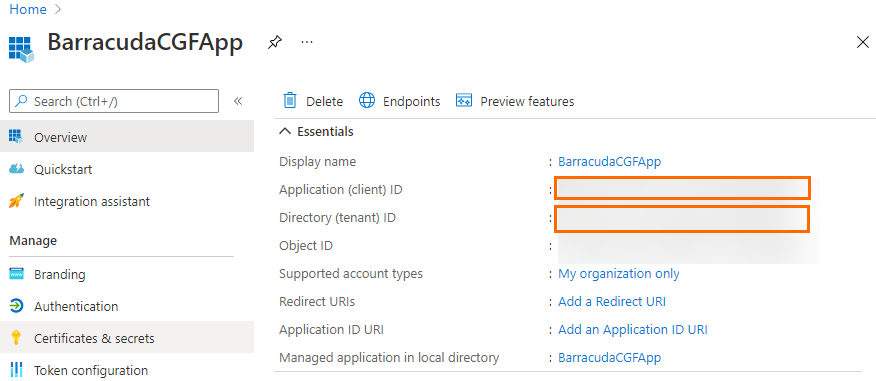
- Click Overview .
- In the Overview blade, copy the Application (client) ID and the Directory (tenant) ID and insert both into a text editor. You will need this information later.
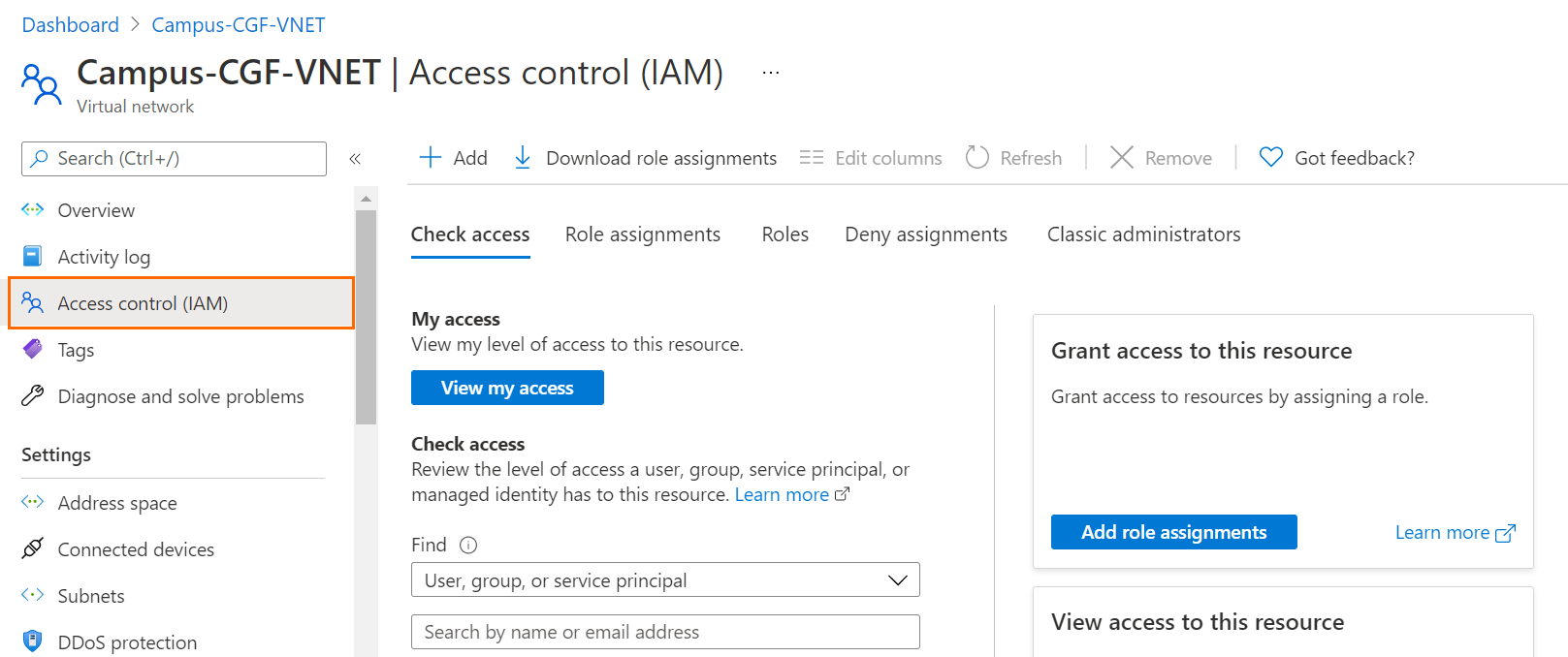
Step 3. Assigning the Permissions
- Go to the Azure portal: https://portal.azure.com
- G o to the Resource Group that contains the VNET and User Defined Routes of the CloudGen Firewall.
