The TLS Inspection policy contains the information needed for the firewall to be able to accept and initiate TLS connections when intercepting TLS connections of clients protected by the firewall. The policy object defines the behavior when encountering validation errors or revocation check failures. TLS connections that do not meet these requirements are blocked. The TLS Inspection policy also defines the minimum TLS version as well as the allowed ciphers. The connection will be terminated if these minimum requirements are not met.
Create TLS Inspection Policy Object
Create a TLS Inspection policy object for outbound TLS Inspection.
- Go to CONFIGURATION > Configuration Tree > Box > Assigned Services > Firewall > Forwarding Rules.
- Click Lock.
- In the left menu, click TLS Inspection.
- Right-click the table and select New Inspection Policy. The Edit TLS Inspection window opens.
- Enter the Name.
- From the TLS Policy Type drop-down list, select Outbound TLS Inspection and, if required, select Download Intermediate CA Certificates automatically to automatically complete and import missing intermediate certificates.
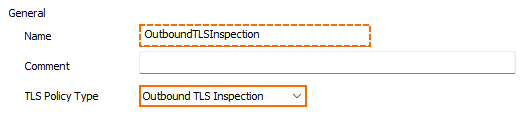
- Configure the TLS Validation Policy settings. For more information on TLS Error Policies, see TLS Inspection in the Firewall.
- Self-Signed Certificates – Select Pass Error to Client, Hide Error from Client, or Block.
- Untrusted Certificates – Select Pass Error to Client, Hide Error from Client, or Block.
- Expired of Not Yet Valid Certificates – Select Pass Error to Client, Hide Error from Client, or Block.
- Revoked Certificates – Select Hide Error from Client or Block.
- Corrupted Certificates – Select Pass Error to Client, Hide Error from Client, or Block.
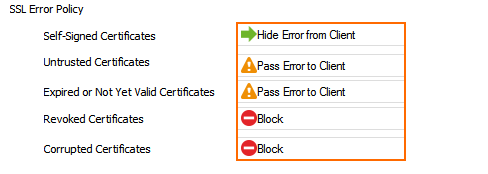
- Select the Enable Revocation Check check box to check the revocation status of the certificate via OCSP stapling, OCSP, or CRL.
- Configure the Action on Revocation Check Error:
- Fail Open – If the revocation check fails due to operational errors, the connection is allowed.
- Fail Close – If the revocation check fails due to operational errors, the connection is blocked.
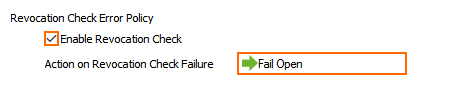
- (optional) Configure Cryptographic Attributes:
Minimum TLS Version – Select the minimum TLS version.
- Cipher Set – Select a preset cipher set, or click Configure to customize the cipher set.
- (optional) Click Configure to customize the cipher set.
- Click OK
- Click Send Changes and Activate.
Next Steps
Configure outbound TLS Inspection. For more information, see How to Configure Outbound TLS Inspection.
