To set up Check Point Firewall-1 Collector, do the following steps, below:
Enable Check Point Firewall Collector
Install the XDR Collector
Configure the Firewall
Open the port on the XDR Collector Host
Enable Check Point Firewall Collector
In Barracuda XDR Dashboard, navigate to Administration > Integrations.
On the Check Point Firewall Collector card, click Setup.
Select the Enable check box.
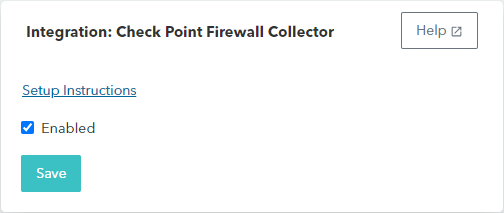
Click Save.
Install the XDR Collector
If you haven't already set up the XDR Collector, do one of the following:
Configuring the Firewall
In Check Point, the Logs & Monitoring > Log Servers page lets you configure external log servers for security and system logs for additional logging storage.
External Syslog Server Configuration
You can configure a gateway to send logs to multiple external syslog servers.
To configure an external syslog server
In Check Point, under Syslog Servers, click Configure.
The External Syslog Server window opens.Enter a Name and IP address.
Enter a Port (9201).
Select Enable log server.
Optionally, select Show Obfuscated Fields.
Obfuscated packets are shown as plain text.Select logs to forward:
System logs
Security logs
Both system and security logs
Click Apply.
Open the Port on the XDR Collector Host
Ensure incoming traffic is allowed on UDP port 9201.
Linux
To open the port, run one of the following, depending on your OS:
Iptables: sudo iptables -A INPUT -p udp --dport 9201 -j ACCEPTfirewalld: sudo firewall-cmd --add-port=9201/udp
Windows
netsh advfirewall firewall add rule name="Check Point Firewall Events" dir=in action=allow protocol=UDP localport=9201