- In the left menu, select Access Control (IAM).
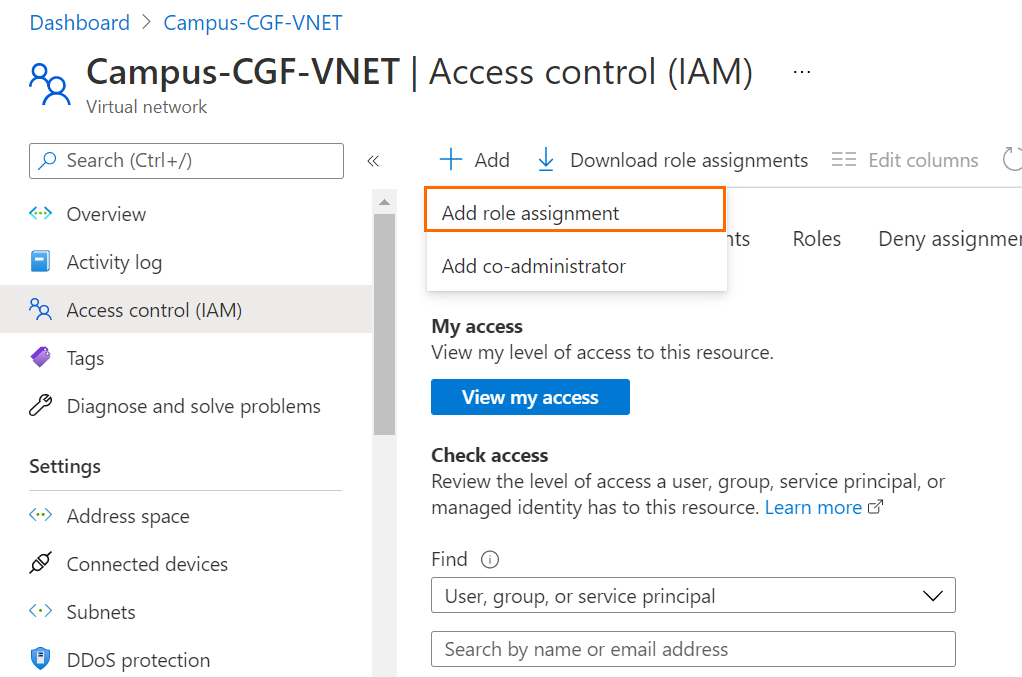
- Click + Add.
- Select Add role assignment.
- The Add role assignment window opens. Specify values for the following:
- Role – Select Network Contributor.
- Assign Access to – Select User, group, or service principal.
- Select – Enter the name of the application created in Step 2 and click on its entry in the list.
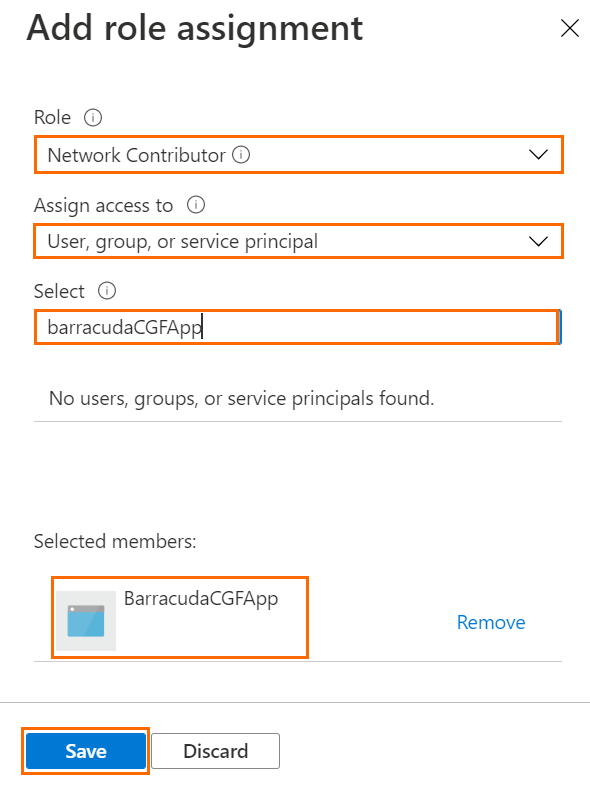
- Click Save.
