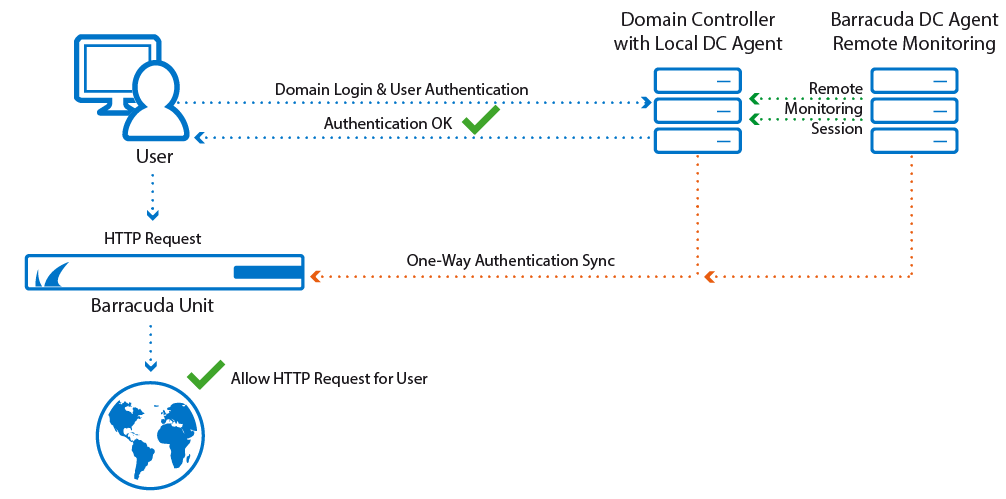
You can install the Barracuda DC Agent either on the domain controller or on a dedicated Windows PC on the office network. The Barracuda DC Agent periodically checks the domain controller for login events and to obtain a record of authenticated users. The IP addresses of authenticated users are mapped to their username and group context. The list of authenticated users is provided to the Barracuda Session Manager on your Barracuda Networks product, allowing true single sign-on capabilities.
A typical use case scenario: Alice comes into her office in the morning and logs into her workstation. She enters her user credentials and is authenticated by the domain controller. The Barracuda DC Agent recognizes that Alice has authenticated herself within the corporate network domain and forwards this information to all connected Barracuda Networks products. These systems now give Alice access to services or network areas for which a valid user or Microsoft Active Directory group context is required. Alice does not need to re-enter any credentials because her initial authentication by Active Directory is reused.
Exclusions
The Barracuda DC Agent lets you manually exclude IP addresses of user client PCs or known multi-user computer systems and provides a "learning mode" that proposes the exclusion of suspicious systems. Due to the complexity of today's network environments and multi-user computer systems, a user-to-IP association is not always possible or required. For example, you can exclude the HTTP Proxy and Terminal Server because they allow multiple users and use a single IP address for authentication against domain controllers.
Remote Monitoring
If you install the Barracuda DC Agent on a dedicated computer system instead of the Active Directory server, you can also remotely monitor Active Directory.