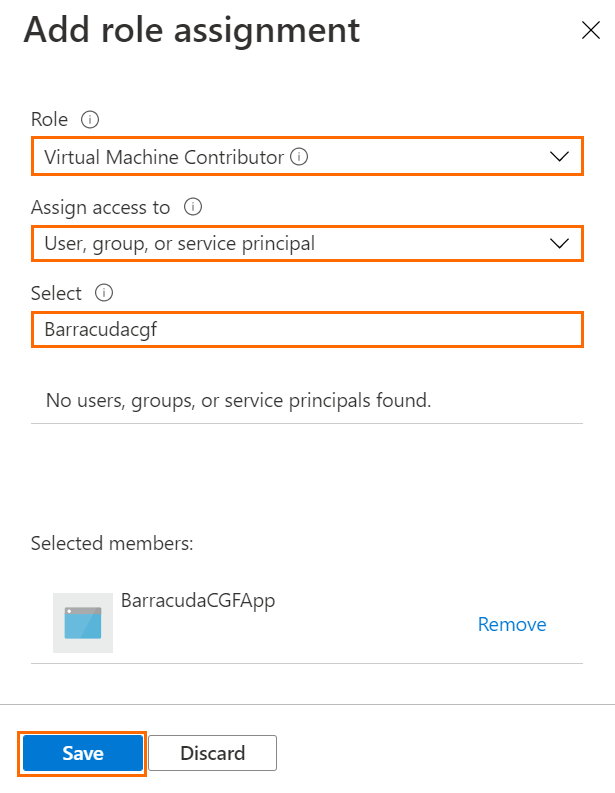
This role is sufficient for the firewall to manage the route tables. If you want the firewall to monitor the IP Forwarding setting of its network interfaces as well, you must add the role Virtual Machine Contributor. Repeat Step 3 and select Virtual Machine Contributor.
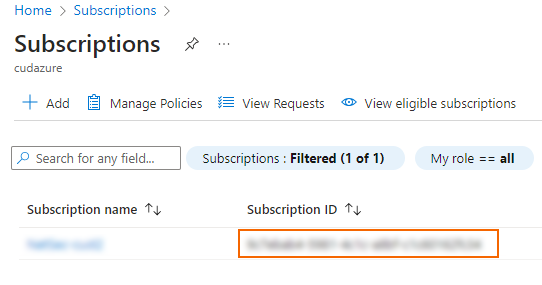
Step 4. Get the Subscription ID
- Log into the Azure portal: https://portal.azure.com
- In the left menu, click Subscriptions.
- Copy the Subscription ID in the Subscription ID column.
- Insert the Subscription ID in the text editor where you already inserted the Application (client) ID and the Directory (tenant) ID. You will need these 3 IDs in the Step 5.
Step 5. Configure Cloud Integration on the Firewall
- Log into the firewall via Firewall Admin.
- Go to CONFIGURATION > Configuration Tree > Cloud Integration.
- Click Lock.
- In the left menu, click Azure Networking.
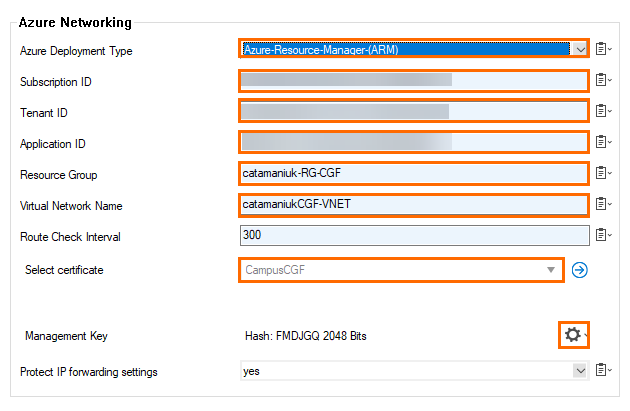
- In the Azure Networking section, specify values for the following:
- Azure Deployment Type – Select Azure Resource Manager.
- Subscription ID – Enter your Subscription ID, retrieved in Step 4.
- Tenant ID – Enter your Tenant ID, retrieved in Step 2.
- Application ID – Enter your Application ID, retrieved in Step 2.
- Resource Group – Enter the name of the resource group containing the VNET and the UDR route table.
- Virtual Network Name – Enter the name of the virtual network.
- Select Certificate – Select the certificate created in Step 1 from the drop-down list.
- Management Key – Click on the settings icon. Select Import from File and select the *.pem file created in Step 1.
- Protect IP forward settings – Select yes.
- Click Send Changes and Activate.
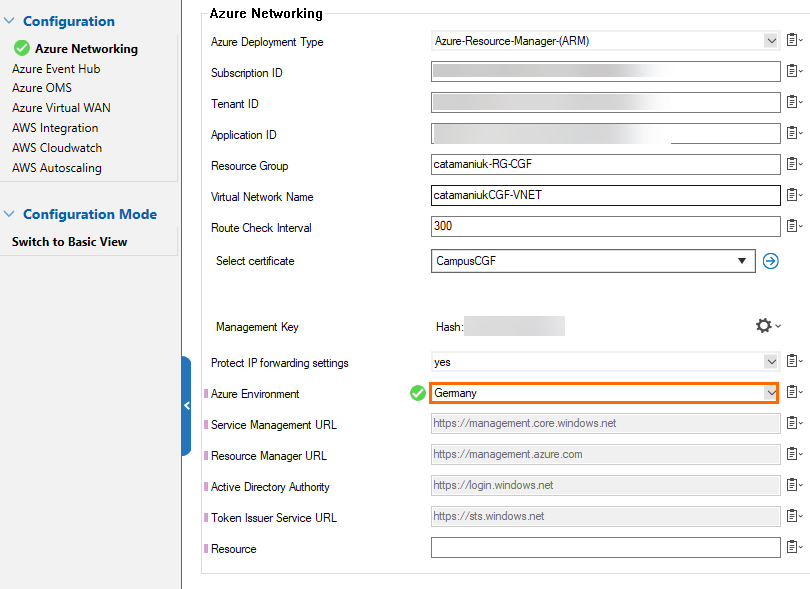
Step 6. Configure Azure Environment
If your firewall is running in a non-default Azure environment, such as Azure Germany, govcloud , Azure China, or Azure Stack, you must configure the Azure environment. Otherwise, you can skip this step.
- Log into the firewall via Firewall Admin.
- Go to CONFIGURATION > Configuration Tree > Cloud Integration.
- Click Lock.
- In the left menu, click Configuration mode and click Switch to Advanced.
- In the left menu, click Azure Networking.
- Then, specify values for the following:
- Azure Environment – Select the Azure Environment from the drop-down menu. Select Explicit if your environment is not listed in the drop-down menu. If you have selected Explicit, you must provide the following configuration:
- Service Management URL – Enter the Service Management URL.
- Resource Manager URL – Enter the Resource Manager URL.
- Active Directory Authority – Enter the Active Directory Authority.
- Token Issuer Service URL – Enter the Token Issuer Service URL.
- Resource – Enter the resource identifier.
- Click Send Changes and Activate.
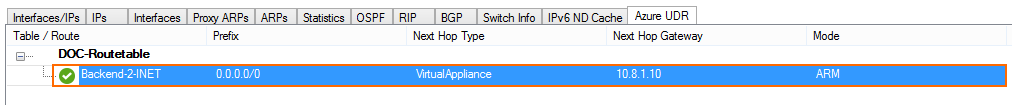
Monitoring
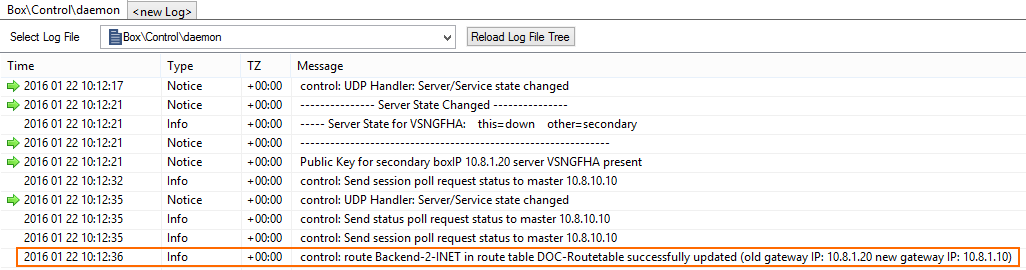
Go to NETWORK > Azure UDR to see the UDR routing table for all subnets in the firewall's VNET. Routes using the firewall VM as the next hop are marked with a green icon. This icon changes to red during the UDR HA failover process.
All activity is logged to the Box\Control\daemon log file.